In today’s increasingly digital world, securing your business against cyber threats is a must. Here at Upper Echelon Technology Group, we understand that every business – big or small – is a potential target to cybercriminals. We know that you, as a business owner, face multiple challenges, notably network security, technology optimization, and leveraging technology to drive business growth. The cyber security risk assessment process plays a significant role in overcoming these challenges.
We live in a world where digitization brings marvelous opportunities, but also unexpected threats. Picture a scenario where your business gets hit by a cyberattack. What would be the cost of potential data loss or network downtime, and how would it affect your bottom-line? Unsettling thoughts, right? That’s exactly why a cybersecurity risk assessment process is crucial. By identifying the threats and vulnerabilities you face, it’s easier to prepare and protect your business.
In case you are looking for a quick answer, here’s a rundown of the critical steps in a cyber security risk assessment process:
- Determine the Scope of the Risk Assessment
- Identify Threats and Vulnerabilities
- Analyze Risks and Determine Potential Impact
- Prioritize Risks
- Document All Risks
Detailed insights on each of these steps will follow in this article. To get the big-picture overview of cyber security risk assessments, head over to our cyber security risk assessments page. Protecting your business from cyber-threats isn’t rocket science – but it does require careful and systematic evaluation. Stick with us, and we’ll show you how – leading to a safer, secure, and more prosperous business.
Understanding the Importance of Cyber Security Risk Assessment
In the rapidly evolving landscape of cyber threats, understanding the importance of a cyber security risk assessment process is crucial for every business. A comprehensive assessment not only helps us identify potential vulnerabilities but also equips us to respond effectively when threats arise. Let’s dive deeper into why this process is so important.
Proving Governance for Compliance Purposes
One of the key reasons to conduct a cyber security risk assessment is to establish and maintain compliance with various regulatory standards. For instance, the ISO 27005 standard provides guidelines for information security risk assessments and is designed to assist with the implementation of a risk-based Information Security Management System (ISMS).
In order to demonstrate compliance with these requirements, it’s vital that we retain documented evidence about the risk assessment process. This includes all steps taken, risks identified, and the measures implemented to mitigate these risks.
Establishing Processes for Risk Management and Identification
A cyber security risk assessment isn’t a one-and-done event. It’s an ongoing process that needs to be integrated into our company’s regular operations. Regular assessments help us establish systematic processes for identifying, analyzing, and managing risks.
It’s important to answer questions like: What are our most crucial IT assets? What type of data breach would significantly impact our business? What are the internal and external vulnerabilities? And, what is the likelihood of exploitation?
By answering these questions, we can effectively prioritize risks and develop data security strategies for remediation. For more on this, you can check out our guide on assessing cybersecurity risk.
Keeping Risk Profiles Up to Date
The digital landscape is continuously changing, with new threats emerging regularly. This makes it crucial to keep our risk profiles up to date.
An annual review of the risk assessment is a must under most compliance mandates. This review should involve executive leadership and the Board of Directors to ensure a thorough understanding of the company’s risk profile.
In addition, certain changes or additions in our IT infrastructure, like onboarding a new Software-as-a-Service (SaaS) or migrating a database from on-premises to the cloud, should also trigger a fresh risk assessment.
At Upper Echelon Technology Group, we combine our expertise in cybersecurity with a personalized approach to IT Managed Services. By regularly updating your risk profile, we ensure your business is always prepared to face any cyber threats head-on!
Next, let’s look at the five-step cyber security risk assessment process, and how it helps us unlock these hidden threats.
The Five-Step Cyber Security Risk Assessment Process
At Upper Echelon Technology Group, our cyber security risk assessment process is a systematic and structured approach to identify, analyze, prioritize, and document risks to your business. Here’s how we do it:
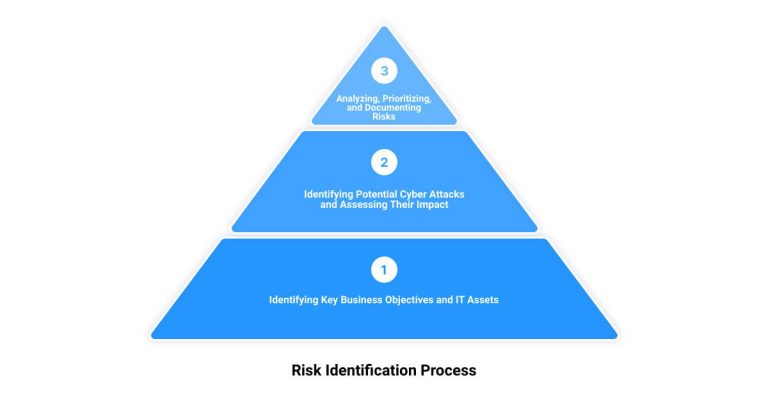
Determining the Scope of the Risk Assessment
We start by identifying the scope of the risk assessment. This involves understanding the breadth and depth of the systems, information, and processes that need protection. We explore everything from your data storage locations, to the individuals who have access to them, and the technology assets you use. This way, we ensure no stone is left unturned, and no potential risk is overlooked.
Identifying Threats and Vulnerabilities
In the second step, we identify potential threats and vulnerabilities. This involves leveraging databases like the MITRE ATT&CK Knowledge Base and resources from the Cyber Threat Alliance. From unpatched software to potential SQL injection attacks, we hunt down all possible sources of danger to your digital assets.
Analyzing Risks and Determining Potential Impact
Next, we assess the likelihood of these threats exploiting the vulnerabilities we’ve identified and estimate the potential impact on your business. This isn’t about guesswork, it’s about making informed decisions based on the discoverability, exploitability, and reproducibility of threats and vulnerabilities. We rank the likelihood and impact on a scale, allowing us to visualize the risks in a clear and understandable way.
Prioritizing Risks
Once all risks are identified and analyzed, we prioritize them. Every threat can’t be tackled at once, so we focus first on the ones that pose the most significant risk to your business. We consider factors like the likelihood of a threat occurring and the potential impact on your business to determine the order of priority.
Documenting All Risks
Finally, we document all identified risk scenarios. This documentation serves as a reference for your team and ours, and aids in risk mitigation strategies. It’s an essential part of the cyber security risk assessment process because it provides a clear and comprehensive picture of your current risk landscape.
Now that we have a clear understanding of the risks, we can build a robust cybersecurity strategy. This includes a mix of avoiding, transferring, or mitigating risks, depending on what’s best for your business.
Remember, at Upper Echelon Technology Group, we don’t just “fix tech issues”. We strive to make your company more profitable by identifying areas where technology can improve your bottom line. Our cyber security risk assessment process is just one way we do that.
To learn more about other aspects of cyber security risk assessments, check out our topic overview page on cyber security risk assessments.
Challenges in Conducting Cyber Security Risk Assessment
When it comes to running a cyber security risk assessment process, several challenges often arise. These issues can be a stumbling block if not properly addressed. Let’s delve into some of these difficulties and how you can overcome them.
Maintaining Asset Inventory
A vital part of the cyber security risk assessment process is keeping an up-to-date asset inventory. This includes identifying all devices connected to your networks that store, transmit, collect, and process data. These could be workstations, servers, smartphones, tablets, and even Internet of Things (IoT) devices, like printers or security systems.
However, this task can be challenging, particularly with the increased adoption of cloud and IoT devices. Devices can be added or removed frequently, leading to visibility issues. Despite these difficulties, maintaining a robust asset inventory is a must for effective risk assessment.
To address this, consider using network scanning tools and ensure regular updates to your asset inventory. These steps will provide better visibility into connected devices and enhance your overall assessment process.
Managing Third-Party Vendor Risk
In today’s interconnected business landscape, many organizations rely on third-party vendors for various services. This relationship, while beneficial, can also expose your business to additional risks. These vendors may have access to sensitive data or critical systems, making their own cyber security practices a crucial aspect of your cyber security risk assessment.
A comprehensive assessment should include evaluating the cyber security measures of your third-party vendors. This ensures that they have robust security controls in place to protect your data from threats.
Addressing Joiner-Mover-Leaver Risk
In any organization, employees come and go, move between departments, or change roles. This constant change, known as the Joiner-Mover-Leaver cycle, can pose a significant risk. For example, an employee leaving the company might still have access to sensitive data, or a new employee might not be properly trained in security protocols.
To mitigate this risk, it’s essential to have strong access control policies in place and to regularly review and update these policies. This includes promptly revoking access for leavers and ensuring that joiners and movers have the appropriate level of access for their roles.
Overcoming Point-in-Time Problems
Many organizations conduct cyber security risk assessments annually, as per compliance mandates. However, this point-in-time approach can be problematic. Risks and threats are constantly evolving, and what was assessed as a low risk a year ago might be a high risk today.
To overcome this issue, consider moving towards continuous risk assessments. This approach allows for real-time monitoring of risks and threats, providing a more accurate and up-to-date view of your organization’s cyber security posture.
At Upper Echelon Technology Group, we understand these challenges and have developed strategies to help businesses overcome them. We offer managed IT services that include continuous monitoring and proactive risk detection to help you stay ahead of potential threats. To learn more about how we can assist you in conducting an effective cyber security risk assessment, contact us today.
Leveraging Managed Services for Effective Cyber Security Risk Assessment
Conducting a robust cyber security risk assessment process is no small feat. It requires continuous monitoring and proactive risk detection, an understanding of compliance requirements, and a dedicated team of professionals to manage it all. As a managed services provider, we at Upper Echelon Technology Group are committed to helping businesses navigate these challenges.
Continuous Monitoring and Proactive Risk Detection
The world of cybersecurity evolves rapidly, and so do the threats that businesses face. It’s not enough to conduct risk assessments at a specific point in time and assume that your security posture remains the same. Continuous monitoring is necessary to keep an eye out for emerging threats and vulnerabilities.
We help you move beyond point-in-time assessments and adopt a proactive approach to risk detection. Our team continuously monitors your systems for potential threats, ensuring that you’re not blindsided by a cyber attack. This approach not only enhances your security posture but also helps you stay ahead of the game.
Enhancing Compliance Posture
Regulatory compliance is an important aspect of cybersecurity risk management. Whether it’s GDPR, HIPAA, or PCI DSS, compliance requirements are constantly changing, and keeping up with them can be a daunting task for businesses.
Our managed services go beyond just solving tech issues. We focus on your business needs and help you navigate the complex world of regulatory compliance. We keep track of changes in compliance requirements and ensure that your business stays compliant, enhancing your compliance posture and reducing the risk of financial and reputational damage.
Collaborating with Managed Detection and Response Providers
Sometimes, the best way to handle cyber risks is to collaborate with experts who have firsthand experience in the field. Managed detection and response (MDR) providers, like Fortra’s Alert Logic, can provide 24/7 risk visibility, threat detection, and compliance coverage.
As part of our commitment to your business, we work with top-tier security consulting partners to perform a comprehensive risk assessment of your IT estate. We provide you with detailed reports documenting continuous monitoring activities, enabling you to make informed decisions about your cybersecurity and compliance programs.
At Upper Echelon Technology Group, we firmly believe that a strong cybersecurity risk assessment process is key to protecting your business. We’re here to support you every step of the way, helping you unlock the hidden threats and secure your business future. If you’re ready to take your cybersecurity to the next level, let’s talk.
The Role of Compliance Requirements in Cyber Security Risk Assessment
In the world of cybersecurity, compliance is more than just a buzzword. It’s a critical component of your overall security strategy. But why is this the case? Simply put, compliance requirements provide a roadmap for implementing adequate security measures. They act as a guide to help us at Upper Echelon Technology Group ensure we’re taking the necessary steps to safeguard your business. Let’s dive a bit deeper into some of these compliance requirements.
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a set of best practices, standards, and guidelines that help organizations manage and reduce cybersecurity risks. It focuses on five core functions: Identify, Protect, Detect, Respond, and Recover. Following this framework enables us to understand the cybersecurity risks your business faces and to develop appropriate measures to manage those risks effectively.
ISO 27000 Series
The ISO 27000 series is an internationally recognized set of standards for information security management systems (ISMS). These standards provide a framework for establishing, implementing, operating, monitoring, reviewing, maintaining, and improving an ISMS. Adhering to these standards means we’re committed to maintaining a robust security posture and continually improving our security processes.
GDPR, HIPAA, and PCI DSS
Specific industries have their own compliance requirements. For example, businesses dealing with personal data of EU citizens must comply with the General Data Protection Regulation (GDPR). Healthcare organizations in the US need to adhere to the Health Insurance Portability and Accountability Act (HIPAA). And companies that process, store, or transmit credit card information must comply with the Payment Card Industry Data Security Standard (PCI DSS).
Each of these regulations has its own specific requirements for protecting sensitive information. Non-compliance can lead to hefty fines and damage to your business reputation. At Upper Echelon Technology Group, we understand the nuances of these regulations and ensure that our cyber security risk assessment process aligns with these requirements.
Compliance requirements play a crucial role in shaping your cybersecurity strategy. They provide the structure and guidance needed to ensure that your business is adequately protecting its assets. But remember, compliance is not a one-time event. It’s an ongoing process that requires regular reviews and updates, something we are more than equipped to help with.
Ready to strengthen your cybersecurity posture and ensure compliance? Let’s have a conversation.
Conclusion: The Ongoing Nature of Cyber Security Risk Assessment
We cannot stress enough that the cyber security risk assessment process is not a one-and-done task. It is a continuous, dynamic process that should evolve with your business, the ever-changing threat landscape, and regulatory requirements.
Continuous Monitoring is Key
As we’ve pointed out, risk assessments provide a snapshot of your organization’s risk and security posture at a given moment in time. However, changes in software vulnerabilities, attack methodologies, and regulatory compliance requirements can impact your risk posture at any time.
This is why continuous monitoring is essential. By proactively looking for new risks and promptly addressing them, your business can significantly mitigate risk and enhance its cybersecurity risk profile.
The Art and Science of Risk Management
Risk is more art than science. Over time, through continuous risk assessments, your organization will develop the skill to more easily identify, manage, and remediate risks. This includes understanding risk velocity (how quickly a risk can affect your organization), acknowledging open vulnerabilities, and classifying assets based on inherent risks.
Our Commitment to Your Security
At Upper Echelon Technology Group, we understand the complexities and challenges of conducting a thorough cyber security risk assessment. We’re here to help solve your technology issues, make your team more efficient, and enhance your company’s profitability by identifying areas where technology can improve your bottom line.
We believe in a proactive approach to cyber risk management. Our managed IT services are designed to provide ongoing monitoring and risk detection, helping you maintain a robust IT security posture and comply with relevant regulatory frameworks.
Conducting a cyber security risk assessment might seem daunting, but you don’t have to do it alone. Whether you’re concerned about network security, technology optimization, or leveraging technology to drive business growth, we’re here to help.
Remember, cybersecurity is not a destination but a journey. Let’s embark on this journey together, unlocking the hidden threats and turning your cybersecurity process into a game-changer for your business.