In today’s digital world, where technology is deeply integrated into the operations of nearly every business, the importance of assessing cybersecurity risk cannot be overstated. Cybersecurity risk assessments are an essential part of any organization’s risk management strategy. They are designed to help organizations understand, control, and mitigate all forms of cyber risk. With an increasing number of businesses falling prey to cyberattacks, a failure to carry out regular and meticulous cybersecurity risk assessments can lead to costly security incidents, data breaches, and compliance issues.
Here at Upper Echelon Technology Group, we understand that every business has unique needs and challenges. As a cybersecurity-focused managed services provider with offices in PA, DE, and FL, we offer a personalized approach to IT Managed Services. We don’t just solve tech issues; we focus on your business needs and help you leverage your technology assets in the most efficient way possible. Our goal is to make your company more profitable by identifying areas where technology can improve your bottom line.
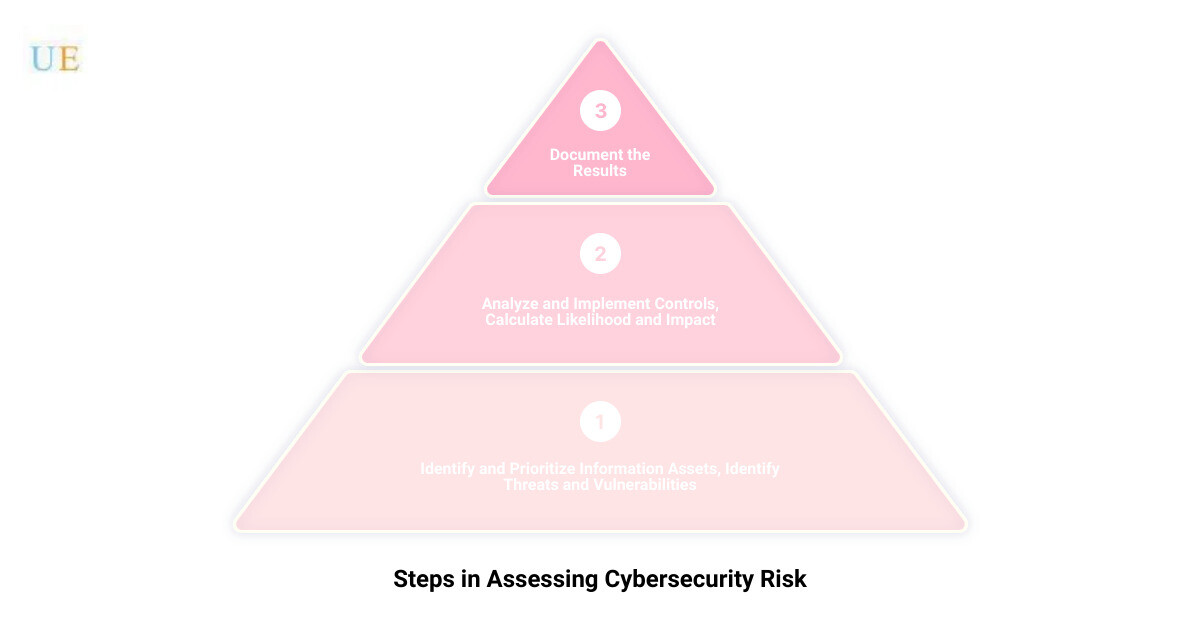
Key Elements of a Cybersecurity Risk Assessment:
- Identify and Prioritize Information Assets: Determine what data is most crucial to your business operations.
- Identify Threats and Vulnerabilities: Understand the potential risks that could compromise your data.
- Analyze and Implement Controls: Decide what measures should be put in place to protect your data.
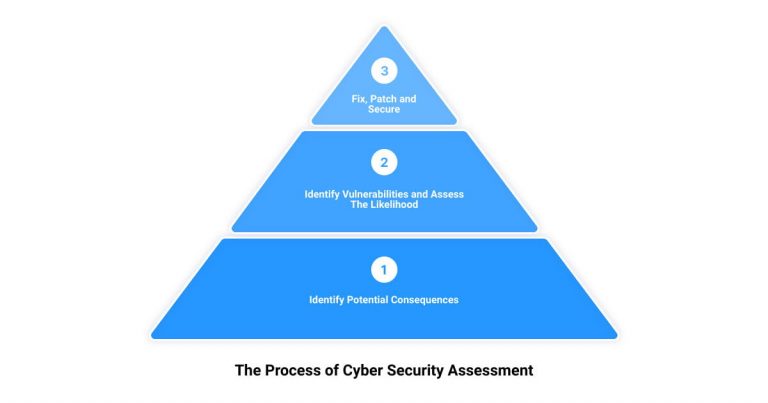
- Calculate Likelihood and Impact: Understand the potential consequences if a risk were to materialize.
- Document the Results: Keep a record of the findings for future reference and plan adjustments.
In the following sections, we’ll delve deeper into the importance of cybersecurity risk assessments, how to conduct them, the key stakeholders involved, and how to utilize frameworks for risk assessment. We’ll also explore the benefits of regular assessments, and how small businesses can implement cybersecurity risk assessments effectively. Stay with us as we unravel the hidden cybersecurity risks and help you crack the code to a safer and more secure digital environment.
Understanding Cybersecurity Risk Assessment
The key to an impenetrable digital fortress lies in understanding the cybersecurity risk assessment.
Definition and Purpose of Cybersecurity Risk Assessment
A cybersecurity risk assessment is your organization’s armor against potential cyber threats. To put it simply, it is an evaluation of your organization’s ability to protect its information and information systems from cyber threats .
The main goal of such an assessment is to identify, assess, and prioritize risks to your information and systems. It helps organizations like ours at Upper Echelon Technology Group to pinpoint areas for improvement in our cybersecurity program. Furthermore, it aids us in communicating these risks to stakeholders and making informed decisions about how to allocate resources to minimize these risks.
The Role of Cybersecurity Risk Assessment in an Organization
In a world where cyber threats are becoming increasingly sophisticated and frequent, a comprehensive cybersecurity risk assessment is no longer a luxury—it’s a necessity. This evaluation plays a critical role in the organization, enabling us to identify risks to our information, networks, and systems. By pinpointing these risks, we’re able to take steps to mitigate or reduce them, ultimately developing a plan to respond to and recover from potential cyber attacks .
At Upper Echelon Technology Group, we believe in the importance of conducting cybersecurity risk assessments on a regular basis to keep our risk profiles up to date. Additionally, any changes to our computer networks or systems warrant a new risk assessment to ensure we’re always prepared and protected.
In the next section, we’ll delve deeper into the process of conducting a cybersecurity risk assessment, exploring everything from identifying and prioritizing information assets to analyzing and implementing controls. So, stick around as we continue to crack the code on unveiling hidden cybersecurity risks.
The Process of Conducting a Cybersecurity Risk Assessment
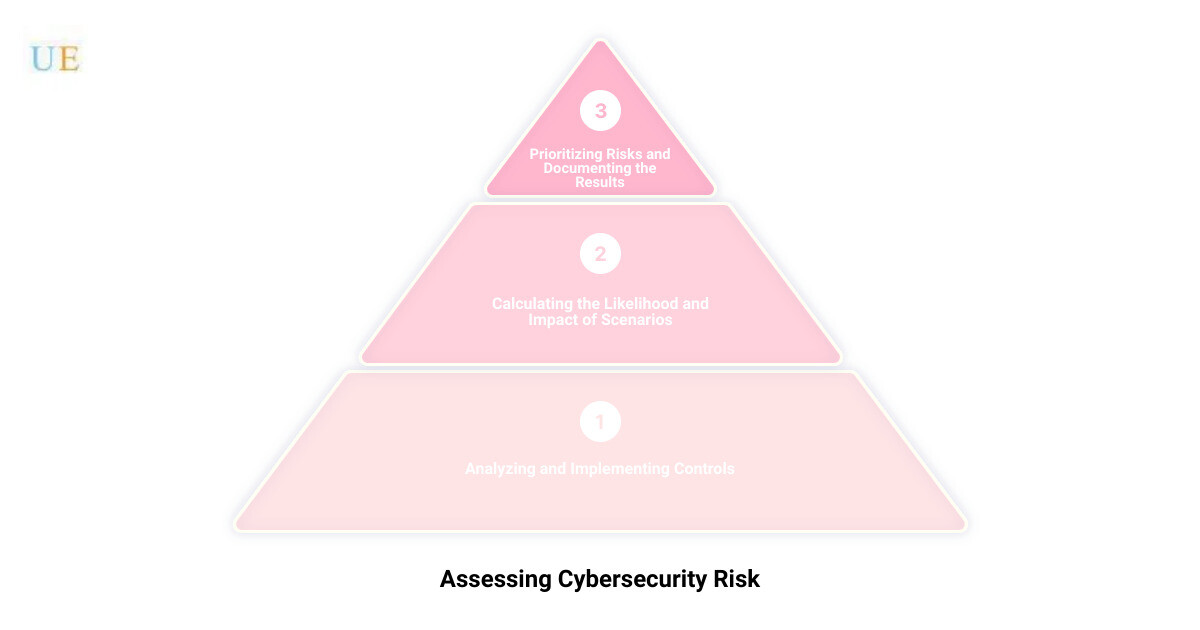
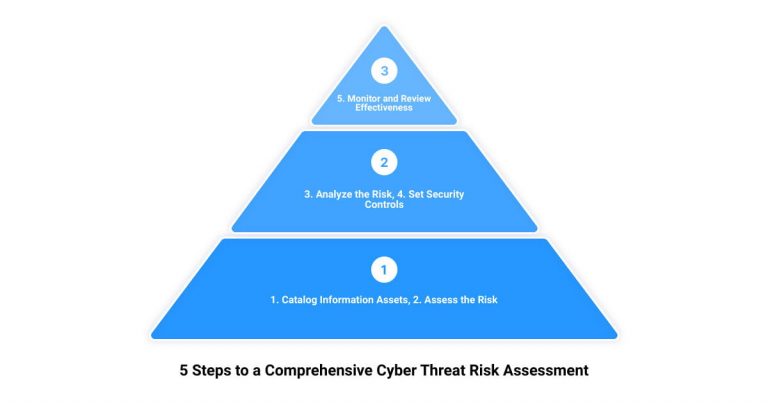
Unveiling hidden cybersecurity risks can often feel like deciphering a complex code, yet with the right expertise and processes, it becomes a manageable task. At Upper Echelon Technology Group, we follow a comprehensive and methodical approach to conducting a cybersecurity risk assessment. Our process is divided into five crucial steps: Identifying and Prioritizing Information Assets, Identifying Cyber Threats and Vulnerabilities, Analyzing and Implementing Controls, Calculating the Likelihood and Impact of Scenarios, and Prioritizing Risks and Documenting the Results.
Identifying and Prioritizing Information Assets
The first step in our process involves identifying and prioritizing all the physical and logical assets within the scope of the risk assessment. It’s a crucial step, because as the old saying goes, “You can’t protect what you don’t know”. We create an inventory of these assets, not only establishing the crown jewels of the organization, but also assets that attackers would want to control. A network architecture diagram is then created, which serves as a visual representation of the interconnectivity between assets and processes, making the identification of threats easier.
Identifying Cyber Threats and Vulnerabilities
Next, we identify threats and vulnerabilities. Threats are the tactics, techniques, and methods used by threat actors that have the potential to cause harm to an organization’s assets. To help identify these, we use resources like the MITRE ATT&CK Knowledge Base and the Cyber Threat Alliance. We also keep an eye on reports and advisories from security vendors and government agencies such as the Cybersecurity & Infrastructure Security Agency. Understanding where each asset sits in the Lockheed Martin cyber kill chain helps us determine the types of protection they need.
Analyzing and Implementing Controls
The third step involves analyzing the identified risks and implementing appropriate controls. This often involves specifying the consequences of a threat exploiting a vulnerability to attack an in-scope asset. It helps in understanding the risk scenarios in relation to business objectives and allows us to identify the best practices and measures to mitigate these risks.
Calculating the Likelihood and Impact of Scenarios
Next, we calculate the likelihood and impact of the identified scenarios. This involves weighing the potential damage caused by a successful attack against the probability of such an attack occurring. This helps us to better understand the potential risks and plan accordingly.
Prioritizing Risks and Documenting the Results
Finally, we prioritize risks based on their potential impact and the likelihood of occurrence. This helps in deciding where to focus resources for mitigation. The results of the risk assessment are then documented, providing a clear overview of the cybersecurity risk environment and the implemented controls.
In a nutshell, conducting a cybersecurity risk assessment is a continuous, structured process that helps in identifying, understanding, and managing cybersecurity risks. At Upper Echelon Technology Group, we ensure that this process is tailored to meet the specific needs of your organization, helping you crack the code and unveil hidden cybersecurity risks.
Key Stakeholders in Cybersecurity Risk Assessment
In the world of cybersecurity, it’s a team sport and every player is crucial. The assessment and management of cybersecurity risks require the involvement of various stakeholders, each of whom play a critical role in ensuring the security of an organization’s information assets.
Involvement of IT Personnel, Management, and Legal Teams
A well-rounded cybersecurity risk assessment starts with knowledgeable IT personnel. Armed with technical expertise, they understand the ins and outs of the organization’s IT infrastructure and can effectively identify potential vulnerabilities and threats. Our expert at Upper Echelon Technology Group, expert’s name, emphasizes the importance of involving IT personnel in the process, stating that their technical insights are invaluable in creating a robust cybersecurity risk profile.
Management teams, on the other hand, bring a broader business perspective to the assessment. They help in prioritizing assets based on their importance to the organization’s goals and objectives. Furthermore, they are vital in aligning the cybersecurity risk management strategy with the overall business strategy.
Legal teams play a pivotal role in navigating the complex landscape of data privacy laws and regulations, such as HIPAA, Sarbanes-Oxley, and PCI DSS. They ensure that the organization’s cybersecurity practices align with these laws and regulations, thus minimizing legal and compliance risks.
The Role of Third-Party Vendors and Partners in Cybersecurity Risk
In today’s interconnected world, cybersecurity risk extends beyond an organization’s own IT infrastructure to include third-party vendors and partners. Vendors and partners often have access to an organization’s data and systems, making them potential weak links in the cybersecurity chain.
At Upper Echelon Technology Group, we understand the importance of assessing the cybersecurity risk posed by third-party vendors and partners. We ensure that they adhere to the same high standards of cybersecurity that we do, thus maintaining a strong and secure network of operations.
Moreover, we believe in the power of collaboration and mutual learning in addressing cybersecurity risks. By working closely with our vendors and partners, we aim to build a cybersecurity ecosystem that is resilient, adaptable, and capable of responding to evolving threats.
In conclusion, conducting a comprehensive cybersecurity risk assessment is a team effort. It requires the active involvement of IT personnel, management, and legal teams within the organization, as well as third-party vendors and partners. At Upper Echelon Technology Group, we are committed to fostering collaboration among all stakeholders in order to build a secure and resilient cybersecurity environment.
Utilizing Frameworks for Cybersecurity Risk Assessment
The path to cyber resilience is not a solitary trek but a guided journey. At Upper Echelon Technology Group, we know that having a map makes the journey easier. In the realm of cybersecurity, this map comes in the form of established frameworks that provide a systematic approach to managing cybersecurity risks. Two of the most recognized frameworks in the industry are the NIST Cybersecurity Framework and the ISO 27001:2013 Standard.
Overview of the NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a voluntary guideline that organizations can adopt to manage and mitigate cybersecurity risk. It provides a common language and systematic approach for managing cybersecurity risk in a cost-effective way based on business needs.
This framework isn’t just a checklist of compliance requirements. It’s a dynamic tool that helps organizations align their cybersecurity activities with their business requirements, risk tolerances, and resources. Its flexible and risk-based implementation can help you identify, assess, and manage cybersecurity risk across your organization, reducing the likelihood of a successful cyber attack and minimizing the impact of a breach should one occur.
Understanding the ISO 27001:2013 Standard
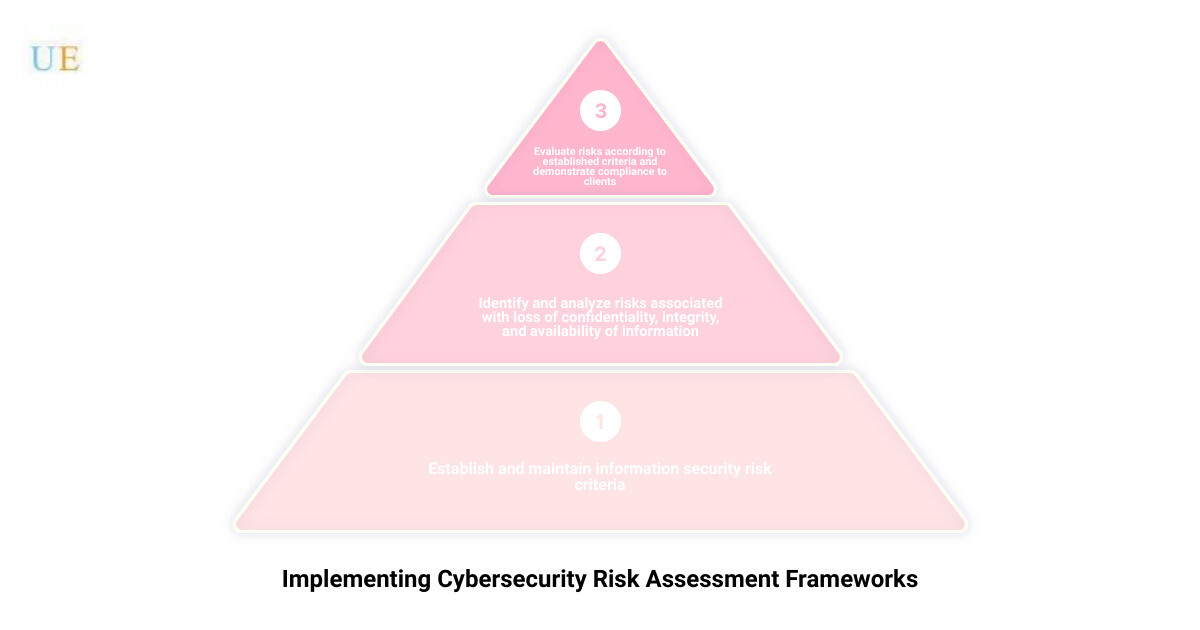
Another crucial tool in your cybersecurity toolkit is the ISO 27001:2013 Standard. This international standard provides specifications for a best-practice Information Security Management System (ISMS) – a risk-based approach to corporate information security risk management that addresses people, processes, and technology.
ISO 27001 sets out the requirements of the information security risk assessment process, ensuring that organizations establish and maintain certain information security risk criteria, identify risks associated with the loss of confidentiality, integrity, and availability of information, and analyze and evaluate these risks according to established criteria.
As our expert at Upper Echelon Technology Group, [Expert’s name], often says, “The ISO 27001 standard not only helps us identify and manage risks but also allows us to demonstrate our compliance with these criteria, providing additional assurance to our clients.”
So, whether you’re navigating the complex landscape of cybersecurity risk assessment on your own, or seeking expert guidance, these frameworks provide a solid foundation. It’s like having a GPS in the world of cybersecurity. And at Upper Echelon Technology Group, we’re here to be your trusted co-pilot, using these frameworks to guide you towards a safer, more secure digital environment.
Infographic illustrating the NIST Cybersecurity Framework and the ISO 27001:2013 Standard and how they are implemented in cybersecurity risk assessment.
The Benefits of Regular Cybersecurity Risk Assessment
In the ever-evolving digital landscape, regular cybersecurity risk assessment is not a luxury but a necessity. As the cybersecurity experts at Upper Echelon Technology Group often emphasize, staying ahead of cyber threats requires a proactive strategy that includes regularly updating threat profiles, quickly responding to changes in computer networks or systems, and identifying vulnerabilities to mitigate risks, thus reducing long-term costs and avoiding data breaches.
Keeping Risk Profiles Up to Date
Our digital world doesn’t stand still, and neither do cyber threats. To stay one step ahead, we at Upper Echelon Technology Group recommend regular updates to your risk profiles. This process involves identifying changes in your IT environment, updating your inventory of information assets, and adjusting your risk assessment based on the new threat landscape. By keeping your risk profiles up-to-date, you ensure a more accurate and effective cybersecurity strategy.
“Regular updates to your risk profile helps in identifying new vulnerabilities and threats before they become a major issue for your organization.” – Reddit user
Responding to Changes in Computer Networks or Systems
Technological advancements bring with them new vulnerabilities. Changes in computer networks, systems, software, or hardware can inadvertently create new openings for cyber threats. Regular cybersecurity risk assessments ensure that you’re aware of these changes and can implement adequate measures to secure your digital landscape.
As one Quora user aptly put it, “The cybersecurity landscape is constantly changing. What was secure yesterday may not be secure today.”
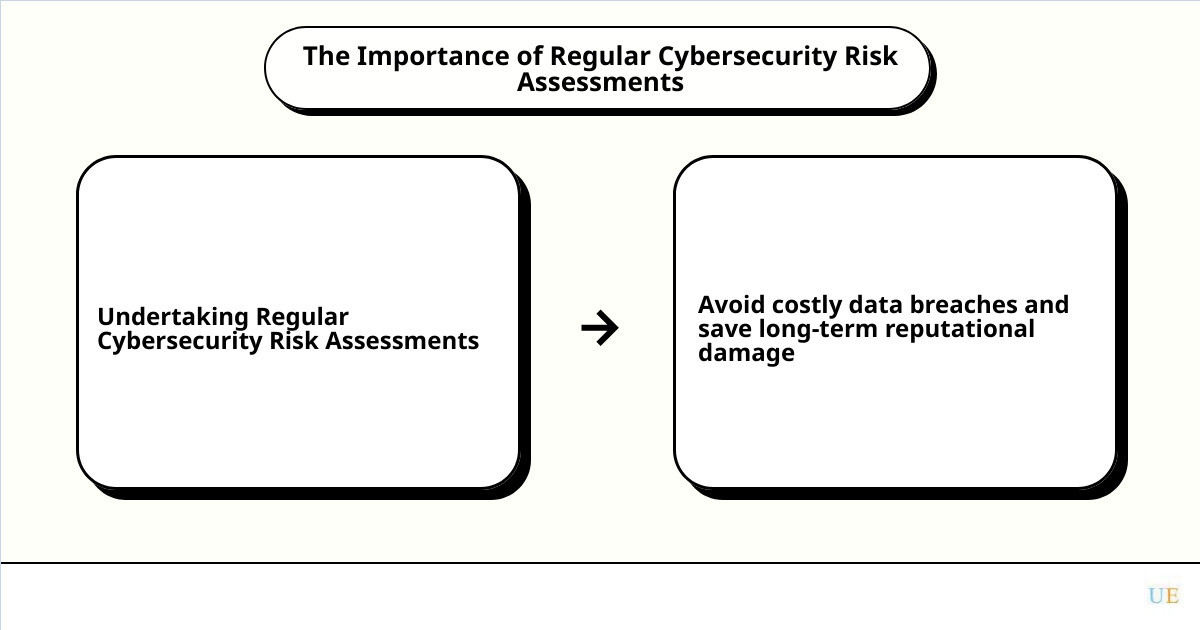
Reducing Long-Term Costs and Avoiding Data Breaches
Infographic illustrating how regular cybersecurity risk assessments can lead to cost savings and prevention of data breaches.
According to a report by IBM, the average cost of a data breach in 2020 was $3.86 million. Undertaking regular cybersecurity risk assessments can help avoid such costly incidents. By identifying potential threats and vulnerabilities, and then mitigating them, your organization not only saves on the immediate costs of a data breach but also on the long-term reputational damage.
“Prevention is always better than cure, especially when it comes to cybersecurity. Regular risk assessments can save your company millions in the long run.” – Reddit user
At Upper Echelon Technology Group, we understand that cybersecurity is a journey, not a destination. Regular assessments are a crucial part of this journey, enabling you to stay ahead of potential threats and ensure that your business remains resilient in the face of evolving cyber risks.
Implementing Cybersecurity Risk Assessment in Small Businesses
The old saying “prevention is better than cure” rings especially true when it comes to cybersecurity. By implementing a robust risk assessment process, small businesses can stay a step ahead of cyber threats. However, the challenge lies in the execution. Small businesses often lack the resources and expertise needed for a comprehensive cybersecurity risk assessment. But fear not, at Upper Echelon Technology Group, we are here to guide you through this complex process.
The Need for Dedicated In-House Teams or Outsourcing
The process of assessing cybersecurity risk requires a deep understanding of an organization’s IT infrastructure, the flow of information, and potential vulnerabilities. This task is best done by dedicated in-house teams who have a comprehensive understanding of the company’s system architecture. However, many small businesses may lack the necessary personnel or expertise to carry out a thorough assessment.
In such cases, outsourcing the cybersecurity risk assessment to experts like us at Upper Echelon Technology Group can be a cost-effective and efficient solution. We have a personalized approach to IT Managed Services and focus on your specific business needs. Our team of experts understands the unique cybersecurity challenges that small businesses face and can help you identify and mitigate potential threats.
The Use of Cybersecurity Software and Tools
In addition to having a dedicated team, leveraging the right tools and software is critical in conducting an effective cybersecurity risk assessment. These tools can automate the assessment process, making it more efficient and less prone to human error. They can also provide real-time monitoring and alerts, helping businesses to respond quickly to potential cyber threats.
At Upper Echelon Technology Group, we not only use the latest cybersecurity tools and software but also keep evaluating their effectiveness to ensure your network is protected and optimized 24x7x365. We believe that technology should serve your business and not the other way round.
Implementing a cybersecurity risk assessment may seem daunting, but the benefits greatly outweigh the initial effort. It can save your organization from costly security incidents, potential regulatory issues, and reputational damage. Remember, in the world of cybersecurity, it’s always better to be proactive than reactive. Trust us at Upper Echelon Technology Group to guide you through this process and help you build a resilient and secure IT infrastructure.
Conclusion: The Proactive Approach to Cybersecurity Risk Assessment
In the dynamic landscape of cybersecurity, a reactive mindset can be costly and devastating. The key to successfully navigating this landscape lies in being proactive – identifying and addressing risks before they materialize into full-blown threats. A comprehensive cybersecurity risk assessment, as we’ve discussed, is a critical tool in this proactive approach. It’s not just about ticking a compliance checkbox; it’s about safeguarding the lifeblood of your business – your data and systems.
At Upper Echelon Technology Group, we understand the importance of proactively managing cybersecurity risks. We’ve seen firsthand how a well-conducted risk assessment can serve as a roadmap, guiding businesses towards a stronger, more secure future. As Abi Tyas Tunggal points out, “Cybersecurity risk assessments help organizations understand, control, and mitigate all forms of cyber risk. They are a critical component of risk management strategy and data protection efforts.”
We strive to embody the principles of proactive cybersecurity risk management in all our services. From solving your technology issues to leveraging technology to improve your bottom line, our personalized approach to IT managed services always places emphasis on proactive risk management.
Upper Echelon Technology Group is more than just a service provider; we’re your strategic partner in navigating the complex world of cybersecurity. Our core values, such as relentless pursuit of personal growth, open and honest communication, and doing the right thing even when no one is looking, reflect our commitment to providing top-tier cybersecurity solutions.
As a business owner, you don’t have to face cyber threats alone. Partner with us, and let’s work together to crack the code of cybersecurity risk assessment. With our expertise and a proactive approach, we can help unveil hidden cybersecurity risks and protect your business from potential threats.
Remember, a secure business is a successful business. So, don’t wait for a cyber attack to happen before taking action. Start assessing your cybersecurity risks today, and take the first step towards a safer, more secure business future.
Don’t just be prepared for cyber threats, stay one step ahead. As the old saying goes, “The best defense is a good offense.” In the world of cybersecurity, a comprehensive, proactive risk assessment is your best offense.
The end of the journey of cracking the code of unveiling hidden cybersecurity risks, remember the journey of cybersecurity is a continuous process.