Unveiling the invisible armor that protects the digital realm of your business begins with understanding the concept of a cyber attack risk assessment. As a small to medium-sized business owner in Wilmington, DE, you’re undoubtedly aware that having a robust cybersecurity strategy is no longer optional. However, the foundation of any effective cybersecurity strategy is an in-depth cyber attack risk assessment.
A cyber attack risk assessment is a systematic approach to identifying, understanding, and managing the various cyber risks that your business faces. It’s like a health check for your business’s digital environment, identifying potential vulnerabilities and threats, and determining how these could impact your business operations and profitability.
This process involves identifying your information assets, such as data, applications, and hardware, and then assessing their value and vulnerability to various cyber threats. It goes beyond merely fixing technical issues, focusing instead on how to leverage your technology assets effectively to safeguard your business. As highlighted by the National Institute of Standards and Technology (NIST), this process involves several steps, including identifying network vulnerabilities, utilizing cyber threat intelligence, and prioritizing risk responses.
In this guide, we’ll delve deeper into the importance of a cyber attack risk assessment, the steps involved, and how companies like the Upper Echelon Technology Group LLC can help you navigate this crucial process. By understanding and implementing a thorough cyber attack risk assessment, you’ll be taking a significant step towards ensuring your business’s digital security and enhancing its overall efficiency and profitability.
The Importance of Cyber Attack Risk Assessment
In the digital age, the threat of cyber attacks has become a grim reality for businesses of all sizes. From startups to multinational corporations, no entity is immune to the potential havoc that cyber threats can wreak. This is precisely why conducting a regular and comprehensive cyber attack risk assessment is non-negotiable. Let’s dive deeper into why these assessments are so crucial.
Protecting Sensitive Data and Business Operations
At the heart of any business are its valuable assets: sensitive data and integral business operations. These can range from client and employee information to proprietary research and development data. A cyber attack risk assessment helps identify the vulnerabilities that could lead to a security breach, enabling your organization to implement effective security measures. This proactive approach helps safeguard the critical information and business operations that keep your company running seamlessly.
Ensuring Regulatory Compliance and Improving Insurance Coverage
In many industries, regulatory compliance dictates the need for stringent cybersecurity measures. Non-compliance can result in hefty fines and damage to your company’s reputation. Regular cyber attack risk assessments can ensure your organization’s cybersecurity measures meet the required standards. Furthermore, companies that can demonstrate a strong commitment to cybersecurity may also benefit from improved insurance coverage. Many insurers now require evidence of risk management strategies, such as regular risk assessments, before offering or renewing cybersecurity insurance policies.
Demonstrating Cybersecurity ROI
Investing in cybersecurity measures is no longer a luxury; it’s a necessity. However, business stakeholders often require proof of return on investment (ROI). A comprehensive cyber attack risk assessment can provide tangible evidence of the potential cost savings associated with preventing cyber attacks. By identifying and mitigating risks, you’re avoiding potential losses associated with data breaches, regulatory fines, and reputational damage.
In essence, cyber attack risk assessments are not just about identifying and mitigating the risks. They also serve as a tool to protect your business operations, ensure regulatory compliance, and demonstrate the ROI of your cybersecurity strategy. Companies like Upper Echelon Technology Group LLC offer personalized IT managed services that can assist you in conducting these assessments and implementing a robust and effective cybersecurity strategy.
The Process of Performing a Cyber Attack Risk Assessment
Don’t let cyber threats ambush your business. Understand your battlefield by undertaking a structured cyber attack risk assessment process. This exercise will help you identify your critical assets, detect potential threats, and implement effective controls to mitigate risks.
Determining the Informational Value of Assets
Your first move in this chess game of cybersecurity is to determine the informational value of your assets. Not all data bears the same value. Some datasets could have dire financial or legal implications if exposed or lost. Therefore, spend time defining a standard for determining the importance of an asset in terms of asset value, legal standing, and business importance.
Identifying and Prioritizing Assets
Next, identify and create an inventory of all physical and logical assets within the scope of the risk assessment. This can range from an Active Directory server to a web application. Once identified, prioritize these assets based on their value and the organization’s risk tolerance levels. Remember, not all assets have the same value and not all threats have the same impact.
Identifying Cyber Threats
In the world of cybersecurity, knowledge is power. Equip yourself with the latest cyber threat information by referring to resources like the MITRE ATT&CK Knowledge Base or vendor reports and advisories from government agencies. Identifying potential threats to your assets helps you anticipate and prepare for potential attacks.
Identifying Vulnerabilities
Cyber threats exploit vulnerabilities. Identifying these weaknesses in your systems, processes, or personnel enables you to devise strategies to counteract threats.
Analyzing and Implementing Controls
After identifying threats and vulnerabilities, it’s time to devise and implement controls to mitigate these risks. This could involve updating software, improving personnel training, or enhancing physical security.
Calculating the Likelihood and Impact of Various Scenarios
This stage involves estimating the probability and potential impact of each identified risk. This can help you understand the potential consequences of a cyber attack and guide your mitigation strategies.
Prioritizing Risks
Once you have a comprehensive list of potential risks, it’s time to prioritize them based on their likelihood and potential impact. This will guide your response plan and resource allocation, ensuring that the most dangerous threats are dealt with first.
Documenting the Results in a Risk Assessment Report
The last step in the risk assessment process is to document your findings in a risk assessment report. This document should include all identified assets, vulnerabilities, threats, and controls, as well as your risk prioritization. This report serves as a roadmap for your cybersecurity strategy and a reference for future assessments.
By conducting a thorough cyber attack risk assessment, you can ensure that your organization is prepared to face the ever-evolving landscape of cyber threats. With the personalized IT services offered by Upper Echelon Technology Group LLC, you can leverage your technology assets in the best way possible to protect your business.
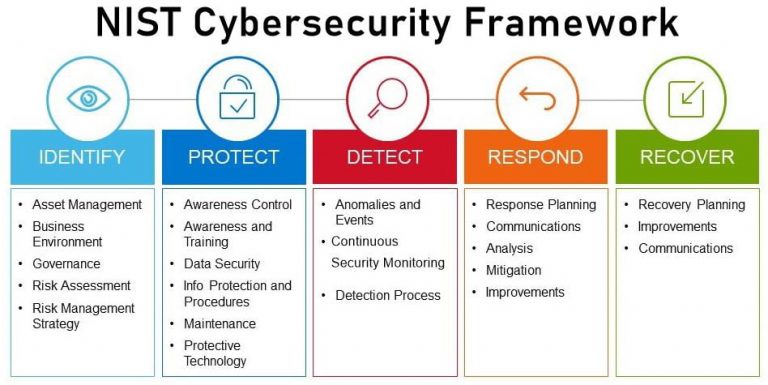
The Role of NIST in Cyber Attack Risk Assessment
In the fight against cyber threats, the National Institute of Standards and Technology (NIST) serves as a lighthouse, guiding businesses with a structured approach to assessing their cybersecurity risks. Let’s delve into the six key steps outlined by NIST to perform a comprehensive cyber attack risk assessment.
Identifying and Documenting Network Asset Vulnerabilities
The first step towards a fortified business is to identify and document potential vulnerabilities within your IT assets. This could involve creating an inventory of your physical and logical assets, including not just the crown jewels of your business, but also assets that could serve as gateways for attackers to expand their attack.
Using Sources of Cyber Threat Intelligence
With your assets identified, it’s time to gather intelligence. Cyber Threat Intelligence feeds provide invaluable insights into potential threats. They can be sourced from various organizations such as CISA, US-CERT, and even cybersecurity companies. Leveraging these resources can provide you with the necessary understanding of major potential threats.
Identifying Internal and External Threats
Armed with cyber threat intelligence, you can now scan your systems for indicators of compromise, audit configuration files for insecure settings, and look for unusual behavior in log files. Remember, threats can come from both outside and within your organization.
Identifying Potential Mission Impacts
It’s crucial to understand that different cyber threats can have varying impacts on your business. For instance, a ransomware attack on a single user’s workstation may not be as devastating as one on your corporate database. Analyzing the potential mission impacts helps quantify the risk posed by each threat.
Determining Risk Based on Threats and Vulnerabilities
By combining the likelihood and impact of each potential threat, you can quantify your organization’s overall risk. This involves collating all the data you’ve gathered – from the list of IT assets and their potential vulnerabilities, to the current threat landscape informed by cyber threat intelligence.
Prioritizing Risk Responses
Finally, with a quantified understanding of the risks your organization faces, you can prioritize your risk responses. This ensures that major risks are addressed as quickly as possible, helping you maximize the return on investment of your remediation efforts.
Remember, a cyber attack risk assessment is not a one-off activity but requires regular reviews and updates. It’s a continuous process to keep up with the rapidly changing cyber threat landscape. And as you navigate through this process, the expertise and personalized approach of a cybersecurity-focused managed services provider like Upper Echelon Technology Group LLC can be invaluable.
The Five Main Steps of a Cybersecurity Risk Assessment
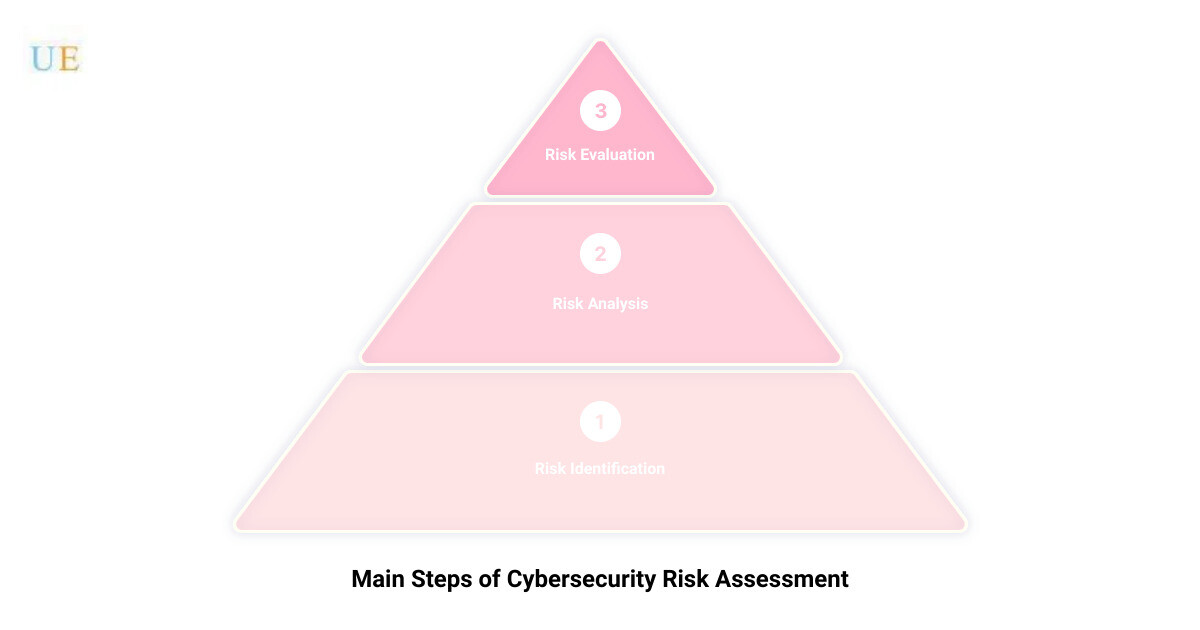
A cybersecurity risk assessment is not a simple one-size-fits-all approach; it’s a meticulously curated process that takes into account the nature of your business, your specific assets, and the unique threats you face. At its core, it involves five key steps: Scoping, Risk Identification, Risk Analysis, Risk Evaluation, and Documentation.
Scoping
The initial step, Scoping, involves defining the boundaries of the risk assessment. It requires you to ascertain your key business objectives and identify the IT assets that are crucial to achieving those targets. It’s like mapping out the battlefield before the war, where you need to understand the terrain, the key strategic points, and the potential areas of vulnerability.
Risk Identification
Once you have a clear picture of your playing field, the next step is Risk Identification. This stage involves determining the cyber threats that could negatively impact your defined assets. It’s a comprehensive scan of your cyber environment to identify potential threats and vulnerabilities that could be exploited by cybercriminals. Remember, the more you know about your enemies and their strategies, the better you can defend against them.
Risk Analysis
Following identification, we delve deeper with Risk Analysis. This step requires evaluating the likelihood of identified threats occurring and the potential impact they could have on your organization. It’s akin to analyzing the strength of your opponent’s army and the potential damage they could inflict. This stage builds a complete picture of the potential threat landscape for your specific business objectives, helping inform your defensive strategy.
Risk Evaluation
Next is Risk Evaluation. This is where you decide on the level of risk you’re willing to accept and determine the most effective and efficient way to manage the risks exceeding that threshold. It’s deciding what risks to avoid, accept, mitigate, or transfer based on their potential impact on your business operations.
Documentation
Finally, we reach Documentation. This is where the findings and decisions from the previous steps are recorded. It’s a critical step as it not only provides a roadmap for implementing security controls but also serves as a reference for future assessments. This documentation helps create a more risk-aware culture within your organization, ensuring everyone understands the cyber risks and the steps taken to manage them.
In conclusion, conducting a cybersecurity risk assessment is a meticulous but necessary process. It helps prevent costly security incidents and regulatory compliance issues, safeguarding your business’s reputation and bottom line. And who better to guide you through this process than a cybersecurity-focused managed services provider like Upper Echelon Technology Group LLC that understands your unique needs and provides personalized IT solutions?
How Upper Echelon Technology Group LLC Can Help with Cyber Attack Risk Assessment
In the digital age, protecting your business from cyber threats is paramount. But tackling this challenge is not a one-size-fits-all approach. Each business has unique needs and risks, and that’s where Upper Echelon Technology Group LLC comes in.
Personalized IT Managed Services
Upper Echelon Technology Group LLC stands out in the crowd of IT service providers with their personalized approach to IT Managed Services. This means they don’t just fix tech issues; they focus on your business needs and how you can leverage your technology assets in the best way possible to help your business. When it comes to cyber attack risk assessment, they ensure that your network is protected and optimized 24/7/365, so your technology serves your business instead of you serving your technology.
Their cybersecurity-focused managed services are designed to solve your technology issues so you can focus on your business. They make your team more efficient by leveraging technology and identifying areas where technology can improve your bottom line. This personalized approach ensures that the cyber attack risk assessment is tailored to your business, its needs, and its vulnerabilities.
Tailored Approach to Meet Specific Business Needs
The team at Upper Echelon Technology Group LLC understands that every business is unique, which is why they offer a tailored approach to cybersecurity. They realize that what works for one business may not work for another, and they take the time to understand your specific needs, risks, and technology assets before designing a risk assessment strategy.
They help you identify and prioritize your assets, identify cyber threats, uncover vulnerabilities, analyze and implement controls, calculate the likelihood and impact of various scenarios, and prioritize risks. The result is a comprehensive risk assessment report, documenting all findings and recommendations, helping you make informed decisions about your cybersecurity strategy.
In conclusion, the team at Upper Echelon Technology Group LLC goes beyond providing managed IT services. They become your trusted partner in securing your business from cyber threats, offering personalized and tailored services that address your unique needs and risks. So, if you’re looking for a cybersecurity-focused managed services provider that can help with your cyber attack risk assessment, look no further than Upper Echelon Technology Group LLC. They’re committed to helping you protect your business, make your team more efficient, and improve your bottom line.
Conclusion: The Necessity of Regular Cyber Attack Risk Assessments
In the rapidly evolving digital world, the significance of regular cyber attack risk assessments cannot be overstated. As a Wilmington-based business owner, you already know that cybersecurity is not a one-and-done task. It’s a continuous process that requires constant vigilance, regular updates, and proactive measures to stay ahead of potential threats.
By conducting regular cyber risk assessments, you’re not only safeguarding your data and business operations but also ensuring regulatory compliance, improving your insurance coverage, and demonstrating a clear cybersecurity return on investment (ROI). This process helps you identify your most valuable assets, prioritize threats, and calculate the likelihood and impact of various scenarios.
Remember, cyber risk = threat x vulnerability x information value. So, whether it’s a known backdoor in a software version or a potential phishing attempt, understanding your risk landscape is crucial to mitigating threats and reducing vulnerabilities.
The National Institute of Standards and Technology (NIST) provides a robust framework for risk assessment practices. However, while this framework is a valuable starting point, tailoring it to your specific needs is where the real benefit lies. And that’s where a personalized approach to IT Managed Services can make all the difference.
At Upper Echelon Technology Group LLC, we understand that every business is unique and so are its cybersecurity needs. That’s why we don’t just focus on tech issues. We go beyond that, focusing on your business needs and how you can leverage your technology assets to improve your bottom line.
In conclusion, regular cyber attack risk assessments are not just a necessity but a strategic business move. It’s about understanding your business’s digital landscape, unmasking hidden vulnerabilities, and unveiling the true potential of your technology assets. So, whether you’re just starting out in the cybersecurity journey or looking to enhance your existing strategies, remember that the right technology partner can make all the difference.
The digital world waits for no one. It’s time to take control of your cybersecurity and protect your business with professional, personalized IT Managed Services.