Introduction: The Importance of Vulnerability Assessment in Cyber Security
In the modern digital landscape where businesses are increasingly dependent on technology, cyber threats pose a significant risk. To stay ahead of the curve, businesses must be proactive in identifying and addressing potential vulnerabilities in their IT infrastructure. This is where vulnerability assessment in cyber security comes into play.
As a small to medium-sized business owner in Wilmington, DE, you may be seeking a cybersecurity-focused managed services provider that can effectively safeguard your IT systems. But how do they do it? The answer lies in the art of vulnerability assessment. Unmasking cyber threats is akin to uncovering hidden vulnerabilities that could potentially expose your business to risk.
This process is not just about identifying weaknesses. It also involves prioritizing these vulnerabilities based on the level of threat they pose, and creating a plan to remediate them. A thorough vulnerability assessment can help your business prevent data breaches, ensure compliance with industry regulations, and enhance overall network security.
In the following sections, we will delve deeper into what vulnerability assessment entails, its critical role in cyber security, and how a company like Upper Echelon Technology Group LLC uses it to protect your business. Stay tuned as we unveil the art of uncovering hidden vulnerabilities.
Understanding Vulnerability Assessment: Definitions and Key Concepts
What is Vulnerability Assessment?
If you’ve ever wondered what makes your business’s IT infrastructure susceptible to cyber threats, then vulnerability assessment is the answer you’re looking for. In the realm of cybersecurity, vulnerability assessment refers to the process of identifying, quantifying, and prioritizing vulnerabilities in a system. It entails a comprehensive analysis of your IT ecosystem, which includes computer networks, systems, hardware, and applications, to spot potential security weaknesses. This information is crucial as it allows security teams to make informed decisions on risk remediation, ensuring that your business’s sensitive data is protected from unauthorized access and breaches.
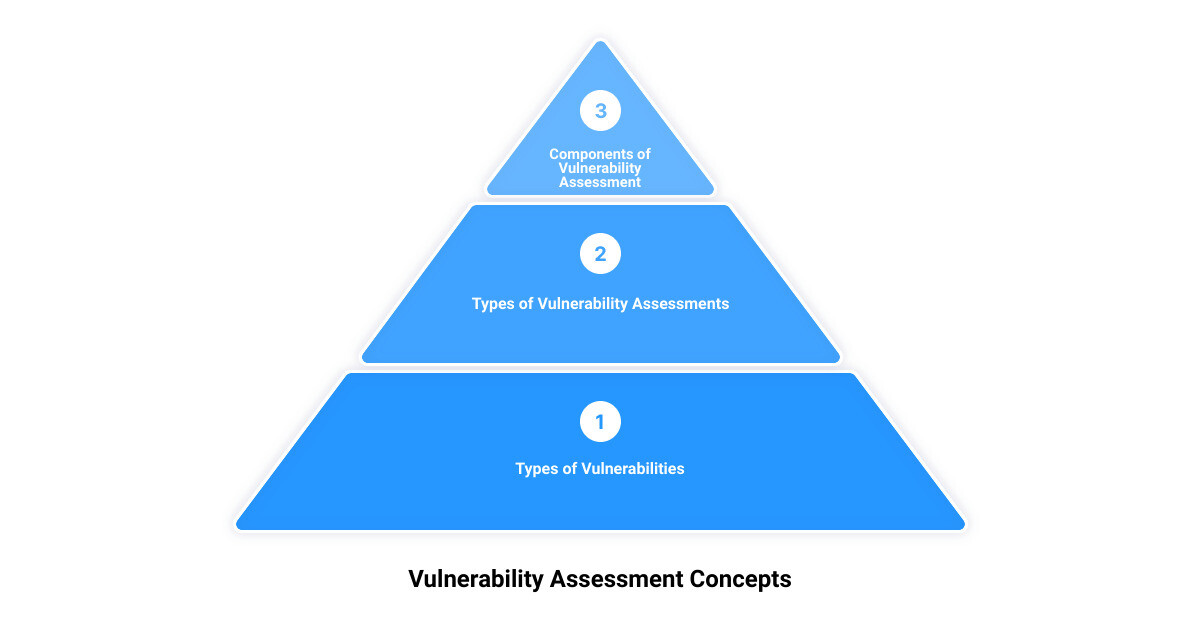
The Four Main Types of Vulnerabilities in Cyber Security
When we talk about vulnerabilities, it’s important to understand that they can exist in various forms in your IT landscape. The four main types that you need to be aware of are: network vulnerabilities, operating system vulnerabilities, process vulnerabilities, and human vulnerabilities.
Network vulnerabilities can exist in your IT infrastructure, making your systems susceptible to attacks. Operating system vulnerabilities are flaws or weaknesses in the system software that runs your computers. Process vulnerabilities refer to security loopholes in your operational or procedural guidelines. Finally, human vulnerabilities, arguably the most difficult to control, stem from human error or lack of awareness about secure practices.
The Five Types of Vulnerability Assessment
Now that we know what we’re looking for, let’s discuss the different types of vulnerability assessments that can be conducted to pinpoint these vulnerabilities. The five key types include: Network-Based, Application-Based, API-Based, Host-Based, and Wireless Network Vulnerability Assessment. In addition to these, physical vulnerability assessments can also be conducted to identify physical security gaps. Each of these types focuses on a specific aspect of your IT ecosystem, providing a comprehensive overview of potential security gaps.
The Three Components of Vulnerability Assessment
Lastly, it’s crucial to understand the three fundamental components of vulnerability assessment: exposure, sensitivity, and adaptive capacity. Exposure refers to the extent to which your system is open to potential threats. Sensitivity is the degree to which your system can be affected by a threat, and adaptive capacity is your system’s ability to adjust to potential threats, thereby reducing potential harm. Together, these components provide a holistic picture of your system’s vulnerability, guiding you towards the best remediation strategies.
By understanding these definitions and key concepts, you are already taking significant strides towards improving your business’s cybersecurity. Stay with us as we explore in more detail the role of vulnerability assessment in cyber security and how it can help secure your business.
The Role of Vulnerability Assessment in Cyber Security
In the ever-evolving landscape of cyber threats, understanding the role and importance of vulnerability assessment is paramount. It’s like having a dedicated security guard who constantly patrols your digital premises, identifying weak spots and reinforcing them before they can be exploited.
Why Vulnerability Assessment is Crucial in Cyber Security
In the world of cyber security, the best defense is a good offense. Vulnerability assessment is the offensive approach towards ensuring network security. It not only uncovers security weaknesses in your environment but also provides direction on how to assess the risks associated with these vulnerabilities. This proactive approach allows you to prevent potential breaches, rather than react to them after the fact.
By identifying risks and vulnerabilities in your IT ecosystem, vulnerability assessments give you the upper hand in the cyber warfare. With this knowledge, you can prioritize risks for potential remediation, thereby strengthening your defenses.
How Vulnerability Assessment Helps in Confirming the Adequacy of Security Measures
Effective cyber security is not just about implementing security measures—it’s also about continually verifying their adequacy and effectiveness. A comprehensive vulnerability assessment ensures that your security measures are not just present, but robust and effective.
Vulnerability assessment tools, such as network security scanners, identify threats and flaws within an organization’s IT infrastructure that represent potential risk exposures. By assessing the severity of these threats, vulnerability assessment helps confirm the adequacy of your security measures and identify areas that require improvement.
The Threats Prevented by Vulnerability Assessment
The threats that vulnerability assessment can help prevent are vast and varied. From data breaches to unauthorized access, the potential cyber threats that businesses face are numerous.
By scanning your networks, systems, and applications for vulnerabilities, assessments can identify potential entry points for hackers and cybercriminals. This early identification of threats and weaknesses in IT security allows for remediation actions to close any gaps and protect sensitive systems and information, thereby preventing a wide range of cyber threats.
In summary, the role of vulnerability assessment in cyber security is to act as a digital detective, uncovering hidden vulnerabilities within your IT environment and providing actionable insights to help fortify your defenses. As a small to medium-sized business owner, investing in regular vulnerability assessments through a reliable partner like Upper Echelon Technology Group is a valuable step towards ensuring the security and longevity of your business in the digital age.
The Process of Vulnerability Assessment
In the realm of cybersecurity, taking action is a matter of when, not if. Just as a skilled detective uncovers hidden threats, the process of vulnerability assessment is your secret weapon for unmasking lurking cyber threats. With Upper Echelon Technology Group, you can rest assured that this process is handled with precision, expertise, and a personalized approach that suits your business needs.
The Steps Involved in Vulnerability Assessment
The vulnerability assessment process is akin to a meticulous investigation, involving several crucial steps:
- Initial Preparation: This stage determines the scope and goals of vulnerability testing. You have to identify protected assets, their business value, security requirements, and whether they hold sensitive data. This information can help security teams understand the potential threats and develop a remediation strategy.
- Vulnerability Assessment Testing: Automated vulnerability scans are run on target devices and environments. These tests, which could range from a minute to several hours, provide valuable insights into the security posture of a system.
- Prioritize Vulnerabilities: Here, false positives from scan results are eliminated, and vulnerabilities are prioritized based on factors such as severity score, business impact, and the effort needed to deploy a patch.
- Create a Vulnerability Assessment Report: A comprehensive report detailing all the vulnerabilities found in your assets, along with a remediation plan, is created.
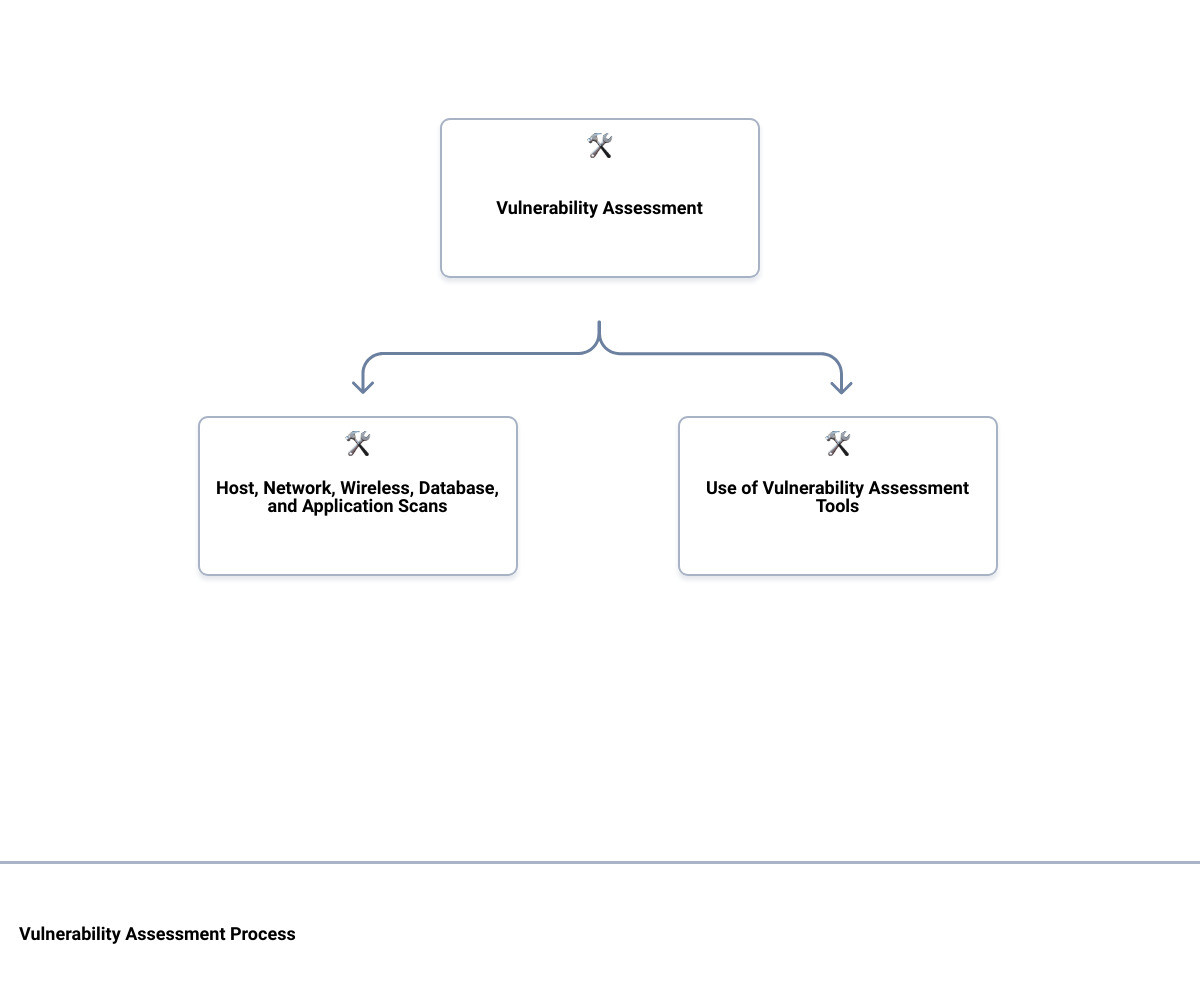
The Different Types of Vulnerability Assessments: Host, Network, Wireless, Database, and Application Scans
Vulnerability assessment isn’t a one-size-fits-all solution. It comprises various types, each designed to unmask different kinds of hidden threats:
- Network-based Scanning: This identifies potential network security attacks and vulnerable systems on wired or wireless networks.
- Host-based Scanning: This type of scan uncovers vulnerabilities on servers, workstations, or other network hosts. It provides insights about open ports, services, configuration settings, and patch history.
- Wireless Network Scans: These scans identify security weaknesses in your Wi-Fi network, including malicious access points.
- Application Scans: These are designed to test websites and mobile applications for known software vulnerabilities and misconfigurations.
- Database Scans: These help identify vulnerabilities that might allow database-specific attacks, as well as general vulnerabilities and misconfigurations in a database server.
The Use of Vulnerability Assessment Tools
To effectively detect vulnerabilities, modern assessments rely on automated scanning tools. These tools play a crucial role in identifying and prioritizing vulnerabilities, helping your security team focus their efforts where it matters most.
Remember, uncovering vulnerabilities is an ongoing process, not a one-time event. By understanding and implementing a robust vulnerability assessment process, you’re proactively fortifying your business against cyber threats. With Upper Echelon Technology Group, you have a trusted partner to guide you through this essential process, ensuring your business remains secure and profitable.
The Benefits of Regular Vulnerability Assessments
In the ever-evolving landscape of cyber threats, one-time vulnerability assessments aren’t sufficient to ensure your business remains secure. Just like regular health check-ups are essential for maintaining physical well-being, routine vulnerability assessments are crucial for your business’s cyber hygiene.
The Importance of Scheduling Regular, Automated Scans of IT Systems
A critical aspect of vulnerability assessment is the automation of regular scans. With the rapid pace of technological changes, IT environments are constantly shifting, with each modification potentially creating a new vulnerability. For instance, a software update or a system configuration change could inadvertently open up a security gap.
Moreover, cyber threats continue to evolve, with new exploits and attack vectors discovered every day. Therefore, it’s paramount to conduct regular and automated vulnerability scans. This proactive approach helps ensure that your systems stay updated against the latest known vulnerabilities.
How Regular Vulnerability Assessments Help Identify and Address Security Weaknesses
The primary benefit of regular vulnerability assessments is the early identification and remediation of security weaknesses. The longer a vulnerability remains undetected, the more time threat actors have to exploit it, potentially resulting in substantial data loss or system damage.
By scheduling regular vulnerability assessments, you’re constantly monitoring your systems for potential vulnerabilities. Once a vulnerability is identified, the assessment tool will report on the issue and suggest corrective actions to mitigate the risk. This not only helps to remove threats but also provides insight into the security and operational impact of remediating a risk versus accepting it.
Moreover, by integrating vulnerability scanning data into a Security Information and Event Management (SIEM) system, you can get a more holistic view of your threat landscape. This integration allows for more effective threat analytics, helping your business understand its overall cyber risk profile, and prioritize fixes accordingly.
Remember, the goal of regular vulnerability assessments is not just to find vulnerabilities, but to fix them. By continually identifying and addressing security weaknesses, you can significantly reduce your exposure to cyber threats, boosting your overall cybersecurity posture. With the expertise of Upper Echelon Technology Group, you can rest assured that your business is taking the right steps towards robust cybersecurity.
Case Study: Upper Echelon Technology Group LLC’s Approach to Vulnerability Assessment
In the ever-evolving world of cybersecurity, businesses require a partner who not only understands the landscape but also knows how to navigate it effectively. Stepping into the spotlight, Upper Echelon Technology Group LLC has demonstrated how vulnerability assessment can be used as a powerful tool to protect businesses from cyber threats.
How Upper Echelon Technology Group LLC Uses Vulnerability Assessment to Protect Businesses
Upper Echelon Technology Group LLC, a cybersecurity-focused managed services provider, has been instrumental in helping businesses leverage their technology assets more effectively. Through a holistic approach, they ensure that not only are technology issues resolved, but that these solutions are aligned with the company’s overall business needs.
Their portfolio of managed IT services is constantly evaluated to ensure that your network is protected and optimized around the clock. Vulnerability assessment forms an integral part of this process. They utilize industry-leading tools to scan IT infrastructure, identifying potential vulnerabilities that could be exploited by cybercriminals. From misconfigurations to policy non-compliance, they take charge of the entire vulnerability management lifecycle, ensuring that potential risks are identified early and addressed promptly.
The Unique Selling Proposition of Upper Echelon Technology Group LLC in Vulnerability Assessment
What sets Upper Echelon Technology Group apart in the realm of vulnerability assessment is their personalized approach. Recognizing that each business is distinct, they tailor their services to meet your specific needs. They understand that technology is not just a tool, but an asset that, when leveraged properly, can drive business growth and profitability.
Their dedicated team works tirelessly to make your company more efficient by leveraging technology and identifying areas where technology can improve your bottom line. They not only solve your technology issues but also equip your team to become more efficient through technology.
Upper Echelon Technology Group’s unique approach extends beyond identifying and fixing tech issues. By focusing on your business needs and how technology can be harnessed to meet those needs, they ensure that your technology serves your business, rather than your business serving your technology.
In conclusion, the vulnerability assessment services provided by Upper Echelon Technology Group LLC are a testament to their commitment to cybersecurity and their drive to provide personalized, effective solutions that enhance business growth and profitability. With them as your partner, you can be assured of a robust, secure, and optimized IT environment.
Conclusion: The Future of Vulnerability Assessment in Cyber Security
Peering into the future of cybersecurity, the increasing sophistication and frequency of cyber threats amplify the urgent need for robust vulnerability assessment. The digital landscape is ever-evolving, and so are the threats that lurk within it. As a business owner, it is crucial to adapt and stay prepared for these emerging threats.
The Need for Continuous Vulnerability Assessment
Continuous vulnerability assessment is no longer a luxury; it’s a necessity. New vulnerabilities are discovered all the time in existing software and hardware components, and organizations introduce new components regularly. This dynamic environment necessitates ongoing vigilance. It’s like a game of cat and mouse; as soon as one vulnerability is patched, another is discovered. Continuous vulnerability assessments allow security teams to stay a step ahead, identifying, analyzing, and categorizing security vulnerabilities on a regular basis.
Moreover, integrating automated vulnerability assessment into the continuous integration and deployment (CI/CD) pipeline in software development teams allows for the early identification and rectification of security weaknesses, reducing the need for patching vulnerable code.
The Role of Vulnerability Management in Preventing Data Breaches and Leaks
Vulnerability management plays a critical role in preventing data breaches and leaks. It is an ongoing process that requires continuous vulnerability assessments. When one assessment completes, another must begin. This process helps prevent data breaches and leaks that can occur due to technology issues or user behavior. Whether it’s an insider accidentally exposing information or cybercriminals installing malware to exfiltrate data, vulnerability management helps companies prevent these scenarios by identifying and remedying security weaknesses.
The Importance of Vulnerability Remediation in Addressing System Security Weaknesses
Finally, vulnerability remediation is a vital part of the vulnerability assessment process. It’s not enough to simply identify vulnerabilities; they must be addressed and fixed. This process involves developing and implementing a plan to remediate the identified vulnerabilities, further enhancing the organization’s security posture.
In conclusion, with the ever-evolving threat landscape, vulnerability assessment is crucial to unmask cyber threats and uncover hidden vulnerabilities. It is an integral part of any robust cybersecurity strategy, helping to prevent breaches, improve security posture, and ultimately, protect your business. As a business owner, partnering with a cybersecurity-focused managed services provider like Upper Echelon Technology Group LLC, you can ensure that your IT environment is robust, secure, and optimized, ready to face the future of cybersecurity.