Introduction: The Importance of Vulnerability Analysis in Cyber Security
A whopping 60% of all data breaches are enabled by vulnerabilities left unpatched. This alarming statistic is a wake-up call for small to medium-sized business owners in Wilmington, DE and beyond. It underscores the criticality of vulnerability analysis in cyber security, an essential practice that can mean the difference between a secure network and a breached one.
Vulnerability analysis, also known as vulnerability assessment, is a systematic process of identifying, prioritizing, and strategizing to mitigate weaknesses in your IT system. It’s a linchpin of the cybersecurity strategy employed by successful businesses to safeguard their technology assets, optimize operations, and drive growth in today’s digital landscape.
The stakes are high. The threats are real. And the solution is clear: a fresh take on vulnerability analysis in cyber security. Ready to unveil the hidden threats lurking in your IT system? Let’s dive in.
Understanding Vulnerability Analysis: A Comprehensive Overview
In the ever-evolving digital landscape, vulnerability analysis in cyber security is your secret weapon against hidden threats. It’s like having a skilled detective on your team, tirelessly working to uncover potential weaknesses before they can be exploited by cybercriminals.
Defining Vulnerability Analysis in Cyber Security
Vulnerability analysis, also known as vulnerability assessment, is a systematic process of identifying, categorizing, prioritizing, and addressing security vulnerabilities in an IT system. This intricate process doesn’t only reveal the weaknesses in your system but also provides a roadmap for remediation. It’s a bit like a health check for your IT system, highlighting potential issues and suggesting ways to fix them before they turn into serious ailments.
The ultimate aim of vulnerability analysis is to fortify your IT system against cyber threats, ensuring your data stays protected and your operations run smoothly.
The Four Main Types of Vulnerabilities in Cyber Security
When discussing vulnerability analysis, it’s important to know the four main types of vulnerabilities in cyber security. These are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
Network vulnerabilities could include insecure network architecture or design, while operating system vulnerabilities might involve outdated or unpatched systems. Process vulnerabilities could stem from inadequate security policies or procedures, while human vulnerabilities often relate to lack of awareness or training in cyber security protocols. Understanding these different types of vulnerabilities can help shape a more effective and comprehensive vulnerability analysis.
The Three Components of Vulnerability Assessment
Vulnerability assessment is often broken down into three key components: exposure, sensitivity, and adaptive capacity.
Exposure refers to the potential threats that your IT system may face, from malware attacks to phishing attempts. Sensitivity involves how susceptible your system could be to these threats, depending on factors like your current security infrastructure and protocols. Finally, adaptive capacity is about your system’s ability to adjust and respond to these threats, which often depends on the resources and skills available to your team.
By considering these three components, you can gain a deeper understanding of your system’s vulnerabilities and tailor your vulnerability analysis to address them in the most effective way.
In the next section, we’ll delve deeper into the process of vulnerability analysis, guiding you step-by-step through this crucial part of your cyber security strategy. Stay tuned.
The Process of Vulnerability Analysis: A Step-by-Step Guide
Diving into the depths of your system’s security can feel like embarking on an expedition into the unknown. Fear not, here’s your roadmap to navigate the intricate process of vulnerability analysis.
Defining Parameters and Planning Assessment
The first step to unveiling hidden threats is to define your parameters and plan your assessment. Start by outlining the scope of the assessment, identifying the systems, networks, and applications to be evaluated. Set clear objectives for the assessment, such as achieving compliance, preventing data breaches, or reducing recovery time. Every vulnerability assessment should be tailored to meet the specific needs and desired business outcomes of your organization.
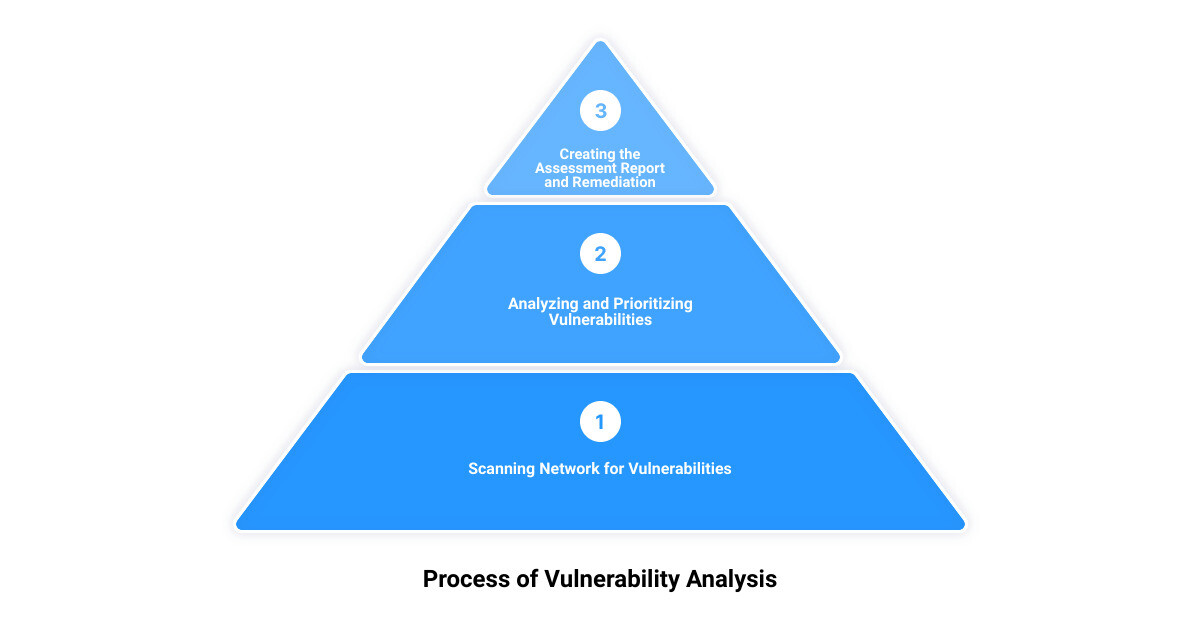
Scanning Network for Vulnerabilities
With your plan in place, it’s time to scan your network for vulnerabilities. This involves using vulnerability analysis tools to inspect your network and detect potential security weaknesses. Remember, the goal is not only to identify vulnerabilities but also to understand the extent of possible exposure if they were to be exploited.
Analyzing Results
Once the scan is complete, it’s time to analyze the results. This involves sifting through the data to identify true positives and filter out false positives. This stage requires a keen eye for detail and a deep understanding of your system’s architecture, as well as the latest security threats and trends.
Prioritizing Vulnerabilities
After analyzing the results, the next step is to prioritize the identified vulnerabilities. Not all vulnerabilities carry the same level of risk, and resources should be allocated to address the most critical threats first. Prioritization should be based on factors such as the severity of the vulnerability, the potential impact on your business, and the cost of remediation.
Creating the Vulnerability Assessment Report
The findings of your vulnerability assessment should be meticulously documented in a comprehensive report. The report should include a detailed description of all identified vulnerabilities, their associated risk levels, recommended mitigation steps, and potential remedies. This report is a valuable tool for communicating the state of your system’s security to stakeholders and for informing your future vulnerability management strategies.
Using Results to Inform Remediation and Mitigation
Lastly, use the results of your vulnerability assessment to inform your remediation and mitigation strategies. This involves patching vulnerabilities, implementing security controls, and regularly monitoring your system for new threats. Remember, vulnerability analysis is not a one-off process but a continuous cycle of assessment, remediation, and review.
The road to robust cybersecurity may be winding, but with a systematic approach to vulnerability analysis, you can effectively navigate the landscape and shield your organization from the ever-evolving threats in the cyber world.
Types of Vulnerability Assessments: A Closer Look
Unveiling the hidden threats in your organization’s cybersecurity landscape requires a comprehensive approach. This involves conducting different types of vulnerability assessments to identify weaknesses in various areas of your IT infrastructure. Let’s delve into four main types of vulnerability assessments that can provide you with a 360-degree view of your cybersecurity posture.
Application Assessments
Application assessments focus on identifying vulnerabilities within the web applications your organization uses. Cyberattackers often exploit weak points in applications to gain unauthorized access or disrupt operations. Therefore, conducting regular application assessments is critical in detecting potential security gaps in your web applications and implementing necessary fixes.
Network Assessments
Network assessments are another crucial aspect of vulnerability analysis. These involve a thorough review of your procedures and policies to guard against unauthorized access. Networks are the backbone of your IT infrastructure, and any vulnerability within this system can have serious implications for your business operations and data security. Network assessments help identify weak points in your network security, enabling you to take corrective measures and fortify your defenses.
Database Assessments
In the digital age, data is one of the most valuable assets of any business. Consequently, protecting your databases from cyber threats is paramount. Database assessments aim to uncover configuration issues, unprotected data, and other vulnerabilities within your infrastructure. By conducting database assessments, you can identify these potential risks and take necessary steps to safeguard your data.
Host Assessments
Last but not least, host assessments play a vital role in vulnerability analysis. These assessments reveal vulnerabilities of your critical servers which could impact operations and security if not adequately tested and protected. In simple terms, a host assessment scrutinizes the security measures in place for your physical servers and virtual machines, checking for any potential weaknesses that could be exploited by cybercriminals.
Each of these assessments plays a unique role in fortifying your cybersecurity infrastructure. By routinely conducting these vulnerability assessments, you can stay one step ahead of potential cyber threats, ensuring your business remains secure and resilient in an ever-evolving cyber landscape.
Tools and Techniques for Effective Vulnerability Analysis
As we venture deeper into the world of cybersecurity, it’s time to equip ourselves with the right tools and techniques for an effective vulnerability analysis. While the process can seem daunting, these resources can make the task more manageable, efficient, and reliable.
Overview of Common Vulnerability Analysis Tools
The cybersecurity industry is teeming with a variety of vulnerability analysis tools, each with their unique strengths. OpenVAS is a comprehensive tool that can scan everything from web apps and servers to network, operating systems, and databases. SolarWinds, a network configuration manager, is ideal for identifying network errors and misconfigured equipment. For cloud-based storage systems, Intruder provides constant monitoring and automatic scanning. Nikto2 is an excellent open-source tool for scanning web applications, and Nexpose offers up-to-date information on new vulnerabilities.
Choosing the right tools for your vulnerability analysis process requires an understanding of your specific needs and the nuances of each tool. It is a crucial part of the process that requires careful consideration, as it directly impacts the efficiency and effectiveness of your vulnerability analysis.
Dynamic Application Security Testing (DAST)
DAST is a testing process that involves checking your web applications for potential vulnerabilities. The beauty of DAST is that it simulates attacks on your applications in a real-time environment, helping identify vulnerabilities that could be overlooked in a more static analysis.
Static Application Security Testing (SAST)
Unlike DAST, SAST is a white-box method of testing. This technique involves reviewing the source code of your application to identify potential security vulnerabilities. SAST allows you to catch and fix issues early in the development process, making it a go-to technique for developers.
Penetration Testing
Often referred to as ethical hacking, penetration testing is a hands-on approach to cybersecurity. Here, security professionals simulate cyber-attacks on your system to identify vulnerabilities that could be exploited by real hackers. Penetration testing is an invaluable tool that helps you understand the resilience of your systems against real-world cyber threats.
In the world of vulnerability analysis, there is no one-size-fits-all solution. The most effective approach is usually a combination of these tools and techniques, tailored to suit your specific business needs and cybersecurity objectives. Remember, the goal is not just to identify vulnerabilities but also to understand them well enough to develop effective mitigation strategies. After all, in the high-stakes game of cybersecurity, knowledge is your most potent weapon.
Best Practices for Conducting Vulnerability Analysis
Navigating the choppy waters of cybersecurity can be daunting, but having a roadmap can make the journey smoother. When conducting vulnerability analysis, following certain best practices can ensure that you get the most out of the process, and more importantly, keep your business assets shielded from potential cyber threats.
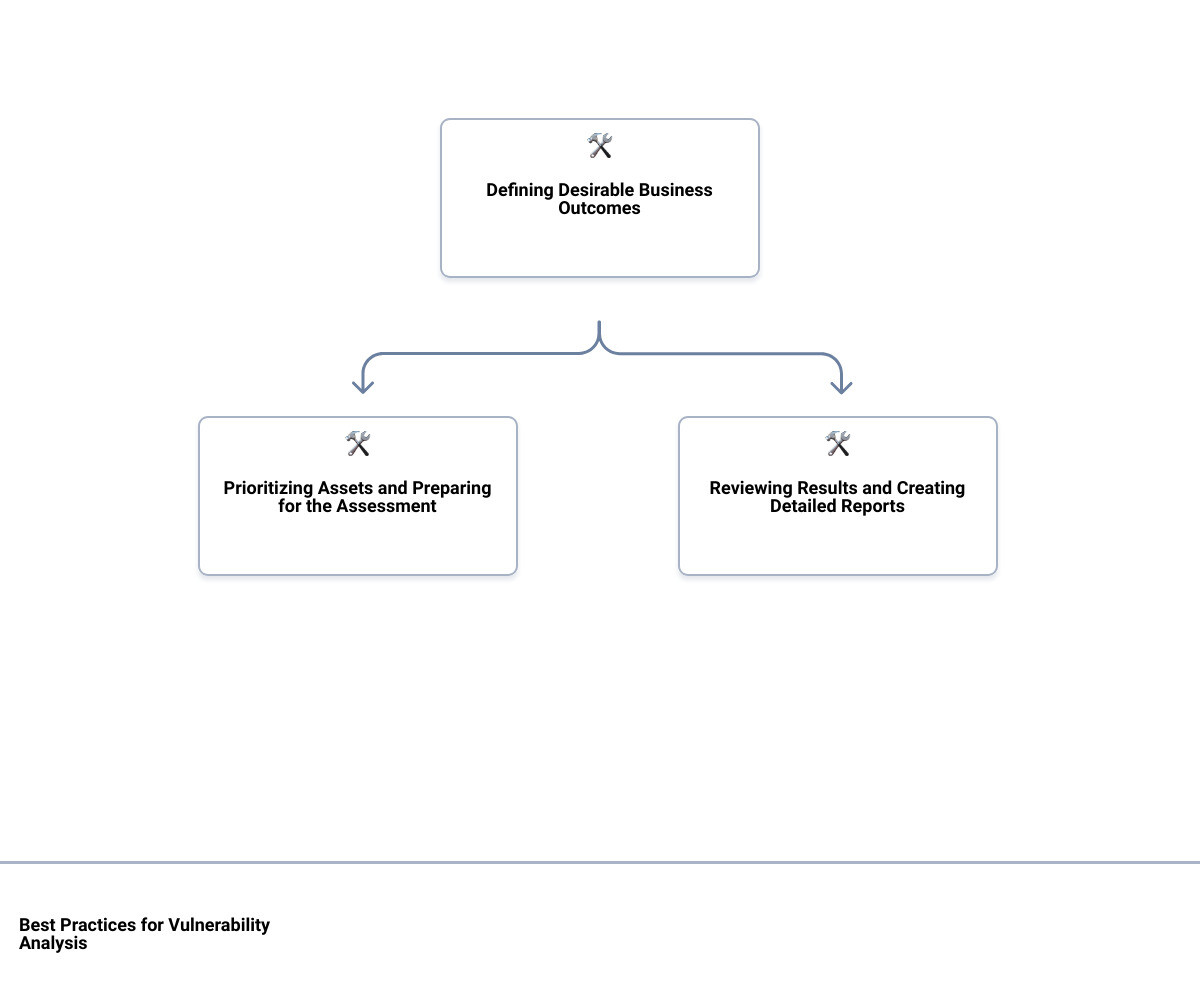
Defining Desirable Business Outcomes
To get the ball rolling, start by defining your business outcomes. While routine processes like vulnerability assessments are integral to your cybersecurity strategy, it’s essential to identify what you want to achieve out of every assessment. This could range from prioritizing risks, achieving compliance, preventing data breaches, to reducing recovery time. Defining these desirable outcomes in advance ensures the process is productive and tailored to your specific business needs.
Prioritizing Assets
Next on the checklist is to prioritize your assets. A comprehensive vulnerability assessment can be exhaustive, especially for the first-timers. Therefore, it’s crucial to assess the most essential components first. By understanding the different types of assessments and structuring them accordingly, you can ensure that the most critical assets receive immediate attention.
Preparing for the Assessment
The road to conducting a vulnerability assessment isn’t just a click away. It involves meticulous technical preparation like conducting meetings, constructing a threat model, interviewing system developers, and verifying the test environment details. Familiarity with passive and active vulnerability testing methods is key to a successful assessment. Knowing when and where to employ each testing method can be the difference between a successful defense and a critical breach.
Reviewing Results
As you sail through the assessment, it’s vital to manually review your results. To ensure accuracy, filter out false positives and prioritize true positives. Record each step taken and collect evidence to ensure the process is fully understood and repeatable. This will be invaluable when you need to explore a particular vulnerability more closely later.
Creating Detailed Reports
Last, but certainly not least, is creating detailed reports after each assessment. The value of a vulnerability assessment is in the insights it provides. Creating a comprehensive report with a thorough description of all vulnerabilities, associated risk levels, mitigation steps, and remedies is key. These reports act as a guidepost for taking action and are invaluable for communicating issues to non-technical stakeholders, such as those in the C-suite who need to be aware of significant risks and strategies to combat them.
In the world of cybersecurity, staying ahead of potential threats is key. By following these best practices, you can ensure your vulnerability analysis process is as thorough, efficient, and productive as possible.
The Role of Continuous Education and Training in Vulnerability Analysis
The digital landscape is ever-evolving, and so are the threats that lurk within it. As a small to medium-sized business owner in Wilmington, DE, keeping up with the latest trends in vulnerability analysis practices is crucial in protecting your valuable digital assets. This involves continuous education and training, which are vital components of an effective cybersecurity strategy.
The Importance of Staying Up-to-Date with Vulnerability Assessment Practices
In the fast-paced world of cyber threats, stagnation equals vulnerability. New vulnerabilities are discovered almost daily in software and hardware components, and cyber threat actors are always on the lookout for new ways to exploit them. Staying current with the latest vulnerability assessment practices is your first line of defense against these threats.
Regular updates about the latest trends, threats, and mitigation strategies are essential. This involves not only following trusted sources of cybersecurity news but also participating in industry events and forums where experts share their knowledge and experience.
Moreover, the vulnerability assessment tools and techniques that were effective yesterday might not be as effective today. Cybersecurity is a field where outdated practices can lead to significant risks. It’s critical to keep up with the developments in vulnerability assessment tools and methodologies to ensure that your processes are as thorough and efficient as possible.
The Benefits of Pursuing Further Education and Training
Investing in further education and training comes with numerous benefits. It equips your IT team with the knowledge and skills to identify, analyze, and mitigate vulnerabilities effectively. Training can help to standardize practices across the team, ensuring everyone is on the same page when it comes to vulnerability assessment.
Moreover, training provides an opportunity to learn from the experiences of others, gaining insights into the types of vulnerabilities that other organizations have faced and how they have responded. This can help to anticipate potential threats and prepare your defenses accordingly.
Also, pursuing certifications like the Certified Ethical Hacker (C|EH) or the Certified Network Defender (C|ND) can significantly enhance the credibility of your IT team. These certifications validate the knowledge and skills of your team members, assuring you and your stakeholders that your organization’s cybersecurity is in capable hands.
Ultimately, the role of continuous education and training in vulnerability analysis is to empower your organization to stay one step ahead of potential threats. By keeping up-to-date with vulnerability assessment practices and investing in further education and training, you can ensure that your defenses are as strong as possible, protecting your business from the ever-evolving threats in the digital landscape.
Conclusion: The Future of Vulnerability Analysis in Cyber Security
In the fast-paced world of cyber security, standing still is not an option. As businesses continue to leverage technology for growth and efficiency, cyber threats also evolve, growing more intricate and damaging. The future of vulnerability analysis in cyber security is heading towards more proactive, predictive, and personalized strategies.
The development of AI and machine learning technologies is expected to streamline vulnerability analysis, making it quicker, more precise, and more efficient. These advanced technologies can sift through vast amounts of data, identifying patterns and predicting vulnerabilities before they can be exploited.
The future also promises a more integrated approach to vulnerability analysis, with the process becoming a fundamental part of the larger IT security framework. This means that vulnerability assessments will not be standalone processes, but will work hand-in-hand with other security measures like penetration testing, encryption, and incident response.
Continuous education and training in cyber security, like the Certified Ethical Hacker (C|EH) course, will remain vital. Staying ahead of the curve in the dynamic landscape of cyber threats requires staying informed about the latest tactics, techniques, and procedures used by threat actors.
Technology will continue to be a double-edged sword. While it opens up new avenues for growth and efficiency, it also exposes businesses to cyber threats. In the face of this reality, vulnerability analysis will continue to be a critical line of defense. It will evolve, innovate, and adapt, just like the threats it aims to neutralize.
In conclusion, vulnerability analysis in cyber security is an ongoing journey, not a destination. It’s about staying vigilant, staying educated, and staying prepared. As a business owner, embracing this process is one of the most powerful ways to safeguard your company’s digital assets and protect the trust that your customers place in you. With the right strategy, tools, and partner like Upper Echelon Technology Group, you can navigate the future of cyber security with confidence.