In a world where digital threats are becoming increasingly complex and pervasive, understanding the nuances of cyber security threat assessment is no longer an option but a necessity for businesses. Cyber security threat assessment is a critical component of a robust security strategy, helping organizations identify, analyze, and mitigate potential threats that could compromise their digital assets. This article delves into the complexities of threat assessment in cyber security, providing an essential guide for small to medium-sized business owners to understand and implement this critical process.
A cyber security threat assessment is a systematic approach used to identify potential threats to an organization’s digital assets, evaluate their potential impact, and devise strategies to mitigate them. These threats can range from direct attacks such as ransomware campaigns, human errors due to negligence, system failures of IT security controls, to natural disasters outside of human control. Understanding and assessing these threats is the first step towards protecting your business and ensuring the integrity, availability, and confidentiality of your sensitive data.
As a small to medium-sized business owner in Wilmington, DE, you might be grappling with these challenges and seeking a personalized, efficient, and effective approach to your IT managed services. This is where the Upper Echelon Technology Group comes into play, offering a unique blend of cyber security expertise and personalized IT managed services, tailored to solve your technology issues, enhance your team’s efficiency, and improve your company’s profitability.
So, are you ready to unlock the secrets of cyber security threat assessment and fortify your business against potential digital threats? Let’s dive in.
Understanding the Importance of Threat Assessment in Cyber Security
In the ever-evolving digital landscape, the significance of threat assessment in cyber security becomes more apparent each day. As the first line of defense against potential cyber threats, understanding its role and why businesses need to conduct these assessments is vital.
The Role of Threat Assessment in Cyber Security
Threat assessment in cyber security serves as the compass guiding your organization through the turbulent waters of digital threats. It’s a methodical process that identifies potential threats to your digital assets and evaluates the risks associated with these threats.
This process is not merely about predicting where the next cyber attack may come from. Instead, it encompasses a comprehensive evaluation of the state of your organization, the types of controls in place, and the vulnerabilities that could potentially be exploited by threat actors. This evaluation aids in predicting which threats are more likely to occur, based on historical evidence and empirical data.
Moreover, threat assessment also involves an evaluation of the adversary’s intent, their capability to carry out an attack, and the intended target of the attack. By systematically identifying, evaluating, and addressing potential vulnerabilities, threat assessment helps in fortifying your organization’s cyber defenses.
Why Businesses Need to Conduct Cyber Security Threat Assessments
In today’s interconnected world, no business is immune to cyber threats. The risk is especially high for small to medium-sized businesses, which are often seen as easy targets by cybercriminals due to their limited resources for cybersecurity.
Conducting a cyber security threat assessment can help businesses gain a clear understanding of their security posture, identify vulnerabilities, and implement robust security measures to prevent potential attacks. This proactive approach to cyber security can save businesses from the devastating effects of data breaches, which can lead to financial losses, damage to reputation, and loss of customer trust.
Moreover, a well-conducted threat assessment can also guide your IT managed services provider, like Upper Echelon Technology Group, in tailoring personalized solutions that address your specific needs. This is an added advantage for businesses who value a personalized approach to IT Managed Services, as it allows them to leverage their technology assets in the best way possible to protect their business.
In conclusion, the importance of threat assessment in cyber security cannot be overstated. It’s a crucial component of a comprehensive cybersecurity strategy that helps businesses stay one step ahead of cybercriminals and ensure the safety of their digital assets.
The Process of Cyber Security Threat Assessment
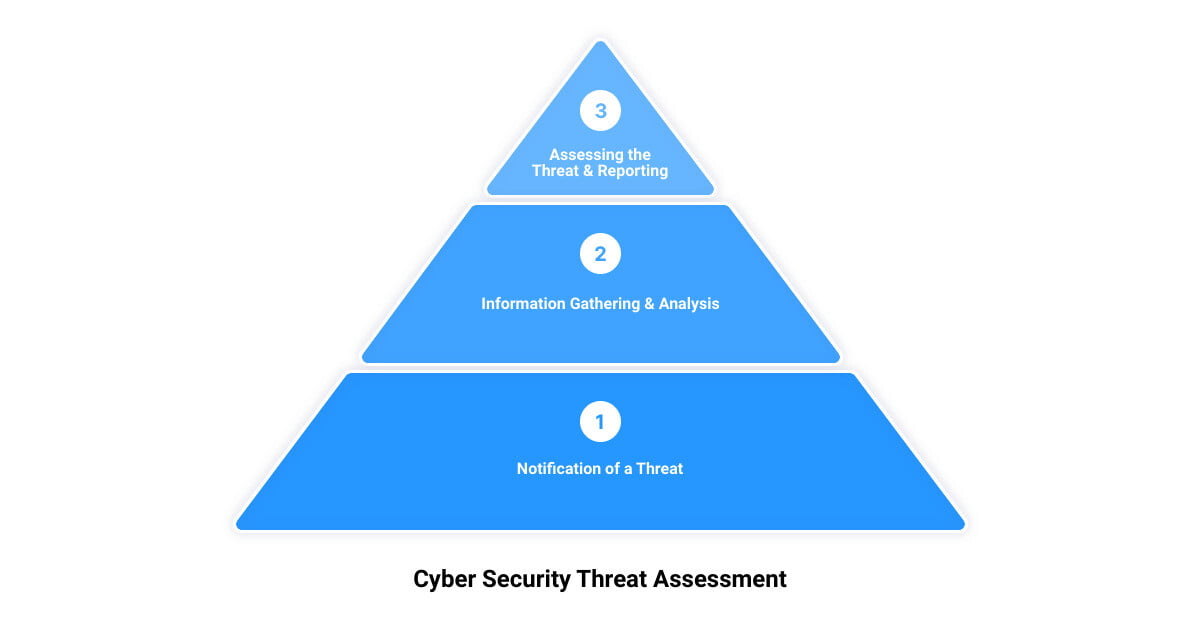
In an increasingly digital world marked by advanced cyber threats, understanding the process behind a cybersecurity threat assessment is paramount for every business owner. This process, which identifies potential security weaknesses and takes action to manage risks, involves five crucial steps.
Step 1: Notification of a Threat
The first step in the process of cybersecurity threat assessment is the notification of a potential threat. This can occur through various means, such as alerts from security software, notification from an employee, or a report from a threat intelligence feed. The key here is to have a reliable system in place that can quickly and accurately identify a potential threat.
Step 2: Information Gathering
Following the notification of a threat, the next step is to gather as much information as possible about the potential risk. This can encompass collecting data from internal and external sources, including historical information on past cyber events and existing security measures. Accurate information gathering is crucial for a comprehensive analysis of the threat.
Step 3: Analysis of Information
Once all relevant information has been collected, it’s time to analyze it. This analysis should consider both the nature of the threat and its potential impact on operations and specific assets. The analysis phase will likely include examining the threat’s potential harm, its likelihood, and the vulnerabilities it may exploit.
Step 4: Assessing the Threat
After analyzing the gathered information, the next step is to assess the threat. This involves evaluating the risk posed by the threat to the organization’s assets and operations. It is crucial that this assessment is objective and uses established risk models to accurately quantify the threat.
Step 5: Documentation and Reporting
The final step in the process is to document and report the findings of the threat assessment. This documentation should include details of the threat, the analysis process, the risk assessment, and any recommended actions for threat mitigation. Reporting these findings ensures that key stakeholders are aware of the threat and can take appropriate actions.
By following these steps, businesses can ensure a systematic approach to cybersecurity threat assessment, increasing their ability to manage and mitigate potential cyber threats effectively. The Upper Echelon Technology Group LLC understands the importance of this process and helps businesses navigate through it with their personalized approach to IT Managed Services.
Key Terms in Cyber Security Threat Assessment
A mastery of cyber threat assessment starts with understanding the lingo. The world of cybersecurity is fraught with a plethora of terms and acronyms that can often seem overwhelming. Fear not! We are here to demystify these terms and ensure you have a firm grasp of the language used in threat assessment and analysis.
Glossary of Threat Assessment/Analysis Terms
Threat Assessment: This is a vital process in the world of cybersecurity that entails formally evaluating the extent of threat to an information system, enterprise, or organization. It involves describing the nature of the threat and how it could potentially impact your business. This term is often used interchangeably with ‘threat analysis’.
Threat Analysis: A synonym for threat assessment, threat analysis involves a detailed evaluation of potential threats to a system or organization. It’s all about understanding the threats that could potentially compromise your cybersecurity.
Understanding Threat Analysis Abbreviations, Acronyms, and Synonyms
In the cybersecurity world, abbreviations and acronyms abound, making it feel like you’re deciphering a secret language. But don’t worry, we’re here to help you unlock this code.
CNSSI 4009-2015: This is a reference to the National Information Assurance (IA) Glossary, a document that provides definitions for terms used in the field of information security.
NIST SP 800: This refers to a series of publications by the National Institute of Standards and Technology (NIST), providing guidelines and recommendations for federal agencies to improve their information security.
NISTIR 7622: Another publication from NIST, which provides practical guidelines for managing risks in federal information systems.
By understanding these key terms and abbreviations, you’re well on your way to mastering the language of cybersecurity threat assessment. Remember, knowledge is power. The more you know, the better prepared you’ll be to protect your business against potential cyber threats. The Upper Echelon Technology Group LLC is here to help you navigate this complex landscape, offering a personalized approach to IT Managed Services that prioritizes your business’s unique needs and objectives.
Cyber Security Risk Assessment: An Integral Part of Threat Assessment
Unlocking the secrets of cyber security threat assessment is akin to navigating a labyrinth, with each corner posing a new challenge. But with a well-planned cyber security risk assessment, this complex maze can be traversed with precision and foresight. The process of risk assessment forms the bedrock of effective threat assessment, giving businesses a powerful tool to anticipate and mitigate cyber threats.
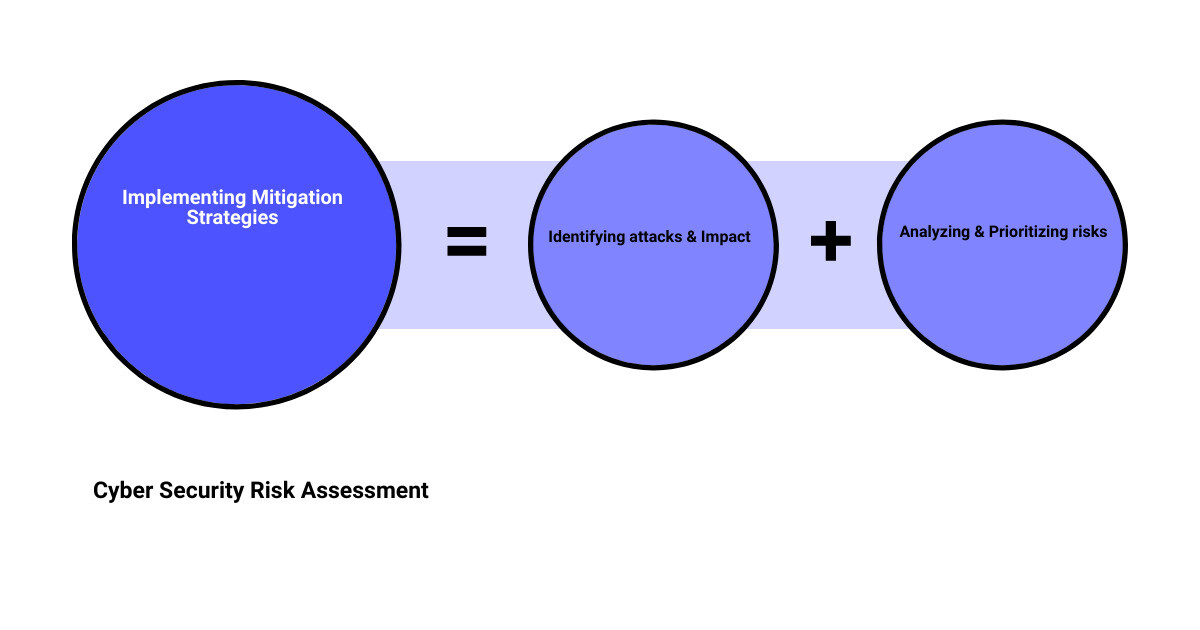
Identifying Key Business Objectives and Essential IT Assets
The path to secure cyber operations begins with a clear understanding of your business objectives and the identification of your essential IT assets. This step requires an in-depth analysis of your business model and the role technology plays in achieving your goals. As the saying goes, “You can’t protect what you don’t know”. Therefore, create a comprehensive inventory of all physical and logical assets within the scope of the risk assessment. This includes identifying not just the obvious targets like customer databases or intellectual property, but also less conspicuous assets like your Active Directory server, which could be exploited as a pivot point to expand an attack.
Identifying Potential Cyber Attacks and Assessing Their Impact
The next step requires you to adopt the mindset of a cybercriminal. Using resources like the MITRE ATT&CK Knowledge Base and advisories from organizations like the Cybersecurity & Infrastructure Security Agency, identify potential cyber threats that your organization may be vulnerable to. Each threat should be evaluated in terms of its potential impact on your business operations, taking into account factors like disruption of business processes, financial loss, reputational damage, and legal implications.
Analyzing, Prioritizing, and Documenting Risks
Once potential cyber threats have been identified and their impact assessed, the next step is to analyze and prioritize these risks. This involves gauging the likelihood of each threat and its potential impact, thereby enabling you to focus your resources on the most significant risks. It’s crucial to document this entire process meticulously, maintaining a detailed record of identified threats, their potential impact, and the underlying assumptions and limitations of your risk analysis. This not only aids in decision-making but also facilitates compliance with various standards and laws like HIPAA, Sarbanes-Oxley, and PCI DSS.
Implementing Mitigation Strategies
The final step involves developing and implementing strategies to mitigate the identified risks. This could range from strengthening your network security defenses and implementing more robust access controls, to undertaking employee training programs for enhancing awareness about phishing and other cyber threats. Remember, the goal isn’t to eliminate all risks – that’s an unrealistic aim in today’s ever-evolving cyber landscape. Instead, the focus should be on reducing risks to a level that is in line with your organization’s risk tolerance.
While the process of cyber security risk assessment may seem daunting, it’s an investment that can pay dividends by safeguarding your business from potentially catastrophic cyber attacks. And with a partner like Upper Echelon Technology Group LLC at your side, you can rest assured that your cyber security needs are in capable hands.
Case Study: Upper Echelon Technology Group LLC’s Approach to Threat Assessment in Cyber Security
Cyber threats are like chameleons, changing colors to blend into their environment and become less detectable. But what if you could see through their camouflage and predict their next move? Welcome to the world of cyber threat assessment at Upper Echelon Technology Group LLC.
Personalized IT Managed Services and Their Role in Threat Assessment
At Upper Echelon Technology Group LLC, the threat assessment process is not about applying a one-size-fits-all solution. Rather, it involves a personalized approach that aligns technology with the unique needs of the business. This approach helps businesses not just address their tech issues, but also leverage their technology assets for maximum efficiency and profitability.
The personalized approach to threat assessment begins with identifying the unique vulnerabilities within an organization. This could stem from the technology used within the industry, the environment in which the business operates, and the organization’s mission or business functions.
In addition, the threat assessment process also takes into account the gaps in organizational governance such as poor risk management practices, improper management of cybersecurity infrastructure, and insufficient oversight of third-party cybersecurity compliance. By identifying these vulnerabilities, Upper Echelon Technology Group is able to predict the likelihood of specific threats occurring, thus enabling them to prevent potential full-blown attacks.
How Upper Echelon Technology Group LLC Tailors Threat Assessment to Meet Business Needs
Upper Echelon Technology Group LLC doesn’t stop at identifying threats. They take it a step further by evaluating the potential impact of these threats on all stakeholders connected to the organization. This involves an assessment of the intent of the adversary, the capability of the cybercriminal, and the intended target of the perpetrator.
This threat assessment process is then combined with the company’s managed IT services offerings, which are continuously evaluated to ensure that the network of their clients is protected and optimized at all times. This holistic approach to threat assessment and cybersecurity ensures that businesses can operate smoothly, without having to worry about serving their technology but instead having their technology serve them.
In conclusion, Upper Echelon Technology Group LLC’s approach to threat assessment in cybersecurity is unique and personalized, focusing on the specific needs of each business. This, coupled with their commitment to providing a culture that allows both their employees and clients to reach their fullest potential, allows them to provide a comprehensive solution to any cybersecurity threat.
Conclusion: The Power of Effective Cyber Security Threat Assessment
As we’ve navigated through the intricate maze of cybersecurity threat assessment, one truth clearly rises above the rest: the power of effective threat assessment is undeniable. A robust cybersecurity threat assessment is a linchpin to safeguarding your IT infrastructure and vital business data. It’s not just about identifying potential threats, but also about understanding their likelihood, potential impact, and how to effectively mitigate them.
Upper Echelon Technology Group LLC stands as a prime example of a cybersecurity-focused managed services provider that understands the importance of a comprehensive cybersecurity threat assessment. Their personalized approach to IT managed services, backed by a deep understanding of risk management, aligns seamlessly with the unique needs of small to medium-sized businesses in Wilmington, DE and beyond.
Their team of experts doesn’t just ‘fix tech issues’. They dive deeper, focusing on leveraging technology to drive business growth, make teams more efficient, and improve company profitability. Their ethos of putting relationships first, relentless pursuit of personal growth, and a culture that prioritizes open, honest, and productive communication sets them apart in a crowded market.
In the end, the secret to unlocking the power of cybersecurity threat assessment lies in a deep understanding of your business needs, and a focused approach to identifying, analyzing, and managing risks. It’s about turning potential vulnerabilities into strengths, threat scenarios into strategic action plans, and fear of cyber attacks into assurance of security.
Choosing a provider like Upper Echelon Technology Group LLC means you’re not just choosing a service, but a partner. A partner who is committed to your business’s success, who understands your needs, and who is equipped with the knowledge and tools to keep your business safe, secure, and ready to face the ever-changing landscape of cyber threats.
In the grand scheme of things, an effective cybersecurity threat assessment is your business’s first line of defense against the digital unknowns. And with a proactive, personalized approach, you can ensure that your cybersecurity is not just a line item on a checklist, but a robust, dynamic shield that stands guard over your business’s most valuable assets.
The power of effective cybersecurity threat assessment is indeed immense. Harness it well, and unlock the potential of your business in the digital age.