In the rapidly evolving digital landscape, cyber security threat and risk assessment has become a crucial line of defense for businesses of all sizes. At Upper Echelon Technology Group, we understand that the stakes are high. Cyber threats can lead to serious financial and reputational damage, and in some instances, they can even cause a business to cease operations. This is why understanding and managing cyber risks is not just a necessity but a business imperative.
A cyber security risk assessment is a systematic process that helps organizations identify threats, vulnerabilities, and potential impacts posed by cyber threats. It provides a clear view of the potential dangers lurking in your IT assets and gives you a roadmap to prioritize your defense strategies. Offering more than just a technical solution, this process also addresses the human element of cyber risk, acknowledging that employees can often be a weak link in cyber security.
Even with the most advanced security measures, no organization is completely immune to cyber threats. Hackers continually evolve their techniques, making it an ongoing challenge to stay ahead. This underscores the importance of regular threat and risk assessment in cyber security.
Key Elements of Cyber Security Threat and Risk Assessment
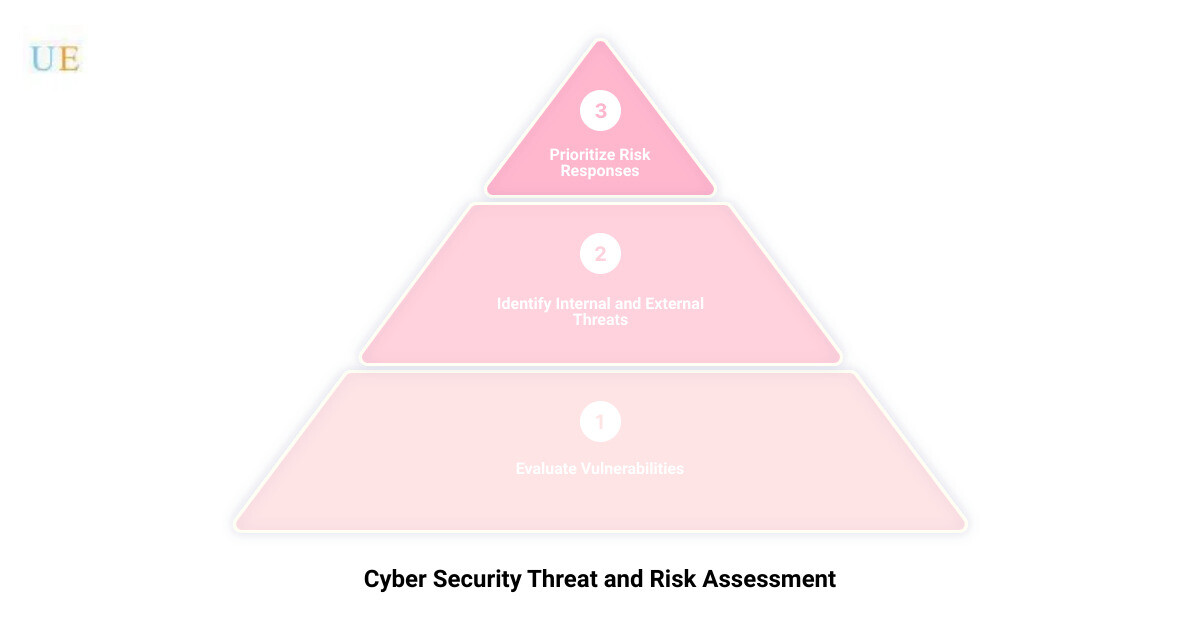
- Identification of IT asset vulnerabilities
- Use of cyber threat intelligence sources
- Documentation of internal and external threats
- Assessment of potential mission impacts
- Determination of risk based on threats, vulnerabilities, likelihoods, and impacts
- Prioritization and implementation of risk responses
!threat and risk assessment cyber security 6 stage pyramid
As cybersecurity experts at Upper Echelon Technology Group, we make it our mission to assist businesses in understanding and managing their cyber risks effectively. With our personalized approach to IT managed services, we go beyond just fixing tech issues. We focus on your business needs and how you can leverage your technology assets in the best possible way to help your business.
Stay tuned as we delve deeper into the world of cyber security threat and risk assessment, and reveal its hidden dangers and how to navigate them.
Understanding Cyber Security Threat and Risk Assessment
In the complex landscape of online security, understanding cyber security threat and risk assessment is a crucial first step to securing your business. The experts at Upper Echelon Technology Group are here to help you gain a better understanding of these crucial terms.
Definition of Threat Assessment in Cyber Security
In the realm of cyber security, a threat assessment is the formal process of evaluating the degree of threat to an information system or enterprise and describing the nature of the threat. It provides a comprehensive understanding of potential hazards that could compromise your business’s critical data and systems.
In essence, a threat assessment is a crucial aspect of your business’s cyber security strategy, highlighting potential vulnerabilities and laying the groundwork for effective countermeasures.
Definition of Security Threat and Risk Assessment
Diving deeper, a Security Threat and Risk Assessment (STRA) is an activity that assesses and reports security risks for an information system. It’s a vital tool for making well-informed, risk-based decisions. An STRA documents risk ratings and suggests treatments to mitigate those risks.
STRA is a comprehensive approach that identifies potential threats, analyses their likely impact, and proposes strategies to mitigate the risk associated with these threats.
The Role of Risk Assessment and Risk Management in Cyber Security
Risk assessment and risk management are integral parts of a robust cyber security strategy. A security risk assessment identifies, assesses, and implements key security controls in applications. It’s focused on preventing application security defects and vulnerabilities.
Carrying out a risk assessment allows an organization to view the application portfolio holistically—from an attacker’s perspective. It’s a proactive approach to security that helps businesses identify potential vulnerabilities before they become a problem.
Risk management, on the other hand, is an ongoing process that involves identifying, assessing, and controlling threats to an organization’s capital and earnings. It’s about making sure that even if a threat becomes a reality, the impact on the business is minimized.
At Upper Echelon Technology Group, we take an integrated approach to risk assessment and management. Our team of experts ensures that your business’s cyber security strategy is always one step ahead of potential threats, keeping your data and systems secure.
In the next section, we will delve into the process of cyber security threat and risk assessment, revealing how this complex procedure can help protect your business from cyber threats.
The Process of Cyber Security Threat and Risk Assessment
Stepping into the world of cyber security threat and risk assessment may seem daunting at first, but it’s a process that can be broken down into manageable, systematic steps. At Upper Echelon Technology Group, we follow industry standards and best practices to ensure comprehensive and effective risk assessments.
The Four Steps of Threat and Risk Assessment
The process of threat and risk assessment can be summarized into four key steps:
-
Prioritize Assets Needing Protection: The first step is to identify and prioritize the assets within your organization that are most critical and need protection. This could be sensitive data, proprietary software, or intricate network systems.
-
Identify Network Vulnerabilities: The second step involves identifying potential vulnerabilities within your network. These may include weak passwords, outdated software, or misconfigured firewalls.
-
Create a Cybersecurity Policy: Having identified the vulnerabilities, the third step is to create a cybersecurity policy that outlines how to address these vulnerabilities and protect your assets.
-
Conduct Awareness Training for Employees: The final step is to conduct awareness training for employees. This is essential as many security breaches are the result of human error or lack of knowledge.
These four steps represent a general framework, but it’s important to remember that every organization is unique. The specifics of each step will vary based on the nature of your business and the specific threats you face.
The Six-Step Process by NIST for Performing a Cyber Security Risk Assessment
In addition to the four steps above, we at Upper Echelon Technology Group follow the six-step process outlined by the National Institute of Standards and Technology (NIST) for performing a cyber security risk assessment. This process is more detailed and provides a comprehensive approach to identifying and addressing cyber risks.
-
Identify and Document Network Asset Vulnerabilities: As with the four-step process, the NIST process begins by identifying potential vulnerabilities within your organization’s IT assets.
-
Identify and Use Sources of Cyber Threat Intelligence: The second step involves gathering and using cyber threat intelligence. This can be obtained from various sources, both internal and external, to help identify potential threats.
-
Identify and Document Internal and External Threats: The third step is to identify and document both internal and external threats. This includes scanning systems for indicators of compromise, auditing configuration files, and monitoring for unusual behavior in log files.
-
Identify Potential Mission Impacts: The fourth step is to identify the potential impact of each threat on your organization’s mission. Different threats have different potential impacts, so it’s crucial to understand the risk each one poses.
-
Use Threats, Vulnerabilities, Likelihoods, and Impacts to Determine Risk: In the fifth step, you’ll use the information you’ve gathered to quantify the risk of each threat. This involves a combination of the likelihood of an attack and the potential impact.
-
Identify and Prioritize Risk Responses: The final step is to prioritize the identified threats and vulnerabilities and develop a response plan. This step ensures that the most significant risks are addressed quickly and efficiently.
These two processes represent the core of what a cyber security threat and risk assessment involves. By understanding and implementing these steps, organizations can significantly improve their cyber defenses and increase their resilience to cyber threats. In the next section, we’ll discuss the outcomes and benefits of these assessments.
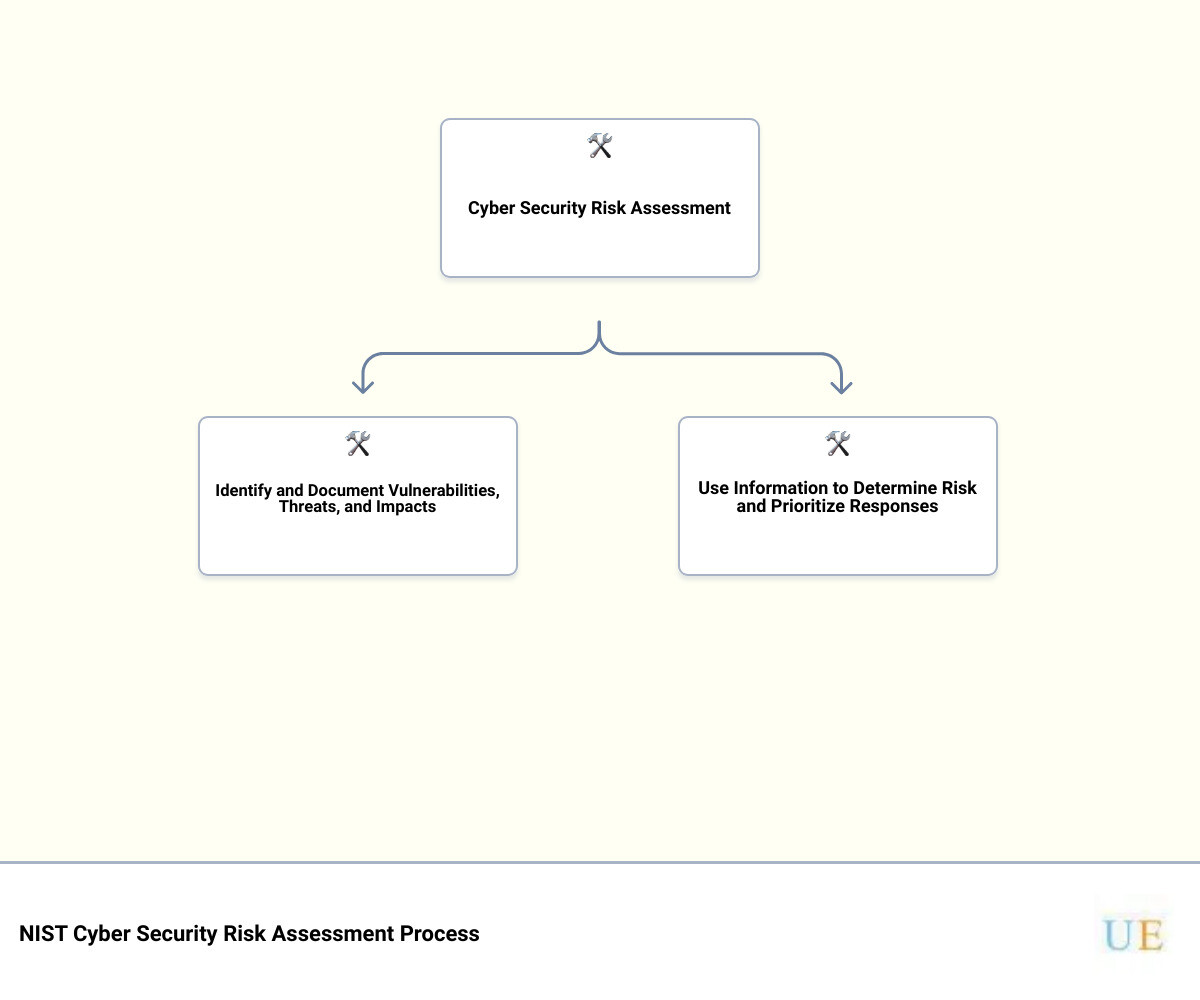
Infographic description: A six-step infographic showing the NIST process for performing a cyber security risk assessment. The steps are: 1) Identify and document network asset vulnerabilities, 2) Identify and use sources of cyber threat intelligence, 3) Identify and document internal and external threats, 4) Identify potential mission impacts, 5) Use threats, vulnerabilities, likelihoods, and impacts to determine risk, and 6) Identify and prioritize risk responses.
The Outcome and Benefits of a Cyber Security Risk Assessment
Emerging from the dark web of potential cyber threats, your business needs a lighthouse to guide it towards secure shores. That’s where a cyber security risk assessment comes into play. This essential process serves as your guiding light, illuminating the vulnerabilities within your cyber defenses and charting a course towards stronger security.
The Action Plan: Correcting Vulnerabilities and Improving Defenses
Here’s where the rubber meets the road. The outcome of a cyber security risk assessment is essentially a comprehensive action plan. This plan, armed with the insights gleaned from the assessment process, is your map towards correcting vulnerabilities in your cyber environment.
Our expert at Upper Echelon Technology Group, often likens this action plan to a physician’s treatment plan. “Just as a doctor would diagnose a patient’s illness and prescribe a treatment plan, a risk assessment identifies weaknesses in your cyber defenses and prescribes remediation strategies,” they explain.
The cyber security team within your organization, or your managed services provider, can then take steps to implement these remediation strategies, thereby fortifying your defenses against real-world cyber attacks.
The Benefits: Vulnerability Remediation, Security Evaluation, and More
A cyber security risk assessment isn’t just a problem-spotter– it’s a problem-solver. It offers a multitude of benefits that enhance your organization’s cyber security posture.
Vulnerability Remediation: The assessment produces a list of prioritized vulnerabilities that your organization can address to improve its cyber defenses. This is like having a personalized ‘to-do’ list for your IT team, guiding them on which security gaps to plug first.
Security Evaluation: The assessment offers valuable insight into the effectiveness of your current defenses. It’s like a report card for your cyber security measures, revealing which ones are performing well and which ones need improvement.
Cyber Security ROI: The assessment can demonstrate the returns on your cyber security investment in terms of reduced risk of cyber attacks. It’s a powerful tool for justifying your cyber security budget and showcasing its value to stakeholders.
Regulatory Compliance: Many regulations require regular security assessments to ensure proper protection of sensitive data. Even if it’s not required, an assessment can be a useful exercise to prepare for a compliance audit.
Insurance Coverage: Given the rise in cyber security risk, cyber security insurance has become more expensive and harder to obtain. A positive cyber risk assessment may improve your chances of obtaining a policy or reducing the cost of an existing one.
At Upper Echelon Technology Group, we believe that a robust cyber security risk assessment is an invaluable tool for any business navigating the choppy waters of cyber threats. Our personalized approach to IT Managed Services includes detailed and comprehensive risk assessments that help your business identify and fix security vulnerabilities. So, let us be your guiding light in the world of cyber security, helping you steer clear of hidden dangers and sail towards a safer future.
The Role of Managed Services Providers in Cyber Security Risk Assessments
In the vast seas of cyber threats, having a capable and reliable Managed Services Provider (MSP) by your side can be a game-changer. The right MSP can navigate your organization through these turbulent waters and ensure that your business remains safe and secure. This is where we, at Upper Echelon Technology Group, come into play.
How Upper Echelon Technology Group LLC Provides Personalized IT Managed Services
At Upper Echelon Technology Group, we don’t just offer a standard, one-size-fits-all solution. We believe in a personalized approach to IT Managed Services. Our team of experts is committed to understanding your business’s unique needs and tailoring our services to meet these requirements.
We understand that each organization faces unique cyber threats and has unique vulnerabilities. Therefore, we take the time to conduct a thorough cyber security threat and risk assessment for your organization. This assessment helps us understand your organization’s weak points and the specific threats you face. Armed with this information, we can then develop a comprehensive, personalized, and effective cyber security strategy for your business.
Our cyber security services are designed to protect your network 24x7x365, ensuring that your technology serves your business instead of causing headaches and hassles. This includes not only identifying and addressing risks but also continually monitoring your systems for any changes that might introduce new vulnerabilities.
Our commitment to you goes beyond merely “fixing tech issues”. We are dedicated to helping you leverage your technology assets in the best way possible to help your business. We aim to solve your technology issues, make your team more efficient, and identify areas where technology can improve your bottom line.
The Importance of a Personalized Approach to IT Services in Cyber Security
In the complex and ever-evolving world of cyber security, a personalized approach isn’t just a nice-to-have – it’s a must. Cyber threats are becoming increasingly sophisticated, and the “one size fits all” approach simply doesn’t cut it anymore.
Each organization has a unique risk profile, which means that the threats you face, the impacts they can have, and the measures you need to take to mitigate them are unique to your business. A personalized cyber security strategy takes all these factors into account, delivering a tailored solution that meets your specific needs.
By choosing Upper Echelon Technology Group as your MSP, you’re choosing a partner who understands the importance of personalization in cyber security. We are committed to providing services that are tailored to your specific needs and circumstances, ensuring that you have the most effective and efficient cyber security measures in place to protect your business.
As our expert, [insert expert’s name], often says, “In the world of cyber security, understanding your unique risks is the first step towards effective protection.” And that’s exactly what we do at Upper Echelon Technology Group. We strive to understand your unique risks and then work tirelessly to mitigate them.

Remember, in the realm of cyber security, the hidden dangers are always evolving. Your defenses must evolve too. With our personalized approach and commitment to understanding your unique risks, we can help your business stay one step ahead of the threats.
So, are you ready to take your cyber security to the next level? Let the experts at Upper Echelon Technology Group help you navigate the complex world of cyber threats and risk assessments. Together, we can ensure that your business remains safe and secure in the face of evolving cyber threats.
Regular Cyber Risk Assessments: Staying Ahead of Evolving Threats
In the ever-evolving digital landscape, one-time cyber threat and risk assessment is not enough. Like a well-oiled machine, your cyber defenses need regular maintenance and updates to stay ahead of the curve. This is where regular risk assessments come into play.
The Need for Regular Assessments
The world of technology and cyber threats is rapidly changing. New vulnerabilities are discovered every day, and cybercriminals are always on the prowl for the next potential loophole. At Upper Echelon Technology Group, we believe that to effectively manage and mitigate these risks, regular cyber security risk assessments are essential.
According to the National Institute of Standards and Technology (NIST) Cybersecurity Framework, regular risk assessments allow organizations to keep their risk profiles up-to-date. If there are changes to your computer networks or systems, it’s crucial to conduct a new risk assessment. This way, you can ensure that your defenses are always at their best, and your valuable data is protected.
The Comprehensive Assessment Process: Involving Stakeholders and Considering All Aspects
A comprehensive cyber threat and risk assessment is not a siloed task. It involves various stakeholders from within the organization and considers all aspects of your IT infrastructure.
Our expert at Upper Echelon Technology Group, emphasizes the importance of stakeholder involvement: “Risk assessment is a collective responsibility. It’s not just about IT personnel identifying and mitigating risks. It involves everyone from the boardroom to the break room. By involving all stakeholders, we ensure that all possible risks are identified and addressed.”
The assessment process includes evaluating the organization’s vulnerabilities, identifying internal and external threats, and prioritizing risk responses. It’s not just about identifying the risks; it’s about understanding the potential impact of each risk on the organization and determining the best course of action.
At Upper Echelon, we believe in a personalized approach to IT services. We understand that every organization has unique needs and challenges. That’s why we tailor our risk assessment process to your specific needs, taking into account your organization’s size, industry, and specific IT infrastructure.
Staying ahead of cyber threats is a continuous battle, but with regular risk assessments, you can ensure that your defenses are always ready. Remember, cyber security is not a destination, but a journey. As your trusted partner, Upper Echelon Technology Group is here to guide you every step of the way.
In the next section, we will wrap up our discussion on cyber security threat and risk assessment and provide key takeaways for proactively managing and reducing exposure to cyber threats.
Conclusion: Proactively Managing and Reducing Exposure to Cyber Threats
If there’s one thing we want you to take away from this discussion on cyber security threat and risk assessment, it’s this: proactivity is the key to effective cyber security. Gone are the days when businesses could afford to be reactive. In today’s fast-paced digital landscape, where threats evolve on a daily basis, a proactive approach to managing and reducing exposure to cyber threats is not just recommended—it’s crucial.
At Upper Echelon Technology Group, we believe that a cyber security risk assessment is not a one-off task but an ongoing process. It’s about continuously monitoring your digital landscape, identifying vulnerabilities, and taking immediate action to mitigate risks.
Our personalized approach to IT Managed Services goes beyond merely fixing tech issues. We are committed to understanding your business needs and leveraging technology to make your team more efficient and your company more profitable.
We offer a comprehensive suite of cyber security services that include continuous monitoring, vulnerability analysis, intrusion detection, and data leak prevention. We believe in a multi-layered security approach that combines technical controls, such as encryption, two-factor authentication, and automatic updates, with non-technical measures like security policies and physical mechanisms.
As one of our clients aptly put it on Quora, “Upper Echelon Technology Group doesn’t just solve our tech issues. They act as our strategic partner, helping us leverage technology to improve our bottom line.”

We understand that every business is unique, and so are its cyber security needs. That’s why we tailor our services to your specific requirements and budget. Remember, the cost of a data breach can far exceed the cost of prevention. As the saying goes, “An ounce of prevention is worth a pound of cure.”
In a world where cyber threats are becoming increasingly sophisticated, it’s essential to stay ahead. With Upper Echelon Technology Group by your side, you can have peace of mind knowing that your business is well-protected against evolving threats.
It’s time to change your mindset from “if I get impacted” to “how can I prevent an impact?”. Let’s embark on this journey together and ensure that your business is secure, efficient, and profitable.
Thank you for joining us in this insightful journey through the hidden dangers of cyber security threat and risk assessment. We hope that this knowledge empowers you to take proactive measures in managing and reducing your exposure to cyber threats.
Stay vigilant, stay proactive, and remember—we at Upper Echelon Technology Group are always here to help in your cyber security journey.