Introduction: The Importance of Risk Identification in Cyber Security
In the digital age, where businesses rely heavily on technology, cybersecurity is no longer a luxury but a necessity. A key aspect of this necessity is the process of risk identification in cyber security. As a business owner, your IT assets – from hardware and systems to customer data and intellectual property – are potential targets for cyber attacks. In fact, the lack of a robust cybersecurity strategy can result in dire consequences, such as compromised business operations, financial losses, and damage to your brand reputation.
One of the most essential steps in managing cybersecurity is identifying potential risks. This process is not as easy as it may seem. Cybersecurity is a constantly evolving field, making risk identification a moving target. However, a well-thought-out risk identification process can not only safeguard your IT assets but also optimize your technology to serve your business better.
In this article, we will take a deep dive into the world of cybersecurity risk identification, shedding light on its importance, the process involved, and how Upper Echelon Technology Group can help you manage and mitigate these risks effectively. As a cybersecurity-focused managed services provider, we believe in a personalized approach to IT managed services, addressing your specific business needs, making your team more efficient, and improving company profitability through technology.
Stay tuned to discover how to unveil the hidden threats in your IT ecosystem and secure your business in the face of ever-evolving cyber threats.
Understanding Cyber Security Risk Identification
Imagine trying to navigate through a dark room filled with tripwires. That’s how operating a business without understanding cyber security risk identification feels like. It’s a daunting task that can lead to drastic consequences if not handled properly. But fret not! We are here to shed light on this critical aspect of cyber security.
Defining Cyber Security Risk Identification
In the world of cyber security, risk identification is the process of recognizing and documenting potential threats that could compromise the integrity, availability, and confidentiality of your business’s digital assets. This risk identification process is the first step towards an effective cyber risk management strategy.
Cyber security risk identification is not a one-time event; it’s an ongoing process. The cyber landscape is as dynamic as it is dangerous, with new threats emerging regularly. However, the process’s fundamental elements remain the same: identify your assets, identify the threats to those assets, and identify your vulnerabilities to those threats.
The Role of Cyber Security Risk Identification in an Organization
The role of cyber security risk identification within an organization cannot be overstated. It’s like the radar on a ship, detecting incoming threats before they can cause damage.
Firstly, it provides a clear understanding of the organization’s digital landscape. It helps identify the critical digital assets, such as hardware, systems, customer data, and intellectual property, that need protection.
Secondly, it helps uncover potential threats and vulnerabilities. This involves identifying possible cyber attacks that could affect your assets and assessing their potential impact.
Most importantly, risk identification forms the foundation of a robust cyber risk management strategy. It informs the risk assessment process, guiding the development of mitigation measures, and helps in deciding what to do about the residual risk.
In essence, understanding cyber security risk identification is a crucial step in protecting your business, making your team more efficient, and leveraging technology to drive growth. Through a personalized approach to IT managed services, such as offered by Upper Echelon Technology Group, businesses can navigate the complex cyber landscape with confidence.
The Process of Risk Identification in Cyber Security
Intricate as a spider’s web, the process of risk identification in cyber security involves a series of interconnected steps that together form a comprehensive view of your organization’s cyber risk landscape. Let’s unravel this web to gain a deeper understanding of each critical step.
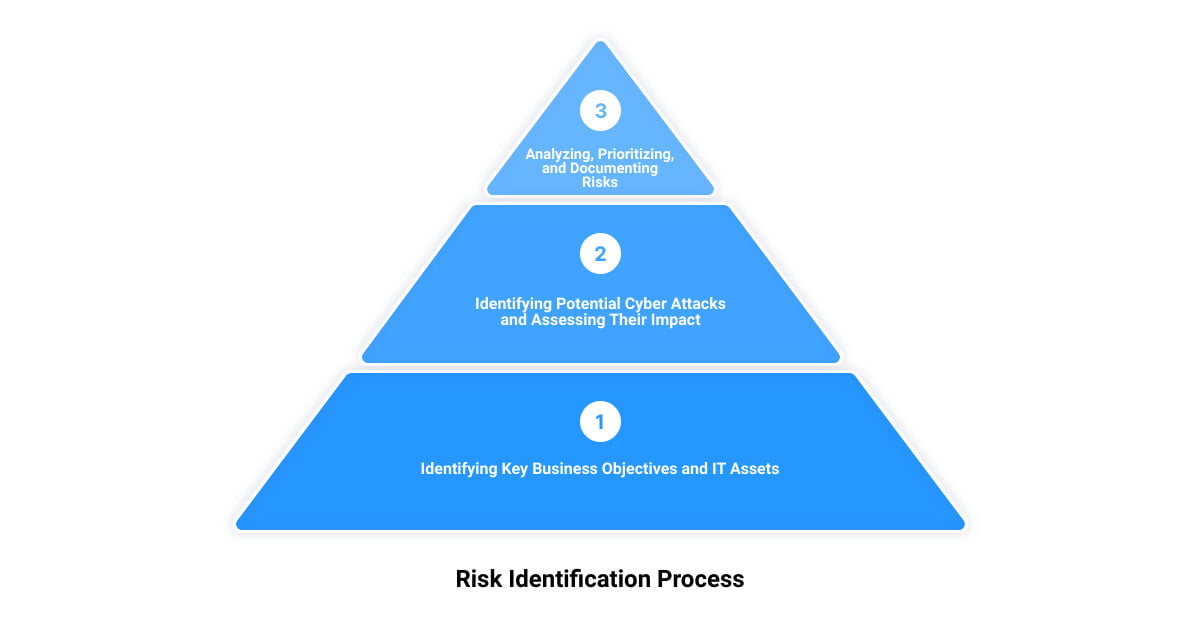
Identifying Key Business Objectives and IT Assets
The cornerstone of a robust cyber security risk identification process starts with understanding your business objectives and the IT assets that support them. Think of your IT assets as the lifeblood of your business operations – hardware, systems, laptops, customer data, and intellectual property. By cataloging these assets, it becomes possible to pinpoint the potential risks to your business operations and the potential impact of a cyber attack on these assets.
Identifying Potential Cyber Attacks and Assessing Their Impact
The next step is to identify potential cyber threats. This could range from ransomware attacks to data breaches and everything in between. Using various methods, such as automated scanning, auditing, penetration testing, vendor security advisories, and application security testing (AST) techniques, you can identify vulnerabilities within your IT assets.
The importance of this step is further underscored by the need to assess the potential impact of these cyber attacks. For instance, a ransomware infection on the corporate database could be devastating compared to a similar attack on a single user’s workstation. Therefore, identifying the potential impact of each cyber threat on your organization is key to quantifying the risk it poses.
Analyzing, Prioritizing, and Documenting Risks
Once the potential cyber threats have been identified and their impact assessed, the next step is to analyze these risks. This analysis should consider not only the technical flaws but also physical and process flaws. This comprehensive view helps in determining the likelihood of each type of attack and quantifying risk based on the combination of the likelihood and impact of each individual threat.
The final part of this step involves prioritizing and documenting the risks. By creating a prioritized list of these risks, your organization can focus its efforts on addressing the most significant risks first, thereby maximizing the ROI of your remediation efforts.
Implementing Mitigation Strategies
Last, but certainly not least, is the implementation of mitigation strategies. This is where the rubber meets the road. A well-executed mitigation strategy should be able to protect your IT assets and ultimately your business operations. This could involve setting up firewalls, installing anti-virus software, and conducting regular security audits, among other measures.
Through a managed IT service provider like the Upper Echelon Technology Group, you can leverage expert knowledge and resources to navigate these steps effectively. Their personalized approach to IT Managed Services can help you identify and mitigate cyber security risks, enabling your business to thrive in a hyper-connected world.
The NIST Approach to Cyber Security Risk Identification
As a business owner, you’re likely familiar with the constant onslaught of cyber threats that can jeopardize your operations. But, did you know there’s a systematic approach to identifying and managing these risks? Enter the National Institute of Standards and Technology (NIST), a federal agency that provides a comprehensive framework for risk identification in cyber security.
Overview of the NIST Risk Identification Process
The NIST risk identification process is built on the premise that understanding your organization’s vulnerabilities is the first step towards effective cyber security. This process involves regular tracking of changes to existing controls and security incidents, and reassessing the effectiveness of security controls. Essentially, NIST provides a structured way to identify and document the vulnerabilities associated with your organization’s IT assets.
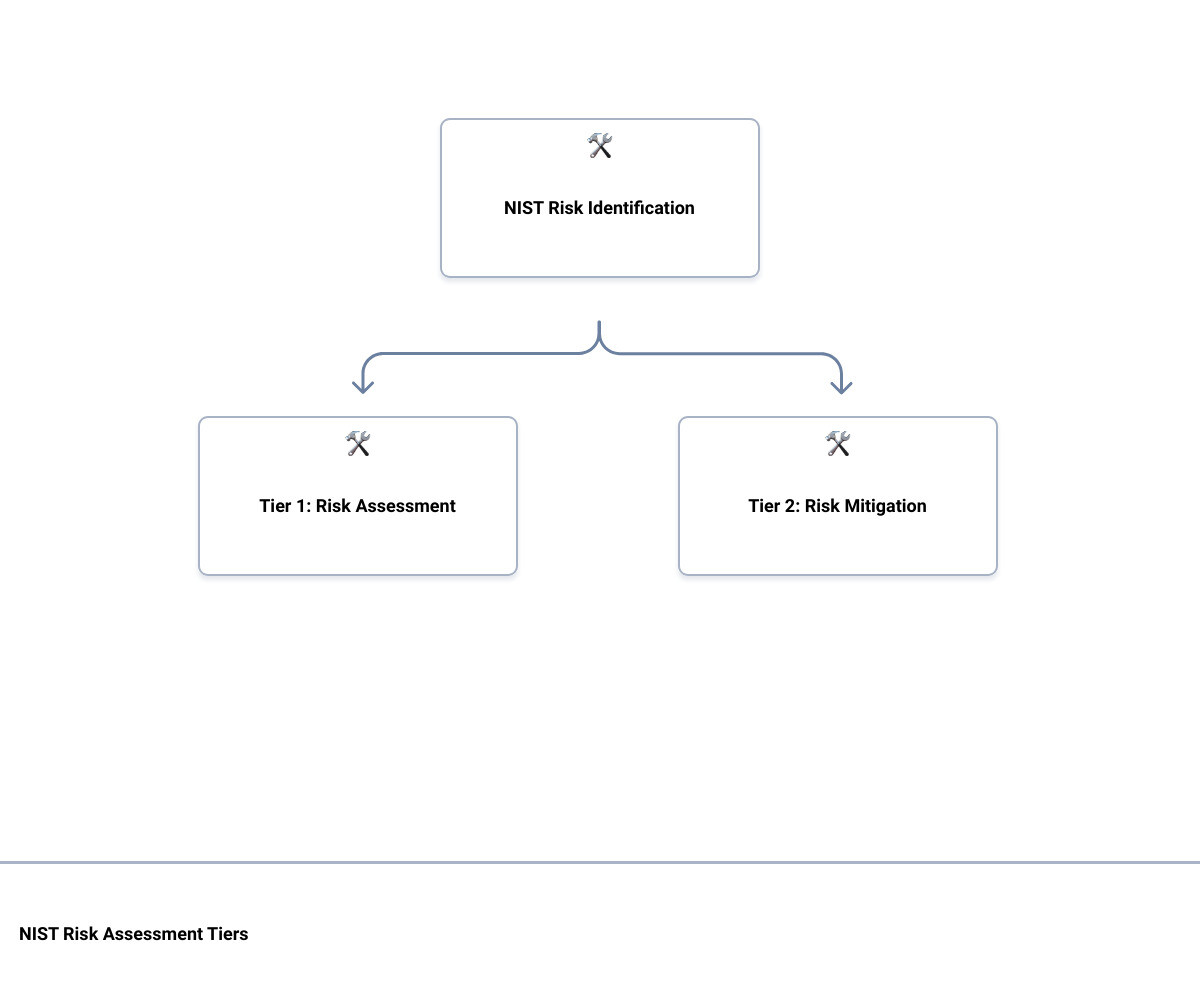
The Three Tiers of the NIST Risk Assessment
The NIST Risk Assessment is divided into three tiers. The first tier involves preparing for the assessment by understanding the IT assets that could be affected by a cyber attack. The second tier involves conducting the assessment, which includes identifying potential cyber threats, analyzing the risks, and determining their potential impact. The third and final tier involves notifying stakeholders of the results and maintaining ongoing assessments to ensure the continued effectiveness of your cyber security controls.
Steps to Conduct a NIST Risk Assessment
Conducting a NIST Risk Assessment consists of six crucial steps.
-
Identify and Document Network Asset Vulnerabilities: Begin by cataloging your IT assets and identifying the potential risks associated with each. This step involves both hardware and software components, as well as any customer data that may be at risk.
-
Identify and Use Sources of Cyber Threat Intelligence: Use internal and external sources to gather information on potential cyber threats. This data can help you identify the most significant risks to your organization.
-
Identify and Document Internal and External Threats: Scan your systems for indicators of compromise and audit configuration files for potential weaknesses or unauthorized changes.
-
Identify Potential Mission Impacts: Understand the potential impact of each threat to your organization. A ransomware infection on a corporate database, for instance, could have a more significant impact than a similar attack on an individual workstation.
-
Use Threats, Vulnerabilities, Likelihoods, and Impacts to Determine Risk: With a clear understanding of the threats and vulnerabilities your organization faces, you can quantify risk based on the likelihood and potential impact of each threat.
-
Identify and Prioritize Risk Responses: After quantifying the risk of each threat, you can prioritize your remediation efforts to address the most significant risks as quickly as possible.
In the ever-evolving landscape of cyber threats, adhering to the NIST approach to risk identification in cyber security can help you stay one step ahead of potential attacks. By partnering with a cybersecurity-focused managed services provider like Upper Echelon Technology Group, you can leverage their expertise to navigate the NIST Risk Assessment process effectively, thus ensuring the robustness of your cyber defenses.
The Five Steps to a Cyber Security Risk Assessment
Unraveling the complexities of cybersecurity starts with understanding how to conduct a comprehensive risk assessment. This process is a must-have for businesses that want to protect their digital assets and maintain their reputation. Let’s dive into the five-step journey to a thorough cybersecurity risk assessment.
Determining the Scope of the Risk Assessment
The first step to a successful cybersecurity risk assessment is to define its scope. This involves identifying the key business objectives and pinpointing the essential IT assets related to those objectives. The more precise your scope, the more effective your assessment will be.
Threat and Vulnerability Identification
The next step is to uncover potential threats and vulnerabilities. This process involves identifying potential cyber attacks that could affect your organization’s assets. It also includes scanning your systems for any existing vulnerabilities. It’s like turning on a flashlight in a dark room, you never know what you might find until you shine the light.
Analyzing Risks and Determining Potential Impact
Once you’ve identified potential threats and vulnerabilities, it’s time to analyze those risks and determine their potential impact. The objective here is to paint a complete picture of the threat environment for particular business objectives. The more detail you have, the better equipped you’ll be to manage these risks.
Determining and Prioritizing Risks
After analyzing the risks and their potential impact, your next step is to determine and prioritize those risks. This stage of the risk assessment process is crucial as it allows you to focus your resources on the risks that could cause the most damage to your organization. It’s like creating a roadmap that guides you on where to focus your efforts first.
Documenting All Risks
The final step in the risk assessment process is documenting all identified risks. This documentation will serve as a reference point for your team and stakeholders when making decisions about implementing security controls. It’s like having a playbook that outlines all the possible scenarios your team could face.
Navigating the complex landscape of cybersecurity risk identification does not have to be daunting. By following these five steps, you can create a comprehensive cybersecurity risk assessment that can help protect your organization from potential cyber threats. As a cybersecurity-focused managed services provider, Upper Echelon Technology Group LLC can offer you a personalized approach to IT Managed Services, guiding you through each of these steps to ensure robust cyber defenses for your business.
The Role of Upper Echelon Technology Group LLC in Cyber Security Risk Identification
The process of identifying cyber risks is a complex, ever-evolving task that requires expertise, vigilance, and a personalized approach. Enter Upper Echelon Technology Group LLC, a cybersecurity-focused managed services provider that prioritizes your business needs and ensures your technology serves your business, rather than the other way around.
Personalized IT Managed Services for Cyber Security
At Upper Echelon Technology Group LLC, we understand that every organization is unique, with its own set of assets, vulnerabilities, and potential threats. That’s why our Managed IT Services are not one-size-fits-all but are tailored to your specific needs and goals.
We offer personalized IT Managed Services that solve your technology issues, enhance team efficiency, and boost company profitability. Our team of experts continually evaluates the services and products we offer to our clients, ensuring your network is protected and optimized 24/7/365.
Tailored Approach to Risk Identification in Cyber Security
The first step in managing cyber risks is identifying them, and this is where Upper Echelon Technology Group LLC truly shines. We don’t just identify the risks; we delve deeper. We ask probing questions about the kind of data you store, who owns it, and what the potential consequences could be if something were to happen to this data.
Our approach to risk identification in cyber security follows a structured process of identifying your key business objectives and IT assets, identifying potential cyber attacks, assessing their impact, and then analyzing, prioritizing, and documenting these risks. This comprehensive risk identification process ensures that nothing is overlooked and that you have a full picture of your cyber risk landscape.
In the dynamic world of cyber security, risk identification is a moving target, but with Upper Echelon Technology Group LLC, you can be confident that you have a partner who will help you navigate the changing landscape and keep your business secure.
Conclusion: The Future of Risk Identification in Cyber Security
As we stare into the digital horizon, the importance of risk identification in cyber security only magnifies. The data-dense landscape we operate in today is fraught with potential threats, making it increasingly essential for businesses to have a robust and dynamic approach to identifying and managing cyber risks.
The future of cyber security risk identification will continue to revolve around the core principles of identifying assets, threats, vulnerabilities and the potential impact of these threats. However, the introduction of advanced technologies like AI and machine learning will revolutionize the way these risks are identified and assessed.
Predictive analytics, backed by machine learning algorithms, will provide businesses with the ability to foresee potential threats and vulnerabilities before they manifest, giving them the upper hand in risk management. Meanwhile, AI can bring speed and accuracy to the risk identification process, quickly scanning vast amounts of data to pinpoint potential risks.
As the cyber landscape continues to evolve, so too will the methods and tools for risk identification. The use of cybersecurity risk registers (CSRRs) and the principles of standards like the NIST Cybersecurity Framework will continue to serve as guides for businesses in their risk identification process.
Despite the advancement in technology, one thing remains clear – the human element in cyber security risk identification will always be crucial. Cyber security is not just about technology; it’s about people and processes. Training employees, fostering a culture of security, and implementing effective processes are all critical in maintaining a strong security posture.
At the intersection of technology and human elements, Upper Echelon Technology Group LLC stands as a beacon of personalized IT Managed Services. We understand that every business is unique, and so are its cyber risks. Our personalized approach to IT Managed Services ensures that we solve your technology issues, make your team more efficient, and improve company profitability through technology.
As we venture further into this digital age, remember that the future of your business’s security starts with risk identification. And with Upper Echelon Technology Group LLC by your side, you can be confident in a secure digital future.