In the era of digital acceleration, cyber threats are becoming more potent and damaging. Whether a startup, mid-sized, or multinational enterprise, every organization faces the crucial task of safeguarding its digital footprint. As a part of Upper Echelon Technology Group, one of the leading cybersecurity-focused managed service providers in Wilmington, DE, we often find that our clients’ prevalent inquiry revolves around understanding and implementing a robust Cyber Security Risk Assessment apparatus.
Would you want your business to fall victim to a cyber-attack, causing financial setbacks, reputational damage, or even more catastrophic consequences? Probably not. Conducting a cyber security risk assessment aids in identifying, evaluating, and mitigating risks in your network infrastructure. Moreover, it assists in fortifying your security posture against potential threats, essentially making the difference between digital resilience and vulnerability.
This Cyber Security Risk Assessment journey comprises several key stages. To guide you through this process and help boost your cybersecurity defenses, we’ve broken it into seven straightforward steps:
Z: Risk Assessment Steps
1. Scoping – Determining the Scope of the risk assessment
2. Risk Identification – Threat and vulnerability identification
3. Risk Analysis – Analyzing risks and determining potential impact
4. Risk Evaluation – Prioritizing risks
5. Documentation – Documenting all identified risks
6. Implementing Security Controls – Addressing the uncovered risks
7. Ongoing Assessment – Ensuring continuous risk assessments
However, the importance of each step cannot be overstated, and each brings you closer to achieving optimal digital resilience.
Dive in as we unravel the comprehensive details of each stage, aiming to make the intimidating process of carrying out a thorough cyber security risk assessment feel within reach.
Stay tuned as we let you in on the winning strategies for security risk assessment, backed up by our expert team’s experiences and industry-standard practices from the National Institute of Standards and Technology (NIST) Framework and more.
Understanding Cyber Security Risk Assessment: Definition and Purpose
In the digital age, where online threats lurk at every corner, a cybersecurity risk assessment serves as a knight in shining armor. But what exactly does this entail? A cybersecurity risk assessment is an essential process that helps an organization identify, understand, and prioritize potential threats to its digital assets. These assets could range from customer data, employee records, and financial information, to the digital infrastructure itself.
The main purpose of a cybersecurity risk assessment is not just to ward off nasty cyber threats. It also serves to inform stakeholders and support appropriate responses to the identified risks. By doing so, it provides a valuable executive summary, helping business leaders make informed decisions about investing in security measures.
The process revolves around several crucial questions, such as:
- What are our organization’s most important information technology assets?
- What type of data breach would significantly impact our business?
- Can we identify all possible threat sources?
- What are the potential impacts of each identified threat?
- What are the internal and external vulnerabilities?
- What would be the impact if these vulnerabilities are exploited, and what is the likelihood of such exploitation?
- What cyber threats or security incidents could affect our ability to operate?
- What level of risk are we comfortable taking?
Answering these questions enables us to recognize what needs protecting, which in turn allows us to develop IT security controls and data security strategies for risk remediation.
Importantly, the cybersecurity risk assessment is not a one-off event—it’s a continuous process that evolves with your business and the ever-changing landscape of cyber threats.
Here at Upper Echelon Technology Group, we have a personalized approach to IT Managed Services that ensures a comprehensive cybersecurity risk assessment tailored to your unique business needs. Our focus is not only on resolving tech issues but also on leveraging your technology assets in the best way possible to bolster your business against cyber threats.
In the next sections, we’ll delve deeper into the seven steps of a cybersecurity risk assessment, offering valuable insights to ensure your business’s digital resilience.
Step 1: Scoping – Determining the Scope of the Risk Assessment
Stepping into the world of cybersecurity risk assessment, the first stride we at Upper Echelon Technology Group take is to define the scope. This crucial step helps us understand the breadth and depth of the assessment. The scope can encompass your entire organization or zoom into specific business units, locations, or components such as payment processing systems.
The initial phase of the risk assessment process involves gathering all relevant stakeholders, especially those whose activities fall within the scope of the assessment. Their input is invaluable in identifying the relevant processes and assets, pinpointing risks, assessing impacts, and defining the organization’s risk tolerance levels. As one Reddit user shared, they found themselves “lacking risk assessment skills” and questioned where they could learn more about this vital field. The answer lies in understanding the steps of a risk assessment, starting with scoping.
It’s essential, at this stage, for all parties involved in the assessment process to be familiar with the relevant terminology, such as likelihood and impact. This understanding helps standardize risk and ensure accurate communication. We also recommend that organizations review frameworks like NIST SP 800-37 and standards like ISO/IEC 27001 for guidance and clarity on effective security controls.
At Upper Echelon Technology Group, we understand that every business is unique. Therefore, we personalize the scope of the risk assessment to fit your specific needs, making sure to consider your unique business model, industry requirements, and specific technology assets. Our goal is to help you leverage your technology in the best way possible to bolster your business against cyber threats.
In the next section, we’ll explore how to identify threats and vulnerabilities within the defined scope. By understanding the potential risks, we can better prepare for them, ensuring that your business remains secure and resilient.
Step 2: Risk Identification – Threat and Vulnerability Identification
Embarking on the second phase of our cybersecurity risk assessment journey, let’s uncover the hidden threats lurking in your digital landscape and identify possible vulnerabilities that could be exploited. This step is critical in creating a robust defense against cyber attacks, allowing us to be proactive rather than reactive.
Identifying Assets
The first step in this phase involves identifying all the assets within your organization. Essentially, we need to know what we are protecting. Your assets include everything from your physical hardware and software to your data and network infrastructure. Notably, we don’t just focus on your most valuable assets (or ‘crown jewels’), but also on those that attackers may want to take control over, such as an Active Directory server or picture archive, which can be used as a pivot point to expand an attack.
At Upper Echelon Technology Group, we create a comprehensive inventory of all your assets, ensuring nothing is overlooked. We then generate a network architecture diagram to visualize the interconnectivity and communication paths between assets and processes, as well as entry points into the network. This makes the task of identifying threats easier.
Identifying Threats
Once we have a clear understanding of what we’re protecting, we can begin identifying potential threats. Threats come in many forms and can be anything from malware and phishing attacks to insider threats and data breaches.
To help identify potential threats, we use resources like the MITRE ATT&CK Knowledge Base and the Cyber Threat Alliance. These resources provide high-quality, up-to-date cyber threat information, ensuring we’re always one step ahead of the attackers.
Identifying Vulnerabilities
Vulnerabilities are weaknesses in your systems that could be exploited by threats. This could be anything from outdated software, weak passwords, or unprotected data.
Identifying these vulnerabilities is a vital part of the risk assessment process. It allows us to understand where our defenses may be lacking and what areas need to be strengthened to prevent potential breaches.
At Upper Echelon Technology Group, we conduct a thorough examination of your systems, using best practices and guidelines from various standards and laws such as HIPAA, Sarbanes-Oxley, and PCI DSS.
Connecting the Dots
Finally, we connect the dots between the assets, threats, and vulnerabilities. By understanding the relationship between these elements, we can create scenarios that help everyone in the organization understand the risks they face in relation to key business objectives. These scenarios also guide our team in identifying appropriate measures and best practices to address the risk.
For example, a threat could be an attacker performing an SQL injection on an unpatched web server (vulnerability), resulting in customers’ private data being stolen (asset). The consequence of this could be regulatory fines and damage to your reputation.
As your cybersecurity partner, we make sure each step of this identification process is conducted thoroughly, ensuring no stone is left unturned in our quest to bolster your digital defenses.
In the next section, we will delve into the analysis of these risks and how we determine their potential impact on your business. Stay tuned as we continue unfolding the cybersecurity risk assessment journey.
Step 3: Risk Analysis – Analyzing Risks and Determining Potential Impact
After successfully identifying threats and vulnerabilities in the previous step, it’s time to set sail on the vast ocean of risk analysis. At Upper Echelon Technology Group, we understand the criticality of this step in the cybersecurity risk assessment process. In the risk analysis phase, we dissect each identified risk scenario to determine how they can potentially impact your business operations, reputation, and bottom line.
Determining the Potential Impact
In the world of cybersecurity, potential risk is the probability that a specific threat will exploit a vulnerability. This probability is primarily based on several factors such as:
- Discoverability of the security weakness
- Ease of exploitability
- Reproducibility of threats (some threats are one-time, and some are continuous)
- Prevalence of the threat in the industry or similar companies
- Historical security incidents
It’s essential to understand that each risk comes with its unique impact level. For instance, a cyber threat that exploits a vulnerability in your customer database might have a more significant impact compared to a threat that targets less critical components of your business.
The Role of Expertise
Analyzing risks and determining their potential impact is not a task for the faint-hearted. It requires a deep understanding of both your business operations and the cyber threat landscape. At Upper Echelon Technology Group, our team of seasoned cybersecurity experts leverages their vast knowledge and experience to provide an accurate risk analysis. We take the time to understand your business needs, your technology assets, and how they align to give you the best possible protection.
Importance of Risk Analysis
Risk analysis is a pivotal step in the risk assessment process as it shapes the subsequent steps of risk evaluation and mitigation. It allows us to prioritize the risks based on their potential impact and helps us create a robust plan for risk control. Without a thorough risk analysis, your business might end up focusing on less impactful risks and overlooking the ones that can cause significant damage.
In the next section, we will be discussing how we prioritize these risks based on the analysis conducted in this step. Stay tuned as we continue to navigate the turbulent waters of cybersecurity risk assessment.
Step 4: Risk Evaluation – Prioritizing Risks
In the realm of cybersecurity, not all risks are created equal. Just as a captain navigates a ship away from the biggest storm, in our role as your cybersecurity-focused managed services provider, we at Upper Echelon Technology Group guide you in identifying and addressing the most significant risks first. Prioritizing risks is a crucial part of the cybersecurity risk assessment journey, and it requires a structured approach to ensure no critical threat is overlooked.
The Power of the Risk Matrix
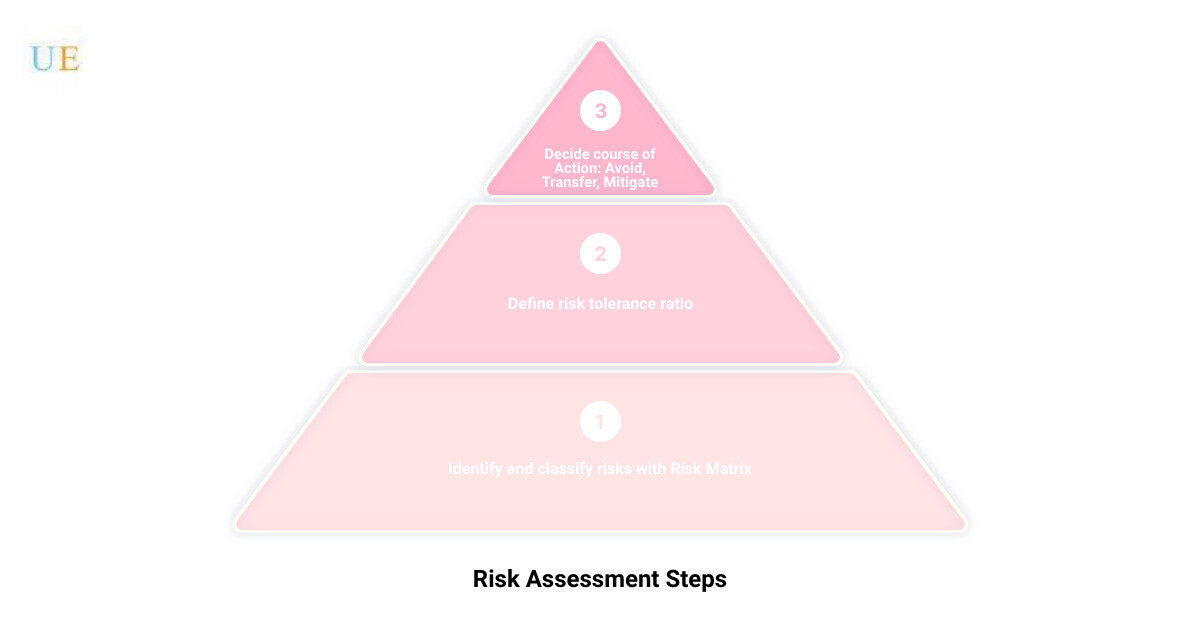
To chart the course and navigate the sea of potential threats, we employ a tool known as a risk matrix. A risk matrix is a visual representation that helps classify each risk scenario based on its likelihood and potential impact. It’s like a compass guiding you on where to focus your resources and attention.
The risk matrix helps us define your organization’s risk tolerance ratio, a measure of the level of risk your organization is willing or able to accept. This ratio helps us determine which threat scenarios exceed your threshold and require immediate attention.
Deciding Your Course of Action: Avoid, Transfer or Mitigate
Based on the risk matrix, we can determine the best course of action for each identified risk. This could be one of three options:
- Avoid: If the risk is low and managing it isn’t cost-effective, it may be best to avoid it. For instance, if a specific software is prone to vulnerabilities and the cost of mitigating this is higher than replacing it, the best course of action might be to avoid this software.
- Transfer: If the risk is significant but difficult to address internally, it’s possible to share the risk by transferring responsibility to a third party. This is typically achieved through cyber insurance or contracting an outsourced security service.
- Mitigate: Risks that are significant and within our operational scope should be mitigated. This is achieved by deploying security controls and measures to reduce their likelihood and potential impact.
It’s important to note that any risk assessment program must recognize that there is a certain level of residual risk that will be missed, or will not be fully addressed. This must be formally accepted by senior stakeholders as part of your organization’s cybersecurity strategy.
Your Trusted Partner in Risk Evaluation
At Upper Echelon Technology Group, we understand the importance of identifying and prioritizing risks that could potentially harm your business. Our team of experienced professionals is committed to helping you navigate the dynamic landscape of cybersecurity threats, ensuring your business remains resilient in the face of cyber threats.
In the next step of our cybersecurity risk assessment journey, we’ll discuss the importance of documenting all identified risks. This is a crucial phase that ensures transparency and accountability throughout the process. Stay tuned as we continue to help you sail through the tumultuous waters of cybersecurity risk assessment.
Step 5: Documentation – Recording All Risks
Every voyage needs a map, and every cybersecurity risk assessment needs a risk register. This is the ‘map’ that we use to document all identified risks in your business’ digital landscape. We believe that a well-documented risk register is a cornerstone in the foundation of an effective cybersecurity plan. It’s not just about identifying risks; it’s about understanding them, planning for them, and tracking their status over time.
In our approach at Upper Echelon Technology Group, we ensure that the risk register is regularly reviewed and updated, giving you an accurate understanding of your cybersecurity landscape at all times. This document becomes a crucial tool in managing and mitigating risks, creating a safer digital environment for your business.
What’s Included in the Risk Register?
The risk register is a comprehensive document that details various aspects of each identified risk. It includes:
- Risk scenario: The situation that could lead to a cybersecurity breach or issue.
- Identification date: When the risk was first identified.
- Existing security controls: What measures are already in place to mitigate this risk.
- Current risk level: How severe the risk is at the moment.
- Treatment plan: The planned activities and timeline to reduce the risk to an acceptable level.
- Progress status: How far along we are in implementing the treatment plan.
- Residual risk: The risk level after the treatment plan has been implemented.
- Risk owner: The individual or group within our team responsible for ensuring the residual risks remain within the tolerance level.
Why is Documentation Important?
Think of the risk register as a living document that grows and changes as your business does. It’s a snapshot of your current cybersecurity risk landscape, but it’s also a historical record. Over time, it can show you trends, improvements, and areas that need more attention.
Moreover, this level of documentation ensures transparency and accountability in our cybersecurity risk assessment process. It acts as a communication tool that keeps all stakeholders informed about the state of cybersecurity risks in your business.
When it comes to cybersecurity, knowledge is power. The more you understand about your risks, the better prepared you are to face them. And we at Upper Echelon Technology Group are here to guide you through this process, every step of the way.
In the next step of our Cyber Security Risk Assessment journey, we will discuss the implementation of security controls to mitigate identified risks. A crucial step to ensure your business’s digital resilience. Stay with us as we continue to navigate the complex waters of cybersecurity risk assessment.
Step 6: Implementing Security Controls – Mitigating Identified Risks
After the thorough documentation of all identified risks, the next key step in the cybersecurity risk assessment journey is the implementation of security controls to mitigate these risks. This is where we at Upper Echelon Technology Group shine, using our cybersecurity expertise to fortify your business’s digital defenses and ensure resilience against potential cyber threats.
The Role of Security Controls
Security controls are safeguards that are strategically put in place to minimize or eliminate the probability of a threat or vulnerability exploiting your digital assets. They can be implemented through technical means such as hardware or software, encryption, intrusion detection mechanisms, two-factor authentication, automatic updates, and continuous data leak detection. Non-technical means can also be employed, such as security policies and physical mechanisms like locks or keycard access.
Security controls can be classified into two categories: preventative and detective controls. Preventative controls are proactive measures designed to stop attacks in their tracks. These include encryption, firewalls, antivirus software, and continuous security monitoring. Detective controls, on the other hand, are reactive measures that aim to discover when a breach has occurred, such as continuous data exposure detection.
The primary goal of implementing these controls is to reduce the likelihood of risk occurrence and minimize its impact should it happen.
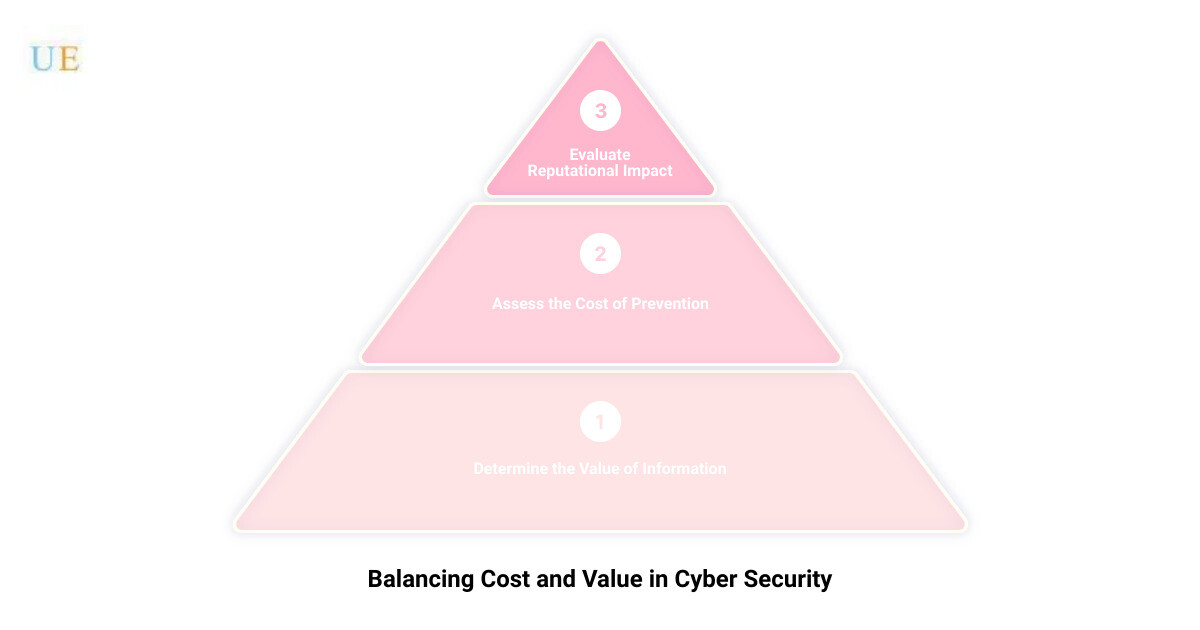
Balancing Cost and Value
As you implement these security controls, it’s essential to prioritize risks based on the cost of prevention versus the value of the information that needs protecting. This approach helps to ensure that resources are allocated efficiently and effectively. For instance, if the cost of protecting an asset is higher than its value, it may not make sense to use preventative control. However, it’s also crucial to remember that a data breach could have a reputational impact, not just a financial one, and this must be factored into the equation.
At Upper Echelon Technology Group, we understand the unique needs of each business. We balance organizational policies, potential reputational damage, feasibility, regulations, effectiveness of controls, safety, reliability, and the company’s attitude toward risk to create a tailored approach to security control implementation.
Continuous Improvement
As the digital landscape continually evolves, so do the threats that businesses face. As such, implementing security controls is not a one-time task, but a continuous process that requires regular review and updates. Security controls must be assessed and adjusted as necessary to ensure their continued effectiveness.
By following these steps and working with a trusted partner like Upper Echelon Technology Group, you can ensure that your business is well-protected from the ever-present threat of cyber-attacks. In the next section, we will discuss the importance of ongoing assessment in maintaining continuous risk assessments. Join us as we continue to unravel the journey of cybersecurity risk assessment to ensure the digital resilience of your business.
Step 7: Ongoing Assessment – Maintaining Continuous Risk Assessments
In a world where cyber threats evolve rapidly, a one-time risk assessment is not enough. The journey towards digital resilience is ongoing and requires continuous maintenance of cybersecurity risk assessments. At Upper Echelon Technology Group, we believe that vigilance is the key to staying a step ahead of cyber threats.
The Rationale Behind Continuous Risk Assessment
The digital landscape is continually evolving, with new technologies, processes, and threats emerging every day. To keep pace with these changes, your risk assessment process should be ongoing. This continuous approach ensures that your organization’s risk profile is up-to-date and reflects the current threat landscape.
Continuous risk assessment involves regularly reviewing and updating your risk assessments, ensuring that you are aware of any new vulnerabilities or threats that might impact your organization. This process allows you to make timely decisions and take proactive steps to mitigate risks before they can cause significant damage.
How We Facilitate Continuous Risk Assessments
At Upper Echelon Technology Group, our expert team continuously monitors the cyber landscape. We keep abreast of the latest security trends, threat intelligence, and industry best practices. This vigilance enables us to update your risk assessments regularly and adjust your security measures accordingly.
Our ongoing risk assessments involve:
- Regularly reviewing and updating the scope of the risk assessment.
- Continuously identifying new threats and vulnerabilities.
- Analyzing and determining the potential impact of new risks.
- Evaluating and prioritizing new risks.
- Regularly updating our risk documentation.
- Implementing new security controls as required.
- Constantly monitoring the effectiveness of implemented controls.
This iterative process ensures that your organization’s risk posture is always up-to-date, giving you peace of mind and letting you focus on your core business operations.
Embracing a Culture of Continuous Risk Assessment
A successful continuous risk assessment process requires more than just technical expertise; it also needs a cultural shift within the organization. All stakeholders, from top management to operational staff, should understand the importance of continuous risk assessment and be committed to its implementation.
In conclusion, continuous risk assessments are a vital part of maintaining your organization’s cybersecurity posture. They allow you to stay ahead of the ever-evolving threat landscape and ensure that your defenses are always up to the task. At Upper Echelon Technology Group, we’re here to guide you on this ongoing journey towards digital resilience, ensuring that your business is always protected, efficient, and profitable.
The Role of Managed Services Providers in Cyber Security Risk Assessment
In our digital era, managing cybersecurity is no longer a luxury but a necessity for businesses of all sizes. The complexity of this task, however, can be daunting, especially for small to medium-sized businesses without a dedicated in-house IT team. This is where managed services providers like us at Upper Echelon Technology Group come into play.
As a cybersecurity-focused managed services provider, we provide a comprehensive and personalized approach to cybersecurity risk assessments. Our team, equipped with extensive knowledge of digital and network infrastructure, is well-positioned to provide a thorough assessment of your security posture.
We Understand Your Business
Our approach goes beyond simply fixing tech issues. We focus on understanding your business needs and how to leverage your technology assets in the most efficient and secure way possible to help your business thrive. By understanding your operations, we can better identify potential threats and vulnerabilities that may impact your business.
Comprehensive Risk Assessments
We conduct a broad analysis of your organization that includes facility analysis, server analysis, network analysis, data security analysis, and evaluation of company policies. We also perform a third-party security analysis for each entity that has access to your company’s systems. This methodical approach ensures no stone is left unturned, providing you with a comprehensive view of your security risks.
Risk Management and Mitigation
After identifying and analyzing risks, we prioritize them based on their potential impact on your business. We then propose specific technical recommendations for mitigating these risks, from firewall configurations to network scanning. Our risk management process is an ongoing effort, with regular identification and mitigation of risks to continually improve your security posture.
Ensuring Continuous Security
We believe in the importance of continuous assessment to ensure your business’s digital resilience. As threat landscapes evolve, so should your security measures. We regularly monitor your security status, addressing and mitigating risks as they emerge. This approach ensures that your technology serves your business, rather than your business serving your technology.
In conclusion, managed services providers like Upper Echelon Technology Group play a pivotal role in cybersecurity risk assessments. We provide you with a comprehensive, personalized, and continuous approach to managing and mitigating your cybersecurity risks, allowing you to focus on what matters most – running and growing your business.
Conclusion: Ensuring Digital Resilience Through Effective Cyber Security Risk Assessment
In the ever-evolving digital landscape, ensuring the resilience of your business against cyber threats is not an option but a necessity. We, at Upper Echelon Technology Group, firmly believe that a well-executed cybersecurity risk assessment is a critical component in your organization’s defense strategy.
Through the seven-step risk assessment journey we’ve outlined, you’ve gained insight into the comprehensive approach required to effectively identify, analyze, evaluate, and mitigate cyber risks. From the initial scoping stage to the ongoing assessments, each step plays a crucial role in fortifying your digital infrastructure against potential cyber threats.
The reality is, cybersecurity is not a one-time fix but a continuous process. This is where managed services providers like us come into play. We ensure that your network is protected and optimized 24x7x365, serving your business needs instead of you serving your technology.
Our cybersecurity risk assessment process is designed to provide repeatable, scalable, and sustainable solutions that improve over time as we address the risks discovered in the assessment responses. The goal is not just to protect your business against current threats, but also to prepare it for future ones. This proactive approach is the key to ensuring your business’s digital resilience in the face of evolving cyber threats.
Remember, a resilient business is not just about having the right technology in place, but also about having a culture of cybersecurity awareness. By understanding the importance of cybersecurity and making it a priority, you can significantly reduce your business’s risk of falling victim to a cyber attack.
At Upper Echelon Technology Group, we strive to empower businesses, like yours, through our managed IT services. We solve your technology issues, make your team more efficient by leveraging technology, and make your company more profitable by identifying areas where technology can improve your bottom line.
In conclusion, as we navigate the digital age, cybersecurity risk assessments are no longer an option but a necessity. It’s time to take your cybersecurity measures to the next level. Let’s ensure the digital resilience of your business together.
Remember, in the world of cybersecurity, prevention is always better than cure.
Are you ready to take the next step in ensuring your business’s digital resilience? Contact us today to learn more about our cybersecurity services and how we can help you stay ahead of cyber threats.