Cybersecurity is not a ‘set and forget’ concept. In a constantly evolving digital landscape, the risk assessment process in cybersecurity is a crucial piece in protecting your organization’s valuable assets. This is especially true for small to medium-scale businesses like yours, operating in the heart of Wilmington, DE. Coming from a personalized approach to IT Managed Services, we at Upper Echelon Technology Group understand the importance of continually reassessing, redefining, and proactively addressing potential threats.
In fact, many organizations underestimate the profound impact that a single cybersecurity breach can have on their operations. We’ve seen businesses crippled by such incidents, often due to a lack of effective risk identification, analysis, and mitigation strategies. Today, we aim to unveil the complex maze of cybersecurity and guide you in adopting a revolutionary risk assessment process.
To give you a snapshot of what is involved a cyber security risk assessment typically comprises of the following crucial steps:
- Asset Mapping: Identifying and categorizing all existing assets, such as systems, data, and services.
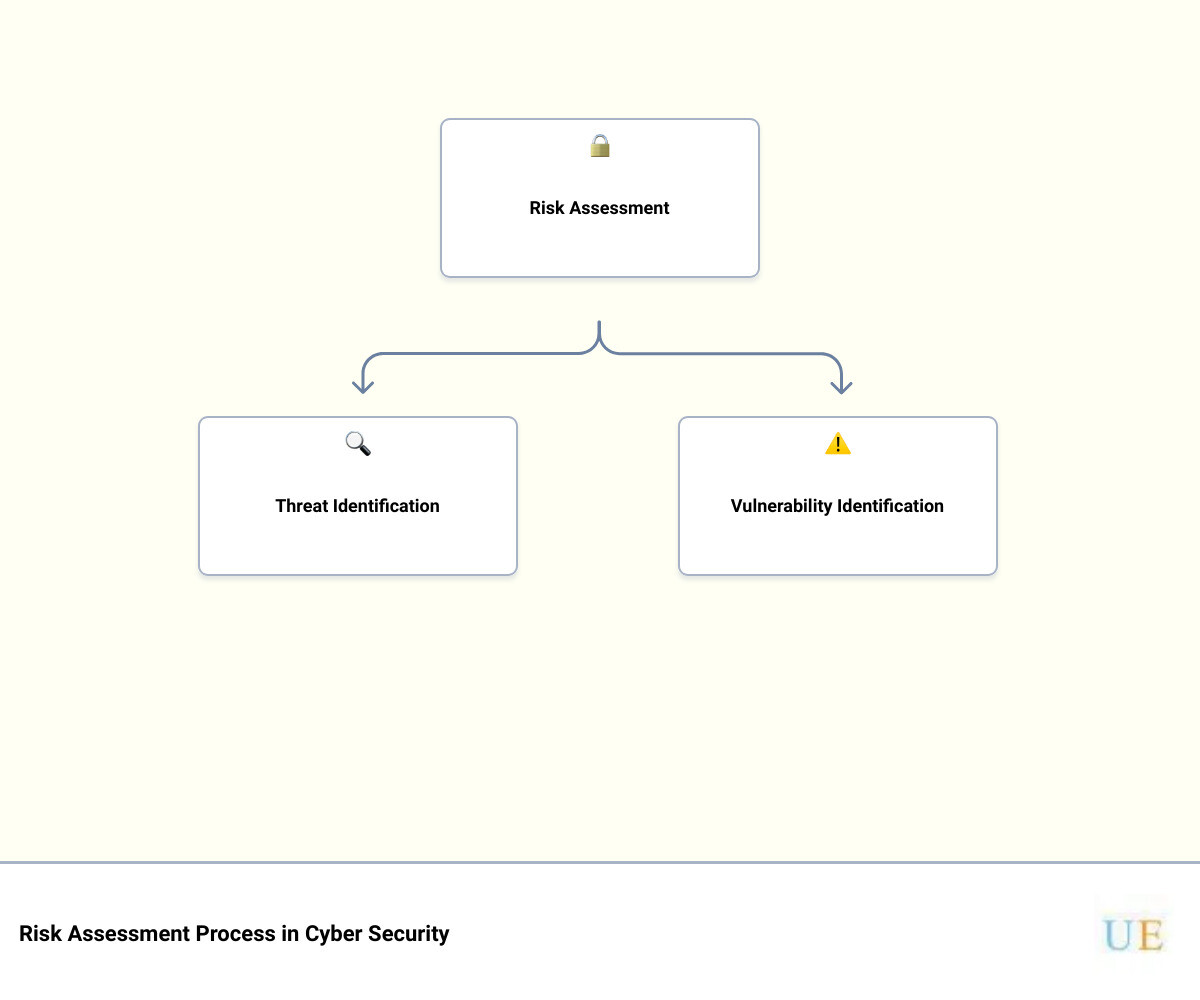
- Threat Identification: Listing any potential threats to those assets, which could be from internal or external sources.
- Vulnerability Identification: Identifying any potential weaknesses that could be exploited by the threats.
- Risk Determination: Prioritizing the identified risks based on their potential impact and likelihood of occurrence.
- Control Analysis: Establishing the most suitable controls to prevent, mitigate, or eliminate the risks.
Detailed in this article is a comprehensive guide on each of these steps and how they should be implemented effectively in the context of your own organization.
This infographic provides a simple illustration of the five-step cybersecurity risk assessment process, designed to ensure an effective, efficient and secure cyber environment for your business. Navigating each of these steps strategically is key to protecting your business from potential threats and we are here to guide you all through it. Stay tuned for a detailed dissection of each of these steps along with helpful insights from our own experiences at Upper Echelon Technology Group.
Understanding the Importance of Cyber Security Risk Assessment
In the digital age, the importance of a cyber security risk assessment cannot be overstated. Whether you’re a small owner-operated business or a growing multinational, your digital assets and operations are exposed to a myriad of potential threats. As we at Upper Echelon Technology Group have experienced, understanding these threats and preparing for them is not just a smart business move, it’s a necessity.
Protecting Information and Information Systems
The heart of any business lies in its data. From customer details and intellectual property to financial records, the information stored in your systems is of immense value. A cyber security risk assessment helps identify and protect these assets. It outlines potential vulnerabilities and threats that could compromise your data, enabling you to put in place the right controls to mitigate these risks.
Preventing Security Incidents and Data Breaches
A critical role of a risk assessment is to prevent security incidents and data breaches. An effective cyber security risk assessment identifies potential cyber attacks that could harm your hardware, systems, and data. By evaluating these risks, you can make informed decisions on which security measures to implement, reducing the likelihood of a breach and the potential damage to your business.
Ensuring Compliance with Regulations
In today’s regulatory landscape, businesses are required to meet a variety of compliance standards, including the GDPR (General Data Protection Regulation). Non-compliance can result in hefty fines and reputational damage. A cyber security risk assessment ensures your business adheres to these standards. For instance, clause 6.1.2 of the ISO 27001 standard requires businesses to conduct regular risk assessments and demonstrate documented evidence of this process.
Encouraging a Risk-Aware Culture
Lastly, a cyber security risk assessment fosters a risk-aware culture within your organization. It’s not just about the technology; it’s about the people too. By involving your team in the risk assessment process, they become more aware of cyber threats and the importance of their role in protecting your business.
At Upper Echelon Technology Group, we believe in the power of a risk-aware culture. We understand that every team member plays a critical role in our collective cyber security. This is why we not only focus on tech issues but also on empowering your team to leverage technology effectively and safely.
In the next section, we will delve into the five-step cyber security risk assessment process to help you better understand what it entails.
The Five-Step Cyber Security Risk Assessment Process
Unraveling the threads of the cyber security maze begins with a structured approach. As experts in the field, we at Upper Echelon Technology Group, have developed a five-step process to conduct a comprehensive cyber security risk assessment. This process, while rigorous and meticulous, is designed to provide a clear understanding of potential risks and formulate effective strategies to mitigate them.
Scoping: Determining the Scope of the Assessment
The first step in any cyber security risk assessment process is defining its scope. This could include the entire organization or specific business units, locations, or aspects of the business, such as payment processing or a web application. The scope depends largely on your business needs and requirements. We understand the importance of stakeholder support and engagement in this exercise, as their input is crucial in identifying the most important assets and processes, potential risks, and defining risk tolerance levels.
Risk Identification: Creating an Inventory of Assets and Identifying Threats
This step involves creating an inventory of critical IT assets and identifying potential threats to these assets. The aim is to understand the cyber attacks that could adversely affect your business operations and objectives. At Upper Echelon Technology Group, we utilize our deep knowledge and industry experience to identify and categorize potential threats to your cyber security environment.
Risk Analysis: Assessing the Likelihood and Impact of Risks
Once potential threats have been identified, we step into the risk analysis phase. This involves assessing the likelihood of a cyber attack and its potential impact on your business. A complete picture of the threat environment is crucial for making informed decisions about the implementation of security controls. We take into account various factors, such as the vulnerability of the asset, the capability of the threat, and the potential impact of a successful attack.
Risk Evaluation: Prioritizing Risks and Selecting Treatment Options
In the risk evaluation phase, we prioritize the identified risks based on their potential impact and likelihood of occurrence. This helps in selecting appropriate treatment options. We believe in striking a balance between risk reduction and cost-effectiveness, ensuring that the overall risk is reduced to a level that your organization is comfortable with.
Documentation: Maintaining a Risk Register and Tracking Progress
The final step in the risk assessment process is documentation. We maintain a risk register that records all the identified risks, their ranking, and the selected treatment options. This document serves as a useful tool for tracking progress and for future reference. It also provides a clear audit trail for compliance purposes.
In essence, the five-step cyber security risk assessment process is a thorough and systematic approach to understanding and managing cyber risks. At Upper Echelon Technology Group, we guide you through each step, ensuring a comprehensive and effective risk assessment tailored to your unique business context.
An infographic showing the five-step cybersecurity risk assessment process: Scoping, Risk Identification, Risk Analysis, Risk Evaluation, and Documentation.
The Role of Automation in Cyber Security Risk Assessment
Automating the cyber security risk assessment process is not just a matter of convenience – it’s a strategic move that can greatly enhance the accuracy and efficiency of your risk management efforts. At Upper Echelon Technology Group, we understand the importance of this automation and how it can revolutionize your approach to managing cyber risk.
Saving Time and Reducing Errors
Traditionally, companies relied heavily on manual processes and spreadsheets to manage their risk assessment, a time-consuming and error-prone method. By automating this process, you can save significant time and reduce the chance of errors creeping into your risk assessments. Automated systems streamline the process of collecting, organizing, and analyzing data, ensuring consistency and accuracy.
Generating Reports and Providing a Comprehensive View of Security Posture
One of the most significant advantages of automation is the ease of report generation. Instead of spending hours compiling data and formatting spreadsheets, your team can generate comprehensive reports with just a few clicks. This not only saves time but also minimizes the risk of errors in the reporting process.
Moreover, automation allows for the integration of data from multiple sources, such as threat intelligence feeds, vulnerability scanners, and other security tools. This integration provides you with a more comprehensive view of your security posture, allowing you to identify potential risks more easily.
Staying Up-to-Date with Changing Security Threats and Compliance Requirements
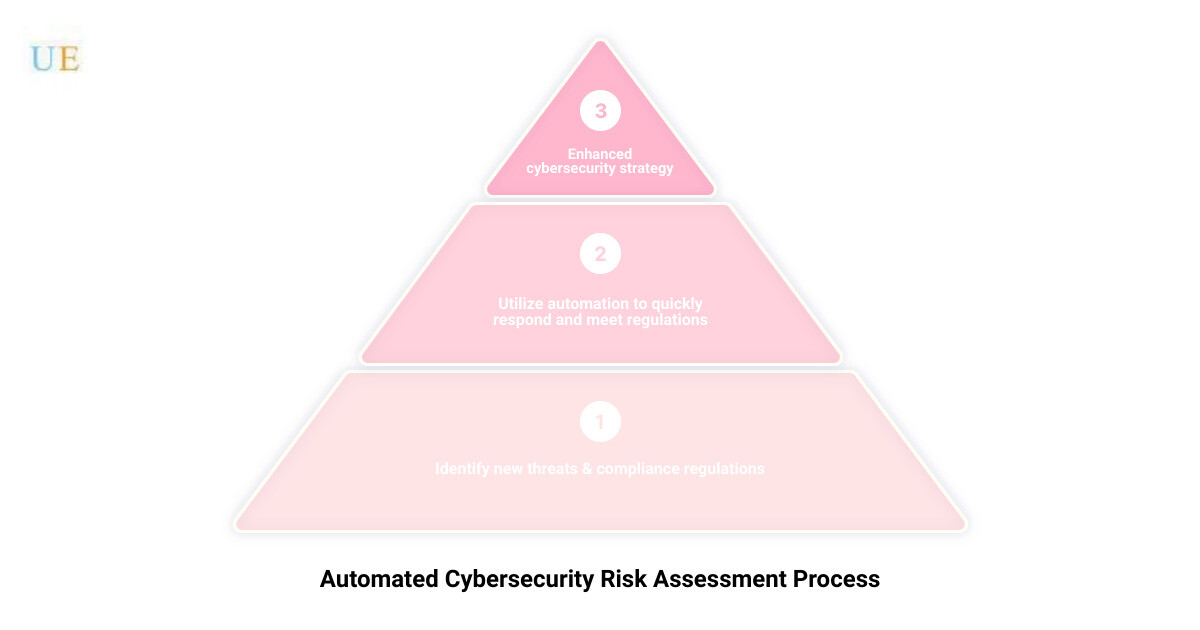
The landscape of cybersecurity threats is constantly evolving, and so are compliance requirements. Automation can help you stay abreast of these changes, allowing you to quickly identify and respond to new threats and ensure your company is meeting all relevant compliance regulations.
At Upper Echelon Technology Group, we believe in leveraging technology to its fullest potential. We have seen firsthand how automation can transform the way businesses handle risk assessments, and we are committed to helping our clients reap these benefits.
In the next section, we will explore some popular frameworks for cybersecurity risk assessment, including those that we use to guide our assessments at Upper Echelon Technology Group. Stay tuned to learn more about these valuable tools and how they can enhance your cybersecurity strategy.
Infographic illustrating how automation can streamline the cybersecurity risk assessment process, from data collection and analysis to report generation and staying updated with changing threats and compliance requirements.
Popular Cyber Security Risk Assessment Frameworks
Navigating the world of cybersecurity can often feel like a maze. There are numerous potential threats and vulnerabilities that can put your digital assets at risk. However, there are a few well-established cybersecurity risk assessment frameworks that can guide your journey, providing a structured approach to identify, assess, and prioritize risks.
The NIST Cybersecurity Framework
The first is the National Institute of Standards and Technology (NIST) Cybersecurity Framework. This framework provides a flexible and structured approach for organizations to assess their cybersecurity risks and prioritize actions to reduce those risks.
Developed by one of the United States’ foremost standards and technology organizations, the NIST Framework is widely respected and followed by both public and private sector organizations. It’s designed to be adapted to various sectors and organizations of all sizes. The core of the NIST framework consists of five functions: Identify, Protect, Detect, Respond, and Recover. These functions guide an organization through the process of understanding its risk environment, setting up protective measures, and outlining steps for responding to and recovering from cybersecurity incidents.
The ISO 27001:2013 Standard
Another globally recognized cybersecurity risk assessment framework is the ISO 27001:2013 standard. This standard provides a comprehensive approach to information security management, including requirements for risk assessment and risk treatment.
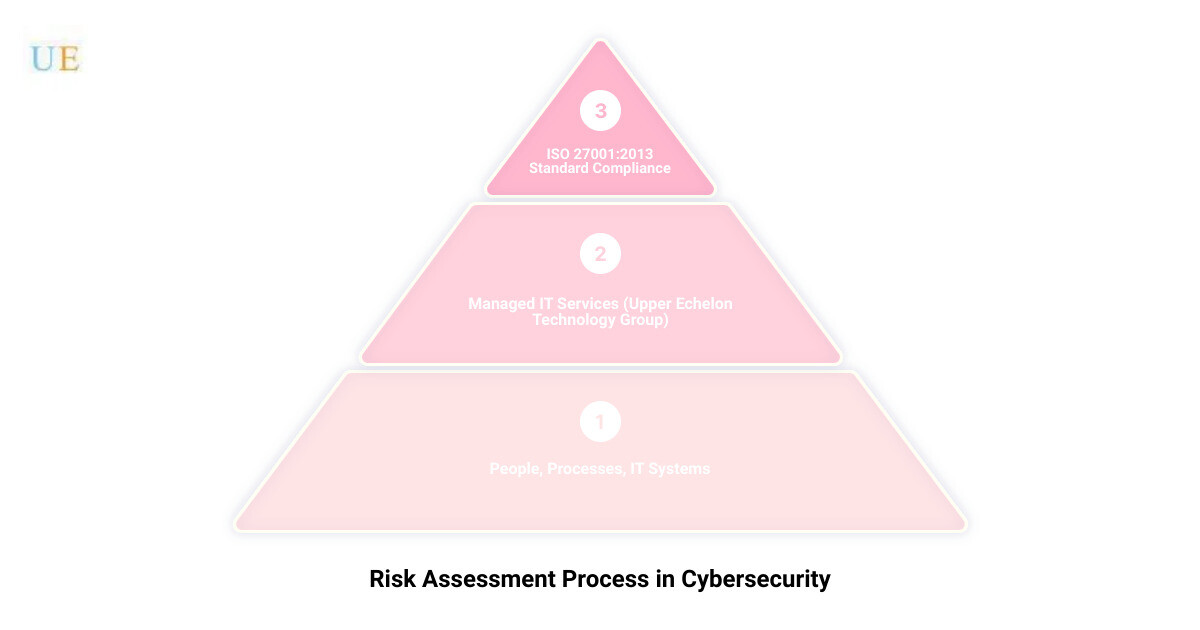
The ISO 27001 standard is a part of the larger ISO/IEC 27000 family of standards, all aimed at helping organizations keep information assets secure. ISO 27001:2013 provides specifications for a best-practice information security management system (ISMS). It offers a systematic approach to managing sensitive company information and ensuring it remains secure. This includes people, processes, and IT systems.
At Upper Echelon Technology Group, we understand the value of these frameworks and incorporate their principles into our own managed IT services. Our approach is to provide a personalized and tailored cybersecurity risk assessment that aligns with these global standards, yet is customized to the unique needs and context of your business.
In the next section, we’ll delve deeper into our unique approach to cybersecurity risk assessment and how it can deliver value to your business. Stay tuned!
Infographic illustrating the features of the NIST Cybersecurity Framework and ISO 27001:2013 Standard and how they guide organizations in performing cybersecurity risk assessments.
The Unique Approach of Upper Echelon Technology Group LLC to Cyber Security Risk Assessment
As we dive into the heart of our cybersecurity model, you’ll discover that at Upper Echelon Technology Group, we stand apart from the crowd with our unique approach to cybersecurity risk assessment. We believe in delivering solutions that are not only robust and secure but also personalized and tailored to the specific needs of your business.
Personalized IT Managed Services
A key aspect of our service offering is our personalized approach to IT managed services. We understand that no two businesses are alike, and thus, their cybersecurity needs will also significantly differ. This recognition drives us to provide a personalized service that caters to the specific needs and business goals of our clients.
We don’t just fix tech issues, we go beyond that. Our team takes the time to understand your business and identifies ways to leverage your technology assets in the best possible manner. This approach ensures that our services align perfectly with your business needs and objectives, thereby improving efficiency and enhancing profitability.
Our services are not limited to just cybersecurity. We offer a comprehensive portfolio of managed IT services, ensuring that your network is protected and optimized around the clock. This means that your technology serves your business, rather than the other way round.
Tailored Solutions for Businesses
At Upper Echelon Technology Group, we understand that cybersecurity is not a one-size-fits-all solution. Therefore, we focus on developing tailored solutions that fit your business like a glove.
Our approach to cybersecurity risk assessment is thorough and meticulous. We start by identifying your valuable assets and potential threats. We then assess the likelihood and impact of these risks, which allows us to prioritize them and select the most effective treatment options. This detailed process ensures that all aspects of your cybersecurity are covered.
Additionally, our team is constantly evaluating the services and products that we offer our clients to ensure that your network remains protected and optimized. This commitment to continual improvement means that your business is always a step ahead when it comes to cybersecurity.
In conclusion, our unique approach to cybersecurity risk assessment combines the best of personalized services with tailored solutions. So, if you’re a business owner who values a personalized approach to cybersecurity, we’d love to have a conversation with you. With Upper Echelon Technology Group, you can rest assured that your cybersecurity is in good hands.
Conclusion: The Ongoing Nature of Cyber Security Risk Assessment
In the ever-evolving world of technology, maintaining a secure digital environment is not a one-time task but a continuous pursuit. At Upper Echelon Technology Group, we understand that cybersecurity risk assessment is a dynamic process requiring regular reviews and updates. The threat landscape changes rapidly, and so must our strategies to combat them.
The risk assessment process in cyber security doesn’t end after a one-time evaluation. It’s an ongoing cycle of reviewing, updating, and enhancing your security measures. As your business evolves, so too will your security needs. Our team is committed to continuously monitor and review the risk environment to detect any changes in the context of your organisation, thereby maintaining an overview of the complete risk management process.
Automating the risk assessment process plays a significant role in this ongoing endeavour. As highlighted earlier, automation not only saves time and reduces errors but also provides a comprehensive view of your security posture, allowing us to quickly identify and respond to new threats. It’s a game-changer in the realm of cybersecurity, ensuring your business’s technology assets are optimally leveraged for maximum security and profitability.
Moreover, our adherence to internationally recognised frameworks like the NIST Cybersecurity Framework and ISO 27001:2013 Standard is a testament to our commitment to providing top-notch cybersecurity services. We don’t just follow these standards; we embody them, ensuring that our clients’ information security risk management is always on par with the best in the world.
In conclusion, the journey through the cybersecurity maze is a continuous one, filled with evolving threats and challenges. But with Upper Echelon Technology Group as your trusted cybersecurity partner, you can navigate this maze with confidence. Our expertise in risk assessment, personalised IT managed services, and tailored solutions will ensure your business is well-protected, efficient, and primed for growth.
Remember, cybersecurity is not a destination but a journey. And we are here to travel this journey with you every step of the way. To start your journey towards a safer digital environment, book an introduction call with us today. Let’s together make your company’s cybersecurity a success story.