In today’s digital era, where data breaches and cyber threats are the new normal, the importance of a robust cyber security risk assessment cannot be overstated. For business owners like you, ensuring the security of your company’s digital assets is undoubtedly a top priority. This is especially true considering the array of evolving cyber threats that can lead to catastrophic consequences when ignored. As a leading cybersecurity-focused managed service provider, we at Upper Echelon Technology Group understand your concerns and tailor our services to meet your specific needs.
However, did you know cyber crime isn’t just about staying one step ahead of the hackers? Yes, it involves identifying potential risks, but it also includes creating strategies and implementing controls to minimize impact. This is precisely where a cyber security risk assessment comes in.
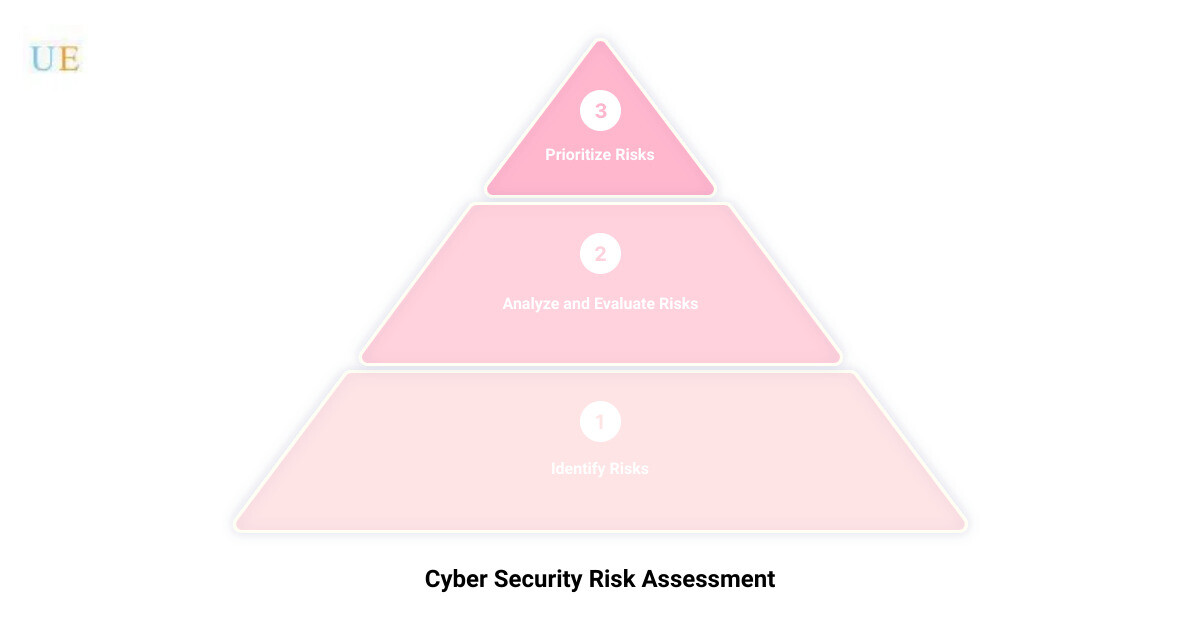
So, what is a cyber security risk assessment? It’s a structured process that helps identify, estimate, analyze, evaluate and prioritize the risks to your business operations and data. This risk-centered approach to cyber security often involves the use of popular frameworks such as the NIST Cybersecurity Framework, but at Upper Echelon Technology Group, we sometimes step outside the box and incorporate unconventional methodologies to maximize effectiveness.
For a quick understanding, below are the five core phases of a typical cyber security risk assessment:
- Scoping: Determine the boundaries of your assessment.
- Risk Identification: Identify the key assets of your organization and the potential threats they face.
- Risk Analysis: Assess the vulnerabilities paired with threat likelihood and impact.
- Risk Evaluation: Prioritize risks and decide on suitable control measures.
- Documentation: Record findings and monitor for changes in risk over time.
Stay tuned as we delve deeper into these phases, popular risk assessment frameworks, our unconventional approaches, as well as the critical role managed service providers like us play in the process.
Understanding Cyber Security Risk Assessment
Before we can discuss how to improve your cybersecurity posture, it’s essential to fully understand what a cybersecurity risk assessment is and why it’s so crucial for businesses today.
Defining Cyber Security Risk Assessment
A cybersecurity risk assessment is a comprehensive evaluation process that identifies potential cyber threats and vulnerabilities that could affect an organization’s information assets – this could include everything from hardware and systems to sensitive customer data and intellectual property. The process involves identifying these assets, assessing the potential risks they could face, and then determining the best controls to mitigate these risks.
In essence, a cybersecurity risk assessment is like a health check for your business’s cybersecurity measures, aiming to ensure they are adequate and effective in protecting your business against the ever-evolving landscape of cyber threats.
The Purpose of Cyber Security Risk Assessment
The primary goal of conducting a cybersecurity risk assessment is to help businesses understand their cybersecurity vulnerabilities and take appropriate actions to mitigate these risks. Without a thorough risk assessment, companies could spend a significant amount of resources defending against threats that are either unlikely to occur or won’t significantly impact the business.
In contrast, businesses could also overlook or underestimate potential risks that could cause substantial damage. This is why many best-practice frameworks, standards, and laws, including the GDPR, require risk assessments to be conducted. It helps you allocate your resources where they’re needed most, ensuring that your cybersecurity measures are as efficient and effective as possible.
The Role of Cyber Security Risk Assessment in Business Operations
At Upper Echelon Technology Group LLC, we believe that a cybersecurity risk assessment plays a pivotal role in overall business operations. It acts as the foundation for an effective cybersecurity strategy, helping organizations understand their risk profile and make informed decisions about their cybersecurity measures.
Not only does a risk assessment help identify potential vulnerabilities, but it also enables a business to understand the potential impact of a cyber attack on its operations. This insight is crucial in the development of a robust and effective incident response plan.
Moreover, it’s not a one-time process. Given the dynamic nature of cyber threats, conducting regular cybersecurity risk assessments is crucial to staying ahead of the curve. It helps businesses adapt their cybersecurity strategies in line with evolving threats and vulnerabilities, thereby ensuring continual protection against cyber attacks.
In the next sections, we will explore popular frameworks used for cybersecurity risk assessments and delve into the five main steps of conducting an assessment. We will also unveil some unconventional approaches we employ at Upper Echelon Technology Group to help our clients mitigate their cyber risks effectively.
Popular Frameworks for Cyber Security Risk Assessment
When it comes to managing cyber risks, businesses often turn to established frameworks which provide guidelines and best practices for assessing and mitigating those risks. Two such widely recognized and applied frameworks are the NIST Cybersecurity Framework and the ISO 27001:2013 Standard.
The NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) is a globally acknowledged authority for setting standards in various disciplines, including cybersecurity. Their risk assessment approach, as outlined in the NIST Special Publication 800-30, is designed to identify risk factors that could negatively impact an organization’s ability to conduct business.
This framework provides a systematic and comprehensive methodology for managing cyber risks. It guides organizations through a process of identifying and categorizing assets, assessing vulnerabilities, and determining the likelihood of threats and their potential impact. The outcome is a clear understanding of an organization’s risk exposure and the necessary actions and controls to mitigate the impact of these risks on business operations.
The ISO 27001:2013 Standard
Another globally recognized standard for managing cybersecurity risks is the ISO 27001:2013 Standard. This international standard provides guidelines for an Information Security Management System (ISMS) and is designed to enable organizations to establish, implement, maintain, and continually improve their information security.
The ISO 27001:2013 Standard requires businesses to conduct regular information security risk assessments and to retain documented information about the risk assessment process. The aim is to ensure that they comply with the standard’s requirements and can demonstrate such compliance, which can be especially useful in case of audits or certifications.
Both the NIST and ISO frameworks are comprehensive, methodical, and prioritizes the protection of an organization’s information assets. However, each organization’s needs, resources, and risk tolerance levels are unique, and so the implementation of these frameworks should be customized to suit the specific needs of the business. That’s where we at Upper Echelon Technology Group come in, with our personalized approach to IT Managed Services and our focus on your unique business needs.
In the next section, we will delve into the five main steps of conducting a cybersecurity risk assessment, and how we apply these steps to deliver robust cybersecurity solutions for our clients.
The Five Main Steps of a Cyber Security Risk Assessment
Embarking on a cybersecurity risk assessment can seem like a daunting task. However, by breaking it down into manageable steps, we can ensure a comprehensive and effective assessment that will keep your business secure. Here at Upper Echelon Technology Group, we utilize a five-step approach, ensuring that each area of potential risk is thoroughly explored.
Scoping: Determining the Scope of the Assessment
The first step is to determine the scope of the assessment. This could cover the entire organization or focus on specific business units, locations, or aspects of the business such as payment processing or web applications. We work closely with stakeholders to understand which assets and processes are the most important, ensuring that their input shapes the focus of the assessment.
Risk Identification: Creating an Inventory of Assets and Identifying Threats
Once the scope is defined, we create an inventory of all the IT assets within that scope. These assets could range from hardware and software to data and network infrastructure. Next, we identify the potential threats to these assets. These threats could be anything from malware attacks to data breaches or system failures.
Risk Analysis: Determining the Likelihood and Impact of Risk Scenarios
The next step in the process involves analyzing the identified risks. This involves determining the likelihood of each risk scenario occurring and the potential impact on the organization if they do. We employ sophisticated tools and methodologies to accurately gauge these factors, providing a comprehensive risk profile that informs future steps.
Risk Evaluation: Prioritizing Risks and Deciding on Mitigation Strategies
After the risks have been analyzed, they need to be prioritized. This involves ranking the risks based on their potential impact and the likelihood of occurrence. The risks that pose the greatest threat to the organization are prioritized for mitigation. We then work with the stakeholders to decide on the appropriate mitigation strategies. This could involve implementing new security measures, updating existing ones, or even accepting the risk if its impact is deemed manageable.
Documentation: Maintaining a Risk Register and Tracking Progress
Finally, all this information is documented in a risk register. This document serves as a record of all identified risks, their potential impact, the chosen mitigation strategies, and their implementation status. We believe in maintaining a living document that is regularly updated to reflect changes in the risk landscape, ensuring that your cybersecurity measures stay ahead of the curve.
By following these steps, we at Upper Echelon Technology Group ensure a thorough and effective cybersecurity risk assessment that is tailored to your unique business needs. This methodical approach allows us to identify, analyze, evaluate, and mitigate the cyber threats to your organization, keeping your business secure and your mind at ease.
Unconventional Approaches in Cyber Security Risk Assessment
In the ever-evolving landscape of cyber threats, sticking to the conventional methods may not always yield the desired results. At Upper Echelon Technology Group, we believe in staying ahead of the curve, which is why we adopt some unconventional approaches in our cybersecurity risk assessments.
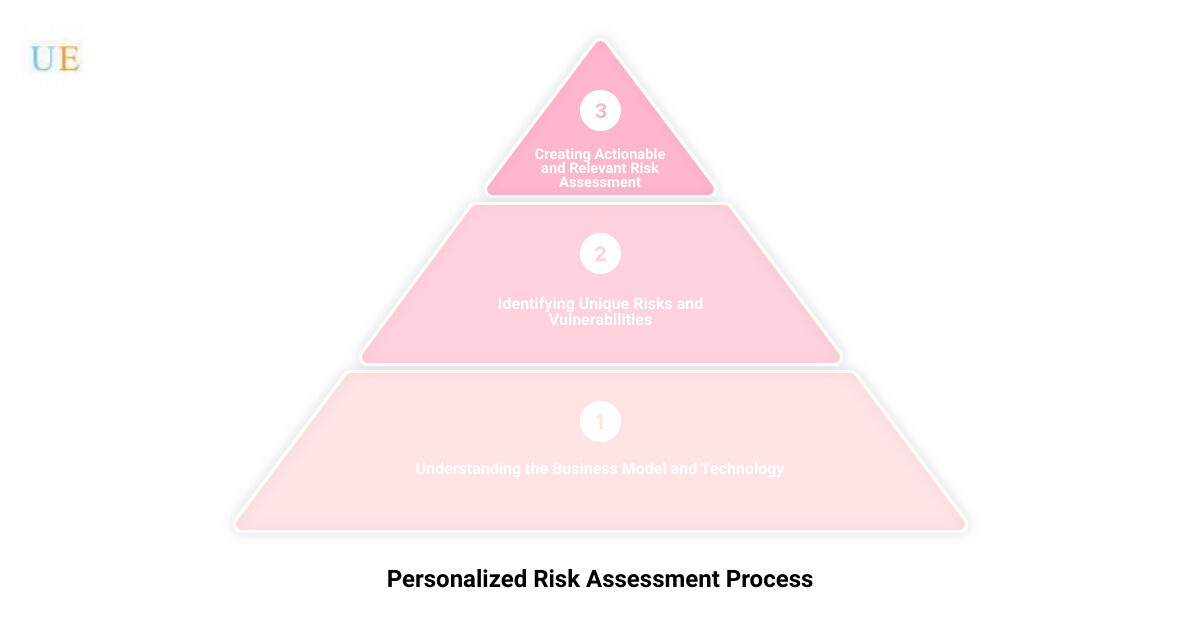
Personalized Risk Assessment: Tailoring the Assessment to the Specific Needs of the Business
Every business has unique needs and vulnerabilities when it comes to cybersecurity. While the traditional risk assessment approaches offer a broad framework, we believe in tailoring our assessments to the specific needs of your business. This personalized approach involves understanding your business model, the technology you use, and the unique risks associated with them. This allows us to identify vulnerabilities that could be overlooked in a more generic assessment. Our customized approach not only enhances the effectiveness of our risk assessments but also makes them more relevant and actionable for your business.
Proactive Risk Assessment: Anticipating Future Threats and Preparing in Advance
We don’t just focus on the current threats, but also anticipate future risks. Cyber threats are constantly evolving, and new vulnerabilities can emerge at any time. By staying abreast of the latest trends in cyber threats and using predictive analytics, we can anticipate potential future threats and vulnerabilities. This proactive approach allows us to recommend preventative measures, so your business is always a step ahead of potential cyber threats.
Continuous Risk Assessment: Regularly Updating the Risk Profile to Stay Ahead of New Threats
Cybersecurity is not a one-time process, but a continuous one. As your business evolves, so does your risk profile. To ensure that your cybersecurity measures are always up-to-date, we adopt a continuous risk assessment approach. This involves regularly updating your risk profile and conducting periodic reassessments, ensuring that no new vulnerabilities are overlooked.
At Upper Echelon Technology Group, we understand that cybersecurity is a journey, not a destination. Our continuous risk assessment approach ensures that your business is always equipped to handle the ever-changing landscape of cyber threats, keeping your business secure and your mind at ease.
In the next section, we’ll delve into the role of Managed Services Providers in Cyber Security Risk Assessment and how we can help your business stay secure.
The Role of Managed Services Providers in Cyber Security Risk Assessment
In today’s rapidly evolving digital landscape, the role of managed services providers (MSPs) in mitigating cyber risk is becoming increasingly crucial. A competent MSP, like Upper Echelon Technology Group, can help businesses navigate the complex waters of cybersecurity, ensuring comprehensive protection against potential threats.
How Upper Echelon Technology Group LLC Provides Personalized IT Managed Services
As a cybersecurity-focused managed services provider, we at Upper Echelon Technology Group offer a personalized approach to IT managed services. We understand that every organization has unique requirements and challenges. That’s why we don’t just “fix tech issues;” we go beyond that.
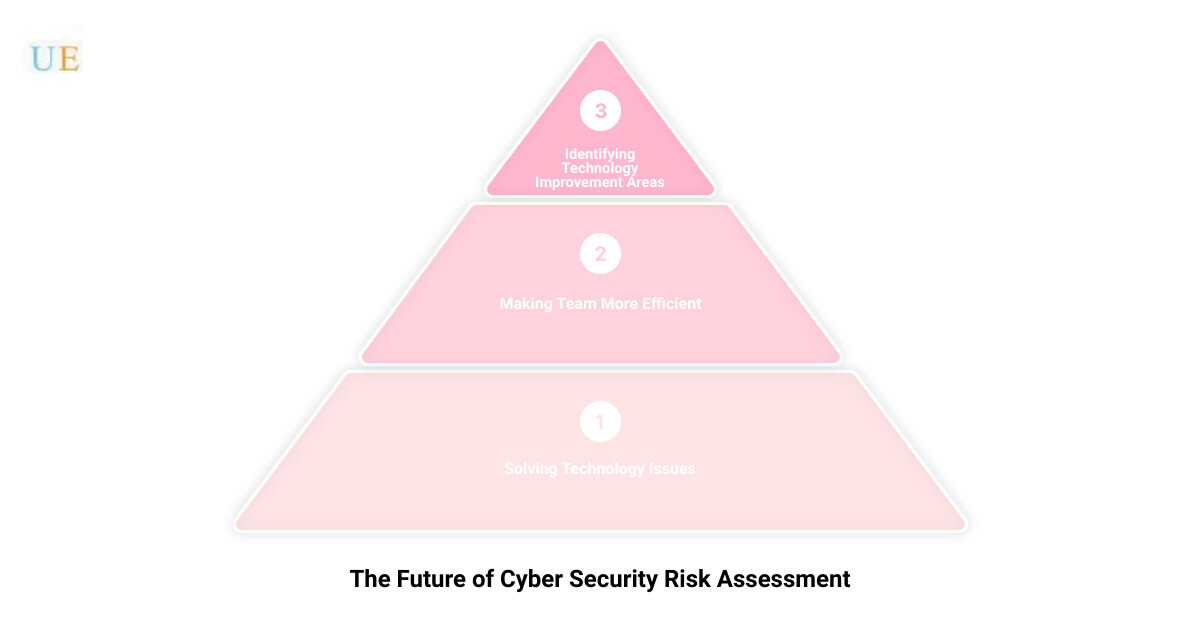
We focus on three key areas to support your business. First, we solve your technology issues, allowing you to focus on your business operations. Second, we make your team more efficient by leveraging technology, streamlining processes and workflows. And last but not least, we strive to make your company more profitable by identifying areas where technology can improve your bottom line.
Our managed IT services portfolio is best of breed, constantly evaluated and updated to ensure that your network is protected and optimized 24x7x365. We believe that technology should serve your business, not the other way around.
The Benefits of Outsourcing Cyber Security Risk Assessment to Experts
Outsourcing cybersecurity risk assessment to experts like us offers several benefits. First, it provides access to a team of cybersecurity specialists with a wealth of experience and knowledge in the field. This ensures that your risk assessments are thorough, accurate, and compliant with industry standards.
Second, it allows for a more objective assessment. In-house teams may be too close to the organization to see certain risks, but an external team can provide a fresh perspective.
Third, outsourcing can save time and resources. Cybersecurity risk assessments can be complex and time-consuming. By leaving this task to the experts, your internal team can focus on other strategic business initiatives.
Finally, it offers peace of mind. Knowing that a dedicated team is constantly monitoring your cybersecurity posture and ready to respond to any threats can significantly reduce stress and worry.
In conclusion, choosing a managed services provider like Upper Echelon Technology Group for your cybersecurity risk assessment needs can provide a comprehensive, tailored approach that aligns with your business needs and goals. It’s a strategic move that adds value to your business, enhances security, and promotes operational efficiency.
Conclusion: The Future of Cyber Security Risk Assessment
As we look ahead to the future of cybersecurity risk assessment, it’s clear that the landscape is rapidly evolving. Cyber threats are becoming more sophisticated, and businesses of all sizes are facing an increasingly complex risk environment.
The rise of emerging technologies like artificial intelligence, machine learning, and quantum computing are set to revolutionize the way we approach cybersecurity. These technologies promise to enhance our ability to predict and detect threats, making proactive risk assessment a reality. Continuous risk monitoring and evaluation will become the norm, enabling businesses to stay one step ahead of cybercriminals.
At the same time, the role of personalized risk assessment will continue to grow in importance. Here at Upper Echelon Technology Group, we firmly believe that every business is unique, and so should be their approach to cybersecurity. By tailoring the risk assessment process to the specific needs and contexts of each business, we can provide more accurate and actionable insights.
In the end, it all comes down to striking the right balance between risk and reward. Cybersecurity is not just about preventing threats; it’s also about enabling businesses to leverage technology safely and confidently to drive growth and innovation.
As a cybersecurity-focused managed services provider, we are dedicated to helping businesses in Wilmington, DE, and beyond navigate this delicate balance. We are here to solve your technology issues, make your team more efficient, and identify areas where technology can improve your bottom line.
The future of cybersecurity risk assessment may be complex and challenging, but with the right partner by your side, it is a future you can face with confidence. Partner with Upper Echelon Technology Group, and let us help secure your business today, tomorrow, and well into the future.
This infographic visualizes how emerging technologies will reshape the cybersecurity landscape, the growing importance of personalized risk assessment, and the role of a managed services provider like Upper Echelon Technology Group in helping businesses navigate these changes.