In today’s ever-evolving digital era, unexpected cyber threats lurk behind every corner, ready to exploit any potential technology vulnerabilities. At the heart of these complexities sits the pressing need for a comprehensive cyber security risk analysis. This preventive security measure is there to fend off threats, protect sensitive data, and maintain the smooth operation of your business.
With the vast majority of small to medium-sized businesses just a single cyber-attack away from potential bankruptcy, understanding and implementing a solid cyber security risk analysis has become more than just a technological choice—it’s become a business imperative. Here at Upper Echelon Technology Group, we not only recognize the importance of proactive cyber risk assessments but also tailor them to align seamlessly with the specific needs of your business and the risks your organization faces.
To get straight to the point: A cyber security risk analysis is an organized approach to scrutinize possible threats, identify significant vulnerabilities, determine the probable likelihood and potential impact of those threats, set sufficient security controls, and finally, monitor and review their effectiveness.
To address this in a concise manner and provide a quick overview, lets look at the key elements of a cyber security risk analysis:
- Defining Threats: Understanding the array of cyber threats your business may face, from malware and phishing to insider risks.
- Identifying Vulnerabilities: Highlighting weak spots that could be exploited by threats.
- Threat Likelihood & Impact: Estimating the probability of threats occurring and gauging their potential impact on your business.
- Security controls: Applying measures to protect against or lessen the impact of threats.
- Monitoring & Review: Regularly checking and updating these measures to ensure ongoing effectiveness.
The above infographic offers a visual representation of this crucial process, presenting the simplicity behind conducting a cyber security risk analysis. It underlines the gravity of each step and its role in keeping your business fortified and resilient in the face of numerous cyber threats.
Stay tuned as we delve deep into understanding and implementing a cutting-edge approach to cyber security risk analysis, adapting and evolving in response to the ever-changing dynamics of the cyber landscape.
Understanding Cyber Security Risk Analysis
In the ever-evolving digital landscape, understanding cyber security risk analysis is more than just a necessity; it’s a survival skill. This process is the cornerstone of a robust cybersecurity strategy, ensuring the right defenses are in place to protect your business.
Definition and Purpose of Cyber Security Risk Analysis
Cyber security risk analysis is a detailed process of identifying, analyzing, and evaluating potential risks that could compromise your cyber defenses. This process is crucial to ensure that the cyber security controls you choose are well-suited to the specific risks your business faces.
It’s like a health check-up for your cyber infrastructure. Just as doctors diagnose potential health issues by analyzing symptoms, we, at Upper Echelon Technology Group, diagnose your cyber health by identifying potential risks and vulnerabilities. This proactive approach ensures you don’t waste time, effort, and resources on irrelevant defenses, and instead, focus on fortifying areas that could be potential threat targets.
The Role of a Cybersecurity Risk Analyst
A cybersecurity risk analyst is the superhero who keeps your business safe in the cyber world. They support the analysis, classification, and response to cyber risks within an organization. This professional assesses cybersecurity risk and analyzes the potential impact on business and customer data, aligning processes and controls to the relevant frameworks and internal systems.
Their role is pivotal in helping you understand the cyber threats that lurk in the shadows of your network. They not only identify the risks but also evaluate their potential impact, helping you prioritize your defenses. In essence, a cybersecurity risk analyst is your guide, helping you navigate the complex terrain of cyber threats.
At Upper Echelon Technology Group, our cybersecurity risk analysts are equipped with cutting-edge tools and a wealth of experience. They perform comprehensive risk assessments, ensuring your cybersecurity strategy is designed to withstand current and emerging threats.
The journey towards robust cybersecurity starts with understanding the fundamentals of risk analysis. In the following sections, we will explore the step-by-step process of conducting a cyber security risk analysis, revealing how you can protect your business from the unseen dangers of the digital world. Stay tuned!
The Process of Cyber Security Risk Analysis
The secret of getting ahead is getting started, Mark Twain once said. As we delve into the process of cyber security risk analysis, we’ll help you get started on your journey to a more secure business.
Step 1: Defining Cybersecurity Threats
Firstly, we must identify the potential threats that could jeopardize your business. These threats could come in various forms, such as unauthorized access to your network, misuse of information or data leakage, failed processes, data loss, and disruption of service. The truth is, cyber threats are evolving every day, and small businesses are increasingly becoming the major targets. In fact, according to Cyber Defense Magazine, 43 percent of all cyber attacks are aimed at small businesses.
Step 2: Identifying Security Vulnerabilities
Secondly, we need to identify areas where your company or information is most vulnerable. This involves taking an inventory of all your business’s network resources, including every device, how they connect, and how information and data travel through the network. It’s essential to note all potential weaknesses and vulnerabilities in your system, even those seemingly innocuous ones. Remember, even a seemingly harmless device could be a potential gateway for a cyber intrusion.
Step 3: Determining Threat Likelihood and Impact
Next, we need to determine the potential impact of these threats on your business. This involves rating potential risks on a scale of low, medium, and high risk. The objective here is to balance the potential damage a cyber attack could cause against the likelihood of a system being compromised. To do this, we assess the value of your data and how much damage could be inflicted if that data was exposed or lost.
Step 4: Setting Security Controls
Once we have identified the threats and vulnerabilities, it’s time to set up controls to minimize or eliminate the risk. These controls could be technical, such as hardware, software, encryption, intrusion detection mechanisms, two-factor authentication, and automatic updates. They could also be non-technical, like security policies and physical mechanisms such as locks or keycard access. The goal here is to implement both preventive controls that stop attacks and detective controls that alert you when an attack has occurred.
Step 5: Monitoring and Reviewing Effectiveness
The final step in the process is monitoring and reviewing the effectiveness of the controls put in place. Here at Upper Echelon Technology Group, we believe in continuous monitoring and regular reviews to ensure that our security measures are always up-to-date and effective against the latest threats. This proactive approach helps us detect potential breaches early, minimizing damage and ensuring your business remains safe and secure.
In conclusion, conducting a cyber security risk analysis is not a one-time event but a continuous process. As your business grows and evolves, so do the potential threats and vulnerabilities. Therefore, regular assessments and updates to your security measures are crucial. At Upper Echelon Technology Group, we are committed to providing you with a personalized approach to IT Managed Services, helping you stay ahead of the curve in cyber security.
Types of Risk Analysis in Cybersecurity
In the vast and complex landscape of cybersecurity, diverse risk analysis strategies are employed to tackle different aspects of the challenge. Three types of risk analysis often used in the realm of cybersecurity are Business Impact Analysis (BIA), Failure Mode and Effects Analysis (FMEA), and Risk Benefit Analysis. Each of these plays a crucial role in a comprehensive cybersecurity risk assessment strategy.
Business Impact Analysis (BIA)
Business Impact Analysis is a critical component of an organization’s business continuity plan; it predicts the consequences of disruption of a business function and process and gathers information needed to develop recovery strategies. BIA helps in identifying the potential impact of a cyber incident on business operations, ranging from a data breach to the complete shutdown of digital operations.
The BIA process involves identifying the key resources and processes that are critical to an organization’s operational and financial success. It then analyzes how quickly these resources and processes need to be restored in case of a disruption. This information can then be used to prioritize recovery strategies and to ensure that the most critical areas are addressed first.
Failure Mode and Effects Analysis (FMEA)
Failure Mode and Effects Analysis is a proactive method for evaluating a process to identify where and how it might fail, assessing the relative impact of different failures, in order to identify the parts of the process that are most in need of change. It helps in identifying potential hardware and software failures that could lead to significant impacts.
In the context of cybersecurity, FMEA helps in understanding how a potential failure of security controls or policies can lead to a security incident, and what the potential impacts of such incidents could be. This type of analysis is useful for prioritizing areas for improvement in an organization’s cybersecurity strategy.
Risk Benefit Analysis
Risk Benefit Analysis involves comparing the estimated costs of implementing specific cybersecurity controls against the estimated benefits that would be derived from their implementation. This type of analysis is essential for making informed decisions about how to allocate resources for cybersecurity risk management.
This process involves quantifying and comparing the potential costs, such as implementation costs and the potential for decreased productivity, against the potential benefits, such as reduced risk of data breaches and the potential for increased trust from customers and partners.
At Upper Echelon Technology Group, we understand that the most effective cybersecurity strategies are those that are tailored to the unique needs and risks of each organization. That’s why we incorporate these risk analysis strategies into our approach to cybersecurity risk management. We work with our clients to understand their unique organizational context and risk profile, and we use this understanding to guide our risk analysis and management strategies. As a result, we can help our clients to make informed decisions about where to invest their resources for maximum impact on their cybersecurity posture.
Practical Examples of Cyber Security Risk Analysis
In the maze of cybersecurity, practical examples can serve as helpful guides. Let’s delve deeper into a couple of real-world scenarios that demonstrate how a risk analysis in cybersecurity can be applied.
Risk Analysis Cyber Security Template
The first step in a cybersecurity risk analysis is to create a catalog of information assets. These might range from servers containing public information to cloud-based software storing payment or customer’s personal information. This can be visualized as a cybersecurity risk matrix, where each asset is assigned a risk level based on its inherent vulnerability and the potential impact of a security breach.
Low-risk items could include servers that host public information and are connected to an in-house network. Medium-risk items might involve offline data storage at a specific physical location, and high-risk items could be payment or customer’s personal information stored in cloud software.
By mapping these risk levels, we can then conduct an analysis to determine the likelihood of a risk scenario and the potential financial impact on the business. This step helps us to prioritize which parts of your infrastructure need to be secured first.
Risk Analysis Cyber Security Example
Let’s consider an example of a high-risk item: customer’s personal information stored in cloud software. A breach of this data could result in significant financial loss and damage to the company’s reputation. In this case, the risk analysis would involve assessing the current security controls in place, such as encryption, firewall settings, and access controls.
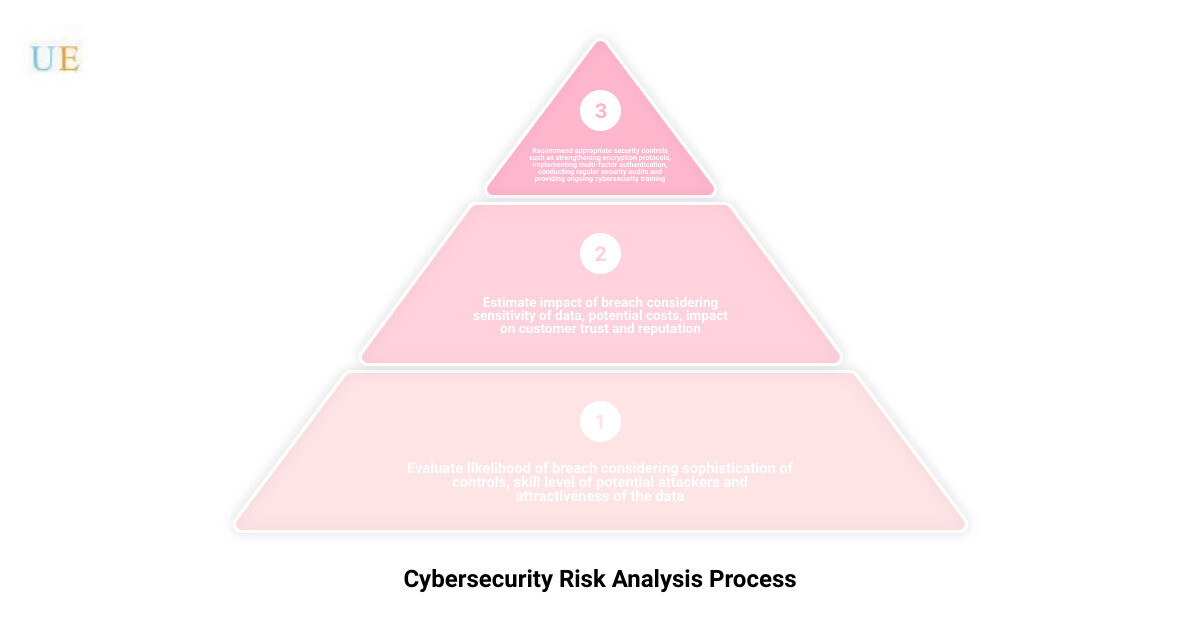
From there, we would evaluate the likelihood of a potential breach, considering factors such as the sophistication of the controls, the skill level of potential attackers, and the attractiveness of the data to cybercriminals. We would also estimate the potential impact of a breach, taking into account factors such as the sensitivity of the data, the potential costs of a breach (including regulatory fines, remediation costs, and potential lawsuits), and the potential impact on customer trust and the company’s reputation.
Based on this risk analysis, we would then recommend appropriate security controls to mitigate the risk. These might include strengthening encryption protocols, implementing multi-factor authentication, conducting regular security audits, and providing ongoing cybersecurity training for staff.
At Upper Echelon Technology Group, we understand that every organization is different, and there is no one-size-fits-all approach to cybersecurity. Our team of experts work closely with each client to conduct a thorough risk analysis and develop a customized cybersecurity strategy that aligns with the client’s specific needs and risk profile.
The infographic demonstrates the process of a cyber security risk analysis, showing how to identify assets, assess the risks, analyze the risks, set security controls, and monitor and review the effectiveness of the controls.
In conclusion, a cybersecurity risk analysis is a critical component of any effective cybersecurity strategy. It enables organizations to identify their most significant risks and implement appropriate controls to mitigate those risks. At Upper Echelon Technology Group, we are committed to helping our clients navigate the complexities of cybersecurity and protect their valuable information assets.
The Role of Managed Services Providers in Cyber Security Risk Analysis
As the digital landscape continues to evolve, so too does the complexity and sophistication of cyber threats. This reality demands a proactive, strategic approach to cybersecurity, one that goes beyond just fixing tech issues. And that’s where Managed Services Providers (MSPs) come in.
MSPs play a crucial role in managing and mitigating cyber risks. They provide a wealth of expertise and resources to help businesses understand, control, and mitigate all forms of cyber risk. They can handle everything from threat detection and response to data protection and recovery.
How Upper Echelon Technology Group LLC Approaches Cyber Security Risk Analysis
At Upper Echelon Technology Group, we believe that a robust cybersecurity strategy starts with a thorough risk analysis. Our approach is rooted in understanding your business needs and leveraging your technology assets in the best possible way to protect your business.
We begin by identifying your most valuable data and the infrastructure that supports it. We then assess potential threats and vulnerabilities that could cause financial and reputational damage to your business. From there, we define a risk assessment policy that guides how risks are addressed and mitigated and how subsequent risk assessment processes are conducted.
Our team constantly evaluates the services and products that we offer to our clients to ensure that your network is protected and optimized 24/7/365. We aim to make sure that your technology serves your business, instead of the other way around.
We believe that building a secure and resilient IT environment is a team effort. Our core values guide us in fostering a company culture that puts relationships first, encourages personal growth, and values open, honest, and productive communication. We work as a true team and strive to be a positive influence, doing the right thing even when no one is looking.
In addition to our cybersecurity offerings, we also offer a host of other Managed IT Services that help your business operate smoothly. This includes cloud hosting services, endpoint management, and Microsoft 365, among others.
In the end, cybersecurity risk analysis is not a one-time event but an ongoing process. As your security implementations improve and you address the risks discovered in assessment responses, your cybersecurity posture should also improve. This is our commitment to you – to help you streamline your cybersecurity risk assessment workflows and to continually enhance your security posture.
Infographic: Cybersecurity Risk Analysis and the Role of Managed Services Providers
In the ever-evolving digital landscape, the need for effective cybersecurity risk analysis has never been greater. As your trusted managed services provider, we at Upper Echelon Technology Group are here to help you navigate these complexities and secure your business for the future.
Conclusion: The Future of Cyber Security Risk Analysis
As we step into the future, the role of cybersecurity risk analysis is set to become more crucial than ever. With the relentless evolution of cyber threats, it’s no longer enough to stay on the defensive. Now, we must anticipate, understand, and respond to these risks proactively.
The Rising Significance of Risk Analysis
Cybersecurity risk analysis will continue to be a vital tool for organizations of all sizes, helping them to understand their unique risk landscape and make informed decisions. It will become even more critical as businesses continue to leverage emerging technologies, such as the Internet of Things (IoT), artificial intelligence (AI), and machine learning.
Predictive Risk Analysis
In the future, we can expect to see a shift towards predictive risk analysis. This approach uses machine learning and AI to predict potential threats before they occur, enabling organizations to take preventative measures. As AI technology continues to evolve, this form of risk analysis will become increasingly accurate and effective.
Increased Regulatory Scrutiny
Furthermore, as data breaches and cyber attacks continue to make headlines, regulatory scrutiny around data protection and cybersecurity is expected to increase. This means organizations will need to ensure their risk analysis strategies are compliant with evolving laws and regulations.
The Crucial Role of MSPs
Managed Services Providers (MSPs) like us, at Upper Echelon Technology Group, will play a crucial role in the future of cybersecurity risk analysis. We not only bring in-depth knowledge and expertise in the field but also provide personalized and adaptive services. We are equipped to respond to the shifting cybersecurity landscape and can help your business stay ahead of the curve.
As we look to the future, one thing is clear – cybersecurity risk analysis is not just about protecting your business; it’s about enabling your business to grow and flourish, unhindered by cyber threats. By identifying vulnerabilities early, implementing robust security controls, and continually monitoring and reviewing their effectiveness, we can help your business turn the tide against cyber threats.
In conclusion, the future of cybersecurity risk analysis is not just about predicting and preventing threats, but also about seizing opportunities. It’s about leveraging the power of technology to create safer, more secure business environments where innovation and growth can thrive. And as your trusted partner, we at Upper Echelon Technology Group are committed to helping you navigate this future, ensuring your business is not just protected but primed for success.