Stepping into the Shadows: Understanding the Dark Web
The internet is much like an iceberg. The part we see and interact with daily, known as the surface web or open web, is just the tip. Below the surface lies a vast, hidden world known as the deep web, and within it lurks a part shrouded in mystery and intrigue, the dark web. As a business owner, you might be wondering, how bad is the dark web? Is it merely a hotbed of illegal activities, or does it have legitimate uses? Let’s delve into the hidden depths of the dark web to unravel its true impact.
The dark web is a part of the internet that isn’t indexed by regular search engines and requires specialized browsers like TOR for access. It offers users anonymity, making it a haven for a range of activities, both legal and illegal. While it’s notorious for being the playground of cybercriminals, the dark web also serves as a crucial platform for whistleblowers, journalists, and ordinary citizens living under oppressive regimes.
Understanding the dark web is vital for the modern business owner. It’s not just about the risks it poses but also about the potential it holds for secure communication and information exchange. Most importantly, a deep understanding of the dark web can help you secure your business in this digital age, a task that Upper Echelon Technology Group is committed to helping you with.
In this article, we’ll take you through the layers of the internet, explore how to access the dark web safely, discuss its potential dangers, and highlight its legitimate uses. We will also delve into the role of cybersecurity and dark web monitoring in protecting your business. So let’s embark on this journey into the unknown and demystify the dark web.
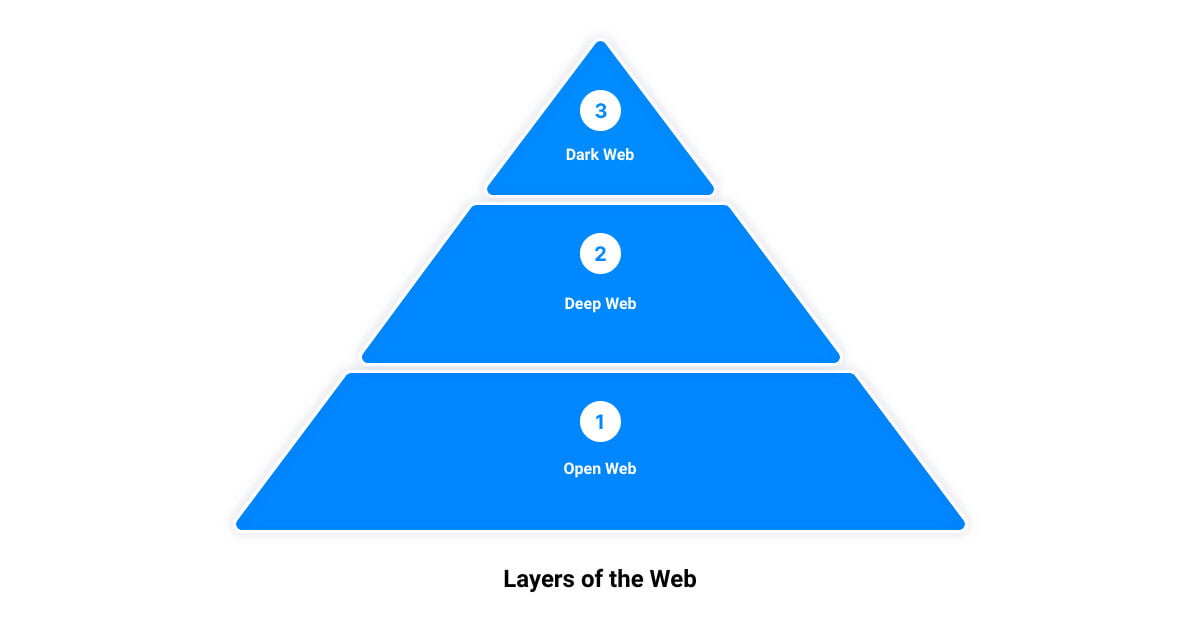
The Structure of the Internet: Open Web, Deep Web, and Dark Web
The internet is akin to an iceberg. The visible tip, the part we interact with daily, is only a fraction of what lies beneath. This visible section is known as the open web, also referred to as the surface web. It includes any public content indexed by search engines such as Google or Bing. The open web is easily accessible and contains common sites like Wikipedia, YouTube, and your favorite news outlets. However, despite its vastness, it only makes up about 4% of the total internet content.
Beneath the surface lies the deep web, which constitutes the bulk of the internet, over 90% of it. The deep web refers to any web content not indexed by search engines. This includes websites behind paywalls or those that require login credentials. These are the everyday sites you visit to check emails, access your bank account, or review health or school records. While the deep web may sound sinister, it’s part of our daily internet usage and isn’t inherently dangerous.
Now, hidden within the depths of the deep web is the dark web. This is an unindexed network of web content made anonymous through various encryption and routing techniques. It’s like a maze within the depths, unregulated and upheld by a network of volunteers around the world who operate proxy servers to route dark web requests. The dark web’s unregulated, anonymous nature is what makes it a valuable tool for both cybercriminals and those seeking a haven from censorship or surveillance.
It’s important to differentiate between the deep web and the dark web. While the dark web is part of the deep web, the inverse is not true. The dark web represents a small fraction of the deep web, not the whole.
Understanding these three layers of the internet is essential for grasping the complexity and breadth of the online world. As a business owner, it can help you appreciate the need for robust cybersecurity measures, such as those provided by Upper Echelon Technology Group LLC, to protect your data and operations from potential threats lurking in the dark web’s shadowy corners.
Accessing the Dark Web: Tools and Precautions
Stepping into the shadows of the dark web is not a casual stroll through your neighborhood park. It requires specific tools and a set of precautions to ensure safe navigation and protection from the potential dangers hidden within its depths. This is where specialized software like the Tor browser and Virtual Private Networks (VPNs) come into play.
The Role of Tor and I2P in Accessing the Dark Web
The dark web is an unindexed part of the internet that requires unique software to access. The Tor browser, developed in the mid-1990s, has emerged as the preferred gateway to this clandestine world. The Onion Router (Tor), named for its layers of security, uses a complex system of encryption and random routing of internet traffic to ensure complete anonymity.
In addition to Tor, the Invisible Internet Project (I2P) is another network layer that allows for anonymous communication, offering a high level of privacy protection. These tools provide a veil of security for those who need to operate beneath the radar, including whistleblowers, journalists, and even law enforcement agencies.
However, despite their legitimate uses, these platforms have also become a haven for criminals who exploit the anonymity offered to conduct illicit activities. This dual use underscores the importance of understanding how these tools work and the precautions needed when venturing into the dark web.
The Importance of VPNs and Secure Browsing Practices
While Tor and I2P provide an access point to the dark web, they alone are not enough to guarantee your safety. Most users on the dark web use Virtual Private Networks (VPNs) to further conceal themselves. A VPN creates a secure tunnel for your data, protecting you from potential surveillance and data breaches.
However, secure browsing practices do not stop at using a VPN. Regularly updating your software, using robust and unique passwords, and being wary of unsolicited or suspicious links are also key precautions to take. And, of course, engaging in illegal activities on the dark web is not just ethically wrong, but it also increases the risk of encountering malicious actors or falling afoul of the law.
In the ever-evolving landscape of the internet, keeping your business secure can feel like an uphill battle. But with the right knowledge and tools, you can navigate the complexities of the online world confidently. As a cybersecurity-focused managed services provider, Upper Echelon Technology Group LLC can help secure your data and improve your company’s profitability by leveraging technology in the most efficient way possible.
The Dark Side of the Dark Web: Illegal Activities and Risks
Behind the veil of anonymity that the dark web provides, lurks an underbelly of illicit activities and cyber threats. While the dark web serves vital functions for legitimate users like whistleblowers and journalists, it’s also a breeding ground for cybercriminals who exploit its hidden depths for nefarious purposes.
The Prevalence of Cybercrime on the Dark Web
The dark web has become a virtual marketplace for cybercriminals, where illegal activities such as drug trafficking, money laundering, and cybercrime are rampant. Child pornography, drug trafficking, illegal arms dealings, and cryptocurrency scams are some of the most predominant criminal activities on the dark web.
The anonymous nature of the dark web enables these activities, making it difficult for authorities to trace transactions back to their source. Therefore, users must exercise extreme caution when interacting with the dark web, as even seemingly harmless activities could have serious legal and financial repercussions.
The Dangers of Phishing and Malware on the Dark Web
Phishing and malware are two of the most prevalent cyber threats on the dark web. Cybercriminals often employ sophisticated tactics to trick users into revealing sensitive data or downloading malicious software. One such method is to mimic surface web scripts on dark web pages, enabling them to trace user activity.
This is a significant risk for those using Tor browsers, which serve as a bridge between the surface and dark webs. Consequently, even if you’re just browsing the dark web, there’s always a possibility that you could be tracked, or worse, fall victim to a cyber attack.
The Role of Cryptocurrency in Dark Web Transactions
Cryptocurrency plays a crucial role in facilitating transactions on the dark web. Its decentralized and anonymous nature makes it the ideal choice for those wishing to maintain their privacy. However, it’s also a double-edged sword. Cryptocurrencies like Bitcoin are often used in illegal activities, creating a thriving underground economy that’s almost impossible to regulate.
Cryptocurrency scams also abound on the dark web. Unscrupulous individuals may trick users into parting with their digital assets, leaving them with no recourse due to the irreversible nature of cryptocurrency transactions. Users must be aware of these risks and take necessary precautions when dealing with cryptocurrencies on the dark web.
Despite the dangers the dark web presents, it’s not all doom and gloom. As a business owner, you can take proactive steps to protect your data and leverage technology to drive growth. Upper Echelon Technology Group LLC, a cybersecurity-focused managed services provider, excels at helping businesses navigate these complexities. Our next section will delve into the legitimate uses of the dark web and how you can enhance your cybersecurity measures.
The Light in the Darkness: Legitimate Uses of the Dark Web
The dark web isn’t all shadowy dealings and clandestine transactions. Inside its labyrinthine network, there are glimmers of light, instances where the anonymity and untraceability of the dark web serve a noble purpose.
How Journalists and Activists Use the Dark Web
The dark web is a beacon of hope for journalists and activists living under oppressive regimes. These brave individuals leverage the anonymity provided by the dark web to uncover truths and fight against injustices. Using tools such as Tor, they can securely communicate, share sensitive information, and access blocked content without the fear of surveillance or retaliation. In fact, the dark web has become a vital tool for journalists worldwide, allowing them to bypass censorship and protect their sources.
The Dark Web as a Tool Against Censorship
Beyond its utility for journalists and activists, the dark web serves as a bulwark against censorship. In regions where internet access is heavily regulated or censored, the dark web offers a lifeline for ordinary citizens to access unbiased news and share their experiences with the world.
For instance, individuals can use a decentralized network like Freenet, introduced by Irish student Ian Clarke, to enable anonymous online communication. This system offers a way for users to bypass government censorship, ensuring the free flow of information and ideas.
The dark web, therefore, plays a significant role in championing freedom of speech and promoting democratic values. It underscores the internet’s original promise: a space for free and open communication, unhindered by geographical barriers or political restrictions.
As we move forward, it’s essential to remember that the dark web, like any tool, can be used for good or ill. Its value lies in the hands of its users. At Upper Echelon Technology Group LLC, we understand this duality and strive to help businesses safely navigate the digital landscape. In the next section, we’ll discuss how you can protect your information and why cybersecurity measures such as dark web monitoring are essential.

Protecting Your Information: Dark Web Monitoring and Cybersecurity
In the vast expanse of the internet, the Dark Web is like a lurking predator, waiting to pounce on your personal and business information. As a responsible business owner in Wilmington, DE, you must understand the importance of cybersecurity and the role of Dark Web monitoring tools in protecting your data.
The Role of Dark Web Monitoring Tools
Dark Web monitoring tools are like your digital guardians. They continuously scan the underbelly of the internet for any traces of your personal and business information. Once your data is stolen and leaked through breaches, it becomes scattered across the web, making it impossible to completely erase from the internet.
However, with Dark Web monitoring tools, you can receive alerts when unauthorized activity surfaces on your credit report, or whenever your details appear on Dark Web sites, data brokers’ lists, or even in public records. This gives you the opportunity to act swiftly and minimize the damage.
How Upper Echelon Technology Group LLC Can Help Secure Your Data
At Upper Echelon Technology Group LLC, we go beyond merely fixing tech issues. We focus on your business needs, helping you leverage technology to improve efficiency and profitability.
Our cybersecurity-focused managed services are designed to protect your network around the clock, every day of the year, so that your technology serves your business instead of the other way around. We also offer identity theft protection services, such as Aura, which extensively monitors your personal information, bank accounts, passport, and driver’s license IDs, and other sensitive data on the internet, including Dark Web sites.
When you partner with Upper Echelon Technology Group, you’ll receive instant notifications if someone opens a new bank account in your name, if unauthorized activities appear on your credit report, or if any of your sensitive data is compromised in the event of a data breach. These scenarios are clear warning signs of identity theft, and our quick alerts facilitate immediate action.
Furthermore, our fraud resolution team is available 24/7/365 to guide you through any critical situation where you feel exposed or uncertain. With our help, you can rest assured that your business is protected against the hidden depths of the Dark Web, allowing you to focus on what matters most – growing your business.
Remember, the Dark Web may be a realm full of risks, but with vigilant monitoring and robust cybersecurity measures from Upper Echelon Technology Group LLC, you can navigate the digital landscape with confidence.
Conclusion: The Dual Nature of the Dark Web and Our Responsibility
In the grand scheme of things, the Dark Web, much like any technology, is a tool whose impact largely depends on how it’s used. It can be a haven for freedom fighters battling oppressive regimes and a sanctuary for journalists seeking the truth. But it can also be a breeding ground for illicit activities, from drug trafficking to money laundering and cybercrime.
Whether we like it or not, the Dark Web is a part of our interconnected world. As business owners, we must be aware of both its potential benefits and dangers. It is not enough to fear the Dark Web; we must understand it, navigate it cautiously, and harness cybersecurity measures to protect our businesses from its potential risks.
Key to this is a robust cybersecurity strategy. Drawing on the expertise of cybersecurity-focused managed services providers like Upper Echelon Technology Group LLC can help safeguard your business from potential Dark Web threats. They not only focus on fixing tech issues but also on understanding your business needs and leveraging your technology assets to boost your bottom line.
In conclusion, the Dark Web is a stark reminder of technology’s dual nature. It underscores the responsibility we all have, as internet users and business owners, to use technology ethically and safeguard our data vigilantly. The Dark Web’s hidden depths can be a source of fear, but armed with knowledge, precaution, and the right cybersecurity partner, we can rise above the challenges it presents.
So, let’s embrace this responsibility and make our corner of the digital landscape a safer place for our businesses and our customers. The Dark Web may be dark, but with the right approach, we can keep its shadows at bay.