Introduction: Understanding the Importance of a Cybersecurity Risk Profile
In the digital age, every click, every download, and every online transaction can potentially open a Pandora’s box of cyber threats. For small to medium-sized businesses in Wilmington, DE, the question isn’t if they will be targeted by cyber threats, but when. This is where the concept of a cybersecurity risk profile comes into play.
A cybersecurity risk profile provides an in-depth understanding of the types of threats your organization faces and how susceptible you are to these threats. It’s a crucial tool in the cybersecurity toolkit, helping businesses identify vulnerabilities and take proactive measures to mitigate potential cyber risks.
Creating a detailed cybersecurity risk profile is not just about protecting your business from threats; it’s also about promoting efficiency and driving profitability. When technology is used effectively and securely, it can become a significant driver for business growth.
In this article, titled ‘Unmasking Your Cybersecurity Risk Profile: What Lies Beneath?’, we’ll delve deep into the importance of a cybersecurity risk profile, how to create one, and how a cybersecurity-focused managed services provider like Upper Echelon Technology Group can help you navigate this crucial aspect of your business. So, let’s pull back the curtain and take a closer look at your cybersecurity risk profile.
Defining Cybersecurity Risk Profile
Consider the cybersecurity risk profile as the blueprint of your business’s cyber health. It’s a comprehensive analysis of the threats your organization faces and the dangers they pose. This profile helps you understand your risk landscape, enabling you to make informed decisions about where to allocate resources for threat prevention, detection, and response.
The Role of a Risk Profile in Cybersecurity
The risk profile plays a pivotal role in cybersecurity, acting as a compass guiding your security strategy. It provides a quantifiable understanding of risk by assigning numerical values to different threats and their potential impact.
Every organization has a unique risk profile that depends on several factors, including the assets it needs to protect, its goals, its ability to handle risks, and its willingness to do so. The profile helps organizations align their strategies and actions with their risk appetite, i.e., the level of risk they are willing to accept after implementing the necessary controls.
The Three Main Components of a Risk Profile: Risk Capacity, Risk Tolerance, and Risk Requirement
Just as an architect needs to understand the soil type, land slope, and local climate to design a building, you need to understand the three main components of a risk profile to build a solid cybersecurity strategy.
-
Risk Capacity: This is your business’s ability to withstand risk without jeopardizing its operations or objectives. You need to assess your company’s financial and operational capacity to absorb potential losses due to cyber threats.
-
Risk Tolerance: This is the level of risk your business is willing to accept. It’s a balancing act between securing assets and achieving business goals. For example, a company focused on innovation might tolerate more risk than a company in a highly regulated industry.
-
Risk Requirement: This component is directly tied to your business objectives and regulatory requirements. It’s the level of risk your company needs to take to achieve its goals and comply with industry standards or laws.
By understanding these three components, you can create a cybersecurity risk profile that not only protects your business but also supports its growth and success. Next, we will delve into the process of creating this essential tool for your cybersecurity strategy.
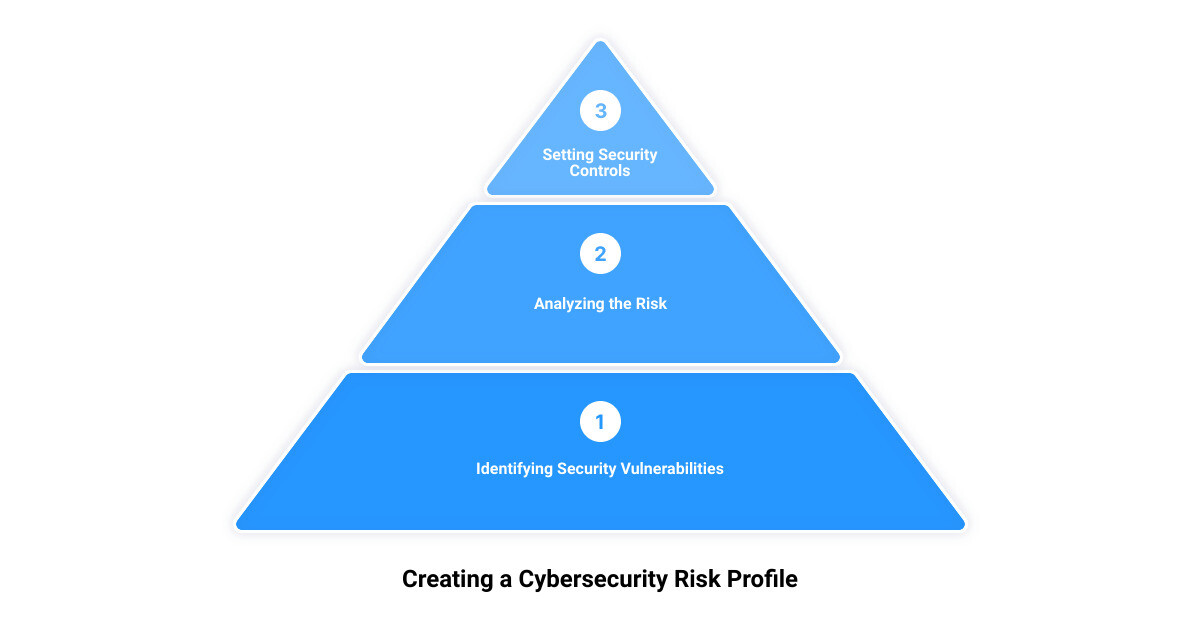
The Process of Creating a Cybersecurity Risk Profile
In the vast digital landscape where cyber threats lurk around every corner, creating a robust cybersecurity risk profile is akin to crafting your business’s personalized armor. This process, though demanding, can help your business become a well-fortified fortress. Let’s strip away the complexity and explore how Upper Echelon Technology Group can help you create an effective cybersecurity risk profile in eight comprehensive steps.
Step 1: Defining Cybersecurity Threats
The first step is to unmask the potential threats that could harm your business. This involves identifying the various tactics, techniques, and methods employed by cyber threat actors that could compromise your digital assets. High-quality, up-to-date cyber threat information sources such as the MITRE ATT&CK Knowledge Base and the Cyber Threat Alliance can aid in this process.
Step 2: Identifying Security Vulnerabilities
Next, we dig deeper to identify the vulnerabilities in your system. This includes potential weaknesses in your network, applications, and other IT assets that could be exploited by cyber threats.
Step 3: Determining Threat Likelihood and Threat Impact
This step involves assessing the probability of a threat occurring and the potential impact on your business. This requires a clear understanding of your business processes, the value of your digital assets, and the potential consequences of a security breach.
Step 4: Cataloging Information Assets
In this stage, we create an inventory of all your digital assets. This list should include not only your business’s crown jewels but also any assets that attackers might target as points of control or expansion.
Step 5: Assessing the Risk
Once the threats and vulnerabilities are identified, we assess the risk by determining the potential damage to your organization should a threat exploit a vulnerability. This assessment is usually based on the likelihood and potential impact of the threat.
Step 6: Analyzing the Risk
This step involves a more in-depth analysis of the assessed risks. This helps to prioritize the risks based on their severity and provides a clearer picture of where to focus your risk mitigation efforts.
Step 7: Setting Security Controls
After identifying and analyzing the risks, it’s time to set the appropriate security controls. These measures are designed to reduce the likelihood of a threat exploiting a vulnerability, and/or minimize the impact if a breach does occur.
Step 8: Monitoring and Reviewing Effectiveness
Finally, once the risk profile and security controls are in place, it’s essential to regularly monitor and review their effectiveness. This helps ensure that your cybersecurity strategy remains robust and relevant in the face of evolving threats.
The journey to unmask your cybersecurity risk profile may seem complex, but with the right guide, it becomes a manageable and worthwhile endeavor. Upper Echelon Technology Group stands ready to help you navigate this process, ensuring your business is not just another target in the cyber landscape but a stronghold secure from cyber threats.
Practical Example of a Risk Profile in Cybersecurity
Peeling back the layers of a risk profile can sometimes feel like navigating a maze. However, it gets simpler when we look at a practical example. So, let’s dive into an example of a cybersecurity risk profile for a risk-averse individual.
Risk-Averse Individual: Maintaining Portfolio Value Over High Returns
Imagine an individual who owns a small online business selling handmade crafts. This individual is not a risk-taker. Their primary concern is to maintain the value of their business portfolio—protecting customer data, securing financial transactions, and keeping their website safe from cyber attacks. They would prefer to invest in robust cybersecurity measures rather than chase high growth that could expose their business to increased cyber risks.
In creating a cybersecurity risk profile, we first define the threats. These could range from phishing scams targeting their emails, malware that could infiltrate their systems, or hackers attempting to breach their customer data.
Next, we identify security vulnerabilities. Maybe their website isn’t frequently updated, or their employees haven’t undergone recent cybersecurity training.
Determining the threat likelihood and impact would be the next step. If a phishing scam were successful, it might lead to a significant data breach, causing severe damage to the business’s reputation and financial standing.
After listing down the business’s digital assets, which include customer data, financial information, and their website, we assess the risk. Given their risk-averse nature, any threat that could significantly impact the business would be considered a high risk.
The next step would be to analyze the risk. We could find that while the business has a moderate risk of falling for a phishing scam, the impact would be high due to potential data breaches.
Following the analysis, we set the security controls. In this case, it could involve setting up a secure email gateway, regularly updating their systems, and conducting frequent cybersecurity training for employees.
Finally, the effectiveness of these controls should be monitored and reviewed regularly. The business might find that while the secure email gateway has efficiently curbed phishing attempts, their employees still show a lack of awareness in identifying potential cyber threats, indicating a need for more in-depth training.
This is a simplified example of how a cybersecurity risk profile is created and used. It provides a clear picture of the cyber risks a business faces, allowing it to set up effective defenses. Remember, it’s not about eliminating all risks—that’s nearly impossible. It’s about managing and mitigating risks to an acceptable level, and that’s what your cybersecurity risk profile helps you achieve.

Utilizing Tools for Cybersecurity Risk Assessment: The Cyber Risk Institute (CRI) Profile
As we venture deeper into the realm of cybersecurity risk management, it’s crucial to introduce you to a tool that has proven invaluable for financial institutions worldwide – the Cyber Risk Institute (CRI) Profile. Developed by the CRI, it is a global standard for cyber risk assessment.
Understanding the CRI Profile: A Global Standard for Cyber Risk Assessment
The CRI Profile is based on the National Institute of Standards and Technology’s (NIST) “Framework for Improving Critical Infrastructure Cybersecurity.” This efficient approach to cybersecurity risk management effectively combats the dynamic, evolving threats while providing adequate assurance to government supervisors. The CRI Profile harmonizes over 2,400 regulatory expectations into 277 control objectives, called diagnostic statements, thus making it an all-encompassing tool for risk assessment.
Regularly updated to reflect the evolving cybersecurity regulatory landscape, the CRI Profile has received global recognition from regulators and industry bodies. Not only does it give financial institutions a simple framework to rely on, but it also provides regulators with a consistent and widely understood framework.
The Benefits of Using the CRI Profile for Financial Institutions and Cloud Service Providers
The CRI Profile, particularly its extension, the CRI Cloud Profile, brings several benefits to financial institutions and cloud service providers (CSPs). It develops a mutual understanding of expectations between these parties, helping everyone to speak the same language. This simplifies regulatory engagements, setting a baseline understanding of requirements and responsibilities.
Moreover, it standardizes contractual terms and language, leading to efficiencies and highlighting key deployments for targeted analysis for cloud launch. It fully addresses the life cycle of the CSP and customer relationship. For financial institutions, the CRI Profile is not just a tool but a roadmap to securely do business in today’s digitally interconnected world.
As a small to medium-sized business owner, understanding these tools and approaches for cyber risk assessment is crucial. But how can you practically apply them to your business? That’s where a cybersecurity-focused managed services provider like Upper Echelon Technology Group comes in—offering personalized IT Managed Services that go beyond fixing tech issues to tailor services that meet your specific business needs. Let’s delve deeper into it in the next section.
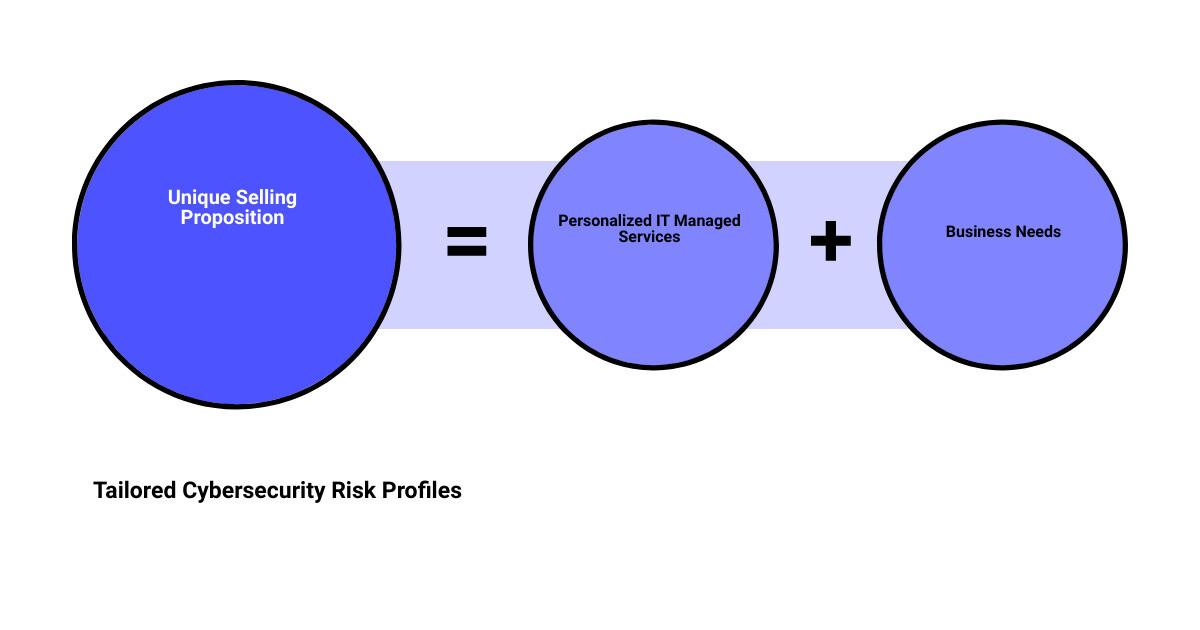
Tailoring Cybersecurity Risk Profiles: The Approach of Upper Echelon Technology Group LLC
The adage that no two businesses are the same holds especially true when it comes to cybersecurity. The unique nature of your business’s operations, assets, and risk tolerance means that a one-size-fits-all approach to cybersecurity just doesn’t cut it. Enter the Upper Echelon Technology Group LLC, a cybersecurity-focused managed services provider that understands the nuances of your business and crafts a personalized cybersecurity risk profile.
Personalized IT Managed Services: Beyond Fixing Tech Issues
At the heart of Upper Echelon Technology Group LLC‘s approach is the belief that IT Managed Services should go beyond just solving technology issues. This approach considers not only the technology side of things but, more importantly, how these tech solutions impact your business operations.
Their experts undertake a rigorous process of understanding your business, from its operational processes, its workforce efficiency, to its bottom-line profit. By doing so, they are able to identify how technology can improve your business’s efficiency and profitability. They then tailor cybersecurity solutions that align with these objectives, ensuring your technology serves your business, not the other way around.
Tailoring Services to Meet Specific Business Needs: The Unique Selling Proposition
What sets Upper Echelon Technology Group LLC apart is their personalized approach to IT Managed Services. Their team evaluates your business needs and leverages your technology assets to help you achieve your business goals. They understand that each business has unique needs and challenges, and their services are designed to cater to these specific requirements.
Moreover, they don’t just set up your cybersecurity defenses and leave you to it. They continuously monitor and review the effectiveness of these security controls, ensuring your network is protected and optimized 24/7/365.
In essence, Upper Echelon Technology Group LLC doesn’t just provide a service—they establish a partnership with your business. They work as a team with your business, striving to be a positive influence and to add value to your relationship. Their mission is to make your company more profitable by identifying areas where technology can improve your bottom line.
In today’s increasingly digital and interconnected world, understanding and managing your cybersecurity risk profile is crucial. By partnering with a provider like Upper Echelon Technology Group LLC, you can ensure your business is equipped with a tailored cybersecurity defense that addresses your specific needs and risks, ultimately contributing to your business’s overall success.
Conclusion: The Value of Unmasking Your Cybersecurity Risk Profile
Unmasking your cybersecurity risk profile isn’t an exercise in futility; rather, it’s a strategic process that helps protect your business from devastating cyber threats. As we navigate in this digital age, the importance of having a robust cybersecurity strategy cannot be overstated. By understanding your risk profile, you’re taking the first step toward a safer, more secure digital presence.
A sound cybersecurity risk profile doesn’t merely provide a snapshot of your business’s current cyber vulnerabilities; it also serves as a roadmap towards a more resilient future. By identifying potential threats and assessing their potential impact, you’re better positioned to implement effective security controls and continuously monitor their effectiveness. This proactive approach to cybersecurity significantly reduces the likelihood of digital attacks and minimizes the potential damages.
The role of a reliable IT Managed Services provider like Upper Echelon Technology Group LLC becomes invaluable in this process. By offering a personalized approach to managed services, the company not only solves your tech issues but it also leverages technology to enhance team efficiency and drive profitability. The key to this approach is understanding the unique needs of your business and tailoring services to meet those specific needs.
A comprehensive understanding of your cybersecurity risk profile, coupled with a partnership with a provider like Upper Echelon Technology Group, empowers you to navigate the digital landscape confidently. It allows you to focus on the crux of your business operations, knowing that your technological assets are secure and optimized.
In conclusion, unmasking your cybersecurity risk profile is not just about understanding the risks you face. It’s about transforming those risks into opportunities for growth and resilience. With the right approach and the right partner, you can turn cybersecurity from a potential threat to a strategic asset. The value of that transformation? It’s priceless.