As we navigate through an increasingly digital world, the risks and threats to our data and information systems are also growing, making cybersecurity a top priority for businesses of all sizes. One of the vital steps in managing these risks and ensuring the safety of our data is through a cybersecurity risk assessment.
Cybersecurity risk assessment is a systematic approach to evaluating an organization’s ability to protect its information and systems from cyber threats. It is a crucial component of any solid cybersecurity strategy, and its importance cannot be overstated. This process aids in the identification, evaluation, and prioritization of cyber risks that could potentially disrupt your organization’s operations.
By performing a cybersecurity risk assessment, companies can identify and understand their vulnerabilities, allowing them to make informed decisions about where to allocate resources for protection against potential cyber threats. It’s a process that goes beyond just fixing tech issues, it focuses on understanding your business needs and how you can leverage your technology assets in the most secure and efficient way possible.
In the following sections, we will delve deep into the world of cybersecurity risk assessment, exploring its significance, the steps involved in conducting one, and a real-life example of how a leading cybersecurity-focused managed services provider, Upper Echelon Technology Group, conducts their assessments. By the end of this guide, you will be well-equipped with the knowledge necessary to understand and implement a cybersecurity risk assessment in your own organization.
So, without further ado, let’s dive into this fascinating, intricate, and essential aspect of cybersecurity management.
The Importance of Cybersecurity Risk Assessment
In the vast, complex landscape of information technology, Cybersecurity Risk Assessment stands as an indispensable compass. It lights the way for businesses, guiding them in making informed decisions on cybersecurity strategies. In this section, we will delve into the key benefits of conducting regular cybersecurity risk assessments.
Insight into Valuable IT Assets
A risk assessment gives you a crystal-clear picture of where your most valuable IT assets reside. Whether it’s data stores, machines, or other IT assets, some are more important than others. The value and location of these assets can shift over time. Hence, regular risk assessments are crucial to keep track of these changes. This process helps you identify what needs to be protected the most, thereby ensuring that high-value assets aren’t left vulnerable.
Understanding of Risks and Vulnerabilities
Cybersecurity risk assessment is akin to a health check-up for your IT infrastructure. It identifies potential threats and vulnerabilities that could harm your business. By assessing these risks, you can focus on the areas that pose the highest potential impact and probability. This process can help you close gaps in your security, such as unpatched software, overly permissive access policies, and unencrypted data, that threat actors can exploit.
Cost Mitigation and Regulatory Compliance
The financial implications of a data breach can be staggering. A single breach can cost a business millions, not to mention the damage to its reputation. Regular security risk assessments not only safeguard your business from such a financial nightmare but also allow prudent budget allocation towards security initiatives that deliver the most value. Moreover, these assessments can help organizations comply with data security requirements of mandates such as HIPAA, PCI DSS, SOX, and GDPR, avoiding costly fines and penalties.
Improved Customer Trust and Informed Decision Making
In a world where data breaches make headlines, customers are more cautious than ever about who they trust with their personal information. A robust cybersecurity posture can significantly boost customer trust, which can, in turn, lead to improved client retention. Moreover, the detailed insights provided by a cybersecurity risk assessment can facilitate better decision-making regarding security, infrastructure, and personnel investments.
In short, a cybersecurity risk assessment is not just a defensive strategy—it’s a smart business move. In the next section, we will outline the steps involved in conducting an effective cybersecurity risk assessment.
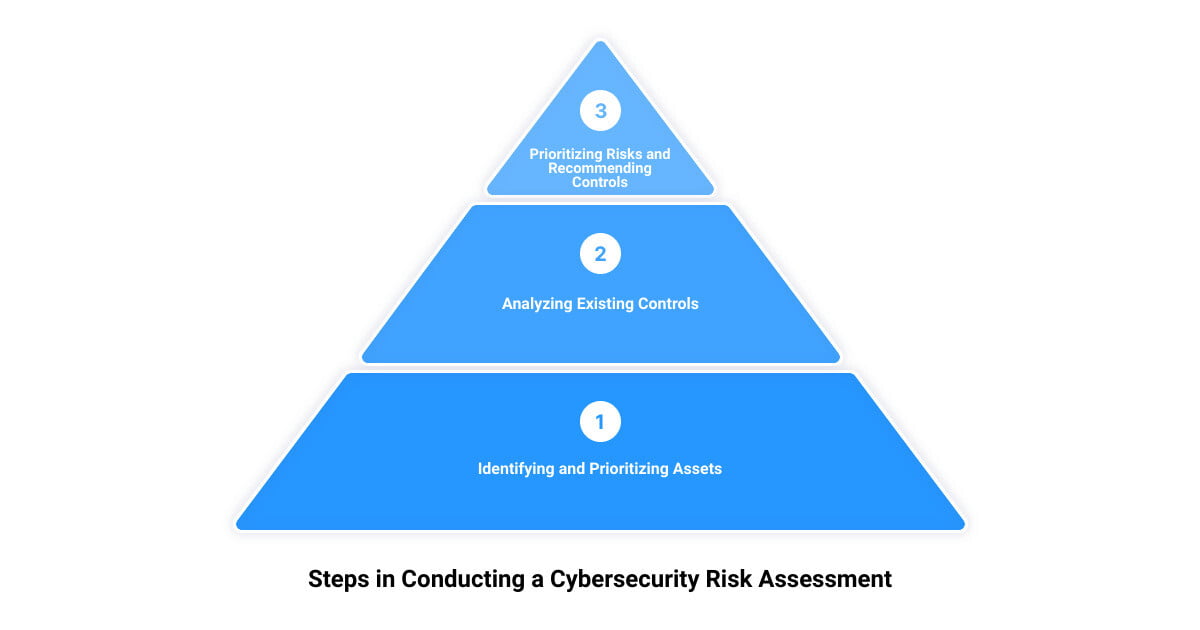
Steps in Conducting a Cybersecurity Risk Assessment
Navigating the digital landscape without a roadmap is like embarking on a journey blindfolded. A cybersecurity risk assessment provides that roadmap, illuminating the potential threats and vulnerabilities that could jeopardize your organization’s assets. Here’s how it’s done:
Identifying and Prioritizing Assets
The first step in a cybersecurity risk assessment involves identifying and prioritizing your organization’s IT assets. These could include hardware, software, data, networks, and even people. After identifying these assets, they are then prioritized based on their value to the organization. This could be their financial value, the importance of the data they hold, or their role in the organization’s daily operations.
Identifying Threats and Vulnerabilities
Once you have identified and prioritized your assets, the next step is to identify any threats and vulnerabilities that could compromise them. Threats could include hackers, malware, or even disgruntled employees. Vulnerabilities, on the other hand, are weaknesses in your systems that could be exploited by these threats. In this stage, it’s essential to focus on the discoverability, exploitability, and reproducibility of these threats and vulnerabilities, not just their historical occurrences.
Analyzing Existing Controls
Having identified your threats and vulnerabilities, you then need to analyze the existing controls in place to mitigate them. These controls could be technological, like encryption or intrusion detection systems, or they could be non-technical, like security policies or physical security measures. The aim is to evaluate how effective these controls are at preventing or mitigating the identified threats and vulnerabilities.
Determining the Likelihood of an Incident
The next step in the cybersecurity risk assessment process is to determine the likelihood of an incident. This involves assessing the probability that a threat can successfully exploit a vulnerability. Remember, a threat’s likelihood doesn’t necessarily correlate with previous occurrences—cybersecurity threats are dynamic by nature.
Assessing the Impact of a Threat
After determining the likelihood of an incident, you then need to assess the potential impact of a threat. This involves calculating the potential damage or loss that could occur if a threat successfully exploits a vulnerability. The impact could be financial, reputational, or operational.
Prioritizing Risks and Recommending Controls
With all this information in hand, you can now prioritize your risks and recommend controls. Risks are prioritized based on their likelihood and impact, and controls are recommended to mitigate the highest priority risks. This is where the organization’s risk tolerance level comes into play—any risk scenario that exceeds this level should be prioritized for treatment.
Documenting the Results
The final step in the cybersecurity risk assessment process is to document the results. This involves recording all identified risk scenarios in a risk register and storing them in a risk assessment report. This report should include details such as the risk scenario, identification date, existing security controls, current risk level, and a treatment plan outlining actions and timelines to reduce the risk to an acceptable level.
In summary, a cybersecurity risk assessment is a comprehensive process that involves identifying and prioritizing assets, identifying threats and vulnerabilities, analyzing existing controls, determining the likelihood of an incident, assessing the impact of a threat, prioritizing risks, recommending controls, and documenting the results. When conducted properly, it provides a clear roadmap for navigating the ever-evolving cybersecurity landscape.
Real-Life Example of a Cybersecurity Risk Assessment
Unveiling the curtains of theory, let’s delve into a real-life example of a cybersecurity risk assessment. This reflective exploration will provide us with a tangible understanding of the process, its nuances, and its significant benefits.
Case Study: Upper Echelon Technology Group LLC
We will focus on the Upper Echelon Technology Group LLC, a cybersecurity-focused managed services provider renowned for its personalized approach to IT Managed Services. This company stands as a beacon in the IT sector, not just fixing tech issues but leveraging technology assets to bolster business growth and profitability.
How Upper Echelon Technology Group Conducts Cybersecurity Risk Assessments
The Upper Echelon Technology Group follows a systematic procedure for their cybersecurity risk assessments, beginning with the identification of cyber threats. They then scrutinize security vulnerabilities within the organization, improving their understanding of threat likelihood and impact.
The process further includes the cataloging of information assets, followed by the risk assessment and analysis. These steps aid in accurately identifying the assets that could be affected by a cyber attack, such as hardware, systems, laptops, customer data, and intellectual property.
The process doesn’t stop here. In the next step, they set security controls and continuously monitor and review their effectiveness. This meticulous approach of identifying, evaluating, and prioritizing risks ensures that the organization’s operations, assets, and individuals are adequately safeguarded.
The Outcome and Benefits of the Risk Assessment
The cybersecurity risk assessment conducted by Upper Echelon Technology Group offers multiple benefits. First, it provides a clear understanding of the potential risks and vulnerabilities that the organization might face. This knowledge is instrumental in crafting robust preventive measures and response strategies.
Second, it helps in cost mitigation. By understanding the potential risks and their impact, the organization can allocate resources wisely to prevent cyberattacks, rather than spending heavily on damage control post-incident.
Finally, it enhances customer trust. In today’s digital world, customers need assurance that their data is safe. A comprehensive cybersecurity risk assessment showcases the organization’s commitment to data protection, thereby enhancing customer confidence.
In conclusion, the cybersecurity risk assessment conducted by Upper Echelon Technology Group LLC is an excellent example of how such assessments should be carried out. It not only identifies potential cyber threats and vulnerabilities but also aids in formulating effective strategies to combat them, thereby ensuring organizational security and customer trust.
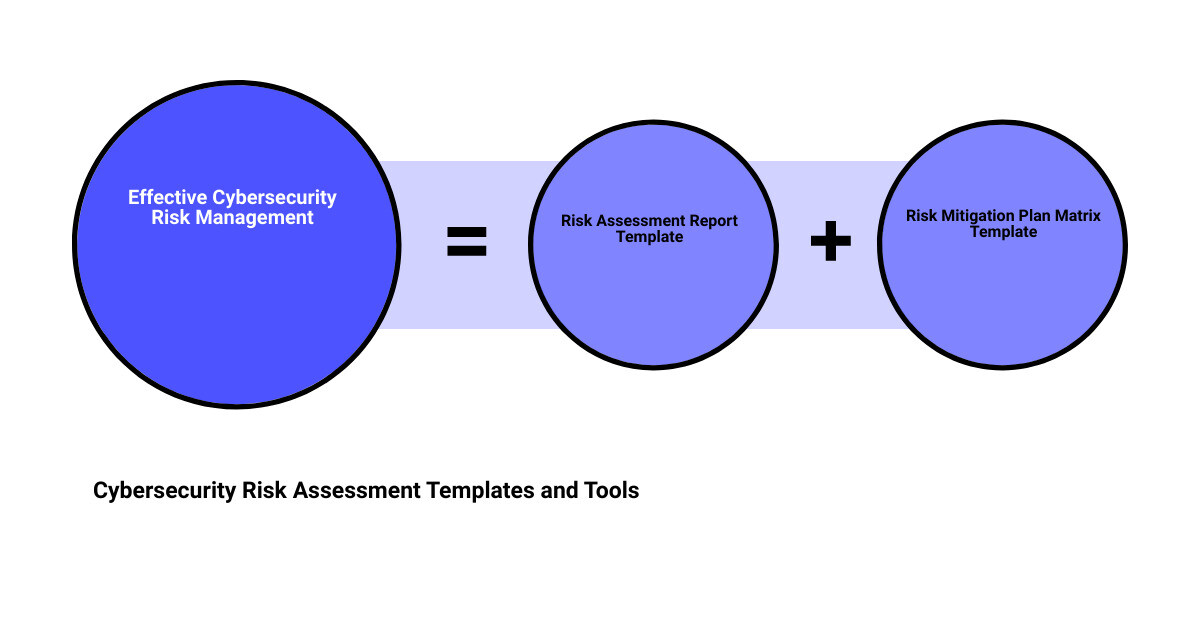
Cybersecurity Risk Assessment Templates and Tools
As the saying goes, “you can’t manage what you can’t measure.” When it comes to cybersecurity, knowing what and where your vulnerabilities are is half the battle. To do this effectively, it’s crucial to have the right templates and tools at your disposal. In this section, we’ll dive into various cybersecurity risk assessment templates and a powerful platform that can streamline your risk assessment process.
Simple Risk Assessment Template
First up is the Simple Risk Assessment Template. This easy-to-use tool allows you to identify and assess cybersecurity risks. You can customize the risk rating key to suit your cybersecurity criteria and use pre-built risk-level scoring to determine the acceptable level of risk for each aspect of your business. It’s the perfect starting point for establishing your cybersecurity risk-mitigation goals and plans.
Information Security Risk Assessment Template
Next, the Information Security Risk Assessment Template provides a comprehensive framework for assessing your information security risks. It includes a column for ISO 27001, allowing you to apply the International Organization for Standardization’s 14 information security standards steps to each of your cybersecurity risks. This template ensures your adherence to ISO 27001’s standards and, subsequently, your organization’s ISO cybersecurity and information security certification.
Risk Assessment Report Template
The Cybersecurity Risk Assessment Report Template is a step-by-step guide for assembling a solid cybersecurity risk assessment report. It includes sections for project ownership, risk management process, roles and responsibilities, financial impact, timeline impact, risk monitoring, risk categories, risk assessment matrix, mitigation grading matrix, and stakeholder tolerances. This comprehensive report plan template strengthens and standardizes your team’s cybersecurity strategy and risk-mitigation procedures.
Risk Assessment Checklist Template
The Cybersecurity Risk Assessment Checklist Template is a practical tool that covers all 14 ISO 27001 information security management steps. This checklist allows you to account for and optimize all your security components, preventing potential security risks.
Risk Mitigation Plan Matrix Template
With the Cybersecurity Risk Mitigation Plan Matrix Template, you can document cybersecurity risks quickly and accurately. It helps in listing risks, describing their potential impact, assessing their likelihood, designating an appropriate response, a contingency plan, and a trigger for each risk, and assigning an owner for each. This template is a real asset for evaluating cybersecurity risks and planning suitable responses.
Risk Breakdown Structure Diagram Template
Lastly, the visually dynamic Cybersecurity Risk Breakdown Structure Diagram Template helps you proactively identify cybersecurity risks and determine their likelihood and potential severity. It includes six pre-built diagram sections but can be customized to include the National Institute of Standards and Technology (NIST) Cybersecurity Framework components.
Smartsheet: A Platform for Cybersecurity Risk Assessment
Finally, let’s talk about Smartsheet, a flexible platform designed to make it easy to plan, capture, manage, and report on work from anywhere. It offers real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed. When it comes to cybersecurity risk assessment, Smartsheet can be a game-changer.
Having these templates and tools in your cybersecurity arsenal can significantly streamline your risk assessment process and fortify your cyber defenses. After all, in today’s digital world, staying one step ahead in cybersecurity is not just an option, but a necessity.
Conclusion: The Value of Cybersecurity Risk Assessment in Today’s Digital World
In the mesmerizing dance of zeros and ones that forms our digital world, cybersecurity risk assessment stands as a vigilant sentinel, protecting your business from unforeseen threats and vulnerabilities. The importance of this process is not just confined to securing your digital assets, but extends to protecting your business reputation, ensuring regulatory compliance, and enhancing customer trust.
The cybersecurity risk assessment conducted by Upper Echelon Technology Group LLC is a prime example of how this process can be effectively implemented in a real-life scenario. This cybersecurity-focused managed services provider doesn’t merely fix tech issues. Instead, it delves deeper, looking at the bigger picture of your business needs and leveraging your technology assets in the best way possible to promote business growth.
By identifying and prioritizing IT assets, recognizing threats and vulnerabilities, analyzing existing controls, determining the likelihood of an incident, assessing the impact of a threat, prioritizing risks and recommending controls, Upper Echelon provides a comprehensive cybersecurity risk assessment service. This not only safeguards your business from potential cyber threats but also enhances your team’s efficiency and contributes to your company’s profitability.
In the ever-evolving landscape of cybersecurity, risk assessments are no longer a luxury but a critical necessity. The complexity and diversity of today’s data security and network environments necessitate an ongoing, adaptive approach to identifying, assessing, and managing cybersecurity risks.
As a business owner, it is crucial to understand the value of a thorough cybersecurity risk assessment. It’s not just about avoiding fines or regulatory sanctions. It’s about preserving the integrity of your business, maintaining the trust of your customers, and ensuring the smooth operation of your digital infrastructure.
In conclusion, a cybersecurity risk assessment is a strategic investment that fortifies your business against the unpredictable future of cyber threats. When done right, it empowers you to navigate the digital world with confidence and peace of mind. So, as you continue to leverage technology for business growth, remember to keep cybersecurity risk assessments at the forefront. After all, in the intriguing world of cybersecurity, prevention is always better than cure!