Introduction: Understanding Cyber Vulnerability Assessment
In the digital battlefield of the 21st century, your business’s frontline defense is its cybersecurity measures. At the heart of these measures lies the crucial process of cyber vulnerability assessment. This process is a systematic examination of your network’s security posture, aimed at identifying, classifying, and prioritizing vulnerabilities in network infrastructure, computer systems, and applications. At the core of Upper Echelon Technology Group’s services, cyber vulnerability assessment is a crucial step towards making your company more efficient and profitable by identifying areas where technology can improve your bottom line.
A cyber vulnerability is essentially a security weakness that might expose your organization to cyber threats or risks. Threat actors are always on the prowl, looking for vulnerabilities they can exploit to breach applications, systems, and possibly entire networks. And new vulnerabilities don’t just magically appear – they can be introduced when new software and hardware components are added to your network.
Regular vulnerability assessments are your company’s lifeline, helping you stay ahead of the game by identifying and fixing these security weaknesses before they’re exploited. By employing automated testing tools such as network security scanners, your business gets a comprehensive vulnerability assessment report. This report serves as an invaluable guide, pointing out the areas that need attention and helping improve your overall security posture.
In the upcoming sections, we’ll dive deeper into the importance of cyber vulnerability assessment, the different types, and how Upper Echelon Technology Group’s unique approach to vulnerability assessment can help safeguard your business.
The Importance of Cyber Vulnerability Assessment
Cyber vulnerability assessment might seem like a daunting tech term, but it’s essentially your business’s health check for any cyber weaknesses. In today’s digital world, where cyber threats are becoming increasingly sophisticated, this assessment is not just important—it’s essential. Let’s explore why.
Early Identification of Threats
Like a regular check-up detects potential health issues, a cyber vulnerability assessment can help identify security threats before they become critical. As noted by HackerOne, organizations face constant cyber attacks, with threat actors constantly on the lookout for vulnerabilities to exploit.
An effective vulnerability assessment helps discover these weaknesses before they can be exploited, thus acting as a proactive shield against cyber threats. It’s a bit like having a security guard constantly patrolling your premises, keeping a vigilant eye out for any potential intruders.
Compliance with Cybersecurity Regulations
In addition to protecting your business, vulnerability assessment can also help ensure compliance with various cybersecurity regulations. Whether it’s HIPAA for healthcare, PCI DSS for businesses dealing with credit card transactions, or any other industry-specific regulations, a comprehensive vulnerability assessment can help you meet these regulatory demands.
Not complying with these regulations can result in hefty fines and damage to your company’s reputation. So, by conducting regular vulnerability assessments, you’re not just securing your business—you’re also ensuring it’s in line with the law.
Protection Against Data Breaches
Data is the lifeblood of any modern business. A data breach can cripple a company, leading to financial losses, eroding customer trust, and damaging the company’s reputation. As underlined by BeyondTrust, vulnerability assessments play a critical role in protecting systems and data from unauthorized access and data breaches.
By identifying vulnerabilities in your IT infrastructure, you can take necessary remedial actions to close these gaps, thereby protecting sensitive systems and information from potential breaches.
In summary, a cyber vulnerability assessment is a vital tool in your cybersecurity arsenal, helping to identify threats, ensure regulatory compliance, and protect against data breaches. Next, we’ll delve into the various components of vulnerability assessments and how they fit into an overarching IT risk management framework. Stay tuned!
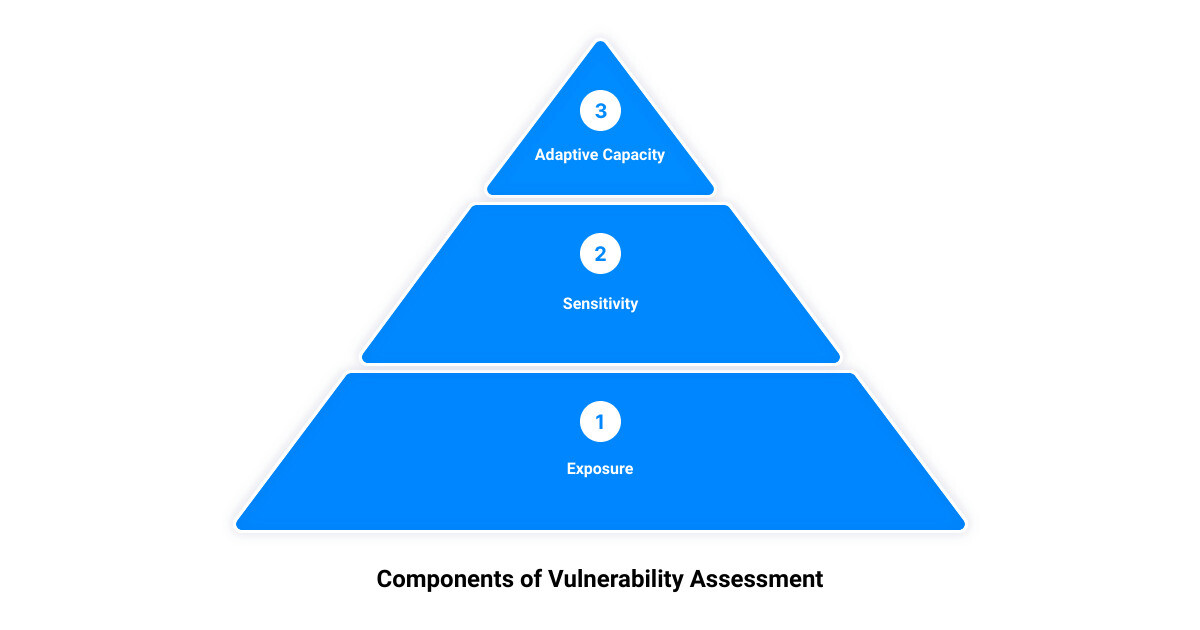
The Three Components of Vulnerability Assessment
The world of cybersecurity can often feel like a labyrinth, but understanding the different components of a vulnerability assessment can help you navigate it with confidence. These components – exposure, sensitivity, and adaptive capacity – function like the three legs of a stool, each equally critical to the overall stability of your cybersecurity efforts.
Exposure
Exposure refers to the extent to which your business’s IT systems are open to potential cybersecurity threats. It’s not just about the systems themselves, but also the ways they’re connected to the outside world. For example, a company with a large online presence could be more exposed to cyber threats compared to a smaller company with limited digital interaction. This component of vulnerability assessment is about identifying where and how your business could be exposed to cyber threats.
Sensitivity
Next up is sensitivity, which gauges the potential impact of a cyber threat on your business. This involves assessing how a breach in your IT systems could affect your operations, finances, and reputation. The higher the sensitivity, the more significant the potential damage. This is why businesses need to understand what data and systems are most sensitive to breaches, and take necessary precautions to protect them.
Adaptive Capacity
Last, but certainly not least, is adaptive capacity. This is essentially your business’s ability to respond to and recover from a cyber threat. It reflects your readiness to adapt and mitigate the consequences of a cyber attack, and can be improved through regular vulnerability assessments, employee training, and the implementation of robust cybersecurity measures.
In a nutshell, understanding the exposure, sensitivity, and adaptive capacity of your IT systems is key to conducting a comprehensive vulnerability assessment. This knowledge allows you to identify potential weak points, understand the implications of a breach, and ensure that you’re well-equipped to bounce back from a cyber attack. It’s not just about surviving in the digital world, but thriving in it. Let’s now explore the different types of vulnerability assessments you can conduct to strengthen your cybersecurity strategy.
The Five Types of Vulnerability Assessment
Peeling back the layers of your organization’s cybersecurity defenses will reveal a complex ecosystem of network connections, software applications, APIs, hosts, and wireless networks. Each of these elements has distinct vulnerabilities that cybercriminals could exploit, making it critical to conduct a variety of vulnerability assessments. Let’s delve into these five crucial types of vulnerability assessment.
Network-Based Vulnerability Assessment
A network-based vulnerability assessment serves as your organization’s first line of defense. This analysis identifies potential network security attacks by scanning your wired or wireless networks for any susceptible systems. It’s like a cybersecurity patrol, monitoring your network’s perimeters for any signs of weak spots that could invite unwanted intrusions.
Application-Based Vulnerability Assessment
Next up is the application-based vulnerability assessment, a crucial tool in the era of digital transformation where businesses heavily rely on software applications for operations. This assessment tests your organization’s websites and mobile applications for known software vulnerabilities and misconfigurations. It’s akin to a digital health check-up, making sure your applications are in the best shape to resist cyber threats.
API-Based Vulnerability Assessment
With the growing use of APIs to facilitate data exchange between software applications, an API-based vulnerability assessment has become increasingly important. This assessment checks the security of your APIs, ensuring they are not an easy entry point for cybercriminals to access and manipulate your organization’s critical data.
Host-Based Vulnerability Assessment
A host-based vulnerability assessment is like a deep dive into the security status of your servers, workstations, or other network hosts. This scan looks for vulnerable open ports and services, providing insights about the configuration settings and patch history of scanned systems. It helps ensure that the hosts in your network are not unwittingly hosting any security threats.
Wireless Network Vulnerability Assessment
Finally, as wireless networks become more pervasive, conducting a wireless network vulnerability assessment is a must. This scan identifies security weaknesses in your Wi-Fi network, checking for malicious access points and ensuring that your wireless networks are configured securely.
Understanding and implementing these five types of vulnerability assessments can significantly bolster your cyber defenses. But remember, the process doesn’t end there. Regular reassessment and remediation are key to maintaining a robust cybersecurity posture in an ever-evolving digital landscape. Next, let’s look at the four major areas you need to consider while performing a physical vulnerability assessment.
The Four Major Areas to Consider While Performing a Physical Vulnerability Assessment
In the quest to fortify your digital infrastructure, we must not overlook the critical role of physical security. A comprehensive vulnerability assessment should encompass both the virtual and the physical realms of your business operations. Let’s delve into the four major areas you need to consider when conducting a physical vulnerability assessment.
Identifying the Hazards
The first step in a physical vulnerability assessment is identifying potential hazards. This is a critical task that involves a thorough inspection of your business premises. From unauthorized access points to weak security systems, you need to uncover everything that could potentially become a gateway for security breaches. This process may involve assessing the security of doors, windows, and other access points, as well as evaluating the effectiveness of existing security measures such as locks, alarms, and surveillance systems.
Deciding Who Might Be Harmed and How
Understanding the potential victims of a security breach and the possible damage that could ensue is the second crucial area of a physical vulnerability assessment. This step involves identifying the individuals or groups who could be harmed if a security breach occurs and the nature of that harm. This could include employees, clients, or any other individuals who have access to or are located near your business premises. The harm could range from physical injury to data theft or damage to property.
Evaluating the Risks and Deciding on Precautions
Once potential hazards and victims have been identified, the next step is to evaluate the risks associated with each hazard and decide on appropriate precautions. This involves determining the likelihood of each hazard leading to a security breach and the potential severity of the consequences. Based on this information, you can decide on the necessary precautions to mitigate these risks. These precautions could include implementing stronger physical security measures, improving surveillance, or developing emergency response plans.
Recording Findings and Implementing Them
The final step in a physical vulnerability assessment is to record your findings and implement the identified precautions. This involves documenting all identified hazards, potential victims, risks, and precautions. This record serves as a valuable tool for tracking progress in enhancing your physical security and can guide future vulnerability assessments. Once the vulnerabilities and risks have been documented, it’s time to implement the necessary precautions. Remember, a vulnerability assessment is only as useful as the actions taken in response to its findings.
In the end, conducting a physical vulnerability assessment is a proactive measure that can significantly enhance your overall cybersecurity posture. By addressing the physical vulnerabilities of your business, you can create a more holistic and robust defense against potential security threats. At the Upper Echelon Technology Group, we understand the importance of comprehensive vulnerability assessments and are here to support you in safeguarding your business in every possible way.
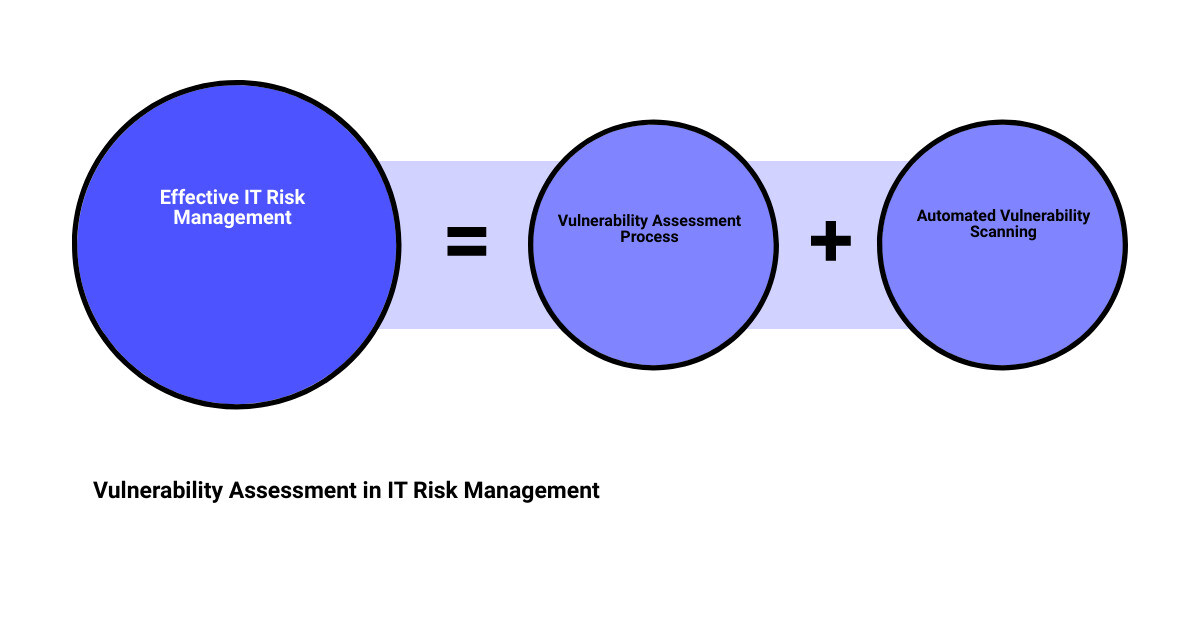
The Role of Vulnerability Assessment in IT Risk Management
Cracking the code to robust cybersecurity requires understanding the key role that vulnerability assessment plays in IT risk management. This process is akin to a medical check-up for your IT ecosystem, identifying any weaknesses that could potentially be exploited by cyber attackers.
The Process of Vulnerability Assessment
In the realm of cybersecurity, a vulnerability assessment is like a comprehensive health check for your IT infrastructure. It explores a vast range of potential vulnerabilities across multiple networks, systems, and other components of your IT ecosystem, whether on-premise or in the cloud. It helps to pinpoint weaknesses that need correction, including misconfigurations and policy non-compliance vulnerabilities that patching and maintenance alone may not address.
Moreover, vulnerability assessments assign a risk level to each threat identified. These risks are assigned priority, urgency, and impact levels, enabling your IT team to focus on areas that could cause the most damage to your business. This information is crucial in guiding IT teams and automated third-party tools like patch management in prioritizing vulnerabilities and charting the path for action, which often means remediation.
The Use of Automated Vulnerability Scanning Software
One of the most common methods of performing vulnerability assessments is through automated vulnerability scanning software. These tools use databases of known vulnerabilities to identify potential weaknesses in your networks, apps, systems, data, hardware, and more. Once the scans are completed, the tool will report on all the issues discovered and suggest actions to remove threats. The more advanced tools can even offer insight into the security and operational impact of remediating a risk versus accepting the risk.
The Importance of Regular Vulnerability Assessments
Just like regular health check-ups are vital for maintaining good health, regular vulnerability assessments are crucial for maintaining a robust cybersecurity posture. IT environments are constantly changing, and new threats continue to emerge. For instance, a simple software update or system configuration change could result in a new vulnerability. Therefore, it’s essential to identify and address vulnerabilities quickly to limit cybersecurity risk.
In conclusion, vulnerability assessments are an integral part of IT risk management, providing a systematic and comprehensive approach to identifying, prioritizing, and addressing threats. As your personalized IT Managed Services provider, Upper Echelon Technology Group is committed to helping you leverage this process to protect your business from cybersecurity threats, improve efficiency, and drive business growth.

Choosing the Right Vulnerability Scanning Tool
In the ever-evolving landscape of cybersecurity threats, choosing the right vulnerability scanning tool is as crucial as the air you breathe. The tool you select should not just identify potential risks but also provide actionable insights to safeguard your business. Here are the key considerations to keep in mind.
Frequency of Updates
In the digital world, threats are constantly emerging and evolving. Your vulnerability scanning tool should be able to keep up with these changes. It should receive regular updates that include the latest known vulnerabilities and potential threats. This ensures your business is always protected against the freshest cyber threats.
Quality and Quantity of Vulnerabilities
The tool should identify a large number of vulnerabilities, ensuring comprehensive coverage of potential threats. But remember, quality trumps quantity. The tool should also be capable of minimizing false positives and false negatives, which can waste valuable time and resources. A high-quality tool will provide precise and accurate vulnerability detection, helping you focus on real threats.
Actionability of Results
A vulnerability scanning tool should not just list potential vulnerabilities, it should provide actionable information on how to fix them. It should be able to suggest remedial actions to remove threats and may even provide insight into the security and operational impact of remedying a risk versus accepting it. This allows your risk managers to prioritize fixes against the overall cyber risk profile of your business.
Integrations with Other Vulnerability Management and IT Security Tools
The scanning tool should not exist in isolation. It should integrate seamlessly with other vulnerability management and IT security tools like patch management systems and Security Information and Event Management (SIEM) systems. This integration allows for a more holistic approach to threat analytics, providing a comprehensive view of your cybersecurity landscape.
At Upper Echelon Technology Group, we understand these nuances and offer expertise in helping you choose the right vulnerability scanning tool. We focus on your business needs and help you leverage your technology assets in the best way possible to protect your business. After all, a well-chosen vulnerability scanning tool is your first line of defense in the cybersecurity battleground.
The Unique Approach of Upper Echelon Technology Group LLC to Cyber Vulnerability Assessment
Picture this: a security approach that doesn’t just fix tech issues, but is intricately tuned to your business needs. That’s where the Upper Echelon Technology Group LLC steps into the picture. We’re not just another managed services provider. We’re a cybersecurity-focused partner that goes beyond the standard approach and brings a unique perspective to cyber vulnerability assessment.
Tailored Solutions for Your Business Needs
At the heart of our approach is our understanding that every business is unique and therefore requires a personalized approach to IT managed services. We don’t just “fix tech issues,” but focus on how your business can leverage technology to drive growth, increase efficiency, and improve your bottom line. It’s not just about identifying vulnerabilities, it’s about creating solutions that align with your business goals.
24x7x365 Network Protection and Optimization
Our team constantly evaluates the services and products that we offer to our clients. Our objective? To ensure that your network is not just protected, but optimized 24x7x365. When it comes to cyber vulnerability assessment, we believe in proactive rather than reactive strategies. This way, your technology serves your business, instead of you serving your technology.
More than Just Cyber Vulnerability Assessment
Our services extend beyond mere vulnerability assessments. We make your team more efficient by leveraging technology, and we identify areas where technology can improve your profitability. In essence, we help turn your technology into a strategic asset that supports your business growth.
Rooted in Core Values
Our commitment to our clients is rooted in our core values. We believe in open, honest, and productive communication, and we work as a true team striving to be a positive influence. We act like owners because we own it, and we have fun while we get stuff done. At the end of the day, it’s not just about providing services, it’s about building lasting relationships.
In conclusion, the Upper Echelon Technology Group LLC brings a unique blend of technical expertise, business acumen, and a commitment to client success to the table. With our help, you can make your company more secure, efficient, and profitable through effective cyber vulnerability assessment and IT management. Experience the difference today.
Conclusion: The Power of Proactive Cyber Vulnerability Assessment
Proactive cyber vulnerability assessment is the silent guardian that shields your business from the perils of the digital world. In the hands of a cybersecurity-focused managed services provider like Upper Echelon Technology Group LLC, it becomes a powerful tool that not only safeguards your cyber landscape but also propels your business towards growth and profitability.
The secret lies in the systematic approach to identifying, quantifying, and prioritizing vulnerabilities in your IT systems. Utilizing state-of-the-art vulnerability scanning tools, Upper Echelon Technology Group performs comprehensive scans on both internal and external fronts. These tools are regularly updated, ensuring a constant vigilance against emerging threats.
But it’s not merely about identifying threats. A crucial part of the process is understanding the impact of each vulnerability and crafting actionable strategies to mitigate them. With this approach, you receive a clear, concise report, enabling you to make informed decisions on prioritizing fixes against your organization’s overall cyber risk profile.
However, the work doesn’t stop there. In the ever-changing digital landscape, new vulnerabilities may arise from system updates and configuration changes. This necessitates regular vulnerability assessments, ensuring that your business maintains its shield against cyber threats.
In the end, a proactive cyber vulnerability assessment equips your business with the knowledge and tools to stand tall against potential cyber threats. It’s no longer about merely reacting to issues as they arise – it’s about anticipating and mitigating risks, creating a safer, more secure digital environment for your business.
As you navigate the complexities of the digital world, remember that you’re not alone. With Upper Echelon Technology Group LLC, you have a committed partner who understands your unique business needs and challenges. We’re here to help you leverage your technology assets in the best way possible, making your company more secure, efficient, and ultimately, more profitable.
In conclusion, it’s time to crack the code to a more secure future. It’s time to experience the power of proactive cyber vulnerability assessment with Upper Echelon Technology Group LLC.











