In a digital world where cyber threats are increasingly sophisticated, Cyber Threat Risk Assessment has become a necessity, not a luxury. It is an essential process for businesses of all sizes, particularly small to medium-sized businesses that often lack the dedicated IT resources of larger corporations. In this article, we delve into the art of uncovering hidden vulnerabilities through comprehensive cyber threat risk assessments.
Understanding and addressing potential vulnerabilities in your organization’s digital framework is crucial to protect your assets from cyber threats. By identifying these risks, you can implement measures to mitigate them, safeguarding your data, systems, and networks from potential breaches. More so, regular assessments ensure that your risk profiles are up-to-date, keeping pace with the ever-evolving world of cyber threats.
Let’s unpack this further as we explore the importance of cyber threat risk assessment, its key steps, types, and how a cybersecurity-focused managed service provider like Upper Echelon Technology Group can help. Through their personalized approach to IT Managed Services, they not only resolve tech issues but also aim to make your team more efficient and your company more profitable by leveraging technology assets to drive business growth.
Understanding Cyber Threat Risk Assessment: Definition and Purpose
In the realm of cybersecurity, knowledge is power – and a cyber threat risk assessment is your secret weapon. But what exactly is it, and why is it essential for your business?
A cyber threat risk assessment is a systematic evaluation of your organization’s IT infrastructure, from hardware and systems to customer data and intellectual property. Its purpose is to identify potential vulnerabilities and risks that could lead to cyberattacks, helping your business to stay one step ahead of cybercriminals.
This assessment is not a one-time event, but rather a continuous process. It begins with identifying your information assets and the threats they could face, followed by estimating and evaluating the risks associated with these threats. The final steps involve selecting security controls to mitigate these risks and consistently monitoring the risk environment for any changes.
Why is this crucial for your business? Without a thorough risk assessment, you could be blindly implementing cybersecurity measures. You might be spending time and resources to defend against threats that are unlikely to occur or won’t significantly impact your organization. Worse, you could be underestimating or overlooking risks that could cause substantial damage.
By conducting a cyber threat risk assessment, you ensure that your cybersecurity controls are tailored to the specific threats your organization faces. You can prioritize your resources effectively, tackling the most significant threats first. More importantly, you create a roadmap for continuously improving your cybersecurity posture, keeping your business safe in an ever-evolving threat landscape.
In the following sections, we will explore the steps involved in a comprehensive cyber threat risk assessment and how a managed services provider like Upper Echelon Technology Group can help you navigate this process. Armed with this information, you can master the art of cyber threat risk assessment and make it a powerful tool in your cybersecurity strategy.
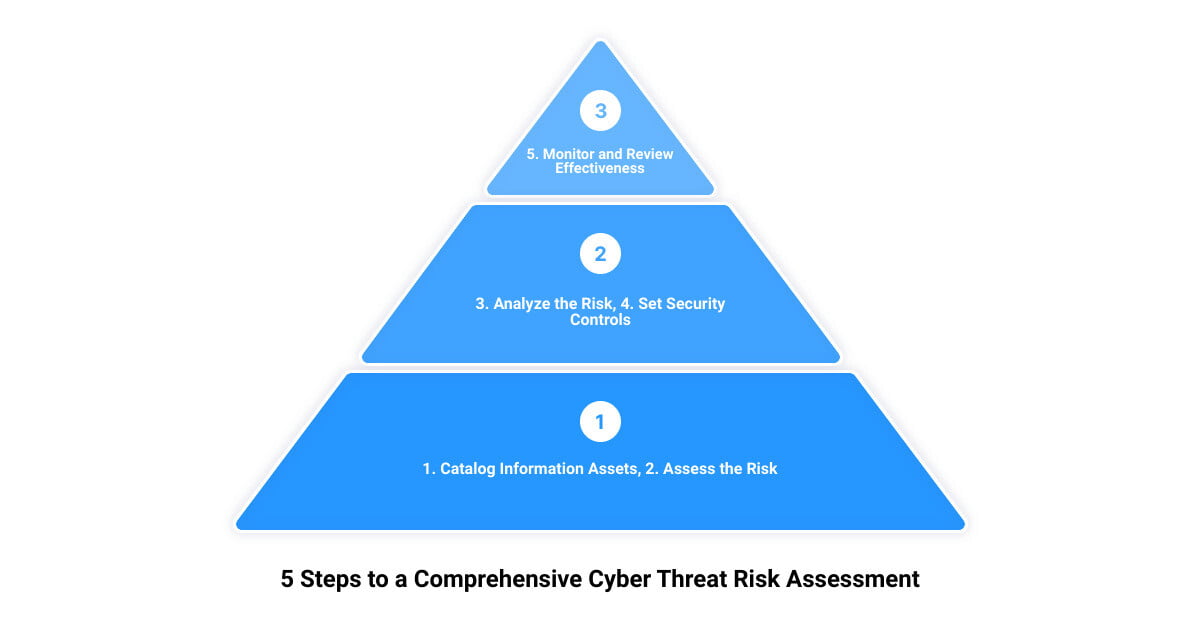
The Five Steps to a Comprehensive Cyber Threat Risk Assessment
Having a clear roadmap is essential when venturing into the complex terrain of cyber threat risk assessment. In the following sections, we’ll delve into a five-step process that can help you uncover hidden vulnerabilities and fortify your organization’s cybersecurity defenses.
Step 1: Catalog Information Assets
Like a librarian cataloging books, the first step in a cyber threat risk assessment is to identify and categorize your information assets. These assets include all data, hardware, and software that are integral to your business operations. This step is crucial as it helps you prioritize resources based on their importance and vulnerability to cyber threats.
Step 2: Assess the Risk
The second step is to assess the risk associated with each of the identified assets. This involves examining potential threats and vulnerabilities that could adversely affect the security of these assets. From malware attacks to data breaches, the threat landscape is vast and ever-changing. Therefore, a comprehensive understanding of these potential risks is key in this phase of the assessment.
Step 3: Analyze the Risk
Once you’ve identified the possible risks, the next step is to analyze them. This entails determining the likelihood of these threats materializing and the potential impact they could have on your organization. Through this analysis, you get a complete picture of your threat environment, enabling informed decision-making about the implementation of security controls.
Step 4: Set Security Controls
The fourth step involves setting up security controls to mitigate the identified risks. These could range from installing antivirus software and firewalls to implementing robust password policies and multi-factor authentication. The goal here is to reduce the overall risk to a level that your organization is comfortable with.
Step 5: Monitor and Review Effectiveness
Finally, the effectiveness of the implemented security controls needs to be continuously monitored and reviewed. Cyber threats are not static; they evolve and adapt rapidly. Hence, your cybersecurity measures must also be dynamic and adaptable. Regular monitoring helps identify any gaps or weaknesses in your security controls and enables timely adjustments.
Mastering the art of cyber threat risk assessment isn’t a one-time event but a continuous process. It’s about staying vigilant and always being one step ahead of potential cyber threats. As a cybersecurity-focused managed services provider, Upper Echelon Technology Group can guide you through this process, ensuring your technology serves your business, rather than becoming a liability.
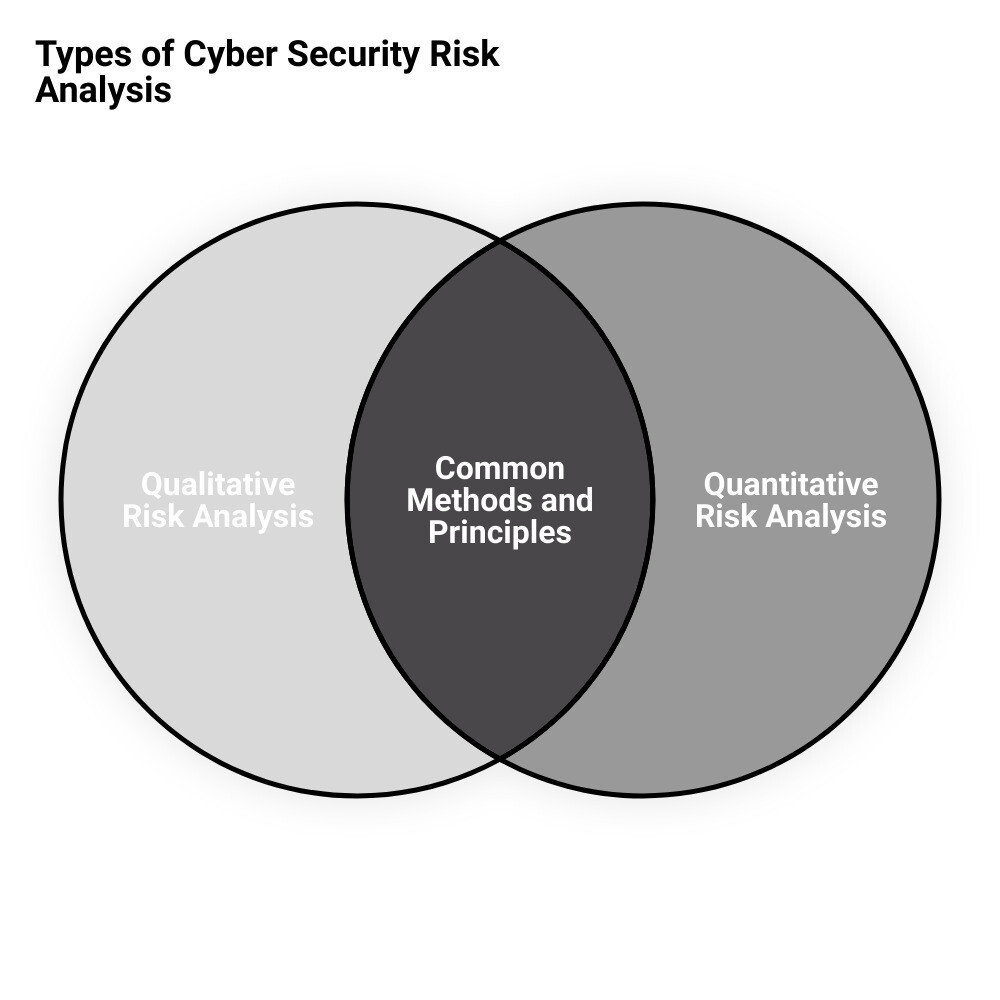
Types of Cyber Security Risk Analysis: Qualitative and Quantitative
When it comes to cyber threat risk assessment, not all methods are created equal. Depending on the specific needs and resources of your business, you may opt for a Qualitative Risk Analysis or a Quantitative Risk Analysis. Both methods have their strengths and are essential for a comprehensive understanding of your cybersecurity landscape.
Qualitative Risk Analysis
The qualitative approach is like an initial reconnaissance of your cybersecurity terrain. It identifies the probability and impact of potential threats in a non-numerical, descriptive format. This method involves categorizing risks into levels such as low, medium, or high based on their potential impact and likelihood of occurrence.
For instance, a minor software glitch might be categorized as a low risk, while a widespread data breach would likely be considered a high risk. This approach is useful for providing an overall picture of your cybersecurity posture and identifying areas that require immediate attention.
Quantitative Risk Analysis
On the other hand, the quantitative method takes the analysis to a more granular level. It involves assigning numerical or monetary values to potential risks and their impacts. This method can provide a clearer view of the potential effect on project objectives or business goals if the risk were to materialize.
For example, you might calculate the cost of a data breach by estimating the potential fines, the cost of emergency IT support, and potential loss of business due to reputational damage. This kind of analysis can provide your business with specific data, enabling more informed decision-making and resource allocation.
Ultimately, the choice between qualitative and quantitative risk analysis will depend on your company’s specific needs and resources. However, a comprehensive cyber threat risk assessment will often incorporate both methods, providing a holistic view of your company’s cybersecurity landscape and paving the way for effective risk mitigation strategies. That’s where a cybersecurity-focused managed services provider like Upper Echelon Technology Group comes into play, offering expert guidance in navigating these complex processes.
Conducting a Cyber Threat Risk Assessment: A Step-by-Step Guide
Risk lurks in the shadows of every digital realm, ready to pounce and disrupt your business operations. Without a comprehensive cyber threat risk assessment, your organization is like a ship sailing in the stormy sea without a compass. Let’s illuminate the pathway to a safer digital environment by exploring the critical steps involved in conducting a cyber threat risk assessment.
Characterize the System at Risk
Just as a doctor can’t treat a patient without a thorough examination, you can’t safeguard your IT infrastructure without a deep understanding of its components. The first phase of a successful cyber threat risk assessment involves identifying and documenting your network asset vulnerabilities. You must inventory your IT assets, which may include hardware, software, data, networks, and people, and assess the potential risks and vulnerabilities associated with each. This step provides a necessary roadmap for where defenses need to be fortified.
Identify Specific Threats to the System
Not all threats are created equal, and they certainly don’t all target the same areas. Armed with an understanding of your IT assets, it’s time to identify and document internal and external threats. You can harness cyber threat intelligence to help identify these risks. This intelligence could be sourced from organizations like CISA and US-CERT, or cybersecurity companies, and even from your own past cyberattacks. Scanning systems for indicators of compromise (IoCs), scrutinizing log files for unusual behavior, and auditing configuration files for insecure settings or unauthorized changes are some of the activities involved in this step.
Determine Inherent Risks and Impacts
Finally, it’s time to evaluate the potential impact of the identified cyber threats on your organization. A ransomware attack on your corporate database, for instance, will have much more severe consequences than a similar attack on a single user’s workstation. Understanding these impacts is essential to quantifying the risk that each threat poses. You can then determine the likelihood of each type of attack using the cyber threat intelligence and quantify risk based on the combination of the likelihood and impact of each threat.
Conducting a cyber threat risk assessment may seem like a towering task, but remember, you’re not alone in this journey. Managed services providers like Upper Echelon Technology Group specialize in guiding businesses through these processes, ensuring that your digital assets are well-protected from cyber threats. The next step? Identifying and prioritizing your risk responses, which we’ll delve into in the following section.
The Cyber Security Risk Assessment Matrix: Scoring Risks for Your Organization
Just as each business is unique, so too are their cybersecurity risks. The Cyber Security Risk Assessment Matrix is a tool that allows you to score and prioritize these risks, providing a clear path for your organization’s cybersecurity efforts.
This matrix is essentially a table where you outline and score potential cybersecurity threats based on their likelihood of occurrence and their potential impact on your business. This scoring system allows you to quickly identify which threats require immediate attention and which can be monitored for future developments.
The process of creating a Cyber Security Risk Assessment Matrix involves several steps which align with the National Institute of Standards and Technology (NIST) cyber security risk assessment process. These include identifying and documenting network asset vulnerabilities, using sources of cyber threat intelligence, identifying internal and external threats, identifying potential mission impacts, and finally, using these threats, vulnerabilities, and impacts to determine risk.
Identifying and Documenting Network Asset Vulnerabilities
The first step in creating a risk assessment matrix is to identify and document network asset vulnerabilities. This involves a comprehensive inventory of your IT assets and an assessment of the potential risks and vulnerabilities associated with each.
Using Sources of Cyber Threat Intelligence
Next, you need to utilize sources of cyber threat intelligence. This information, which can be internal or external, will aid in identifying cybersecurity risks. Many organizations, including the CISA, US-CERT, and cybersecurity companies like Upper Echelon Technology Group, offer access to cyber threat intelligence feeds.
Identifying Internal and External Threats
Once you have a clear understanding of your IT assets and potential threats, you can begin identifying both internal and external threats. This may include scanning systems for indicators of compromise (IoCs), inspecting log files for unusual behavior, and checking configuration files for insecure settings or unauthorized changes.
Identifying Potential Mission Impacts
The fourth step in creating a risk assessment matrix is identifying potential mission impacts. Different cybersecurity risks will have varying impacts on your organization. For instance, a ransomware infection on your corporate database could have a more significant impact than a similar attack on a single user’s workstation.
Determining Risk
The final step involves determining the risk associated with each identified threat and vulnerability. Using the information gathered so far, you can quantify the risk based on the combination of the likelihood and impact of each individual threat.
Each of these steps helps to build a comprehensive Cyber Security Risk Assessment Matrix, providing a clear picture of your organization’s potential cybersecurity risks. This matrix is not static but should be continually updated and reviewed to reflect changes in your risk environment and evolving cyber threats.
By using a Cyber Security Risk Assessment Matrix, you can ensure that your organization’s cybersecurity measures are as effective and efficient as possible, safeguarding your business from the ever-present threat of cyber attacks. Remember, cybersecurity is not a one-time task, but a continuous process that requires vigilance and proactive management. This is where managed services providers like Upper Echelon Technology Group can provide invaluable support, offering expertise and resources to ensure your organization’s cyber defenses are robust and resilient.
The Role of Managed Services Providers in Cyber Threat Risk Assessment: A Case Study of Upper Echelon Technology Group LLC
In the dynamic landscape of cybersecurity, the role of managed services providers (MSPs) is crucial. They not only handle the day-to-day IT operations but also shoulder the responsibility of safeguarding the company’s digital assets. Let’s unravel how Upper Echelon Technology Group, a cybersecurity-focused MSP, masters the art of cyber threat risk assessment.
Upper Echelon Technology Group LLC, with its offices in PA, DE, and FL, provides a personalized approach to IT managed services. They understand that technology should serve the business, not the other way round. Their best-of-breed managed IT services are designed to keep your network protected and optimized 24x7x365.
Expertise in Identifying Hidden Vulnerabilities
One of the key offerings of Upper Echelon is its expertise in identifying hidden vulnerabilities in your network. A comprehensive cyber threat risk assessment is a crucial part of their managed IT services. They understand that every company has a unique set of digital assets and potential threats. Their personalized approach allows them to tailor the threat assessment process to the specific needs of each business.
Leveraging Technology for Efficiency and Profitability
Upper Echelon is not just about ‘fixing tech issues’; they aim to make your team more efficient by leveraging technology. They identify areas where technology can improve your bottom line, making your company more profitable. The risk assessment process helps in identifying potential cyber threats that could hamper the efficiency and profitability of your business.
Continuous Monitoring and Review
As mentioned earlier, cybersecurity is a continuous process that requires vigilance. Upper Echelon understands this and offers ongoing monitoring and review of your network’s security controls. They ensure that your defenses remain robust and resilient against the evolving cyber threats.
Enhancing Business Relationship with Value-Added Services
The value Upper Echelon brings to a business relationship goes beyond the basic IT services. They offer various value-added services like backup and disaster recovery solutions, cloud hosting services, and endpoint management. These services further strengthen the security posture of your business.
In conclusion, the role of a managed services provider like Upper Echelon Technology Group LLC in cyber threat risk assessment is multifaceted. They not only identify and assess cyber threats but also offer solutions to mitigate these threats. Their personalized approach ensures that your network is protected, your team is efficient, and your business is profitable.
Conclusion: The Continuous Process of Cyber Threat Risk Assessment
As the digital landscape continues to evolve, so do the threats that lurk within it. Cyber threat risk assessment is not a one-time event but an ongoing, cyclical process. It requires constant vigilance to stay ahead of the curve, continually identifying potential weaknesses, evaluating the risk they pose, and implementing appropriate security measures.
The Upper Echelon Technology Group LLC, a top-tier managed services provider, understands the dynamic nature of cybersecurity threats. More than just a cybersecurity-focused provider, they are a partner in your business’s growth and success. They take a personalized approach to IT Managed Services, going beyond just solving tech issues. They work with you to optimize your team’s efficiency and leverage technology to drive profitability.
This constant process of risk assessment is embedded in the core of their services. They believe that cybersecurity is not a destination but a journey that involves continuous learning, adapting, and evolving. It’s about staying proactive, anticipating threats before they happen, and being prepared to respond swiftly and effectively when they do.
In the face of ever-evolving cyber threats, it’s crucial to have a cybersecurity partner that understands your business’s unique needs and challenges. The Upper Echelon Technology Group LLC is that partner. They offer a blend of expertise, personalized service, and cutting-edge technology solutions to help keep your business secure, efficient, and profitable.
Remember, in the cyber landscape, the only constant is change. Stay ahead of the curve with continuous cyber threat risk assessment. After all, the safety and success of your business might just depend on it.