Introduction: The Importance of Cyber Security Risk Assessments
In an increasingly digital world, cyber threats lurk in every corner of the internet, waiting to exploit vulnerabilities in your business network. The importance of cyber security risk assessments cannot be overstated. These assessments provide the first line of defense against potential cyber attacks, ensuring your business is fortified against the myriad of threats that could wreak havoc on your operations.
Conducted by experts in the field, a cyber security risk assessment identifies the various information assets that could be affected by a cyber attack. These assets can range from hardware and systems to customer data and intellectual property. The assessment doesn’t stop there. It goes on to evaluate the various risks that could affect those assets, helping you select the appropriate controls to treat the identified risks.
Without such assessments, your business could be left exposed to threats that could cost significant time, effort, and resources to remedy. Worse yet, these threats could lead to severe financial and reputational damage that could be challenging to recover from. Therefore, implementing a comprehensive cyber security risk assessment is a crucial step in safeguarding your business in the digital age.
This article, titled ‘Unveiling the Hidden Threats: Unconventional Cyber Security Risk Assessments’ will help you better understand the ins and outs of cyber security risk assessments, their importance, and how a cybersecurity-focused managed services provider like Upper Echelon Technology Group LLC can help protect your business from cyber threats.
As a small to medium-sized business owner in Wilmington, DE, it’s vital to stay ahead of the curve, leveraging technology to drive business growth. This starts with understanding and mitigating the potential risks associated with your digital operations. Stay tuned to unravel the complexities of cyber security risk assessments, and discover how they can be a game-changer in your business’s security strategy.
Understanding Cyber Security Risk Assessments
In the digital landscape, where threats are always evolving, understanding cyber security risk assessments is the first step towards robust data protection.
What is a Cyber Security Risk Assessment?
A cyber security risk assessment is a systematic process to identify, analyze, and evaluate potential risks that could affect an organization’s information assets. These assets could range from hardware and systems to customer data and intellectual property. The goal is to pinpoint threats that could exploit vulnerabilities and compromise the security of your assets. As Wilmington DE Managed IT Services, Upper Echelon Technology Group LLC, perfectly puts it, without a risk assessment to guide your security decisions, you could end up wasting resources on unlikely threats or overlook risks that could cause significant damage.
Why are Cyber Security Risk Assessments Essential?
The importance of cyber security risk assessments cannot be overstated. They ensure that the cyber security controls you select are tailor-made to address the risks your business faces. This is vital because, in the absence of an informed risk assessment, you might underestimate or ignore risks that could potentially cause significant harm. For this reason, many best-practice frameworks, standards, and laws, including the GDPR (General Data Protection Regulation), mandate the conduct of risk assessments. Furthermore, these assessments help you optimize resources by focusing on high-priority threats, ensuring that your defense strategy is both effective and cost-efficient.
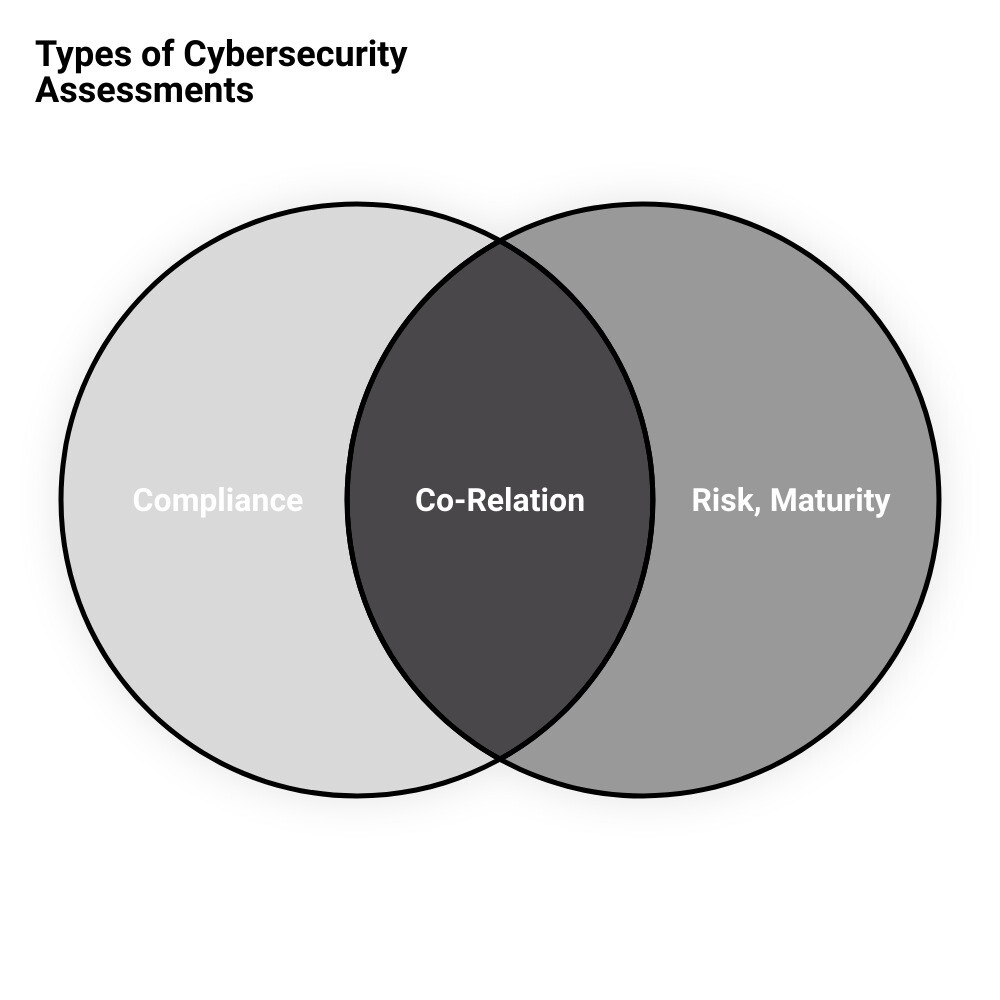
The Three Main Types of Cybersecurity Assessments: Compliance, Risk, and Maturity
There are three main types of cybersecurity assessments that your business should be aware of.
- Compliance assessments measure your organization’s compliance with relevant regulations and standards.
- Risk assessments, as we’ve discussed, identify potential threats and vulnerabilities that could compromise your security.
- Finally, maturity assessments evaluate your organization’s cybersecurity capabilities and preparedness. They gauge your ability to respond to and recover from security incidents.
Each of these assessments plays a crucial role in building a comprehensive cybersecurity strategy. They ensure that all bases are covered, from regulatory compliance and risk management to the continuous improvement of your cybersecurity posture. Armed with this understanding, you can better navigate the complex terrain of cyber security risk assessments and build a strong defense against digital threats.
The Process of Conducting a Cyber Security Risk Assessment
Unmasking the invisible enemy requires a methodical approach. Conducting a cyber security risk assessment is a step-by-step process that involves understanding your organization’s risk context, defining the scope, identifying assets, assessing threats and vulnerabilities, and estimating the likelihood of an attack.
Step 1: Establishing the Context for Risk Management
Every organization is unique, with its own set of objectives, assets, and vulnerabilities. The first step in a cybersecurity risk assessment is to establish the context for risk management. This involves determining your business objectives and identifying the IT assets essential to achieving these objectives. Your risk management context helps you understand the potential impact of a cyber attack on your organization.
Step 2: Defining the Scope of the Risk Assessment
Scope definition is crucial. It ensures that the risk assessment covers all areas of potential cyber risk within your organization. This could include systems, hardware, customer data, intellectual property, and other key business assets. The scope should be comprehensive enough to identify all potential cyber risks while being specific enough to be manageable and actionable.
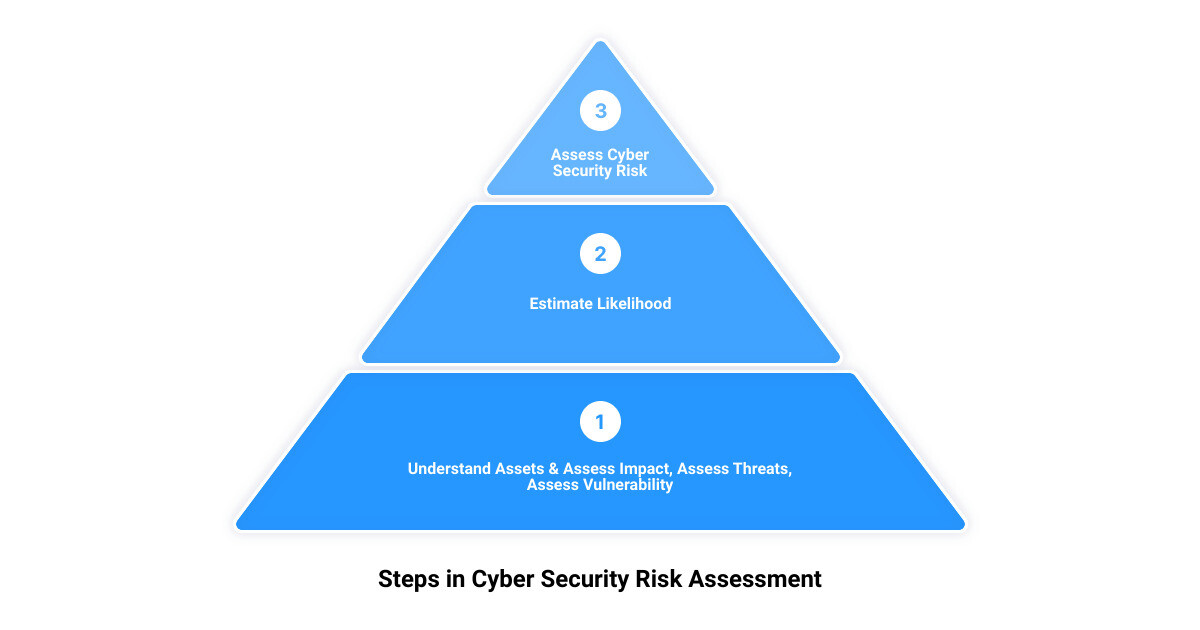
Step 3: Understanding Your Assets and Assessing Impact
A clear understanding of your assets and the potential impact of a cyber attack on these assets is vital. This involves identifying the value of each asset, the potential threats they could face, and the potential impact on your organization should they be compromised. The impact could be measured in terms of financial loss, reputational damage, or operational disruption.
Step 4: Assessing the Threat
Threat assessment involves identifying the various cyber threats that could potentially harm your assets. This could include malware, phishing attacks, DDoS attacks, or insider threats. Understanding the nature and potential impact of these threats on your organization is crucial in formulating a robust cyber defense strategy.
Step 5: Assessing Your Vulnerability
Vulnerability assessment involves identifying loopholes or weaknesses in your IT systems that could be exploited by threat actors. These vulnerabilities could exist in your network, systems, or even your people, processes, and procedures. Identifying vulnerabilities is crucial to taking proactive measures to strengthen your defenses.
Step 6: Estimating Likelihood
Once you understand your assets, threats, and vulnerabilities, you must estimate the likelihood of a cyber attack. This involves assessing the probability of a threat exploiting a vulnerability. This estimation helps you prioritize risks and focus your resources on the most likely and potentially damaging threats.
Step 7: Assessing Cyber Security Risk
Finally, all these elements come together in the risk assessment step. Here, you calculate the potential risk by combining the likelihood of an attack with the potential impact on your organization. This comprehensive risk picture allows you to make informed decisions about where to implement security controls, helping to reduce overall risk to a level your organization is comfortable with.
Conducting a cyber security risk assessment is a complex yet critical process that helps organizations understand and manage their cyber risks. By following these steps, you can systematically identify, analyze, and evaluate risks, providing a solid foundation for your cybersecurity strategy.
NIST Risk Assessment: A Comprehensive Approach to Cyber Security
Navigating the complex world of cyber security can quickly become overwhelming. That’s where the NIST Risk Assessment comes into play, serving as a comprehensive and standardized approach to evaluating cyber threats.
Understanding NIST Risk Assessment
The NIST (National Institute of Standards and Technology) Risk Assessment is a process designed to identify risks to organizational operations, assets, individuals, and even the nation, stemming from the operation of an information system. This framework doesn’t just identify potential issues; it also offers guidance on how to mitigate them effectively.
The goal of this approach is not to eliminate all risks – an impossible feat in the ever-evolving cyber landscape – but to manage them to an acceptable level. It’s about understanding where your vulnerabilities lie and taking proactive steps to protect those areas.
How NIST Risk Assessment Helps in Identifying Risks
The power of the NIST Risk Assessment lies in its thoroughness. It dives deep into your organization’s information systems, identifying potential risks that might otherwise go unnoticed. By considering every facet of your operations, from your mission and functions to your reputation and assets, this assessment ensures that no stone is left unturned in the battle against cyber threats.
Importantly, it identifies both the likelihood of a risk event occurring and the potential impact it would have. This dual focus on probability and impact allows organizations to prioritize their risk management efforts effectively, focusing their resources where they’re most needed.
NIST Cybersecurity Risk Assessment Template: A Useful Tool for Organizations
To streamline the process, NIST provides a Cybersecurity Risk Assessment Template. This tool is designed to guide organizations through the risk assessment process, ensuring they don’t miss any critical steps along the way.
The template provides a step-by-step guide for identifying and assessing risks, making it an invaluable resource for any company looking to enhance its cyber security measures. It’s adaptable and flexible, allowing it to be tailored to the unique needs and contexts of different organizations.
In essence, the NIST Risk Assessment and its accompanying template provide a roadmap for navigating the often confusing and complex world of cyber security. By following this framework, organizations can be confident they’re doing everything they can to protect their operations from the ever-present threat of cyber attacks.
Cybersecurity Key Risk Indicators: Measuring Potential Risks
Are you driving your business down the cybersecurity highway with your eyes closed? It’s time to open your eyes and pay attention to your Cybersecurity Key Risk Indicators (KRIs).
What are Cybersecurity Key Risk Indicators?
KRIs are crucial metrics that provide a quantifiable measure of potential risks associated with specific decisions or everyday operations within an organization, regardless of its size. Picture KRIs as the dashboard of your car, providing real-time information on the health and performance of your business’s cybersecurity efforts. They allow you to identify vulnerabilities, measure the effectiveness of your risk management strategies, and make informed decisions to enhance your security posture.
How KRIs Measure Potential Risks
KRIs are not about measuring the consequences of past breaches but rather predicting potential future risks. They focus on quantifiable data that can provide insights into potential vulnerabilities and threats. This data might include the number of failed login attempts, the number of unpatched systems, or the amount of sensitive data shared externally. The goal is to identify patterns and trends that could signify an impending cyber attack, allowing you to take proactive measures to mitigate risks.
The Role of KRIs in Security Reporting to the Executive Level
KRIs play a significant role in communicating the state of cybersecurity to the executive level in an organization. They provide a concise, data-driven snapshot of the organization’s cyber risk landscape. Executives often have to make critical decisions based on these reports. Therefore, it’s essential to present them in an easily digestible format, highlighting the most pressing risks that need immediate attention.
In summary, KRIs are an indispensable tool in the cybersecurity toolkit. They allow businesses to stay ahead of potential cyber threats, making cybersecurity a proactive, rather than reactive, endeavor. As a cybersecurity-focused managed services provider, Upper Echelon Technology Group LLC understands the vital role that KRIs play in safeguarding your business. We enable you to leverage KRIs effectively to measure, manage, and mitigate cyber risks, thereby making your company more secure and profitable.
The Role of Managed Services Providers in Cyber Security Risk Assessments
In today’s digital age, the role of managed services providers (MSPs) in cybersecurity risk assessments is paramount. As cyber threats evolve in complexity and severity, it’s crucial for businesses to partner with a trusted MSP to ensure the safety and integrity of their IT assets. Upper Echelon Technology Group LLC stands at the forefront of this revolution, offering a personalized approach to IT Managed Services that goes beyond “fixing tech issues” and focuses on leveraging technology to drive business growth.
How Upper Echelon Technology Group LLC Provides Personalized IT Managed Services
At Upper Echelon Technology Group LLC, we understand that each business is unique and so are its technology needs. Our personalized approach to IT Managed Services is designed to solve your technology issues, making your team more efficient and your company more profitable. We go beyond the standard IT services by identifying areas where technology can improve your bottom line. This approach allows us to ensure that your technology serves your business, rather than the other way around.
The Unique Selling Proposition of Upper Echelon Technology Group LLC
What sets Upper Echelon Technology Group LLC apart is our commitment to the core values that drive our company. We believe in prioritizing relationships, personal growth, open communication, and doing the right thing even when no one is watching. We work as a true team, striving to be a positive influence, and acting like owners because we own it. These values form the backbone of our personalized approach to IT Managed Services, making us a trusted partner for businesses looking to leverage technology for growth.
How Upper Echelon Technology Group LLC Helps in Conducting Cyber Security Risk Assessments
Conducting cybersecurity risk assessments is a critical part of our service offering. We follow a systematic approach that includes establishing the context for risk management, defining the scope of the risk assessment, understanding your assets, assessing threats and vulnerabilities, estimating likelihood, and assessing cybersecurity risk.
Our approach is in alignment with the NIST Cybersecurity Framework, providing a comprehensive and effective way to manage cyber risks. We help businesses identify, protect, detect, respond, and recover from cybersecurity risks, ensuring compliance with prevalent cybersecurity frameworks.
In a world where cybersecurity is no longer a luxury but a necessity, partnering with a trusted MSP like Upper Echelon Technology Group LLC can be your best bet to safeguard your business from potential cyber threats.
Conclusion: The Future of Cyber Security Risk Assessments
With the digital landscape evolving at an unprecedented pace, cybersecurity is no longer a matter of if, but when. As the final line of defense, cyber security risk assessments have become an integral part of an organization’s security strategy. They have transitioned from being a one-time activity to a continuous process that dynamically adapts to the ever-changing threat landscape.
The future of cyber security risk assessments lies in leveraging advanced technologies and methodologies to uncover hidden threats and vulnerabilities. As we move forward, we can expect to see more focus on proactive risk identification and management, with an emphasis on threat intelligence, machine learning, and automation.
Managed Services Providers (MSPs) like Upper Echelon Technology Group LLC are poised to play a crucial role in this future landscape. As an expert in conducting cyber security risk assessments, Upper Echelon Technology Group LLC provides personalized IT Managed Services that not only address your immediate tech issues but also strategically align with your business needs.
Their approach goes beyond the traditional, focusing on how technology can be leveraged to improve efficiency, drive business growth, and enhance profitability. By providing a comprehensive risk assessment, they ensure that you are equipped with the knowledge and tools to effectively mitigate and manage potential cyber threats.
In conclusion, the future of cybersecurity risk assessments lies in their ability to adapt, evolve, and innovate in response to the ever-changing digital landscape. As business owners, it is vital to choose a partner like Upper Echelon Technology Group LLC, who understands this dynamic landscape and can provide personalized, effective, and forward-thinking cybersecurity solutions.
In a world where the only constant is change, staying one step ahead in terms of cybersecurity could be the difference between business success and failure. So as we look to the future, let’s embrace cyber security risk assessments as an essential tool in our arsenal, guiding us towards a safer, more secure digital future.