Introduction
Brief on Cyber Security Evaluation
In today’s digital landscape, cyber security evaluation is the virtual armor that protects your business operations from the devastating impacts of cyber threats. This evaluation process involves proactively identifying and analyzing potential vulnerabilities in your system to fortify your defenses against cyber attacks. It’s not just about dealing with tech issues; it’s about securing your digital kingdom.
Importance of Cyber Security Evaluation
The significance of a thorough cyber security evaluation cannot be overstated. As cyber attacks continue to evolve in complexity and frequency, it’s paramount that businesses stay one step ahead. A robust cyber security evaluation provides a comprehensive picture of your network’s security posture, allowing you to identify, assess, and manage cyber threats effectively. It’s the difference between facing a catastrophic data breach and maintaining a secure, efficient, and profitable business operation.
Role of Upper Echelon Technology Group LLC in Cyber Security Evaluation
In this high-stakes scenario, Upper Echelon Technology Group LLC steps in, offering a personalized approach to IT Managed Services. We are a cybersecurity-focused managed services provider that goes beyond merely fixing tech issues. We partner with businesses to evaluate their cyber security, identify vulnerabilities, and implement robust solutions that optimize their technology assets.
Our approach is comprehensive. We identify potential cyber threats, assess the risk, analyze the impact, set security controls, and continually monitor and review their effectiveness. In essence, we empower businesses to leverage technology effectively, improving efficiency and driving profitability while maintaining a secure network. If you value a business partner who can fortify your defenses while helping you harness the power of technology, Upper Echelon Technology Group is ready to step in. Let us help you build a stronghold in this digital world.
Understanding Cyber Security Evaluation
In the face of evolving and increasingly sophisticated cyber threats, the need for comprehensive Cyber Security Evaluation has never been more crucial. This section will dive into the definition of this essential process, explore why it’s vital for businesses, and examine its role in protecting and enhancing your business operations.
Definition of Cyber Security Evaluation
A Cyber Security Evaluation is a systematic process that identifies, assesses, and prioritizes potential vulnerabilities in a company’s digital ecosystem. It involves cataloging information assets, assessing the risk, analyzing the risk, setting security controls, and continually monitoring and reviewing the effectiveness of these controls. This process is not a one-time event but a continuous cycle that helps businesses stay one step ahead of cyber threats.
The Need for Cyber Security Evaluation
In today’s digital age, no business is immune to cyber threats. From data breaches to ransomware attacks, these threats can severely disrupt operations, damage reputations, and lead to significant financial loss. Cyber Security Evaluation is a critical tool that businesses can use to identify potential vulnerabilities before they can be exploited. It allows businesses to proactively address these vulnerabilities, mitigating risks, and ensuring the integrity, confidentiality, and availability of their critical data and systems.
The Role of Cyber Security Evaluation in Business
The role of Cyber Security Evaluation in business is multifaceted. At a basic level, it provides a clear understanding of the company’s cybersecurity posture, highlighting areas of strength and pinpointing vulnerabilities that need attention.
From the perspective of the Upper Echelon Technology Group, Cyber Security Evaluation is not just about protecting a company’s digital assets. It also plays a crucial role in helping businesses leverage their technology assets effectively, increase efficiency, and drive profitability. By identifying and addressing cyber risks, businesses can focus on their core operations, knowing their digital landscape is secure.
Moreover, a thorough Cyber Security Evaluation aids in regulatory compliance, ensuring your business adheres to industry standards and regulations. This can bolster your business’s reputation, instill trust in your stakeholders, and even provide a competitive edge.
In the end, Cyber Security Evaluation is not just a defense strategy—it’s a business enabler. It’s about turning cybersecurity from a potential vulnerability into a business strength. And with experts like the Upper Echelon Technology Group by your side, you can navigate through the complex cybersecurity landscape with confidence.
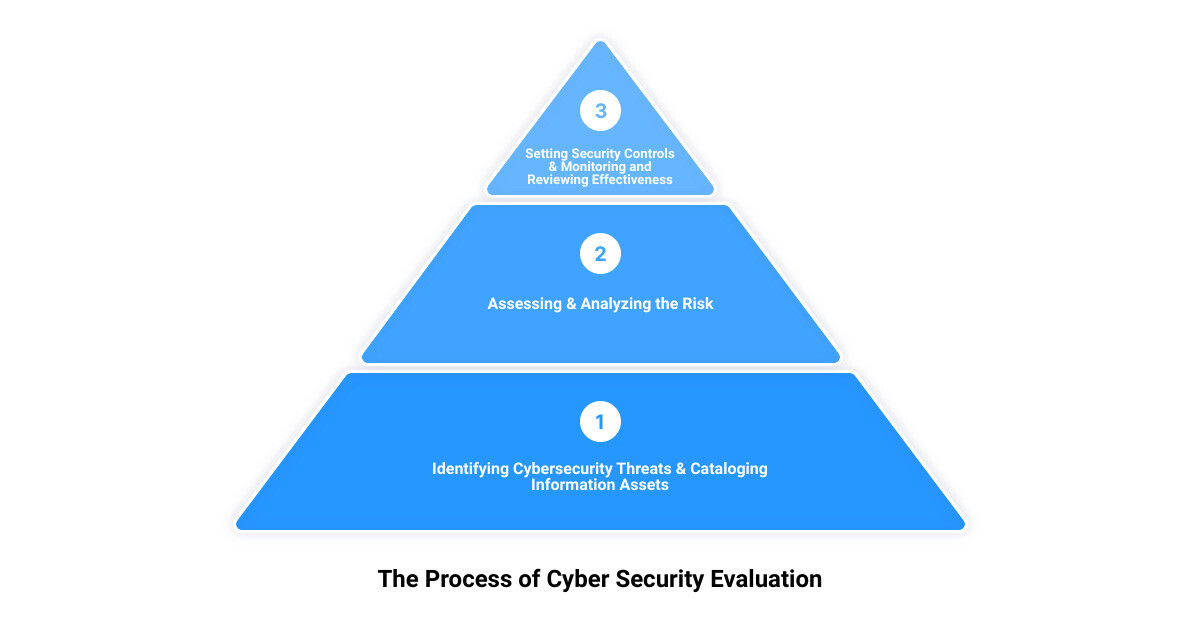
The Process of Cyber Security Evaluation
Just as a doctor would diagnose an illness by evaluating symptoms, a comprehensive cyber security evaluation involves a systematic examination of your organization’s information systems to identify potential threats and vulnerabilities. This evaluation is a crucial component of your organization’s risk management process, as it helps to maintain the overall health of your business’s digital infrastructure. The Upper Echelon Technology Group follows a meticulous procedure to ensure a holistic cyber security evaluation.
Identifying Cybersecurity Threats
The first step in the cyber security evaluation process is identifying cybersecurity threats. These threats can range from cybercriminals trying to steal sensitive data to malware that can disrupt your business operations. We leverage resources like the MITRE ATT&CK Knowledge Base and advisories from agencies like the Cybersecurity & Infrastructure Security Agency to stay updated with the latest cyber threat information, ensuring we’re always ready to tackle new threats.
Cataloging Information Assets
Once we’ve identified potential threats, we move on to cataloging information assets. This process involves creating an inventory of all your organization’s physical and digital assets. We make sure to highlight the ‘crown jewels’ – the most important assets that, if compromised, could cause significant harm to your business operations or reputation.
Assessing the Risk
The third step in the process is risk assessment. This involves determining the likelihood and potential impact if a cybersecurity threat were to exploit a vulnerability in your information systems. From our extensive experience in managing IT services, we understand that a one-size-fits-all approach doesn’t work when it comes to risk assessment. We customize our approach to fit your business’s unique needs and risk tolerance levels, ensuring a comprehensive and effective risk assessment.
Analyzing the Risk
Once we have a clear understanding of the risks, we move on to risk analysis. This involves quantifying the potential impact of each identified risk and prioritizing them based on their likelihood and potential impact. This step provides invaluable insights that allow us to develop a strategic plan for managing your cyber risks.
Setting Security Controls
After analyzing the risks, we establish security controls to manage and mitigate these risks. This could involve implementing new technologies, adjusting policies, or improving user training. The goal is to reduce the likelihood of a cybersecurity threat exploiting a vulnerability in your systems and lessen the impact in case a breach occurs.
Monitoring and Reviewing Effectiveness
Last but not least, we monitor and review the effectiveness of the security controls put in place. This is an ongoing process that involves regular audits and reviews to ensure that the controls are working as intended and adjusting them as necessary based on new threats or changes in your business.
At the Upper Echelon Technology Group, we understand that cyber security is not a one-time task but a continuous process. We’re committed to staying by your side every step of the way, helping your business stay resilient in the face of ever-evolving cyber threats.
Tools for Cyber Security Evaluation
In today’s digital world, a comprehensive cyber security evaluation is no longer a luxury but a necessity for businesses, big or small. The task is far from easy, but thanks to cutting-edge tools like the Cyber Security Evaluation Tool (CSET), the process is made more manageable and efficient.
Introduction to Cyber Security Evaluation Tool (CSET)
A pioneering tool in the realm of cyber security, the Cyber Security Evaluation Tool (CSET) is a free stand-alone desktop application that guides asset owners and operators through a systematic process of evaluating their operational and information technology. Designed with a user-friendly interface, it simplifies the complex task of identifying vulnerabilities and assessing risks.
How CSET Works
CSET operates by guiding users through a comprehensive step-by-step process to evaluate industrial control system (ICS) and information technology (IT) network security practices. It allows users to evaluate their own cyber security stance using many recognized government and industry standards and recommendations. With CSET, you can effortlessly conduct a detailed analysis of your network, identify potential vulnerabilities, and establish effective security controls.
Benefits of Using CSET
There are several advantages to using CSET for your cyber security evaluations. First, it provides a disciplined, systematic, and repeatable approach to evaluating your organization’s security posture. Second, CSET’s inclusion of the Cyber Performance Goals (CPG) Assessment helps businesses outline high-priority cybersecurity goals and associated actions to enable progress towards a consistent baseline across all critical infrastructure sectors. Finally, CSET offers a cost-effective solution. Being a free tool, it allows even small and medium-sized businesses to conduct thorough cyber security evaluations without straining their budget.
Other Cyber Security Evaluation Tools
While CSET is a powerful tool, it’s not the only one available for cyber security evaluations. There are other similar tools available, each with their own strengths and unique features. These include the Security Evaluator 5.0, which is known for its in-depth vulnerability scanning and risk assessment capabilities, and the Ford Foundation’s Cybersecurity Assessment Tool (CAT) which excels in helping non-profit organizations navigate the complex world of cyber security.
At Upper Echelon Technology Group, we understand that choosing the right tool for your cyber security evaluation can be daunting. Our experts are here to guide you through the process, ensuring that you pick the tool that best fits your business needs and objectives. We are committed to helping you leverage technology to protect your business, streamline your operations, and drive profitability.
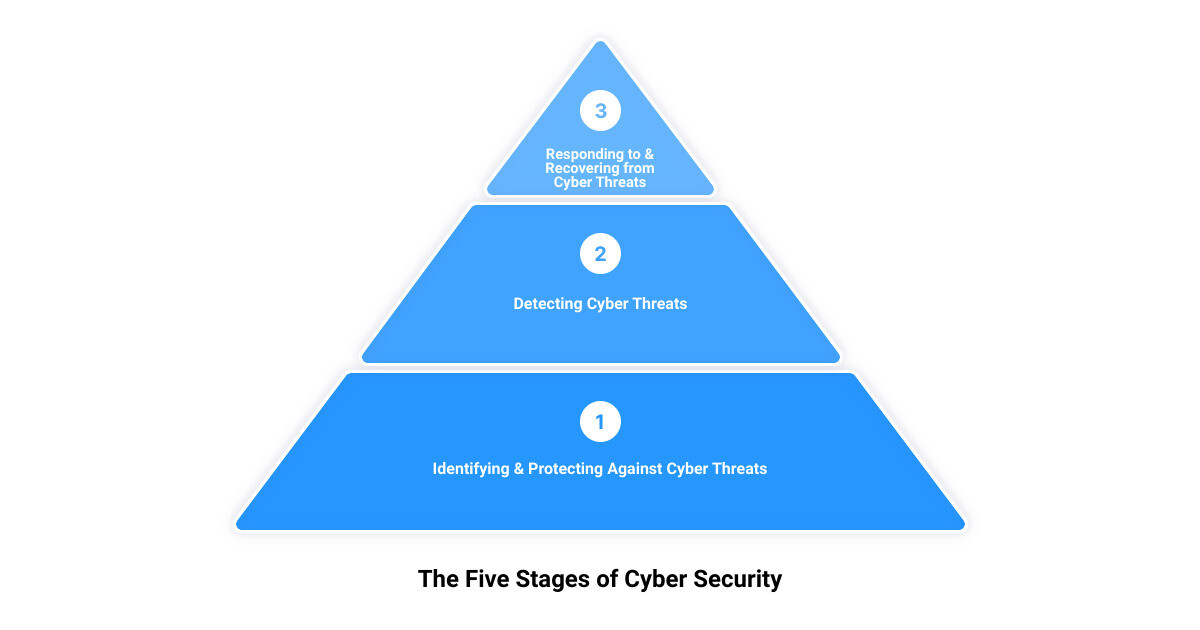
The Five Stages of Cyber Security
In the digital realm, strength lies in knowledge. Understanding the five stages of cybersecurity is paramount in ensuring your business is prepared for any potential threats. These stages include identifying cyber threats, protecting against them, detecting them, responding to them, and recovering from them.
Identifying Cyber Threats
The first step in achieving a robust cybersecurity posture is identifying potential cyber threats. This involves understanding where your vulnerabilities are and what types of threats could exploit them. Threats could come from various sources, such as malware, phishing, or denial-of-service attacks. Businesses need to keep their finger on the pulse of the rapidly evolving cyber threat landscape, a task that Upper Echelon Technology Group is well-equipped to handle.
Protecting Against Cyber Threats
After identifying potential threats, the next step is to protect your IT assets. This involves implementing security controls to mitigate the risks these threats pose. These controls could range from encryption and firewalls to authentication systems and access control measures. Upper Echelon Technology Group provides bespoke solutions to secure your business against cyber threats, ensuring that your technology serves your business, instead of it becoming a liability.
Detecting Cyber Threats
Even with the best protective measures in place, some cyber threats might slip through the cracks. This is where detection comes in. Continuous monitoring of your network and systems can help identify any unusual activity that could indicate a breach. Detection tools can provide real-time alerts, allowing your IT team to respond quickly and effectively.
Responding to Cyber Threats
When a cyber threat is detected, a swift and decisive response is crucial to minimize damage. This involves isolating affected systems, removing the threat, and investigating the breach. It’s essential to have a clear incident response plan in place, outlining roles, responsibilities, and procedures. Upper Echelon Technology Group can not only help you develop such a plan but also provide the necessary support during incident response.
Recovering from Cyber Threats
Finally, recovering from a cyber incident involves restoring systems and data, addressing vulnerabilities that were exploited, and implementing measures to prevent future incidents. It’s vital to learn from each incident and continually improve your cybersecurity practices.
The road to cybersecurity might seem complex, but with the right partner like Upper Echelon Technology Group, it becomes manageable. We guide you through each stage, using our expertise to identify, protect, detect, respond, and recover, ensuring your business remains resilient in the face of cyber threats.
Case Study: Ford Foundation’s Cybersecurity Assessment Tool (CAT)
Stepping into the spotlight, let’s examine a real-world example of effective cybersecurity evaluation. The Ford Foundation, a globally recognized social justice philanthropy organization, has crafted a tool known as the Cybersecurity Assessment Tool (CAT) to help organizations assess their cybersecurity efforts.
Overview of CAT
The Ford Foundation’s Cybersecurity Assessment Tool (CAT) is a meticulously designed questionnaire aimed at assessing the maturity, resiliency, and strength of an organization’s cybersecurity initiatives. Being conscious of the busy schedules of non-technical grant makers, grantee partners, and nonprofits, the tool is designed to be completed in one 30-minute sitting. However, it might require input from various members of your staff, including operations staff or decision makers.
Key Areas Covered by CAT
The CAT focuses on multiple key areas of cybersecurity within an organization. Its primary objective is to gauge the maturity level of an organization’s cybersecurity program and identify potential components that could be improved or added. The tool, however, does not provide a roadmap for securing the organization against cyber attacks or misuse of data or systems, and it isn’t a basis for determining legal compliance.
Benefits of Using CAT
One of the primary benefits of using the CAT is its accessibility and ease of use. It’s designed with non-technical individuals in mind, making it a valuable tool for organizations that may not have robust IT departments. Moreover, it provides an initial assessment to guide organizations on their cybersecurity journey. And in the spirit of open-source collaboration, the Ford Foundation has made a beta version available for public use, amplifying its reach and impact.
Limitations of CAT
While the CAT is a valuable tool for initial assessment, it’s important to note its limitations. It does not provide a detailed roadmap for cybersecurity. It also doesn’t definitively determine compliance with any legal obligations or provide a definitive list of the cybersecurity program components an organization should develop. It’s an assessment tool, not a comprehensive solution.
Navigating the realm of cybersecurity can be overwhelming, but with the right tools like the CAT and partnerships with experienced providers like Upper Echelon Technology Group, organizations can begin to fortify their digital defenses effectively.
Conclusion
Recap of Cyber Security Evaluation
In the digital age, the importance of conducting thorough and reliable cyber security evaluations cannot be overstated. From identifying potential threats and vulnerabilities to monitoring and reviewing the effectiveness of set security controls, these evaluations are crucial in fortifying your digital defenses.
A comprehensive cyber security evaluation involves several steps. This includes defining and identifying potential cybersecurity threats, cataloging information assets, assessing and analyzing the associated risks, setting appropriate security controls, and consistently monitoring and reviewing effectiveness. Utilizing cyber security evaluation tools such as the Cyber Security Evaluation Tool (CSET) can streamline this process, providing a systematic approach to evaluating operational and information technology.
The Role of Upper Echelon Technology Group LLC in Cyber Security Evaluation
As a cybersecurity-focused managed services provider, the Upper Echelon Technology Group plays an instrumental role in cyber security evaluations. With a personalized approach to IT Managed Services, we not only solve your technology issues but also help your team become more efficient and your company more profitable through leveraging technology.
Our team constantly evaluates the services and products we offer to our clients to ensure that your network is protected and optimized all year round. Our goal is to ensure your technology serves your business instead of you serving your technology. We understand the unique needs of small to medium-sized businesses in Wilmington, DE, and beyond, providing tailored cybersecurity solutions that meet these specific requirements.
Final Thoughts on Cyber Security Evaluation
In conclusion, cyber security evaluation is a critical process that can significantly enhance your organization’s resilience against cyber threats. It provides an in-depth understanding of your system’s vulnerabilities, enabling you to take proactive measures to mitigate potential risks.
The complexity of cybersecurity can indeed be overwhelming, but with the right tools and a partnership with an experienced provider like the Upper Echelon Technology Group, organizations can fortify their digital defenses effectively. Remember, in the realm of cybersecurity, prevention is always better than cure. The role of cyber security evaluations in safeguarding your digital assets, data, and overall business operations cannot be overemphasized.