In the ever-evolving landscape of digital technology, businesses of all sizes are finding themselves increasingly reliant on complex networks and systems to carry out their operations. While technological advancement offers a myriad of benefits, it also comes with its fair share of challenges. Among the most pressing of these challenges is the need to ensure that these systems are adequately protected from cybersecurity threats. Enter Cyber Security Assessment and Management (CSAM), a holistic approach that offers a robust solution to this challenge.
In this comprehensive guide, we aim to shed light on the ins and outs of Cyber Security Assessment and Management, helping you understand its importance and how you can leverage it to safeguard your digital realm. Whether you’re a small business owner in Wilmington, DE, looking for a cybersecurity-focused managed services provider, or an IT professional seeking to enhance your knowledge of cybersecurity, this guide is for you.
Cyber Security Assessment and Management, in essence, is an end-to-end assessment and authorization application that provides automated inventory, configuration, and vulnerability management. This process helps businesses identify cybersecurity vulnerabilities in their systems, analyze the severity of each risk, and develop an effective plan for risk mitigation.
But, how does this process work? What steps do businesses need to take to perform a cybersecurity risk assessment? What tools are available to facilitate this process? And how can a managed services provider like Upper Echelon Technology Group LLC help in optimizing this process?
These are some of the questions we’ll address as we delve deeper into the realm of Cyber Security Assessment and Management. So, sit tight as we embark on this enlightening journey to help you secure your digital assets in the best way possible.
Understanding Cyber Security Assessment and Management (CSAM)
What is CSAM?
Every digital journey begins with understanding. So, what exactly is Cyber Security Assessment and Management (CSAM)? CSAM is a comprehensive system designed to identify, assess, and prioritize IT infrastructure for protection. It’s an end-to-end Assessment and Authorization (A&A) application that automates inventory, configuration, and vulnerability management, providing valuable data for reports and dashboards.
In the complex world of digital business, CSAM serves as a reliable compass, guiding your organization towards a safe and secure IT environment. Whether it’s tracking inventory or managing vulnerabilities, the CSAM process ensures your digital infrastructure is always up-to-date and resilient against potential cyber threats.
The Importance of CSAM in Today’s Digital Landscape
In today’s hyper-connected world, the digital landscape is fraught with potential pitfalls. From malicious malware to sophisticated phishing scams, cyber threats lurk around every corner. That’s where CSAM comes in. It’s your first line of defense against these digital dangers, ensuring your business’s valuable data and IT infrastructure remain secure.
CSAM is not just a want but a need in the current digital age where cyber threats are evolving daily. It’s an essential tool that helps organizations identify areas of weakness, assess the potential impact of threats, and implement the necessary security measures.
How CSAM Contributes to an Organization’s Security Posture
An organization’s security posture is only as strong as its weakest link. CSAM fortifies these weak links by providing a comprehensive view of an organization’s IT infrastructure and potential vulnerabilities. It’s like having a bird’s eye view of your entire IT landscape, enabling you to spot weak points before they can be exploited.
By leveraging CSAM, businesses can implement proactive measures to improve their security posture. This includes regular risk assessments, vulnerability management, and setting up the necessary security controls. All these contribute to a robust security posture that not only protects your business from threats but also helps build trust with clients, stakeholders, and employees.
In essence, CSAM is the foundation of a secure digital realm. It provides the necessary structure for assessing and managing cyber risk, ensuring your organization can operate safely in today’s perilous digital landscape.
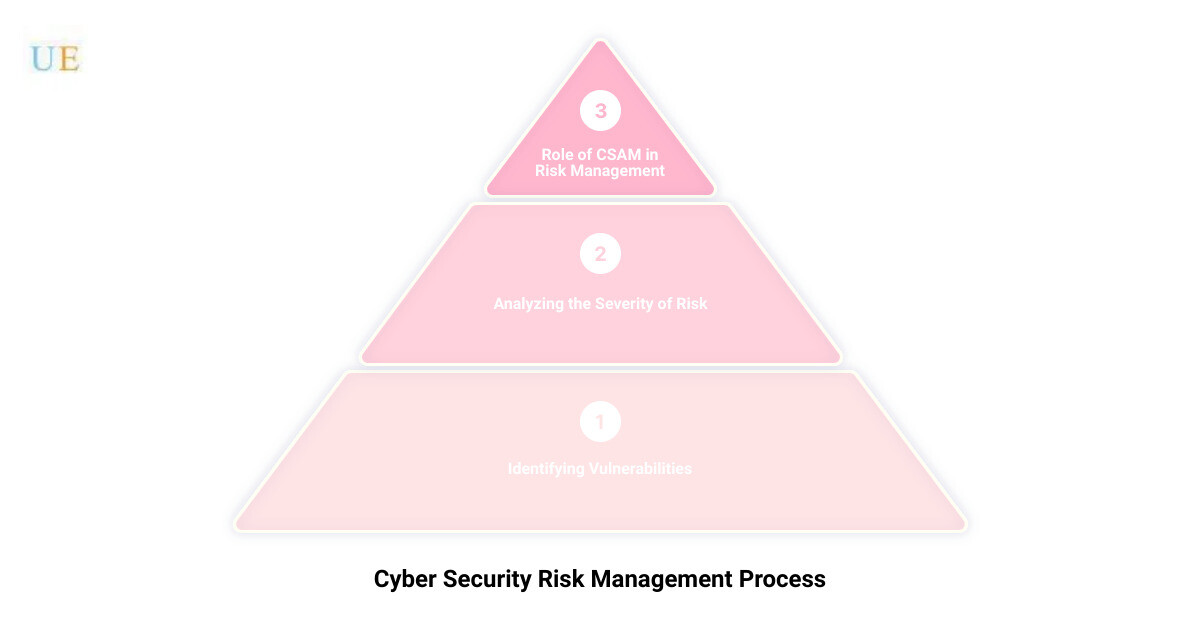
The Cyber Security Risk Management Process
Having delved into the concept of Cyber Security Assessment and Management (CSAM), let’s now unravel the heart of this strategy – the cyber security risk management process. This process, often likened to the backbone of CSAM, provides a structured approach to understanding, managing, and mitigating cyber risks.
Identifying Cyber Security Vulnerabilities
Your digital realm is an intricate network of systems, applications, and data. Each component, while essential for your business operations, could potentially be a gateway for cyber threats if not properly secured. The first step in the cyber security risk management process is to identify these vulnerabilities within your system.
This involves a thorough examination of your IT infrastructure, including your hardware, software, networks, and data. The goal is to uncover any weaknesses that could be exploited by cyber threats. With the help of a cybersecurity-focused managed services provider like Upper Echelon Technology Group, this step can be done effectively and efficiently.
Analyzing the Severity of Each Risk
Once the vulnerabilities have been identified, the next step is to analyze the severity of each risk. This means assessing how likely it is that a vulnerability could be exploited, and what the potential impact would be if it were.
Understanding the severity of each risk involves asking critical questions: What is the potential impact of each identified threat? What is the likelihood of exploitation? The answers to these questions help in determining which risks need immediate attention and which ones can be dealt with later.
The Role of CSAM in Risk Management
CSAM plays a pivotal role in the cyber security risk management process. It provides a framework for identifying vulnerabilities, assessing risks, and implementing security controls. Moreover, CSAM enables continuous monitoring and review of the effectiveness of these controls, ensuring your digital realm remains secure over time.
In essence, CSAM is an essential tool for managing cyber risks. It enables businesses to be proactive in their approach to cyber security, rather than reactive. By identifying vulnerabilities before they can be exploited, and by continuously monitoring and managing risks, CSAM helps safeguard your digital realm against the ever-evolving landscape of cyber threats.
With a personalized approach to IT Managed Services, Upper Echelon Technology Group can help your business effectively navigate the cyber security risk management process. Leveraging your technology assets, we can help you identify vulnerabilities, assess and manage risks, and enhance your overall security posture. In doing so, we help solve your technology issues, make your team more efficient, and ultimately, improve your company’s bottom line.
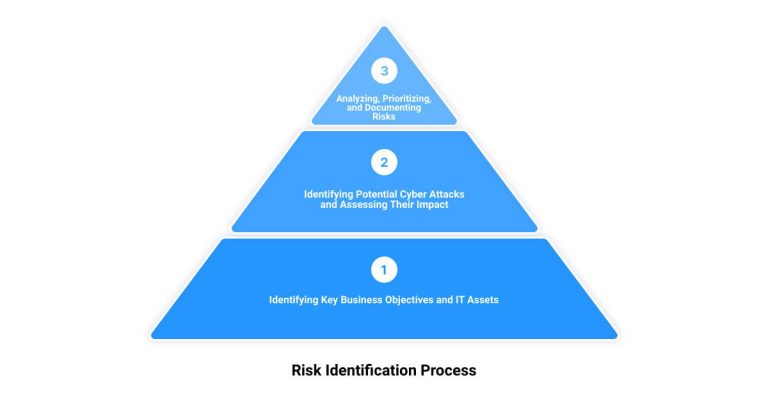
The 5 Steps to a Cyber Security Risk Assessment
Unleashing the power of technology in your business goes hand-in-hand with understanding and mitigating the inherent risks. Cybersecurity risk assessments provide a clear roadmap for this journey. Here is a step-by-step guide to conducting a thorough risk assessment.
Step 1: Catalog Information Assets
Every effective risk assessment begins with a comprehensive understanding of what you’re protecting. To do this, develop an inventory of all physical and logical assets within the scope of the assessment. This includes not only your most critical assets, but also those that an attacker might target to gain broader access to your systems, such as an Active Directory server. A detailed network architecture diagram can help visualize the interconnectivity between assets and processes and identify entry points into the network.
Step 2: Assess the Risk
The next step is to identify potential threats to each asset. Utilize resources like the MITRE ATT&CK Knowledge Base and the Cyber Threat Alliance to gain insights into the latest cyber threat trends. Also, consider where each asset sits in the Lockheed Martin cyber kill chain, which maps out the stages and objectives of a typical real-world attack.
Step 3: Analyze the Risk
After identifying potential threats, it’s time to analyze the risk. This involves determining the likelihood of these threats occurring and the potential impact they could have on your business. This analysis will help you build a complete picture of your threat environment, enabling informed decisions about implementing security controls.
Step 4: Set Security Controls
With a clear understanding of your assets and the risks they face, you can now implement appropriate security controls. These should be designed to reduce the overall risk to a level your organization is comfortable with. It’s important to remember that no solution offers 100% security, but a well-planned strategy can significantly mitigate potential threats.
Step 5: Monitor and Review Effectiveness
This final step is an ongoing process. Cyber threats evolve constantly, and so should your strategies for dealing with them. Regularly monitor and review the effectiveness of your security controls. This will help you identify areas for improvement and ensure your defenses remain robust against emerging threats.
At Upper Echelon Technology Group, we are here to guide you through every step of this cybersecurity risk assessment. Our personalized approach ensures that we understand your unique business needs, providing you with a tailor-made risk management strategy.
Tools for Cyber Security Assessment and Management
As we journey deeper into the digital age, the realm of cybersecurity grows increasingly complex. To navigate this landscape, businesses need to leverage the right tools for cybersecurity assessment and management. Just as a ship needs its compass, your business requires robust, reliable tools to navigate the cyber seas.
Overview of the Cyber Security Assessment and Management Application
A Cyber Security Assessment and Management (CSAM) application is a comprehensive tool that provides end-to-end Assessment and Authorization (A&A). This application automates various processes such as inventory, configuration, and vulnerability management, enabling a seamless analysis of your system’s security.
The CSAM application collects and organizes standard data, making it accessible for use in reports and dashboards. This feature allows you to have a bird’s eye view of your network’s security status, empowering you to make informed decisions based on real-time insights.
Features and Benefits of the Cyber Security Assessment and Management Application
The CSAM application comes packed with numerous features designed to fortify your cybersecurity infrastructure. It automates the identification of vulnerabilities in your system and the threats that might exploit them. It also enables you to analyze the severity of each risk by assessing its likelihood of occurrence and potential impact.
The application’s automated inventory management feature keeps track of all your IT assets, making it easier to monitor their security status. Meanwhile, its vulnerability management feature regularly scans your network for potential weaknesses that could be exploited by cyber threats.
One of the most valuable benefits of the CSAM application is its continuous monitoring capability. This feature allows you to keep an eye on the effectiveness of your security controls, ensuring that they remain robust against evolving cyber threats.
How to Access and Use the Cyber Security Assessment and Management Application
Accessing and using a CSAM application is a straightforward process. Typically, it’s a cloud-based tool that you can access via a secure login. Once logged in, you can start leveraging its features to assess and manage your cybersecurity.
The application’s user-friendly interface allows you to easily navigate through its various features. It provides clear instructions for every process, making it simple to use even for those without extensive technical knowledge.
At Upper Echelon Technology Group, we ensure you have full access to a CSAM application as part of our cybersecurity-focused managed services. We provide the necessary training and support to ensure you can leverage the tool effectively, helping safeguard your digital realm against cyber threats.
In the next section, we will delve into how you can implement Cyber Security Assessment and Management in your organization, and how Upper Echelon Technology Group LLC can assist you in this process.
Implementing Cyber Security Assessment and Management in Your Organization
In the ever-evolving digital landscape, implementing Cyber Security Assessment and Management (CSAM) in your organization is not just an option—it’s a necessity. But how exactly can you go about this process, and who can assist you along the way?
The Role of Managed Services Providers in CSAM
Managed Services Providers (MSPs) play a pivotal role in CSAM. These providers act as a virtual IT department for your business, taking care of tech issues, boosting efficiency through technology, and identifying areas where technology can enhance your profitability. They offer a range of services, including automated inventory, configuration, and vulnerability management, which form the backbone of CSAM.
Moreover, MSPs like Upper Echelon Technology Group LLC offer a personalized approach to IT Managed Services, ensuring your technology serves your business needs rather than the other way around.
How Upper Echelon Technology Group LLC Can Help with CSAM
Upper Echelon Technology Group LLC, a cybersecurity-focused MSP, goes beyond just fixing tech issues. With a dedicated team evaluating services and products offered to clients, they ensure your network is protected and optimized 24x7x365. This constant vigilance is crucial in the realm of CSAM, where threats can emerge at any moment.
The Upper Echelon Technology Group LLC team offers a CSAM process that identifies your cybersecurity vulnerabilities and threats, analyzes the severity of each risk, and sets security controls. They also monitor and review the effectiveness of these controls, making necessary adjustments to keep up with changing cyber threat landscapes.
Case Study: Successful CSAM Implementation with Upper Echelon Technology Group LLC
Let’s look at a real-life example of how Upper Echelon Technology Group LLC has successfully implemented CSAM. One small to medium-sized business in Wilmington, DE, was grappling with network security and technology optimization. They turned to Upper Echelon Technology Group LLC for a personalized approach to IT Managed Services.
The result? Through a comprehensive CSAM process, the business was able to identify and mitigate cyber risks, boost their team’s efficiency, and leverage technology to drive growth. Ultimately, they could focus on their core business needs, knowing that their digital realm was safeguarded by a robust CSAM system.
In conclusion, implementing CSAM in your organization is a vital step in safeguarding your digital assets. With the help of a managed services provider like Upper Echelon Technology Group LLC, you can navigate the complexities of CSAM, ensuring your business thrives in the digital age.
Conclusion: Safeguarding Your Digital Realm with CSAM
In the modern business landscape, the realm of digital assets is as valuable as any physical property. Cyber Security Assessment and Management (CSAM) is the knight in shining armor, protecting your kingdom from the onslaught of cyber threats. With the right approach to CSAM, organizations can guard their digital frontiers and ensure that their operations run smoothly, securely, and efficiently.
The Long-Term Benefits of Effective CSAM
There’s a wealth of benefits that come with a well-executed CSAM strategy.
Firstly, it provides a robust defense against potential cyber-attacks, protecting your valuable data from falling into the wrong hands. A successful CSAM implementation also enhances your overall security posture, enabling you to confidently navigate the digital landscape without fear of compromise.
Moreover, it increases operational efficiency by identifying and addressing vulnerabilities, thus preventing costly and time-consuming breaches. In the long run, a proactive approach to CSAM can boost your organization’s profitability by mitigating potential losses from cyber threats.
Finally, and importantly, effective CSAM promotes trust among your stakeholders. Customers, partners, and employees can rest assured knowing that their data is secure, thereby strengthening your business relationships and enhancing your brand reputation.
Next Steps for Implementing CSAM in Your Organization
So, what’s next on your journey to mastering CSAM?
If you’re a small to medium-sized business owner in Wilmington, DE, or anywhere else for that matter, your first port of call should be to partner with a reputable managed services provider like Upper Echelon Technology Group LLC. With a personalized approach to IT Managed Services, Upper Echelon’s team can help you navigate the ins and outs of CSAM, solving your technology issues and leveraging technology to drive your business growth.
Whether you’re starting from scratch or looking to enhance your current cybersecurity measures, Upper Echelon Technology Group LLC can provide the expertise and resources necessary for a successful CSAM implementation.
In conclusion, in the digital realm where cyber threats loom large, a solid CSAM strategy is your best line of defense. By investing time and resources in CSAM, you’re not only protecting your business today but also securing its future. So, gear up, partner with the right managed IT services provider, and get ready to master the art of Cyber Security Assessment and Management.