In the digital age, the importance of cyber security cannot be overstated. But how do you know if your business is truly secure? The answer lies in conducting a comprehensive cyber security assessment. Welcome to ‘The Untold Secrets of Cyber Security Assessment: Unveiling Hidden Vulnerabilities’. This article is your guide to understanding, preparing for, and leveraging the power of cyber security assessments to protect your business.
Cyber security assessments are essential not only for tech-based companies but for businesses of all sizes and industries. They are your first line of defense against cyber threats that can disrupt your operations, cause financial losses, and damage your reputation. Through a cyber security assessment, you can identify vulnerabilities in your systems before they become a target for hackers.
Moreover, regular cyber security assessments are crucial to keeping your risk profiles up-to-date. After all, the cyber landscape is constantly evolving, and new threats arise every day. Therefore, it’s not enough to conduct a one-time assessment. You need to stay vigilant and consistently evaluate your cyber security measures.
In the following sections, we will delve deeper into the world of cyber security assessments, learn about different types, and understand the role of managed services providers like Upper Echelon Technology Group in this critical process. By the end, you will have a clear roadmap on how to prepare for a cyber security assessment and implement effective strategies to mitigate risks and enhance your business’s cyber security posture. Stay with us as we unveil the hidden vulnerabilities in your systems and fortify your defenses against cyber threats.
Understanding Cyber Security Assessment: Definition and Purpose
In a digital world where cyber threats are lurking around every corner, understanding cyber security assessment is the key to unlocking your business’s potential. A cyber security assessment, at its core, is a systematic process that scrutinizes the various layers of your organization’s information system. It involves identifying, analyzing, and evaluating risk to ensure that the cyber security controls you choose are appropriate to the risks your organization faces. But, you may ask, why is this process so crucial to your business?
The Purpose of a Cyber Security Assessment
Imagine navigating through a dense forest without a map; you’re likely to lose your way and potentially face dangers. In the business landscape, cyber threats are the dangers, and the cyber security assessment is your map. It offers you a comprehensive understanding of your organization’s existing cyber security posture, thereby enabling you to identify potential vulnerabilities and areas of improvement.
The purpose of a cyber security assessment is multifold:
-
Risk Identification: It helps in identifying the risks associated with your organization’s information system. This includes understanding the various threat sources and potential events that could compromise your system’s security.
-
Thorough Analysis: It provides a detailed analysis of the potential consequences should a breach occur. This could range from financial losses to reputational damage.
-
Control Selection: Based on the identified risks and their potential impact, it guides the selection of appropriate cyber security controls for your organization.
-
Resource Optimization: Without a cyber security assessment, you could end up wasting valuable time, effort, and resources on ineffective strategies. This process ensures resource optimization by aligning your cyber security strategies with the actual risks faced by your organization.
-
Compliance Assurance: Many industries have regulations that require businesses to conduct regular cyber security assessments. Thus, it helps in ensuring compliance.
By understanding the purpose of a cyber security assessment, you can leverage it to fortify your defenses, mitigate risks, and ensure that your business can withstand the onslaught of cyber threats. In the next section, we will delve deeper into the step-by-step guide of conducting a cyber security assessment.
The Process of Cyber Security Assessment: A Step-by-Step Guide
Embarking on a cyber security assessment might seem like a daunting task. Yet, breaking it down into manageable steps can make it a more comprehensible process. This step-by-step guide provides a straightforward roadmap to perform a cyber security assessment, which can help businesses uncover hidden vulnerabilities and fortify their defenses effectively.
Step 1: Audit of Assets
The first step in any cyber security assessment is an audit of your digital assets. This entails identifying all the hardware, software, data, and information systems in your organization. It includes servers, workstations, mobile devices, applications, and data repositories. Having a comprehensive understanding of what constitutes your digital landscape is foundational to identifying where potential vulnerabilities may lie.
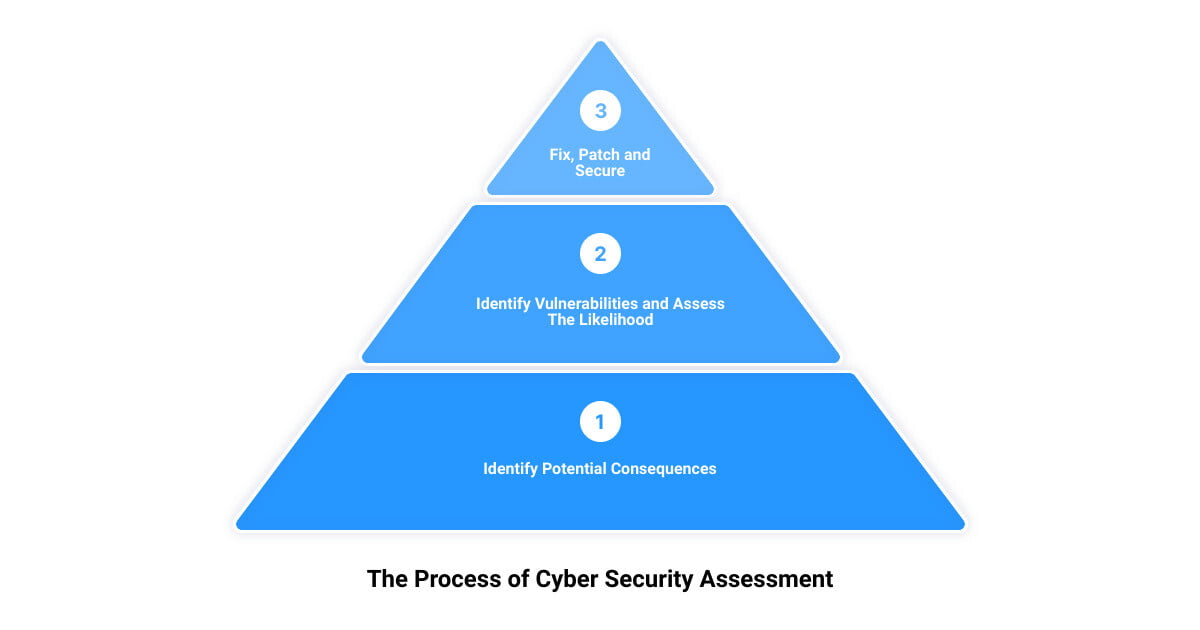
Step 2: Identify Potential Consequences
Once you have a clear understanding of your assets, the next step is to identify the potential consequences of a cyber attack. This involves evaluating the impact of a breach on each asset and the potential damage to your organization. This could range from financial loss, reputational damage, operational disruption, to regulatory penalties.
Step 3: Identify Threat Sources and Threat Events
The third step involves identifying threat sources and threat events. Threat sources could be external, such as hackers, or internal, like disgruntled employees. Threat events refer to the ways these sources could potentially exploit your system’s vulnerabilities. It is crucial to note that threats can vary greatly depending on your organization’s size, industry, and geographical location.
Step 4: Identify Vulnerabilities and Assess The Likelihood
The fourth step is to identify vulnerabilities and assess their likelihood. Vulnerabilities are weaknesses in your systems that could be exploited by threat sources. This step involves a thorough examination of your digital assets for any known vulnerabilities, outdated software, lax security policies, or inadequate security controls. The likelihood of each vulnerability being exploited is also assessed.
Step 5: Assess Risk and Probability Impact
In the fifth step, you assess the risk and probability impact. This is determined by the potential consequences of an attack and the likelihood of the vulnerability being exploited. High-risk vulnerabilities are those that could cause significant damage and have a high likelihood of being exploited. These should be prioritized for remediation.
Step 6: Fix, Patch and Secure
The final step in the cyber security assessment is to fix, patch, and secure. This involves addressing the identified vulnerabilities to reduce the risk of exploitation. It could involve patching software, updating security policies, or implementing new security controls. Once this step is completed, it’s important to reassess your cyber security posture regularly, as new vulnerabilities and threats can emerge over time.
In conclusion, conducting a cyber security assessment is a crucial process in protecting your business from the ever-growing cyber threats. By following these steps, you can identify your vulnerabilities, assess the risks, and take necessary actions to secure your digital assets. Remember, in today’s digital age, a robust cyber security posture is not a luxury, but a necessity.
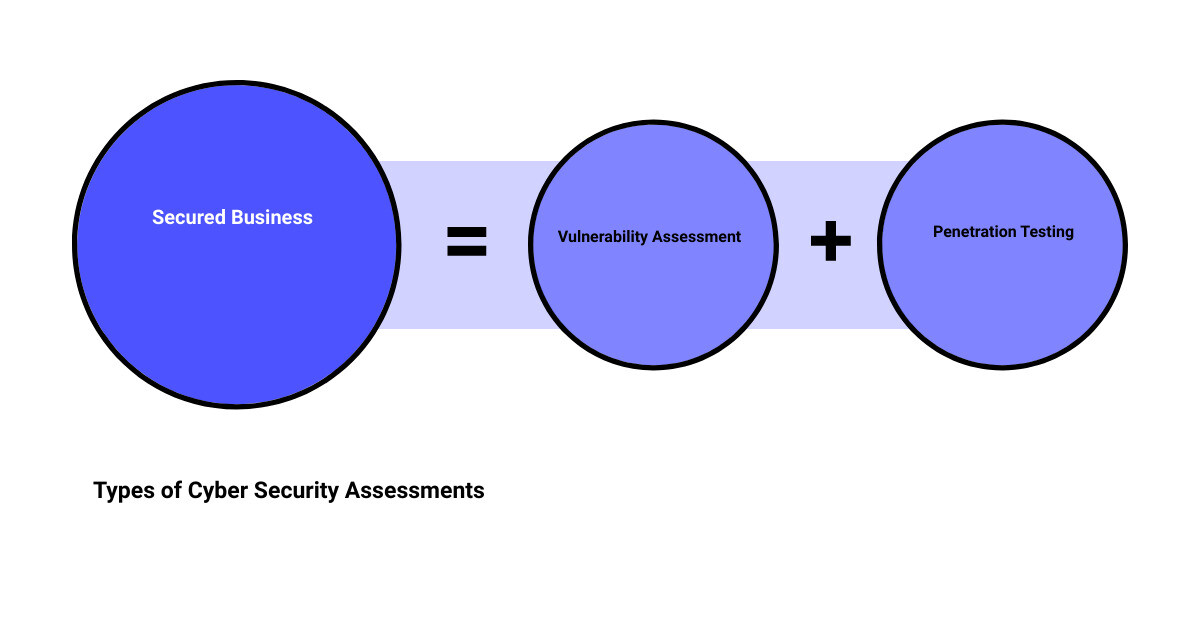
Types of Cyber Security Assessments: Choosing the Right One for Your Business
Just like a doctor prescribes different tests to diagnose various health issues, there are multiple types of cyber security assessments available to identify and treat distinct vulnerabilities in your business’s digital health. Let’s delve into these assessments, and help you make an informed choice for your business.
Vulnerability Assessment
A Vulnerability Assessment is essentially a health check for your digital assets, aiming to identify potential bugs or flaws in your software, network, or other assets. It is one of the most commonly performed security tests in the cyber security industry. This assessment is vital to track open paths and vulnerabilities in your systems, allowing for the timely release of patches or updates.
Penetration Testing
Penetration Testing is the equivalent of a stress test for your cyber security defenses. This in-depth method involves exploiting identified vulnerabilities to assess how an attacker could breach your systems. It can be performed from various perspectives, including a malicious hacker (Black-box), a potential insider threat (White-box), or a hybrid approach (Grey-box).
Compromise Assessment
A Compromise Assessment is akin to a forensic investigation, probing whether your organization has already suffered a breach. It involves a thorough examination of your systems and data to identify signs of past or ongoing unauthorized access.
Social Engineering Assessment
The Social Engineering Assessment is a psychological evaluation of your employees’ preparedness against social engineering attacks, where attackers manipulate individuals into revealing confidential information.
Red Team Assessment
A Red Team Assessment is a full-scale simulated attack on your organization’s systems, designed to test your overall security posture and incident response capabilities.
Cloud Security Assessment
As more businesses migrate to the cloud, a Cloud Security Assessment is crucial to ensure that your cloud-based assets are secure and compliant with relevant regulations.
Third-Party Risk Assessment
Third-Party Risk Assessment evaluates the cyber security risks posed by your business partners, suppliers, or other third parties with access to your systems or data.
Risk Assessment
Risk Assessment is a comprehensive evaluation of your organization’s overall cyber risk landscape, including potential threats, vulnerabilities, and their potential impact.
Security Audit
A Security Audit is a systematic evaluation of your organization’s adherence to a set of established cyber security standards or regulations.
Bug Bounty
Bug Bounty programs involve inviting external cyber security researchers to find and report vulnerabilities in your systems, often in exchange for a reward.
CIS Control Assessment
CIS Control Assessment measures your organization’s alignment with the Center for Internet Security’s 20 critical security controls.
Application Security Program Assessment
Application Security Program Assessment evaluates the security of your applications, including design, development, deployment, and maintenance processes.
Ransomware Simulation Assessment
A Ransomware Simulation Assessment tests your systems’ resilience against ransomware attacks and your ability to recover from such an incident.
Incident Response Readiness Assessment
Incident Response Readiness Assessment evaluates your organization’s preparedness to respond to a cyber security incident effectively and efficiently.
Tabletop Exercises
Tabletop Exercises are simulated cyber attack scenarios that test your incident response team’s skills and your organization’s incident response plan.
Choosing the right cyber security assessment for your business can seem like a daunting task. But remember, the goal is not to eliminate all risk – that’s impossible. Instead, you should aim to understand and manage your risk effectively. Whether it’s a vulnerability assessment or a full-scale red team assessment, the right choice depends on your business’s specific needs, requirements, and risk tolerance.
The Role of Managed Services Providers in Cyber Security Assessment: A Case Study of Upper Echelon Technology Group LLC
A common misconception among many small to medium-sized business owners is that cyber security assessments are a DIY project. But the truth is, conducting a thorough cyber security assessment requires professional expertise, time, and dedication. This is where managed services providers like Upper Echelon Technology Group LLC step in.
Upper Echelon Technology Group: A Cybersecurity Focused Managed Services Provider
Upper Echelon Technology Group LLC is a cybersecurity-focused managed services provider that prides itself on its personalized approach. They don’t just focus on fixing tech issues, they go beyond that by aligning their services with your business needs. They understand the value of technology as a business asset and help you leverage it in the best way possible.
Their offerings include solving your technology issues so you can focus on your business, making your team more efficient by leveraging technology, and making your company more profitable by identifying areas where technology can improve your bottom line. They are committed to providing a company culture that allows their employees and clients to reach their fullest potential while invoking their core values.
A Personalized Approach to Cyber Security Assessment
By understanding that every business has unique needs, Upper Echelon Technology Group tailors their cyber security assessment process to suit each client. They understand that a one-size-fits-all approach is not the solution when it comes to cybersecurity. Instead, they offer a customized cybersecurity solution that extends beyond mere tech issues.
Their team of professionals constantly evaluates the services and products that they offer to their clients to ensure that your network is protected and optimized 24x7x365. This ensures that your technology serves your business instead of you serving your technology.
Transparency and Trust in Cyber Security Assessment
Trust and transparency are critical when it comes to cybersecurity. Upper Echelon Technology Group makes this a priority by providing an inside look at the data that drives their technology. They believe that trust begins with transparency and strive to provide you with a clear understanding of their processes and the data that informs their decisions.
In a world where cyber threats are increasingly sophisticated and relentless, having a trusted partner like Upper Echelon Technology Group LLC to handle your cyber security assessments can be the difference between maintaining the integrity of your business or suffering a damaging breach. With their comprehensive and personalized approach, they ensure that your company’s cybersecurity needs are fully covered, allowing you to focus on what you do best – running your business.
How to Prepare for a Cyber Security Assessment: A Comprehensive Guide
Navigating the maze of cyber threats can be a daunting task, especially if you are a business owner focused on your core operations. But, preparation is the key to success when it comes to cyber security assessment. A well-structured and thorough preparation process can unveil hidden vulnerabilities, helping you fortify your defenses before a cyber attack happens. Here’s a step-by-step guide to prepare for a cyber security assessment:
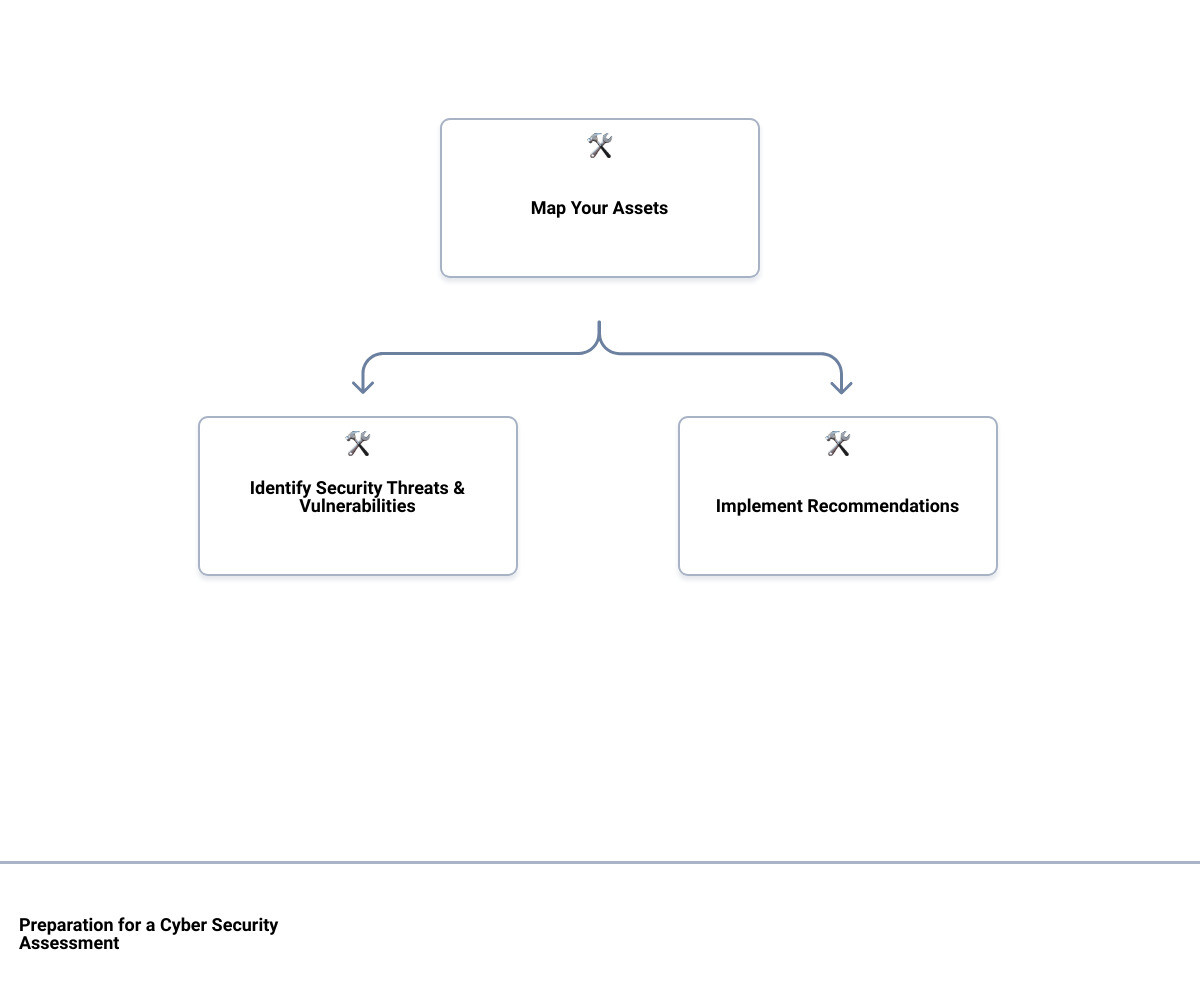
Map Your Assets
The first step to a successful cyber security assessment is mapping your assets. This involves identifying all the digital resources that your business relies on. It could be anything from your website and email servers to your customer database and cloud storage. The aim here is to understand what needs to be protected and where potential vulnerabilities may exist.
Identify Security Threats & Vulnerabilities
Next, you need to identify possible security threats and vulnerabilities. This could include outdated software, weak passwords, unsecured wireless networks, or even potential threats from rogue employees. The threats could also come from third-party vendors or partners who have access to your systems.
Determine & Prioritize Risks
With the potential threats and vulnerabilities identified, the next step is to determine and prioritize the risks. Not all threats pose the same level of risk. You need to assess each one based on the potential impact on your business and the likelihood of it occurring. This will help you allocate resources effectively towards addressing the most critical risks.
Analyze & Develop Security Controls
Once you’ve identified and prioritized risks, it’s time to analyze and develop security controls. This involves determining what measures can be put in place to prevent, detect, and respond to the identified risks. It could be anything from implementing strong password policies and regular software updates to installing firewalls and antivirus software.
Document Results From Risk Assessment Report
After the risk analysis, you should document the results in a risk assessment report. This report should detail the identified threats, the potential impact, the likelihood of occurrence, and the recommended preventive measures. This document will serve as a roadmap for improving your cybersecurity posture.
Create A Remediation Plan To Reduce Risks
Based on the risk assessment report, you should create a remediation plan. This plan should outline the steps needed to address each identified risk. It could involve patching software vulnerabilities, educating employees about cyber threats, or enhancing your network security.
Implement Recommendations
After creating the remediation plan, the next step is to implement the recommendations. It’s crucial to take immediate action to address the identified risks. Delaying could expose your business to potential cyber attacks.
Evaluate Effectiveness & Repeat
Finally, you should evaluate the effectiveness of the implemented measures and repeat the assessment process. Cyber threats are constantly evolving, so it’s important to regularly reassess your cybersecurity posture and make necessary adjustments.
Taking the time to prepare for a cyber security assessment will allow you to uncover hidden vulnerabilities, strengthen your defenses, and ensure the continuity of your business operations. Remember, in the digital world, it’s not a question of if a cyber attack will happen, but when. So, stay prepared with a robust cybersecurity plan.
Conclusion: The Continuous Need for Cyber Security Assessment
In the ever-evolving landscape of cyber threats, staying one step ahead is not a luxury, but a necessity. Cybersecurity is not a one-time solution but a continuous process of assessing, improving, and reassessing. This process is vital for businesses of all sizes and industries, as cyber threats can lead to significant financial loss, damage to brand reputation, and potential regulatory penalties.
A comprehensive cybersecurity risk assessment, therefore, forms an integral part of any robust cybersecurity strategy. It helps in identifying vulnerabilities, assessing potential risks, and implementing necessary measures to mitigate these risks. This continuous process allows organizations to keep their cybersecurity posture updated and in line with the latest threats and vulnerabilities.
Furthermore, adhering to various regulations such as GDPR, HIPAA, PCI-DSS, CMMC, and FERPA is not just about compliance, but it’s also about protecting your customer’s data and your organization’s reputation. Using a widely recognized framework like the NIST Cybersecurity Framework or the ISO 27000 standards can provide a systematic and structured approach to managing these risks.
However, conducting a cybersecurity assessment can be a daunting task, especially for small to medium-sized businesses without a dedicated in-house IT team. This is where a cybersecurity-focused managed services provider like Upper Echelon Technology Group LLC can provide invaluable expertise. They offer a personalized approach to IT Managed Services, ensuring a secure and optimized network environment for your business.
In conclusion, the need for cybersecurity assessments is ongoing and not a one-time event. It’s a critical part of your business strategy that should be periodically reviewed and updated. As technology continues to evolve, so too does the potential for cyber threats. With a proactive approach to cybersecurity, you can ensure that your business is always prepared to face these challenges head-on.
Remember, cybersecurity is not just about safeguarding your business today, but it’s about ensuring its longevity and success for tomorrow. Stay vigilant, stay secure, and keep assessing.