Introduction: The Importance of Cyber Risk Management
In today’s digital world, cyber threats don’t discriminate. They affect businesses of all sizes, sectors, and locations. No matter whether you’re a local business owner in Wilmington, DE or running a multinational corporation, cyber risk management should be at the top of your priority list. Cyber risk management is no longer optional; it’s a vital necessity for the survival and success of your business in the present-day cyber landscape.
Imagine this: You’ve built your business with hard work, dedication, and strategic decision-making, only to see it crumble due to a single cyber-attack. Suddenly, you’re dealing with lost revenue, a tarnished reputation, and potentially hefty regulatory fines. That’s the harsh reality for many businesses that overlook the importance of a robust cybersecurity risk management process.
The importance of cyber risk management goes beyond just safeguarding your business from cyber threats. It plays a pivotal role in ensuring that your technology serves your business rather than becoming a liability. It helps your business operate smoothly, making your team more efficient and your company more profitable. It’s about leveraging technology optimally to drive business growth.
At Upper Echelon Technology Group LLC, we understand the importance of personalized IT Managed Services that go beyond “fixing tech issues”. We focus on your unique business needs and goals, helping you navigate the complex maze of cyber risks while enabling you to leverage your technology assets in the best possible way. In the following sections, we’ll delve deeper into understanding cyber risk management and how mastering this art can propel your business to new heights.
Understanding Cyber Risk Management: A Strategic Approach
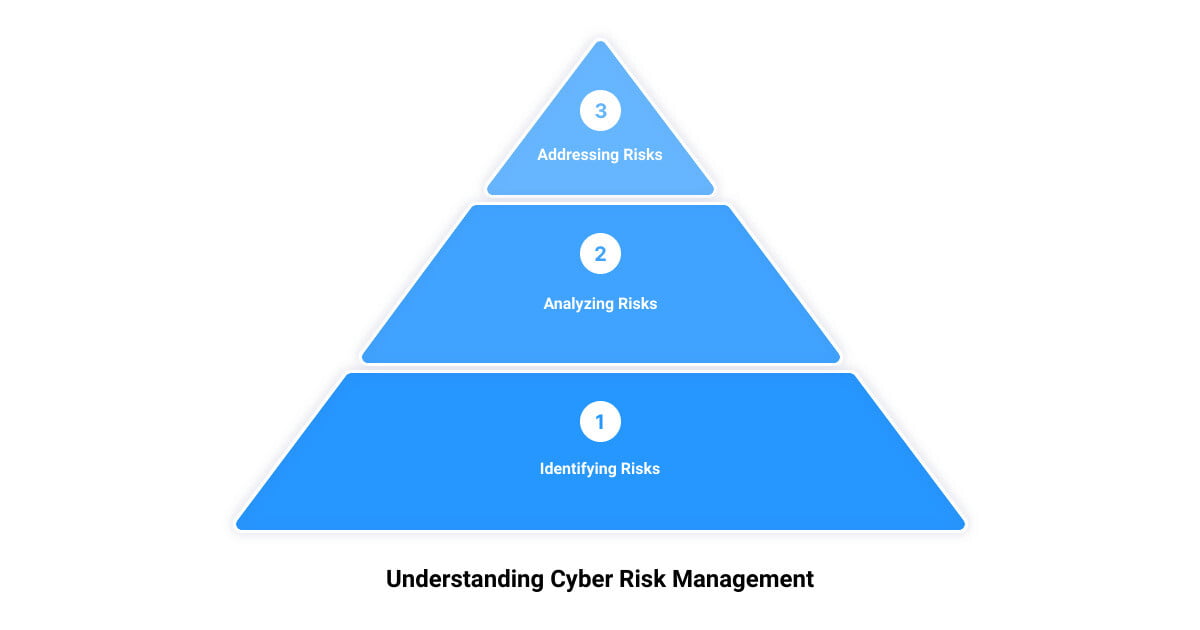
In the digital era, cyber risk management is no longer an option but a necessity for businesses. The strategic approach to understanding and managing cyber risks involves a four-step process that includes identifying, analyzing, evaluating, and addressing cybersecurity risks.
Identifying Cybersecurity Risks
The first step in any cybersecurity risk management strategy is identifying potential cybersecurity risks. This process involves understanding your digital assets, the vulnerabilities they might have, and the potential threats they could face. Remember, the cyber threat landscape is constantly evolving, with new exploits being discovered and patches released to fix them. As your business grows and more devices join your network, the attack surface increases, making ongoing identification of potential risks a critical aspect of your cybersecurity strategy.
Analyzing Cybersecurity Risks
After identifying potential risks, the next step is analyzing these risks. This involves understanding the potential impact of each identified risk on your business operations. Knowing the potential damage an exploit could cause helps prioritize your efforts and resources more efficiently. Cyberattacks are planned and not random. Signs of a planned attack against an organization may include mentions of the organization on the dark web, the registration of similar domain names for phishing attacks, and confidential information like user account credentials being up for sale.
Evaluating Cybersecurity Risks
Evaluating cybersecurity risks is the third step in the process. Here, each identified and analyzed risk is ranked based on its potential impact and the likelihood of it occurring. High-impact, high-probability risks typically receive the highest priority. This step requires a combination of technical understanding, industry knowledge, and business acumen to accurately assess the potential damage a cyber event could cause.
Addressing Cybersecurity Risks
Finally, after identifying, analyzing, and evaluating the risks, it’s time to address these cybersecurity risks. This involves developing and implementing strategies to mitigate the identified risks. It may include putting up firewalls, installing patches, enforcing stricter access controls, or even training employees to recognize and avoid potential cyber threats.
At Upper Echelon Technology Group, we understand that each organization has its unique set of digital assets, vulnerabilities, and potential threats. Therefore, we provide personalized cybersecurity risk management strategies designed to address your specific needs. This includes ongoing monitoring, identification, mitigation, and management of cyber risks, ensuring your business is always a step ahead in the ever-evolving cyber threat landscape.
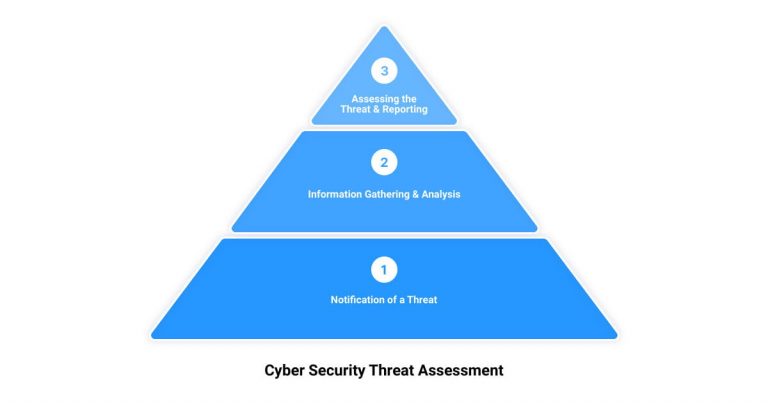
The Five Steps to a Cyber Security Risk Assessment
In the realm of cyber risk management, understanding and managing potential threats is crucial. This is where a thorough Cyber Security Risk Assessment comes into play. A well-executed risk assessment forms the backbone of any robust cybersecurity strategy, enabling businesses to proactively identify vulnerabilities and take appropriate action before they can be exploited.
Scoping: Defining the Boundaries of the Assessment
The first step in a risk assessment is Scoping. This involves clearly defining the boundaries of the assessment to ensure a focused and effective approach to risk management. Here, you identify the systems, data, and processes that are crucial to your business operations, and therefore need to be part of the assessment. The more specific you are about what needs to be protected, the more effective your cybersecurity measures will be.
Risk Identification: Spotting Potential Threats
The next phase is Risk Identification. This is all about spotting potential threats that could negatively impact your key IT assets. Cyber threats range from adversarial threats such as hackers and malware, to natural disasters and human error. The goal is to map out the entire threat environment and understand how these threats could impact your business objectives.
Risk Analysis: Understanding the Impact of Threats
Once potential threats have been identified, Risk Analysis is conducted to understand the impact of these threats should they materialize. This stage involves determining the potential consequences of an attack, including data loss, service disruption, financial losses, and reputational damage. Understanding the possible ramifications of an attack helps in prioritizing risk management efforts.
Risk Evaluation: Prioritizing Risks Based on Impact and Likelihood
Next is Risk Evaluation. Here, risks are prioritized based on their potential impact and the likelihood of their occurrence. This helps to ensure that your risk management strategy is focused on addressing the most significant risks first. Not all risks are created equal, so prioritizing them provides a clear roadmap for implementing security measures.
Documentation: Recording the Assessment Process and Findings
Finally, documenting the entire risk assessment process and findings is essential. This step, Documentation, ensures that there is a record of what was done, what was discovered, and what actions were taken in response. A well-documented risk assessment serves as an important historical reference and provides insights for future risk management efforts.
The aim of a Cyber Security Risk Assessment is to give you a clear picture of your potential vulnerabilities and threats, allowing you to make informed decisions about where to allocate resources for risk mitigation. By following these steps, you can create a strong foundation for your cyber risk management strategy, ensuring your business stays protected in a rapidly changing digital landscape.
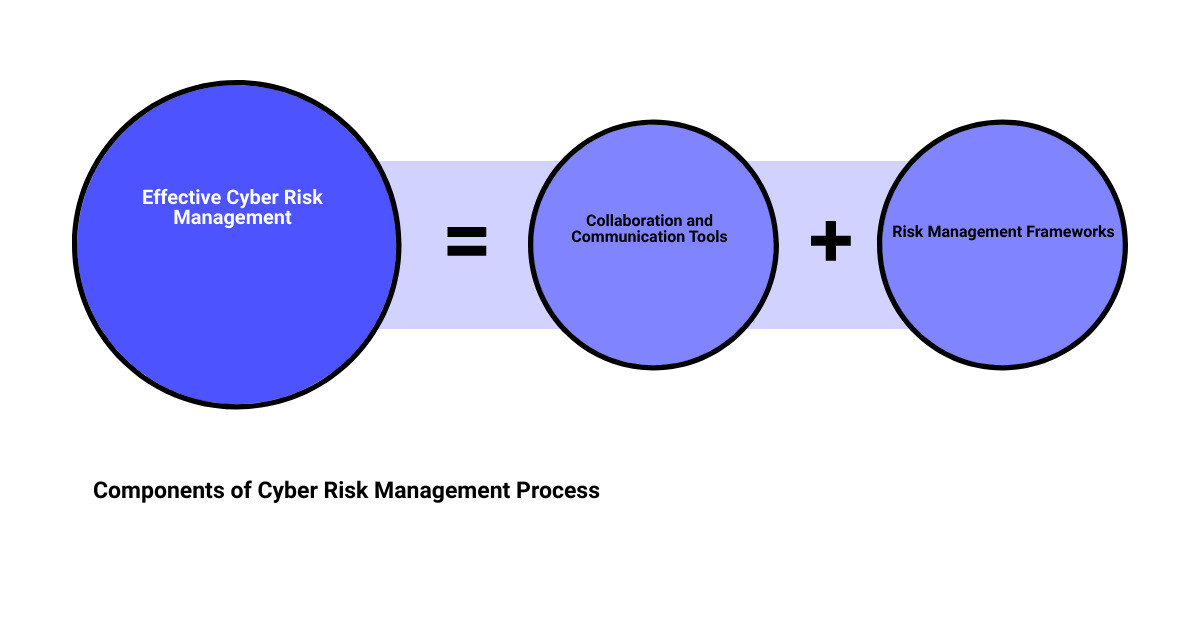
Major Components of a Cyber Risk Management Process
The heart of robust cybersecurity lies in the cyber risk management process. It’s the engine room where potential risks are identified, analyzed, and responded to. This process fosters a proactive approach to cyber risk, rather than a reactive one, allowing businesses to stay ahead of potential threats. Here, we delve into the major components of a cyber risk management process, which are crucial in supporting a comprehensive and robust cybersecurity strategy.
Collaboration and Communication Tools: Ensuring Everyone is on the Same Page
Effective cybersecurity isn’t a one-man show. It requires a collaborative effort from various stakeholders within an organization. Critical in this is the use of collaboration and communication tools. These tools ensure that everyone understands their roles and responsibilities in the cyber risk management process. They facilitate real-time communication, allowing for swift response to potential threats and ensuring that everyone is kept in the loop about current risks and mitigation strategies.
Risk Management Frameworks: Guiding the Process
A cyber risk management process is not a wild guesswork. It’s guided by proven risk management frameworks such as the NIST Cybersecurity Framework or ISO/IEC 27001. These frameworks provide a structured approach to identifying, analyzing, and responding to cyber risks. They serve as a road map, guiding businesses through the complex terrain of cybersecurity, and ensuring they don’t miss any critical steps along the way.
Analytics: Making Sense of Data
In the era of big data, cybersecurity isn’t just about preventing attacks; it’s about understanding them. Analytics play a crucial role in the cyber risk management process by providing insights into potential risks and threats. They allow businesses to make sense of vast amounts of data, identifying patterns and trends that could signify a potential cyber threat. By leveraging analytics, businesses can stay ahead of cybercriminals and proactively address potential vulnerabilities.
Issues Management Tools: Keeping Track of Risks and Responses
Keeping track of identified risks and the corresponding responses is a critical part of the cyber risk management process. Issues management tools facilitate this by providing a centralized platform where all risks and responses can be documented and monitored. They allow businesses to keep a pulse on the status of identified risks, track the progress of mitigation strategies, and ensure that no risk goes unnoticed.
Mastering the cyber risk management process is a crucial step in fortifying your business against cyber threats. By understanding and implementing these major components, businesses can create a robust and effective cybersecurity strategy that keeps them one step ahead of cybercriminals. As a cybersecurity-focused managed services provider, Upper Echelon Technology Group is committed to helping businesses navigate the complexities of cybersecurity and master the art of cyber risk management.
Implementing a Cybersecurity Risk Management Framework
Navigating the treacherous waters of cybersecurity can be a daunting task. Fear not, as we’re here to turn the tide. The key to mastering the art of cyber risk management lies in the strategic implementation of a cybersecurity risk management framework. Let’s dive into the steps involved.
Understanding the Security Landscape: Knowing What You’re Up Against
The first step is akin to mapping out the battlefield. Understanding the security landscape involves getting to grips with the nature, volume, and severity of cyber threats that your business might face. This involves staying updated on the latest cybersecurity threats, the methods employed by cybercriminals, and the areas of your IT infrastructure that may be most vulnerable.
Identifying Gaps: Finding Weaknesses in Your Current Approach
Once you understand the threats, it’s time to turn the lens inwards. Identifying gaps involves conducting a thorough audit of your existing cybersecurity measures. Are there areas that are not adequately protected? Are there policies and procedures that are outdated or ineffective? These gaps are your weak points that cybercriminals may exploit.
Creating a Team: Assembling the Right People for the Job
Cybersecurity is not a one-man show. It requires a dedicated and skilled team to ensure all bases are covered. Your cybersecurity team could include IT professionals, risk management experts, and even representatives from various business units. The goal is to have a team that can work together to manage, mitigate, and respond to cyber risks effectively.
Assigning Responsibilities: Making Sure Everyone Knows Their Role
Once the team is assembled, it’s crucial that everyone knows their role. Clear role definition ensures that every aspect of the cybersecurity risk management process is addressed and that there is accountability. Everyone should know their responsibilities and be equipped to fulfill them.
Prioritizing Risk Management Training: Ensuring Everyone is Prepared
Training is the secret sauce that makes your cybersecurity team effective. It’s not enough for your team to know their responsibilities; they should also be trained to fulfill them effectively. This could involve training on the latest cybersecurity best practices, how to identify and respond to threats, and how to use any cybersecurity tools or software you have in place.
Implementing Cybersecurity Awareness Campaigns: Keeping Everyone Informed
Awareness is the first line of defense against cyber threats. Hence, implementing cybersecurity awareness campaigns across your organization is crucial. These campaigns can educate employees about the importance of cybersecurity, the types of threats they may face, and the steps they can take to protect themselves and the business.
Implementing a Risk Management Framework Based on Industry Standards
Finally, it’s time to implement a risk management framework. This could be based on industry standards such as the NIST CSF, ISO 27001, or DoD RMF, which provide a comprehensive roadmap for managing cyber risks. These frameworks provide guidelines for identifying, assessing, and mitigating cyber risks, and can be tailored to fit the unique needs of your business.
Implementing a cybersecurity risk management framework is not a one-time task. It’s an ongoing process that requires constant vigilance, regular updates, and periodic evaluations. However, with the right approach and the help of a trusted partner like Upper Echelon Technology Group, you can navigate the cyber risk maze and ensure that your business is well-protected against cyber threats.
The Role of Managed Services Providers in Cyber Risk Management
When it comes to cybersecurity, there’s no such thing as a one-size-fits-all approach. Each organization has its unique set of challenges, risks, and assets that need to be considered. A trusted Managed Services Provider (MSP) can play a crucial role in helping businesses navigate the complexities of cyber risk management.
How Upper Echelon Technology Group LLC Can Help
As a leading cybersecurity-focused MSP, Upper Echelon Technology Group LLC is uniquely positioned to help small and medium-sized businesses tackle their cybersecurity challenges head-on. With offices in PA, DE, and FL, we offer a personalized approach to IT Managed Services that sets us apart from the competition.
Our approach to cyber risk management is comprehensive and customer-focused. We believe that there are three key components to a successful IT strategy:
- Solving Technology Issues: We understand that tech issues can be a significant distraction for businesses. Our team of experts is always on hand to swiftly resolve these issues, allowing you to focus on your core business functions.
- Leveraging Technology for Efficiency: Technology should be an asset, not a burden. We provide strategic advice on how to leverage your technology assets to enhance your team’s efficiency and productivity.
- Driving Profitability through Technology: By identifying areas where technology can improve your bottom line, we help make your company more profitable.
Our portfolio of managed IT services is best-of-breed, and we constantly evaluate the services and products we offer to our clients. We ensure that your network is protected and optimized 24x7x365, so that your technology serves your business instead of you serving your technology.
In addition to these services, we also uphold a strong company culture that values relationships, personal growth, communication, integrity, teamwork, and service. We believe in doing good in the world while having fun and getting stuff done.
As the digital landscape continues to evolve, so too do the cyber threats that businesses face. With Upper Echelon Technology Group LLC as your trusted partner, you can rest assured that your business is well-equipped to manage these risks and thrive in the digital age.
Mastering the art of cyber risk management is no small feat, but with the right partner, it can be an achievable goal. Let us help you unravel the cyber risk maze and secure your business’s future.
Facing the labyrinth of cyber risks may seem daunting, but with a strategic approach, a comprehensive understanding of the process, and the right partner, you can turn this challenging task into a navigable path towards enhanced security and business profitability.
Upper Echelon Technology Group LLC, a cybersecurity-focused managed services provider, offers a personalized approach to IT Managed Services, helping businesses in Wilmington, DE, and beyond to effectively navigate the cyber risk maze. Our expertise lies in resolving your technology issues, making your team more efficient, and improving your company’s bottom line through strategic technology use.
Our approach goes beyond the technical aspects. We understand that every business is unique, and so are its cybersecurity needs. Therefore, we don’t just “fix tech issues”; we focus on your specific business needs, helping you leverage your technology assets in the most beneficial way possible. Our goal is to ensure your technology serves your business, not the other way around.
As your trusted partner, we will work with you to implement a cybersecurity risk management framework tailored to your business and industry standards. This will involve understanding your security landscape, identifying gaps in your current approach, creating a competent team, assigning responsibilities, prioritizing risk management training, and implementing cybersecurity awareness campaigns.
Our commitment to your business doesn’t end with the implementation of a plan. We believe in the power of continuous improvement and adaptability in the face of evolving cyber threats. We will consistently evaluate and adjust your cybersecurity measures to ensure they remain effective and relevant.
In conclusion, mastering the art of cyber risk management is not just about technology; it’s about understanding your business needs, crafting a strategic approach, and working with a partner you can trust. With Upper Echelon Technology Group LLC, you’re not just getting a service provider; you’re getting a committed partner who cares about your business as much as you do.
Remember, the cyber risk maze may be complex, but it’s not insurmountable. With the right approach and the right partner, you can transform your cyber risk management from a daunting challenge into a strategic advantage. Let’s unravel the cyber risk maze together.