Introduction: The Importance of Cyber Risk Assessment in Today’s Digital Landscape
In the ever-evolving digital universe, cyber threats are more prevalent than ever. They are not just lurking around the corner, but actively knocking on the doors of businesses, big and small. As a small to medium-sized business owner in Wilmington, DE, you may feel like you’re standing on the edge of a cybersecurity abyss, staring into an array of complex threats and vulnerabilities. But, fear not! With a comprehensive cyber risk assessment, you can illuminate the path forward, and ensure your business is fortified against cyber threats.
A cyber risk assessment is not just an IT necessity, but a crucial business tool. It’s your guiding light in the dense fog of cybersecurity, helping you identify, analyze, and prioritize potential risks to your critical systems and sensitive data. It’s an investment that can protect your business, enhance your team’s efficiency, and ultimately improve your bottom line.
In this article, we will unravel the intricacies of the cyber risk assessment process. We will delve into its key concepts, types, and stages, and show you how it can be tailored to meet your specific business needs. Welcome to your cyber risk assessment journey with Upper Echelon Technology Group, your trusted partner in personalized IT Managed Services. Let’s embark on this journey together, paving the way to a more secure and profitable future for your business.
Understanding Cyber Risk Assessment: Definition and Key Concepts
Diving headfirst into the world of cybersecurity can feel daunting, but with the right knowledge and partner, you can navigate this journey with confidence. The first stop on our journey is understanding Cyber Risk Assessment. In essence, this is the process of identifying, assessing, and understanding the various cyber threats that your business could potentially face.
In the realm of IT, risk refers to potential events that could lead to undesired outcomes, such as data breaches or system failures. These events can cause substantial damage to a company’s reputation, financial status, and overall operations. Therefore, a cyber risk assessment is a crucial tool for any business that wants to protect its digital assets and mitigate potential threats.
A typical cyber risk assessment involves identifying the various information assets that could be affected by a cyber attack, such as hardware, systems, laptops, customer data, intellectual property, and other valuable assets. The next step is to identify the various risks that could affect these assets. These risks could stem from a myriad of sources, ranging from cybercriminals and hackers to insider threats and even natural disasters.
After identifying the risks, the process involves analyzing these risks in terms of their potential impact and the likelihood of their occurrence. The resulting information is then used to prioritize which risks should be addressed first and to devise appropriate risk mitigation strategies.
Cyber risk assessments can be performed using different methodologies, including qualitative and quantitative risk analyses. A qualitative risk analysis focuses on the potential impact and probability of an event, while a quantitative risk analysis uses numerical estimates to assess a risk’s effect on your business objectives.
Understanding the intricacies of a cyber risk assessment can feel overwhelming, but rest assured, with the right insights and a comprehensive approach, it becomes a manageable task. As we continue to unravel the complexities of this process, remember that Upper Echelon Technology Group is here to guide you every step of the way, providing robust cybersecurity solutions and personalized IT Managed Services that align with your unique business needs.
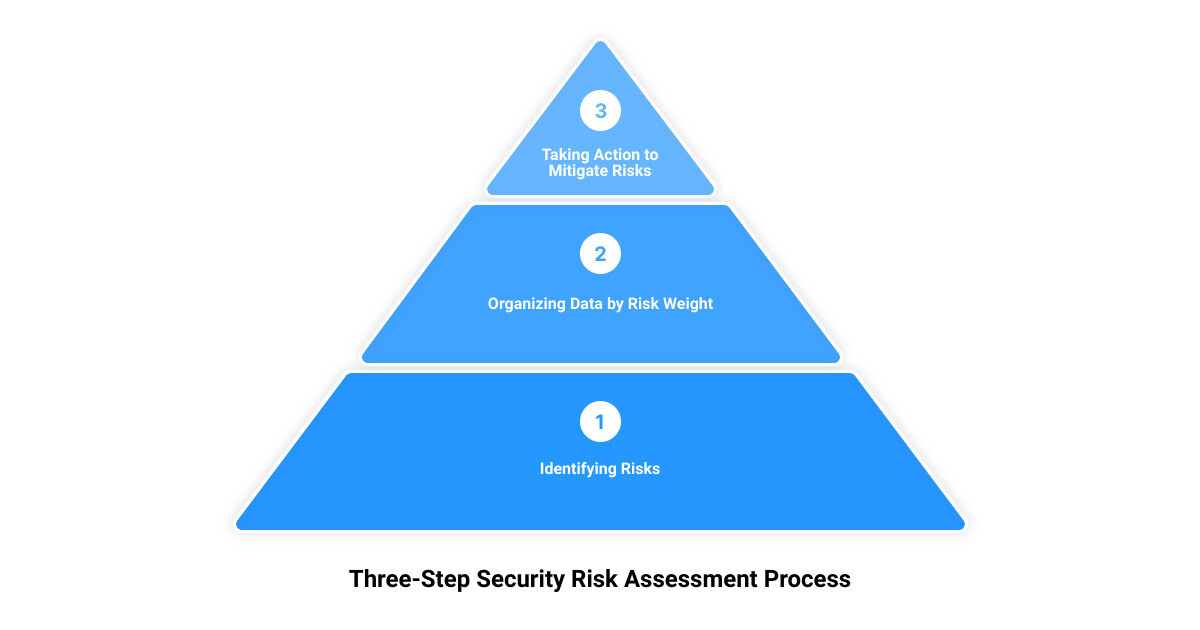
The Three-Step Security Risk Assessment Process
Embarking on the cybersecurity risk assessment journey can feel like navigating a labyrinth without a map. But fear not, it’s more like a three-step dance: identifying risks, categorizing them by weight, and taking action to mitigate them.
Identifying Risks to Critical Systems and Sensitive Data
The first step in this process is akin to casting a wide net, capturing all possible threats that could target your systems and sensitive data. This includes everything from SQL injections on unpatched web servers to DDoS attacks. The aim is to understand the multitude of ways your business could be compromised and the potential damage that could be inflicted. Be sure to consider all possible scenarios, from cyber attacks by malicious hackers to unintentional data breaches caused by employee error.
Organizing Data by Risk Weight
Once the threats have been identified, it’s time to organize them according to their potential impact and likelihood of occurrence. This is where the concept of risk weight comes into play. Each identified risk is assessed based on the potential damage it could cause and its probability of occurrence. For example, an SQL injection on an unpatched web server could result in stolen customer data, leading to regulatory fines and reputational damage. The severity of these consequences would make this a high-weight risk.
Taking Action to Mitigate Risks
Finally, with a clear understanding of the risks and their weight, it’s time to take action. There are several ways to manage these risks: avoid, transfer, or mitigate. If a risk outweighs the benefits, it might be best to avoid it entirely by discontinuing a particular activity. Transferring involves sharing a portion of the risk with another party, such as outsourcing certain operations or purchasing cyber insurance. Mitigation, on the other hand, involves implementing security measures to reduce the likelihood and impact of a risk.
While these steps may seem straightforward, they require careful thought, meticulous analysis, and input from various stakeholders. But remember, you’re not alone. As your trusted cybersecurity partner, Upper Echelon Technology Group can help guide you through each step, ensuring that your business is protected from cyber threats.
Types of Risk Assessment in Cyber Security
To safeguard your business from cyber threats, a detailed risk assessment is crucial. In the realm of cyber security, risk assessments are typically conducted using two distinct methodologies: Qualitative Risk Analysis and Quantitative Risk Analysis. Each type of analysis offers its own benefits and can provide a unique perspective on your company’s cyber risk profile.
Qualitative Risk Analysis: Probability and Impact
In a Qualitative Risk Analysis, the focus is on understanding the probability of a threat occurring and the potential impact it could have on your organization. This approach goes beyond just identifying threats—it involves categorizing them based on severity and their likelihood of occurrence.
Outcomes of a qualitative analysis are typically expressed in terms such as high, medium, or low, which provide a generalized understanding of the risks. This type of analysis is beneficial when you need to quickly prioritize risks and decide where to allocate resources. It is more subjective in nature and relies on the experience and judgement of the cybersecurity team.
Quantitative Risk Analysis: Numerical Estimates of Risk
On the other hand, a Quantitative Risk Analysis involves a more numerical and statistical approach to assessing risks. It provides specific, measurable data, such as the potential financial loss a specific threat could cause. This type of analysis takes into account various factors such as the value of the information asset, the exposure factor (how much of the asset would be lost in an event), and the annual rate of occurrence (how often the event is likely to occur in a year).
By providing a numerical value for potential risks, quantitative risk analysis allows you to make more data-driven decisions about where to invest in cyber security. It offers a more objective and detailed view of the potential risks, making it an excellent tool for long-term planning and budgeting.
In the end, both types of risk assessments – qualitative and quantitative – offer valuable insights and serve different purposes. Often, they are used in tandem to provide a holistic view of an organization’s cybersecurity risk landscape.
Stay tuned for our next section where we will delve deep into the step-by-step process of conducting a cyber risk assessment. From determining your key business objectives and identifying essential IT assets, to implementing mitigation strategies and regularly repeating the process, we will guide you through each step of this crucial journey.
The Cyber Risk Assessment Process: A Detailed Walkthrough
Navigating the intricacies of the cyber risk assessment process might seem daunting, but taking it step by step can make it more manageable. Let’s unravel this process together.
Determining Key Business Objectives and Identifying Essential IT Assets
The first step in the risk assessment journey is to define the scope of the process. This involves determining your key business objectives and identifying all the crucial IT assets that could be affected by a cyber attack. This could include hardware, systems, customer data, intellectual property, and more. It’s important to have full support from all stakeholders whose activities fall within the scope of the assessment, as their input will be vital in understanding which assets and processes are the most important. This step might require the assistance of a third-party specializing in risk assessments to guide through this resource-intensive stage.
Identifying Potential Cyber Attacks and Assessing Their Likelihood and Impact
Once the key assets have been identified, the next step is to identify potential cyber threats to these assets. Resources like the MITRE ATT&CK Knowledge Base and the Cyber Threat Alliance can provide high-quality, up-to-date cyber threat information. It’s also important to consider where each asset sits in the Lockheed Martin cyber kill chain. This will help determine the types of protection they need, as it maps out the stages and objectives of a typical real-world attack.
Analyzing, Prioritizing, and Documenting Risks in a Risk Register
After identifying potential threats, it’s time to analyze and prioritize them based on their potential impact and likelihood of occurrence. This involves assessing each threat’s potential impact on your business and its likelihood. After this, all identified risks should be documented in a risk register. This document should include detailed information about each risk, including its description, cause, effect, existing controls, proposed responses, and more.
Implementing Mitigation Strategies to Reduce Overall Risk
Once the risks have been identified and prioritized, it’s time to implement mitigation strategies to reduce the overall risk. This could involve enhancing security measures, implementing new policies, or even investing in new technologies. The key is to reduce the likelihood of the threat occurring or minimize its impact if it does happen.
Regularly Repeating the Risk Assessment Process to Account for New Threats and Changes
Cyber threats are not static. They evolve and change over time. Therefore, the risk assessment process should be repeated regularly to account for new threats and changes in your IT environment. This enables your business to stay proactive and maintain a strong defense against potential cyber attacks.
The cyber risk assessment process might seem complex, but breaking it down into these five steps can make it more manageable. Remember, the goal is not to eliminate all risks but to manage them effectively. With the proper approach and the right resources, you can navigate this journey successfully and ensure your business remains secure in the digital landscape.
Cyber Risk Management: Beyond the Assessment
Now that we’ve unraveled the elaborate process of a cyber risk assessment, let’s delve into the crucial next steps – managing the identified risks. This stage goes beyond the simple identification and assessment of risks. It involves deciding how to handle the identified risks strategically and implementing the necessary mechanisms to reduce their potential impact on the business.
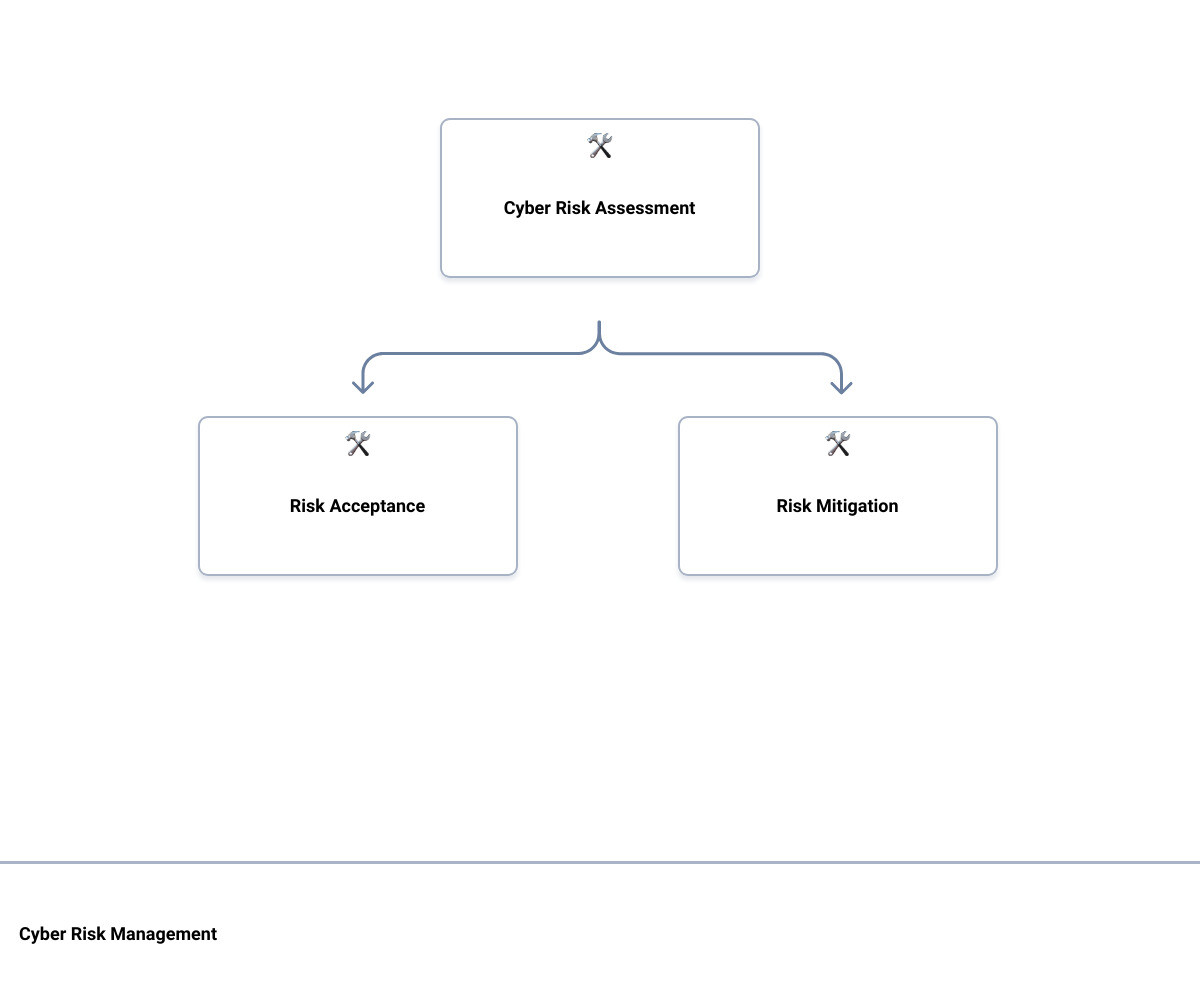
Accepting, Avoiding, Transferring, or Mitigating Risks
There are four primary ways to treat cybersecurity risks: accepting, avoiding, transferring, or mitigating. The choice depends on the specific risk characteristics and the business’s risk tolerance.
Accepting a risk signifies that the organization has determined the risk as minimal or unmanageable with the available resources. However, accepted risks should be reassessed periodically to ensure the risk level remains acceptable.
Avoiding a risk involves halting the activity causing the risk. This option is feasible if the activity is not a vital business function.
In transferring risks, the organization offloads the risk to third parties capable of reducing the risk level. It’s essential to reevaluate transferred risks regularly to ensure the associated risk level has not escalated beyond acceptable levels.
Mitigating a risk means taking appropriate steps to reduce the risk to the organization. This approach often involves implementing mitigating controls or remediation plans, followed by reassessment to ensure the risk level has decreased satisfactorily.
Meaningful Cybersecurity Risk Reporting: What It Should Include
Cybersecurity risk reporting is a vital component of the risk management program. It ensures organizational-wide awareness and active participation in reducing risks. A meaningful risk report should include a defined scale for scoring, compliance alignment, frequency of assessments, risk scoring inputs, treatment decisions, and risk remediation. These components provide comprehensive insights into your organization’s risk landscape and aid in devising effective risk management strategies.
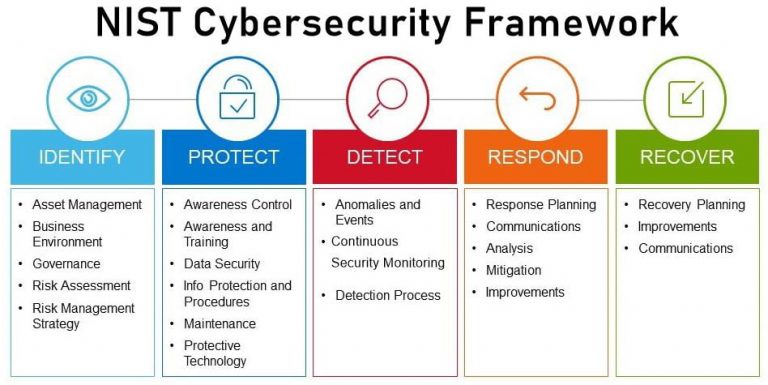
Understanding Different Cybersecurity Frameworks and Their Risk Management Requirements
Various cybersecurity frameworks provide guidelines for managing cyber risks effectively. Each framework has specific risk management requirements that organizations need to understand and adhere to. For instance, SOC 2, ISO 27001, PCI 4.0, and NIST CSF are common frameworks that provide detailed guidance on risk management.
The ultimate goal of cybersecurity risk management is not to eliminate all risks but to manage them effectively. By understanding and implementing the steps of accepting, avoiding, transferring, or mitigating risks, creating meaningful risk reports, and understanding different cybersecurity frameworks, organizations can navigate the complexities of cyber risk management successfully.
How Upper Echelon Technology Group LLC Can Help with Your Cyber Risk Assessment Journey
Navigating the convoluted path of cyber risk assessment might seem daunting. But with the right partner at your side, it becomes a manageable, even rewarding, journey.
Personalized IT Managed Services for Effective Cyber Risk Management
The Upper Echelon Technology Group LLC stands apart in the realm of cybersecurity-focused managed services providers. We don’t merely fix your tech issues. We delve deeper into your unique business needs, leveraging technology to efficiently solve your challenges, enhance your team’s productivity, and ultimately, boost your bottom line.
We understand that every business is different and so are its technology needs. Therefore, we continually evaluate the services and products we offer, ensuring your network is always protected and optimized. This allows your technology to serve your business needs instead of the other way around.
Tailored Approach to Meet Specific Business Needs
Our approach to cyber risk assessment is as unique as your business. We don’t believe in one-size-fits-all solutions. Instead, we design a custom cyber risk assessment process that aligns with your specific business objectives and the types of data you process.
We help you identify potential cyber attacks, assess their likelihood and impact, and document these risks in a risk register. Once the risks have been analyzed and prioritized, we work with you to implement effective mitigation strategies, reducing your overall risk.
But our job doesn’t end there. Recognizing that the cyber threat landscape is continually evolving, we regularly repeat the risk assessment process, accounting for new threats and changes in your business operations.
With the Upper Echelon Technology Group LLC managing your cyber risk assessment journey, you can focus on what you do best – running your business. And you can rest easy, knowing that your network security is in capable hands, ready to tackle whatever cyber threats may emerge.
Conclusion: Navigating the Cyber Risk Assessment Journey Successfully
In the intricate labyrinth of today’s digital landscape, a comprehensive cyber risk assessment is your reliable compass. It’s a crucial endeavor that not only safeguards your business from potential cyber threats but also empowers it to leverage technology for growth, efficiency, and profitability – the three key values that the Upper Echelon Technology Group LLC strives to deliver for its clients.
The cyber risk assessment journey unfolds through multiple stages, from identifying risks associated with critical systems and sensitive data to implementing mitigation strategies to reduce overall risk. It involves qualitative and quantitative risk analysis, meticulously documenting risks in a risk register, and regularly repeating the risk assessment process to account for new threats and changes.
Remember, the journey doesn’t end with the assessment. Effective cyber risk management extends to accepting, avoiding, transferring, or mitigating risks, and generating meaningful cybersecurity risk reports. It also requires a deep understanding of different cybersecurity frameworks and their risk management requirements.
While the journey may seem daunting, partnering with a cybersecurity-focused managed services provider like the Upper Echelon Technology Group LLC can ease your way. Their personalized approach to IT managed services ensures that your cybersecurity measures are not only robust but also tailored to your specific business needs.
As the digital landscape continues to evolve and cyber threats become increasingly sophisticated, the importance of a comprehensive cyber risk assessment cannot be overstated. Navigating this journey successfully is paramount to your business’s resilience and growth. So, equip your business with the right tools, partner with the right experts, and embrace the cyber risk assessment journey as an integral part of your business strategy.
In the end, it’s more than just about mitigating risks—it’s about harnessing the power of technology to drive your business forward. With the Upper Echelon Technology Group LLC by your side, you can confidently navigate the cyber risk assessment journey and transform potential threats into opportunities for growth.