As the digital landscape continues to evolve, so does the plethora of cyber threats that lurk within it. Cyber risk is a reality that businesses, especially small to medium-sized ones, can no longer ignore. The stakes are high, and the consequences of a data breach can be devastating. This is the world of cyber risk assessment and management, a world in which we at Upper Echelon Technology Group excel.
At the heart of any robust cybersecurity strategy is an understanding of the risks involved. Cyber risks, sometimes called security threats, can take many forms including ransomware, data leaks, phishing, malware, and insider threats. Each of these threats carries a potential for unauthorized network access and significant reputational or financial damage if exploited.
Cyber risk, therefore, is the likelihood of a vulnerability being exploited, and it can range from zero, low, medium, to high-risk. The level of risk is determined by a combination of factors such as the nature of the threat, the vulnerability of the system, and the impact of a potential breach.
As a business owner, it’s essential to understand your organization’s cyber risk landscape and how to effectively manage it. At Upper Echelon Technology Group, we specialize in conducting comprehensive cyber risk assessments and providing personalized IT Managed Services to safeguard your business.
Here’s a quick look at what cyber risk assessment and management entail:
-
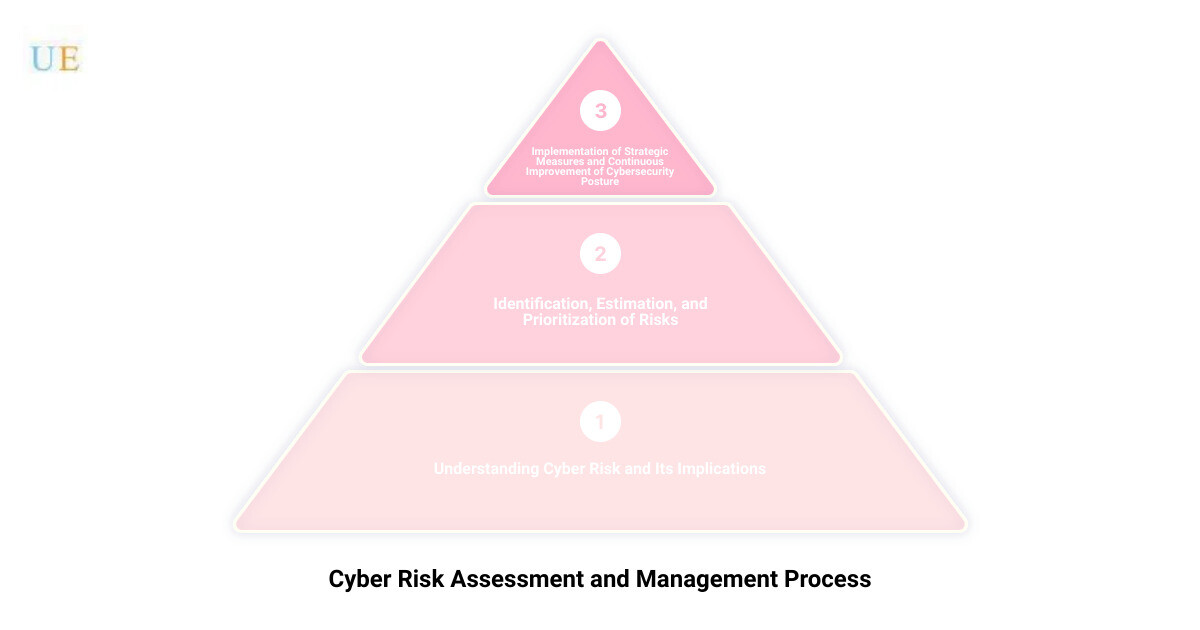
Cyber Risk Assessment: This is a process used to identify, estimate, and prioritize risk to organizational operations, assets, and other stakeholders, resulting from the operation and use of information systems.
-
Cyber Risk Management: This involves the implementation of strategic measures to mitigate identified risks, monitor their effectiveness, and ensure the continuous improvement of your cybersecurity posture.
Understanding cyber risk and its implications is the first step towards securing your business in the digital age. Stay tuned as we unravel the complexities of cyber risk assessment and management and guide you towards a more secure future.
Defining Cyber Risk Assessment and Management
What is Cyber Risk Assessment and Management?
In the constantly evolving landscape of cybersecurity, understanding and addressing potential vulnerabilities and threats is crucial. Enter Cyber Risk Assessment and Management. But what exactly does that entail?
According to the National Institute of Standards and Technology (NIST), cyber risk assessments are used to identify, estimate, and prioritize risk to organizational operations, assets, individuals, and even other organizations, emanating from the operation and use of information systems. In essence, it involves analyzing the potential risks associated with cyber threats and the impact they could have on an organization’s operations.
Cyber risk management, on the other hand, is a continuous, strategic process that involves identifying, analyzing, and responding to these risk factors. It considers not only the potential impact of a successful cyber attack but also the organization’s overall risk tolerance and existing cybersecurity measures.
At Upper Echelon Technology Group, our team of cybersecurity experts is adept at understanding the complexities of cyber risk assessment and management. We are equipped to help businesses navigate these challenges and secure their digital assets.
The Importance of Cyber Risk Assessment and Management
As the saying goes, knowledge is power. In the realm of cybersecurity, understanding potential threats and vulnerabilities is the first step in fortifying defenses. A comprehensive cyber risk assessment provides this knowledge, enabling organizations to better manage and mitigate risks associated with their digital operations.
A robust cyber risk management strategy goes beyond just identifying potential risks. It facilitates the development of security controls and measures tailored to the unique needs of each organization. By anticipating and planning for potential cyber threats, organizations can protect crucial data, maintain customer trust, and ensure business continuity.
The importance of cyber risk assessment and management cannot be overstated. As cyber threats continue to evolve and grow in sophistication, having a proactive and comprehensive approach to managing these risks is essential for all businesses, regardless of size or industry.
At Upper Echelon Technology Group, we understand the critical role that cyber risk assessment and management plays in overall business strategy. That’s why we offer personalized IT Managed Services focusing on cybersecurity, empowering businesses to leverage their technology assets securely and efficiently.
As we continue to delve into the intricacies of cyber risk, stay tuned to learn more about the process of conducting a cybersecurity risk assessment and the five elements of cyber risk management.
The Process of Conducting a Cybersecurity Risk Assessment
With the rising tide of cyber threats, understanding the process of conducting a cybersecurity risk assessment is crucial. It’s an intensive process that helps businesses identify, analyze, and evaluate potential risks. Performing an assessment ensures that the cyber security controls you implement are suited to the risks your organization faces. Let’s break this process down into digestible steps.
Step 1: Defining Cybersecurity Threats
The process begins by defining the cybersecurity threats that could pose a risk to information assets such as hardware, systems, laptops, customer data, and intellectual property. This identification is crucial to recognize what you are defending against.
Step 2: Identifying Security Vulnerabilities
Next, we at Upper Echelon Technology Group identify vulnerabilities. These are the weak spots in your systems that could be exploited by threats. From outdated software to insecure user practices, these vulnerabilities can take many forms.
Step 3: Determining Threat Likelihood and Threat Impact
Once threats and vulnerabilities are identified, we assess the likelihood of each threat and the potential impact if they were to occur. This estimation and evaluation help prioritize the risks based on their severity.
Step 4: Cataloging Information Assets
We then catalog information assets that could be affected by a cyber attack. This step is important to understand what data is at risk and prioritize its protection.
Step 5: Assessing the Risk
The next step is the risk assessment itself. This involves assessing the level of risk posed by each identified threat and vulnerability, considering both the likelihood of occurrence and potential impact.
Step 6: Analyzing the Risk
After assessing the risks, we analyze them according to the criteria established in the previous steps. This helps in understanding the nature of the risks and how they might affect your organization.
Step 7: Setting Security Controls
Following the analysis, we select security controls to treat the identified risks. These controls can vary from technological solutions like firewalls and encryption to policies and procedures like password requirements and user training.
Step 8: Monitoring and Reviewing Effectiveness
Finally, it’s crucial to monitor and review the effectiveness of the security controls. This is a continuous process, as the risk environment can change over time. Regular reviews ensure that your risk management process adapts to any changes and remains effective.
The cybersecurity risk assessment process is not a one-and-done deal. It’s a cycle that needs to be repeated regularly to keep up with evolving cyber threats and changes within your organization. At Upper Echelon Technology Group, we emphasize a personalized approach to this process, ensuring that it aligns with your business needs and helps you leverage your technology assets in the best way possible.
The Five Elements of Cyber Risk Management
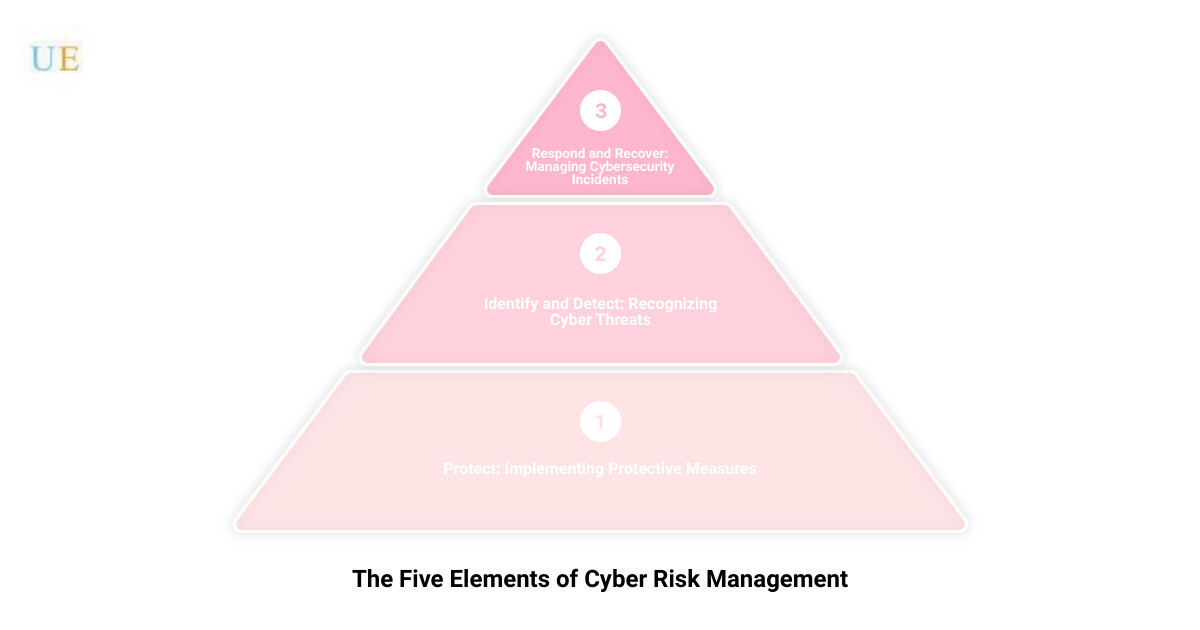
Just like a well-oiled machine needs various components working in harmony to function optimally, an effective cyber risk management strategy requires a blend of key elements. These elements, based on the NIST (National Institute of Standards and Technology) framework, provide a comprehensive approach to managing cyber risks. They are Protect, Identify, Detect, Respond, and Recover.
Protect: Implementing Protective Measures
The first line of defense in any cybersecurity strategy is protection. This step involves implementing safeguards to ensure delivery of critical infrastructure services and to limit or contain the impact of potential cybersecurity incidents.
At Upper Echelon Technology Group, we understand that the best defense is a good offense. We constantly evaluate the services and products we offer our clients, ensuring that your network is protected and optimized 24x7x365. This way, your technology serves your business instead of you serving your technology.
Identify: Recognizing Potential Threats
Knowledge is power, and in cybersecurity, identifying potential threats is a critical first step in mitigating cyber risks. This involves developing an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
Our expert team at Upper Echelon Technology Group uses state-of-the-art tools and techniques to identify threats that could compromise your business’s security, enabling you to take pre-emptive measures.
Detect: Monitoring for Cybersecurity Incidents
Despite the best protective measures, cybersecurity incidents can still occur. This is where detection comes in. It involves developing and implementing appropriate activities to identify the occurrence of a cybersecurity incident in a timely manner.
Our advanced monitoring systems and incident detection procedures ensure that if a breach or attack occurs, we are able to detect it quickly and respond effectively.
Respond: Taking Action Against Cybersecurity Threats
Responding to a cyber threat involves taking action to contain the impact of a detected cybersecurity incident. It’s about having a plan in place to deal with the aftermath of a cyber attack and to minimize business disruption.
At Upper Echelon Technology Group, we have a dedicated response team that springs into action the moment a cyber threat is identified, working diligently to contain and neutralize the threat.
Recover: Restoring Systems After a Cybersecurity Incident
The final piece of the puzzle is recovery. This involves maintaining plans for resilience and restoring any capabilities or services that were impaired due to a cybersecurity incident.
Our team at Upper Echelon Technology Group is committed to getting your business back on its feet as quickly as possible after a cyber incident, minimizing downtime and loss of productivity.
These five elements form the backbone of our cyber risk management strategy at Upper Echelon Technology Group. By incorporating these elements into our services, we provide our clients with a comprehensive and robust defense against cyber threats.
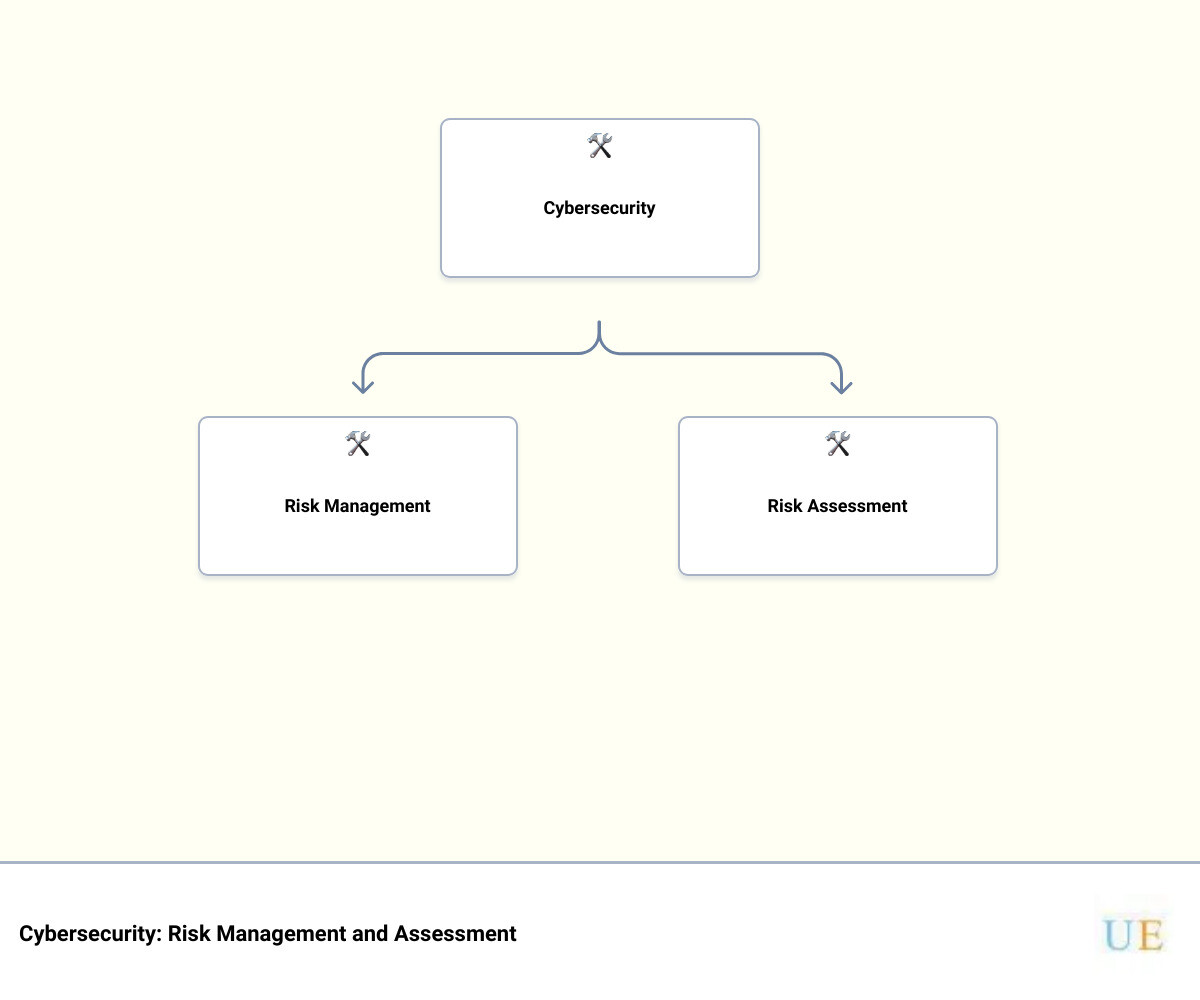
The Difference Between Risk Management and Risk Assessment in Cybersecurity
In the realm of cybersecurity, risk management and risk assessment are two distinct but interconnected concepts that play an integral role in safeguarding your business. They represent different stages in the process of identifying and mitigating potential threats to your organization’s information systems. Let’s take a closer look at each of these.
Understanding Risk Management
Risk management, as we practice at Upper Echelon Technology Group, is an ongoing, proactive process aimed at identifying, analyzing, and responding to risk factors that could potentially harm your business operations. It involves establishing strategic plans and implementing security controls to minimize the potential impact of cyber threats on your business. The goal is to ensure that your technology serves your business, instead of your business serving your technology.
Risk management is not a one-time event, but a continuous process that evolves with your business and the ever-changing cybersecurity landscape. It encompasses the entire lifecycle of risk, from identification and assessment to mitigation and monitoring.
Understanding Risk Assessment
On the other hand, risk assessment is a component of risk management that focuses specifically on detecting hazards and analyzing all potential risks in the workplace. It’s a systematic process that involves defining cybersecurity threats, identifying security vulnerabilities, determining threat likelihood and impact, and cataloging information assets.
Risk assessment gives you a clear picture of your organization’s risk landscape, helping you understand where your vulnerabilities lie and how they could potentially impact your business. By conducting regular cybersecurity risk assessments, you can stay one step ahead of cyber threats and ensure that your risk management strategies are up-to-date and effective.
In conclusion, while risk management is the broad, ongoing process of managing and mitigating risks, risk assessment is a specific step within that process aimed at identifying and analyzing potential threats. Both are critical for maintaining a strong cybersecurity posture and protecting your business from the evolving landscape of cyber threats.
At Upper Echelon Technology Group, we understand the importance of both risk management and risk assessment in cybersecurity. We continuously evaluate our services and products to ensure that your network is protected and optimized, providing you with the peace of mind that your technology is serving your business as it should.
(An infographic illustrating the relationship between risk management and risk assessment in cybersecurity, showing how risk assessment is a component of the broader risk management process.)
The Role of Upper Echelon Technology Group LLC in Cyber Risk Assessment and Management
When it comes to navigating the intricate landscape of cybersecurity, the unique approach of Upper Echelon Technology Group makes a significant difference. Our expertise lies not only in resolving tech issues, but also in strategically leveraging your technology assets to drive business growth, efficiency, and profitability.
Personalized IT Managed Services
At Upper Echelon Technology Group, we are more than just an IT company. We are your partner, dedicated to understanding your business needs and aligning them with the right technology solutions. We are driven by a commitment to our core values, which emphasize relationships, personal growth, honest communication, and a strong work ethic. As stated on our company website, “[We] provide a company culture that allows our employees and clients to reach their fullest potential.”
Our portfolio of managed IT services is best-in-class. We constantly evaluate the services and products we offer to ensure your network is protected and optimized 24/7/365. We want technology to serve your business, not the other way around.
Tailored Approach to Cyber Risk Assessment and Management
Understanding cyber risk is not a one-size-fits-all process. Our approach to cyber risk assessment and management is tailored to your specific business needs. Using the proven methodologies from established frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework and the ISO 27001:2013 standard, we identify, assess, and prioritize your cyber risks.
As part of our cyber risk assessment, we evaluate your organization’s vulnerabilities and threats to establish a comprehensive understanding of the risks you face. We provide recommendations for mitigating those risks, ensuring that you are equipped with the knowledge and tools needed to protect your information and systems from cyber threats.
In addition, we understand that managing cyber risk is a continuous process. As your business evolves, so do your cyber risks. That’s why we emphasize ongoing monitoring and reviewing of the risk environment to detect any changes and maintain an overview of the complete risk management process.
At Upper Echelon Technology Group, we don’t just provide a service, we offer a partnership. We are here to help you navigate the complexities of cybersecurity, so you can focus on what you do best – running your business.
(A photo of the Upper Echelon Technology Group team, showcasing their commitment to providing personalized IT managed services.)
In the next section, we will conclude our discussion on cyber risk assessment and management, underlining its importance and the crucial role it plays in ensuring the security of your organization’s information and systems.
Conclusion: The Importance of Regular Cyber Risk Assessment and Management
As we power down our discussion on cyber risk assessment and management, one thing remains clear: it’s not a one-and-done process. The digital landscape is dynamic, evolving rapidly with new threats and vulnerabilities emerging regularly. Therefore, it’s not only crucial to conduct an initial cyber risk assessment and management, but also vital to keep this process an ongoing routine.
The Ever-Changing Nature of Cyber Threats
The cybersecurity landscape is a battlefield that never sleeps. With cybercriminals continually innovating and refining their strategies, an organization’s cybersecurity measures must adapt accordingly. The threats we face today may not be the same ones we face tomorrow. This constant evolution necessitates regular cyber risk assessments and management.
Regular assessments enable your organization to stay one step ahead of potential cyber threats. They help you identify new vulnerabilities, understand evolving threat patterns, and update your cybersecurity strategy accordingly. This proactive approach to cybersecurity is a critical factor in protecting your organization’s information and systems.
The Role of Upper Echelon Technology Group in Sustaining Cybersecurity
At Upper Echelon Technology Group, we understand the significance of maintaining a robust cybersecurity posture. Our personalized approach to IT Managed Services extends to our cyber risk assessment and management strategies. We work closely with our clients to understand their unique business needs and technology assets. By leveraging this understanding, we tailor our cyber risk assessment and management to align with their specific circumstances and requirements.
Our team continually monitors the cybersecurity landscape, staying up-to-date with the latest threats and vulnerabilities. We regularly review and update our clients’ cybersecurity strategies, helping them stay ahead of the curve. In addition to solving technology issues, we focus on how technology can improve your bottom line. This is part of our commitment to making your company more profitable by identifying areas where technology can enhance your operations.
In Conclusion
Given the significant consequences a cybersecurity incident can have on an organization, the importance of regular cyber risk assessment and management cannot be overstated. It is critical for any organization that values its data and the continuity of its operations. With our commitment to personalized service and our deep understanding of cybersecurity, we at Upper Echelon Technology Group stand ready to address your cyber risk assessment and management needs.
In a world where cyber threats are a daily reality, staying ahead of the curve is no longer an option, but a necessity. And that’s exactly what we’re here for. Upper Echelon Technology Group – your trusted partner in navigating the complex landscape of cybersecurity.