Introduction to Cyber Risk Analysis
In the ever-evolving digital landscape, cybersecurity is no longer a mere option—it is a necessity. One crucial facet of cybersecurity that businesses need to pay attention to is cyber risk analysis. As technology becomes increasingly intertwined with our everyday operations, understanding and mitigating potential cyber threats becomes essential to ensure business continuity and data integrity.
Cyber risk analysis is the process of identifying, assessing, and responding to cybersecurity threats. It’s an analytical method that helps organizations understand the potential risks they face, allowing them to take steps to reduce their vulnerabilities and protect their most valuable digital assets. This process is a critical component of a sound cybersecurity strategy, enabling businesses to expose hidden threats and take proactive measures to prevent costly breaches.
For a small to medium-sized business operating in today’s digital economy, the stakes are high. A single cyber attack can result in significant financial losses, customer trust erosion, and potential regulatory penalties. That’s where the expertise of a cybersecurity-focused managed services provider like Upper Echelon Technology Group becomes invaluable. With a personalized approach to IT Managed Services, we can help you navigate the complexities of cyber risk analysis, ensuring your business remains resilient in a perilous cyber threat landscape.
In the following sections, we will delve deeper into the nature of cybersecurity risks, the importance of risk assessments, and how businesses can leverage different types of risk analysis to protect their operations and drive growth.
Understanding Cybersecurity Risks
Unmasking the invisible enemy begins with understanding the nature of cybersecurity risks. In an era where cyber threats are ever-evolving, and the digital landscape is continually expanding, it’s vital to keep a finger on the pulse of potential dangers lurking in the shadows of your network.
The Importance of Cybersecurity Risk Assessment
A cybersecurity risk assessment is not just a box to be checked; it’s a strategic tool that uncovers hidden vulnerabilities and potential points of attack within your business’s IT infrastructure. It goes beyond mere compliance. While regulations such as HIPAA, Sarbanes-Oxley, and PCI DSS require formalized risk assessments, merely fulfilling these requirements does not guarantee total protection. A thorough risk assessment illuminates the path to robust cybersecurity, empowering organizations to understand, control, and mitigate cyber risks.
Identifying Key Business Objectives and IT Assets
The first step in a risk assessment is to identify your business’s key objectives and IT assets. This process is not limited to listing out your organization’s crown jewels; it also involves identifying assets that attackers might target as pivot points in a broader attack. Assets such as an Active Directory server or picture archive and communications systems could be potential targets. A comprehensive inventory of all physical and logical assets within the scope of the risk assessment is thus crucial. Not only does it help define the scope of the risk assessment, but it also aids in visualizing the interconnectivity between assets, processes, and potential entry points into the network.
Recognizing Potential Cyber Attacks and Their Impact
Understanding the types of cyber threats your assets face is pivotal in cybersecurity risk analysis. Threats are the tactics, techniques, and methods used by threat actors that have the potential to harm an organization’s assets. Resources like the MITRE ATT&CK Knowledge Base and the Cyber Threat Alliance provide valuable insights into potential threats, helping you better understand how threat actors might attack your systems. Additionally, knowing where each asset sits in the Lockheed Martin cyber kill chain can reveal the types of protection they need and help anticipate the stages and objectives of a typical real-world attack.
Unveiling the hidden threats in your IT infrastructure requires a comprehensive understanding of cybersecurity risks. It involves recognizing the importance of risk assessments, identifying key business objectives and IT assets, and understanding potential cyber attacks and their impact. Armed with this knowledge, you can embark on your cybersecurity risk analysis journey with Upper Echelon Technology Group, equipped to expose and conquer the hidden threats in your network.
Types of Cyber Security Risk Analysis
Let’s dive deeper into the ocean of cyber risk analysis. There are two main types of cybersecurity risk analysis approaches that businesses can employ to assess their digital vulnerabilities – Qualitative Risk Analysis and Quantitative Risk Analysis. Both have their unique strengths and are best used in conjunction with each other for a comprehensive view of your company’s cybersecurity posture.
Qualitative Risk Analysis
First off, let’s discuss Qualitative Risk Analysis. This approach is akin to a seasoned detective investigating a crime scene. It doesn’t rely on numbers or hard data but rather on the subjective expertise of security professionals. By following the probability and impact number, it provides an understanding of potential threats based on their likelihood of occurrence and the potential damage they could cause.
In this analysis, threats and vulnerabilities are ranked according to their severity and potential impact on the business, often using a scale like low, medium, or high. For instance, a high-level threat with a high impact would be given top priority in your risk mitigation strategies.
Though qualitative in nature, this method provides a high-level overview of the security risks and helps businesses prioritize their actions.
Quantitative Risk Analysis
Next up is Quantitative Risk Analysis. Think of this as the meticulous accountant of cyber risk analysis. Unlike its qualitative counterpart, this method uses numerical data to estimate the effects of potential risks. It provides a more concrete and measurable approach, allowing businesses to quantify their risk in terms of potential financial loss or downtime.
Quantitative Risk Analysis employs statistics, simulations, and numerical estimates to provide a potential dollar value associated with a risk. For instance, how much would a data breach cost your company in recovery efforts, regulatory fines, and lost business?
This type of risk analysis is particularly useful in making informed budgeting decisions regarding security investments and insurance coverage.
Both these methods of analysis are key tools in the arsenal of cybersecurity risk assessment. By understanding and applying both qualitative and quantitative risk analysis, businesses can gain a holistic view of their cybersecurity landscape, enabling them to effectively manage and mitigate risks.
With Upper Echelon Technology Group, your business can leverage these risk analysis methods to expose hidden threats and strengthen your cybersecurity defenses. Our expert team is adept at both qualitative and quantitative risk analysis, ensuring that you’re armed with the most comprehensive risk assessment possible.
The Process of Cyber Risk Analysis
Embarking on a cyber risk analysis journey can feel like navigating a dense labyrinth. However, with a clear map and an experienced guide, you can make it through unscathed. Here’s how the process unfolds with the Upper Echelon Technology Group.
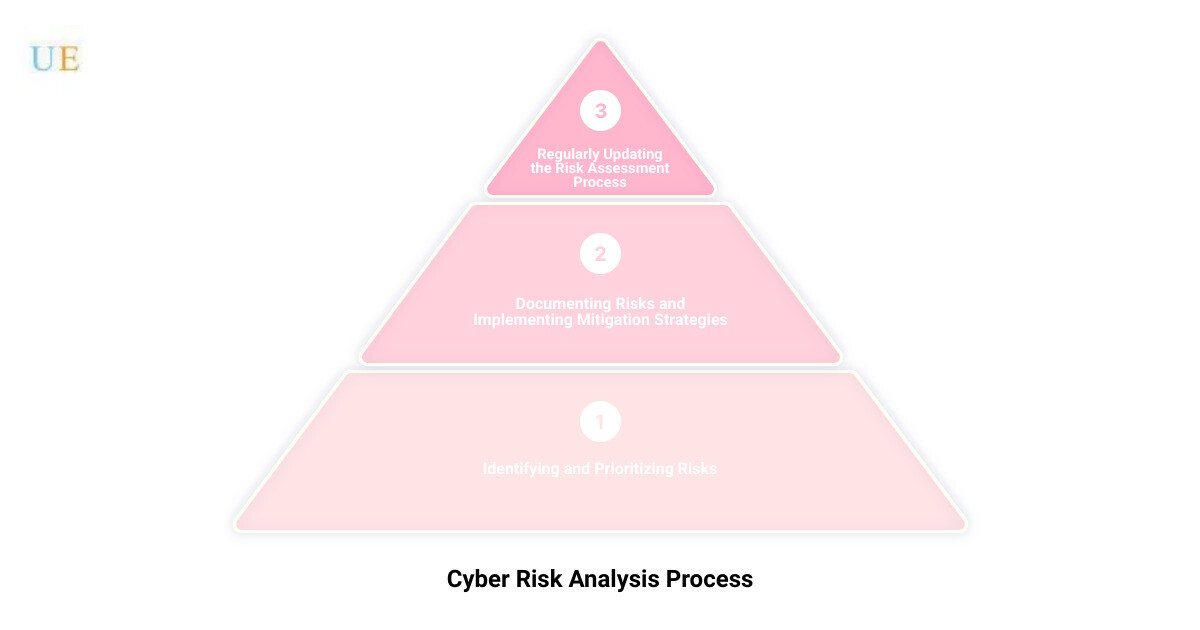
Identifying and Prioritizing Risks
Unseen threats lurk in the shadows of your IT infrastructure. The first step is to identify these risks. This involves gathering data about your digital ecosystem, understanding your business objectives, and pinpointing the IT assets that underpin these goals. Risks are then prioritized based on their potential impact on your business. This ensures that the most critical threats are tackled first.
Documenting Risks in a Risk Register
All identified risk scenarios are meticulously documented in a risk register. This is more than just a ledger of problems. It’s a living document that provides an up-to-date account of your cybersecurity risks, including crucial details like the risk scenario, identification date, existing security controls, current risk level, treatment plan, and progress status. It also identifies the risk owner, the individual or group responsible for ensuring the residual risks remain within acceptable levels.
Implementing Mitigation Strategies
Armed with the insights from your risk register, the next step is to implement mitigation strategies. This involves developing a treatment plan that outlines the planned activities and timeline to bring the risk within an acceptable tolerance level. The treatment plan also includes the commercial justification for investment, ensuring that your cybersecurity strategy aligns with your business objectives.
Regularly Updating the Risk Assessment Process
The cyber risk landscape is not static. It evolves rapidly, with new threats emerging and existing ones morphing into more sophisticated forms. Therefore, the risk assessment process is not a one-time event but requires regular updating. Upper Echelon Technology Group makes this a priority, ensuring that your business is always prepared for the latest cyber threats.
In conclusion, the process of cyber risk analysis is a methodical and continuous effort. It involves identifying and prioritizing risks, documenting them in a risk register, implementing mitigation strategies, and regularly updating the process to reflect the ever-changing cyber risk landscape. With Upper Echelon Technology Group, you can navigate this process with confidence, knowing that your cybersecurity defenses are robust and ready to combat any threat.
Standards for Cyber Risk Assessment
Navigating the complex landscape of cybersecurity can feel like deciphering a foreign language. But fear not, as there are established standards for cyber risk assessment which provide a roadmap for businesses. These standards help to ensure your organization’s resilience against industry-specific risks, and they serve as the backbone for any effective cybersecurity strategy.
NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) offers a comprehensive framework for managing and reducing cybersecurity risks. This voluntary framework is widely recognized and provides guidelines for identifying, protecting, detecting, responding, and recovering from cyber threats. With its flexible and customizable approach, it’s no wonder that the NIST Cybersecurity Framework is a popular choice among businesses of all sizes.
CIS Controls
For a more specific set of actions, the Center for Internet Security Controls (CIS Controls) provides a prioritized set of practices that mitigate the most common cyber attacks. These controls are regularly updated to adapt to evolving threats and are often used in conjunction with the NIST framework for a comprehensive cybersecurity strategy.
ISO/IEC 27001
If international standards are what you’re after, look no further than the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) standard 27001. ISO/IEC 27001 provides requirements for an information security management system (ISMS), helping organizations secure their information assets.
HIPAA
For businesses in the healthcare sector, compliance with the Health Insurance Portability and Accountability Act (HIPAA) is non-negotiable. HIPAA provides standards for protecting sensitive patient data, ensuring that entities take necessary administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of electronic protected health information.
PCI-DSS
Does your business handle credit card transactions? If so, the Payment Card Industry Data Security Standard (PCI-DSS) is your go-to standard. PCI-DSS provides an actionable framework for developing a robust payment card data security process, including prevention, detection, and appropriate reaction to security incidents.
GDPR
Last but not least, if your business operates within the European Union or handles data of EU citizens, compliance with the General Data Protection Regulation (GDPR) is a must. GDPR provides guidelines for the collection, processing, and protection of personal data of EU citizens.
In conclusion, these standards provide a solid foundation for your cybersecurity strategy. However, adherence to these standards alone does not guarantee immunity from all cyber threats. That’s why working with a cybersecurity-focused managed services provider like Upper Echelon Technology Group LLC is so beneficial. We can help you navigate these standards and implement a customized cybersecurity strategy that aligns with your specific business needs and objectives.
Managing Cyber Risks with Upper Echelon Technology Group LLC
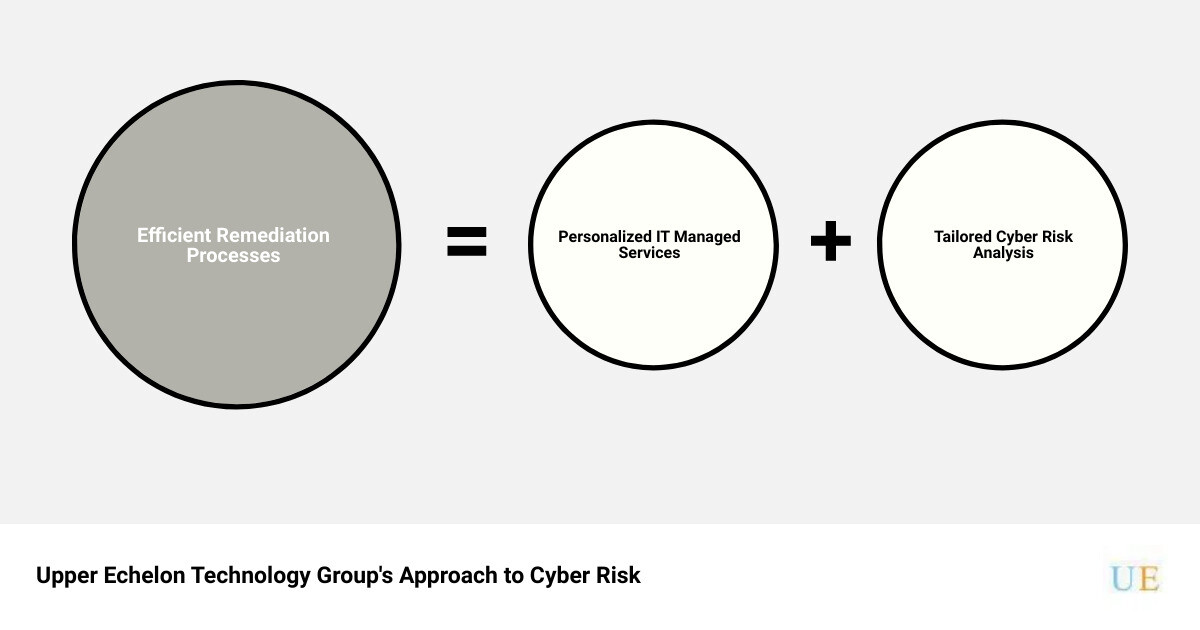
In the digital world where threats continually evolve, strategic cyber risk management is not a luxury but a necessity. Upper Echelon Technology Group LLC is your reliable partner in navigating the complex landscape of cybersecurity, offering personalized IT managed services, a tailored approach to cyber risk analysis, and efficient remediation processes.
Personalized IT Managed Services
Upper Echelon Technology Group LLC is not your typical managed services provider. We believe that every business is unique, and so are its cybersecurity needs. Our team is committed to resolving your technology issues and leveraging your technology assets to improve efficiency and profitability. By constantly evaluating the services and products we offer, we ensure that your network is protected and optimized 24/7, 365 days a year. This way, your technology serves your business instead of the other way round.
Tailored Approach to Cyber Risk Analysis
At Upper Echelon Technology Group LLC, we recognize the importance of comprehensive cyber risk analysis. We take a methodical approach to identifying, assessing, and prioritizing risks, documenting them in a risk register, and implementing appropriate mitigation strategies. We believe in the value of ongoing risk assessment and monitoring, using security scores to evaluate the effectiveness of risk management processes. A drop in security scores could indicate new risks that need to be addressed. Our goal is to help you take proactive measures to prevent cyber threats before they impact your business.
Efficient Remediation Processes
Our commitment to your business security doesn’t stop at identifying risks. We also manage the remediation process for all discovered risks, ensuring vulnerabilities are addressed before they’re exploited by cyber attackers. Through our partnership with UpGuard, we offer features such as risk mitigation workflows, security risk management, and potential threat discovery to enhance your cybersecurity program. Our trusted security rating methodology and step-by-step guidance on securing sensitive information for third-party risk management frameworks ensure your business is not just compliant but also secure.
In a world where cyber threats are an everyday reality, Upper Echelon Technology Group LLC stands as a beacon of security, offering comprehensive and personalized IT managed services. Don’t let your business become another cyberattack statistic. Partner with us, and let our team of experts guide you towards a safer, more secure digital future.
Conclusion: The Importance of Regular Cyber Risk Analysis
In the ever-changing landscape of digital threats, conducting regular cybersecurity risk assessments is not just important—it’s essential. Understanding and managing cyber risks is a continuous process that needs to evolve with the changing threat landscape. As a business owner, you need to keep in mind that a single cybersecurity risk assessment isn’t a panacea, but a starting point in your journey towards securing your digital assets.
The importance of regular cyber risk analysis can’t be overstated. It helps in identifying new threats, vulnerabilities, and potential impacts on your business. This information is paramount in ensuring that your business operations remain smooth and uninterrupted, even in the face of potential cyber threats.
Regular assessments allow you to have a real-time understanding of your cyber risk posture, enabling you to respond effectively to threats and vulnerabilities. With this information, you can prioritize resources, develop effective mitigation strategies, and ensure that your cybersecurity measures align with the evolving threat landscape.
But as we all know, cybersecurity isn’t a one-size-fits-all solution. That’s where Upper Echelon Technology Group LLC steps in. We take a personalized approach to IT managed services, tailoring our cyber risk analysis to align with your specific business needs and objectives. We don’t just fix tech issues; we help you leverage your technology assets in the most efficient way possible, turning potential threats into opportunities for growth.
We understand that each business is unique, with its own set of risks and vulnerabilities. That’s why we offer a tailored approach to cyber risk analysis, focusing on your specific business needs and how you can best leverage your technology assets. Our efficient remediation processes ensure that potential threats are quickly identified and mitigated, minimizing disruption to your business operations.
In conclusion, while cyber threats may be an everyday reality, with the right partner, they don’t have to be a cause for constant concern. Regular cyber risk analysis, coupled with personalized IT managed services from Upper Echelon Technology Group LLC, can help your business navigate the complex world of cybersecurity, empowering you to focus on what you do best—growing your business.
Remember, cyber threats are inevitable, but a cyber attack is not. Make regular cyber risk analysis a part of your business strategy today, and take a proactive approach towards securing your digital future.