In the ever-evolving digital landscape, businesses are constantly exposed to a myriad of cyber threats. These threats can disrupt operations, damage reputation, and cause considerable financial loss. As a small to medium-sized business owner in Wilmington, DE, you understand the importance of having robust cybersecurity measures in place. However, cybersecurity is not a one-size-fits-all solution. It requires a customized approach that aligns with your unique business needs and objectives. That’s where a Cyber Program Assessment comes in. This article, ‘Unveiling the Secrets: Mastering Cyber Program Assessment’, will guide you through the intricacies of cyber program assessments and demonstrate how they can be leveraged to protect your business from the ever-present cyber threats.
Cyber program assessments are a crucial part of a comprehensive cybersecurity strategy. They provide an in-depth understanding of your current security posture, highlight potential vulnerabilities, and offer strategic recommendations to fortify your defenses. By conducting regular cyber program assessments, you can stay one step ahead of cyber criminals, safeguarding your business, employees, and customers.
In the following sections, we will delve into the process of conducting a cyber program assessment, explore different types of cybersecurity assessments, and highlight how a cybersecurity-focused managed services provider like Upper Echelon Technology Group can guide you through this process. Stay tuned to unlock the secrets of mastering cyber program assessments.
Understanding Cyber Program Assessment
What is a Cyber Program Assessment?
In the ever-evolving landscape of digital threats, understanding your organization’s cyber-health is not an option but a necessity. A Cyber Program Assessment, also known as a Cybersecurity Program Assessment, is a tool that helps organizations understand their current cyber posture and identify areas of vulnerability. It offers an objective analysis of the programs and practices in place to protect the confidentiality, integrity, and availability of your information and environments.
Taking a deep dive into the world of your organization’s cybersecurity, the assessment examines the effectiveness and maturity of your internal policies and procedures. It evaluates various aspects such as your security controls, threat identification and management, risk assessment, and overall security strategy.
Why is a Cyber Program Assessment Crucial for Businesses?
Imagine sailing a ship without a compass, or running a race blindfolded. Sounds risky, right? Operating a business without having a clear understanding of its cybersecurity health is a similar gamble.
The digital world we live in is fraught with potential threats and vulnerabilities. Cyberattacks can lead to devastating consequences, including costly data breaches, damage to the company’s reputation, and even legal implications. This is where a Cyber Program Assessment becomes crucial for businesses.
A well-conducted assessment provides a clear map of your cybersecurity landscape, helping you navigate potential risks and threats. It enables you to identify gaps in your security measures and prioritize areas that need immediate attention. With a comprehensive understanding of your cyber-health, you can make informed decisions about future investments in cybersecurity.
Moreover, a Cyber Program Assessment aids in aligning your security program with industry compliance standards. This not only ensures that your organization is up-to-date with best practices but also prepares you to meet (and exceed) regulatory requirements.
In essence, a Cyber Program Assessment equips you to sail confidently in the digital sea, ensuring your business is shielded against cyber threats and positioned for growth. Embracing this tool is an investment in your organization’s future, ensuring your business continues to thrive in a digitally driven world.
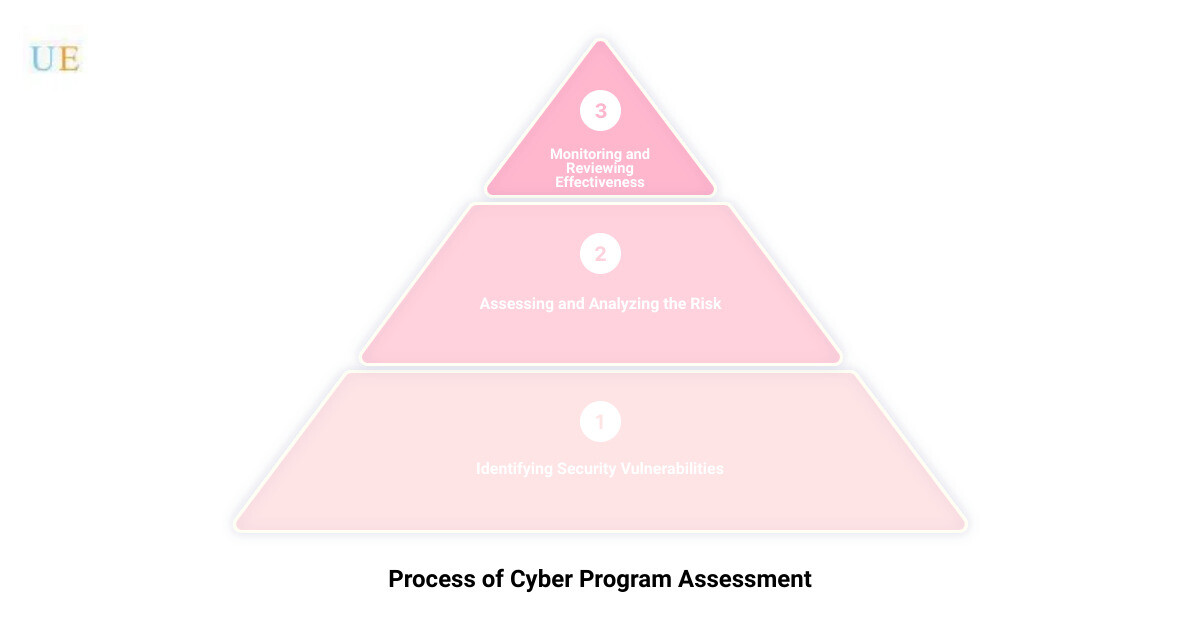
The Process of Conducting a Cyber Program Assessment
Having established the importance of a Cyber Program Assessment, let’s delve into the nuts and bolts of this critical process. A well-executed assessment provides invaluable insights into an organization’s cybersecurity posture, allowing for proactive risk management. The process is a systematic evaluation that encompasses several key steps:
Defining Cybersecurity Threats
The first step is to define the cybersecurity threats that your organization might face. This includes both internal and external threats and can range from malware attacks, phishing scams, ransomware, to insider threats. Defining these potential threats helps to establish the landscape of risk that your business operates within.
Identifying Security Vulnerabilities
Once the threats are defined, the next stage is identifying the vulnerabilities in your organization’s network, systems, and data that could be exploited by these threats. This could involve examining your IT infrastructure, software, and hardware for any potential weak spots. Regular penetration testing and vulnerability scans can be invaluable tools in this process.
Determining Threat Likelihood and Impact
The third step is to determine the likelihood of these threats materializing and the potential impact that they could have on your organization. This is often a complex process that requires a deep understanding of your organization’s operations, the value of your information assets, and the potential consequences of a successful cyber attack.
Cataloging Information Assets
Next, you need to catalog your organization’s information assets. These can include data, software, hardware, and networks. This step is essential to understand which assets are critical to your operations and which are most at risk.
Assessing and Analyzing the Risk
Now, armed with a clear understanding of the threats, vulnerabilities, and assets, you can assess and analyze the risk. This involves evaluating the potential damage that could occur if a threat exploits a vulnerability and impacts an information asset. This risk analysis forms the basis for your cybersecurity strategy.
Setting Security Controls
Once the risks are understood, the next step is to set security controls to mitigate these risks. These controls could range from implementing firewalls, encryption, and two-factor authentication, to educating staff about phishing scams. The goal is to reduce the risk to an acceptable level.
Monitoring and Reviewing Effectiveness
Finally, it’s crucial to monitor the effectiveness of your cybersecurity measures on an ongoing basis and review them regularly. Cyber threats are continually evolving, and so too should your cybersecurity strategy. Regular reviews and updates ensure your cybersecurity measures remain robust and effective.
The process of conducting a Cyber Program Assessment may seem daunting, but with the right guidance and expertise, it can be a transformative exercise for your organization. A partner like Upper Echelon Technology Group, with its personalized approach to IT Managed Services, can assist you in conducting comprehensive assessments, ensuring your business is well-protected against the ever-evolving landscape of cyber threats.
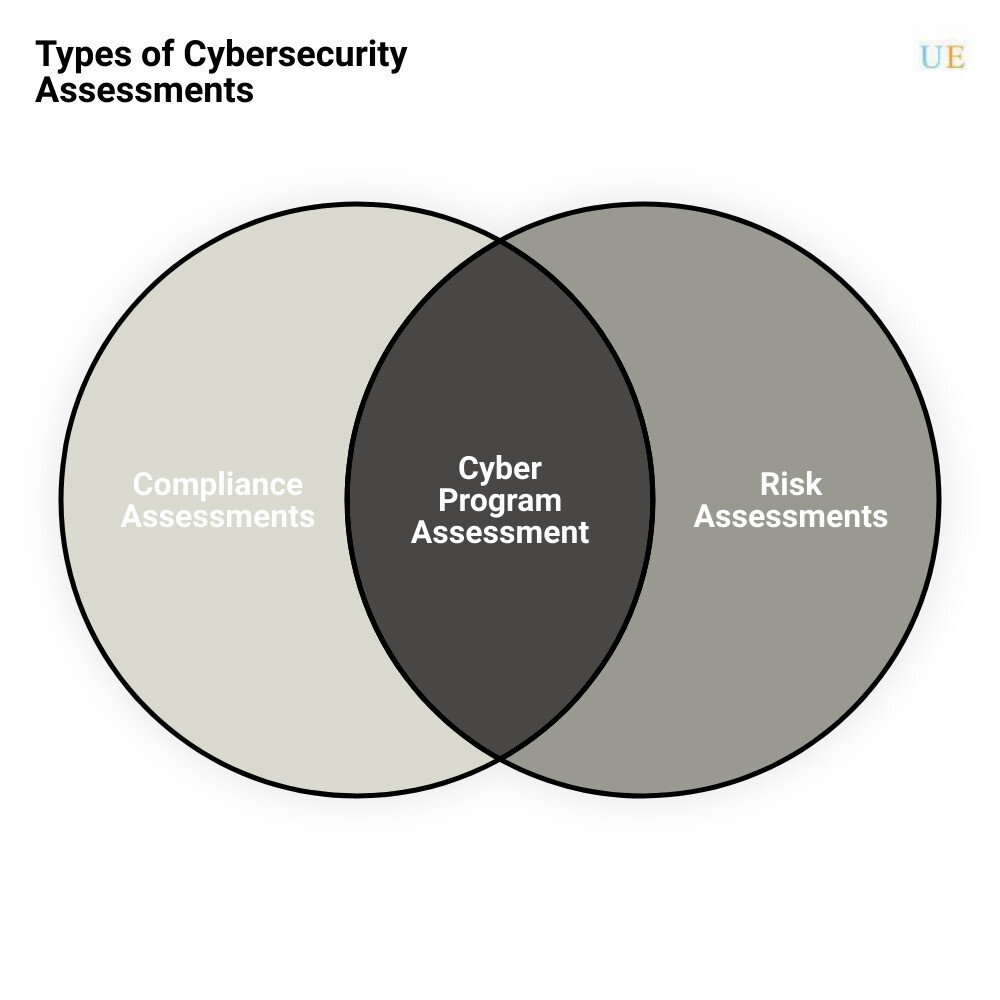
Different Types of Cybersecurity Assessments
In the realm of cybersecurity, not all assessments are created equal. There are three main categories of cybersecurity assessments that are utilized to maintain a company’s digital fort: Compliance Assessments, Risk Assessments, and Maturity Assessments. Each serves a distinct purpose and together, they form a sturdy foundation for your organization’s cyber defenses.
Compliance Assessments
When it comes to safeguarding your business and its critical data, staying in line with industry regulations and standards is paramount. Compliance assessments provide a thorough evaluation of your organization’s current state of compliance with these standards, such as the Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), or the New York Department of Financial Services Cybersecurity Regulation 23 NYCRR 500 (NYDFS). This type of assessment is crucial in avoiding costly fines and maintaining trust with your customers and partners.
Risk Assessments
With the ever-increasing sophistication of cyber threats, it’s vital to stay a step ahead. Risk assessments are designed to identify potential vulnerabilities and threats to your organization’s digital infrastructure. This process involves defining cybersecurity threats, identifying security vulnerabilities, determining threat likelihood and impact, cataloging information assets, assessing and analyzing the risk, setting security controls, and monitoring and reviewing effectiveness. By conducting regular risk assessments, you can ensure that your defenses are up-to-date and robust enough to withstand the latest cyber threats.
Maturity Assessments
Just as a fine wine matures with age, so should your cybersecurity strategy. Maturity assessments gauge how well your organization’s cybersecurity measures have developed over time and how they stand up against industry best practices. The Cybersecurity Maturity Assessment from Upper Echelon Technology Group, for example, leverages recognized cyber-frameworks like the NIST Cybersecurity Framework (NIST CSF), ISO/IEC 27001:2013 (ISO 27001), and the Center for Internet Security (CIS) Top 18 Critical Security Controls to provide a comprehensive view of your current security posture. This helps your organization develop strategic plans for further maturation and strengthening of your security program, thereby ensuring your defenses remain resilient against evolving cyber threats.
In conclusion, regular cybersecurity assessments are not just a box to be checked off but a crucial aspect of your business strategy. By leveraging compliance, risk, and maturity assessments, you can ensure your organization maintains a robust, up-to-date, and compliant cybersecurity posture. As a business owner in Wilmington, DE, you can trust Upper Echelon Technology Group to provide personalized and effective cybersecurity-focused managed services, tailored to your unique needs and goals.
Upper Echelon Technology Group’s Approach to Cyber Program Assessment
Navigating the cyber landscape can be challenging, but with the Upper Echelon Technology Group, the daunting task of mastering cyber program assessment is made manageable and efficient. Our approach is centered on three core aspects: personalized IT managed services, tailored cybersecurity solutions, and aligning security programs with industry compliance standards.
Personalized IT Managed Services
In the vast ocean of tech issues, it’s easy to get lost. The Upper Echelon Technology Group understands that each business has unique needs and goals, which is why we adopt a personalized approach to IT managed services. We don’t just fix your tech issues; we provide solutions that resolve your technology obstacles, allowing you to focus on your business. Our aim is to make your team more efficient and your company more profitable by leveraging technology to its full potential.
Tailored Cybersecurity Solutions
Cybersecurity is not a one-size-fits-all solution. At Upper Echelon Technology Group, we believe in customizing cybersecurity solutions to match your unique business needs. Our cybersecurity program assessment helps in identifying areas where technology can improve your bottom line. We evaluate the services and products that we offer to our clients regularly to ensure that your network is protected and optimized 24x7x365. This ensures that your technology serves your business, rather than you serving your technology.
Aligning Security Program with Industry Compliance Standards
Compliance with industry standards is not just about ticking boxes; it’s about ensuring your business’s continued survival in a rapidly evolving cyber landscape. Upper Echelon Technology Group ensures your cybersecurity program is aligned with industry compliance standards. We use our business-driven approach and Cyber Program Accelerator (CPA) to align findings and observations with industry standards and frameworks. This way, we ensure your cybersecurity posture is equipped to meet evolving cyber threats and inform future investments.
In conclusion, Upper Echelon Technology Group’s approach to cyber program assessment is designed to provide a comprehensive, personalized, and effective solution to your cybersecurity needs. With us, you’re not just getting a service provider; you’re getting a partner dedicated to ensuring your business’s cyber resilience.

Case Study: Successful Cyber Program Assessment with Upper Echelon Technology Group
Embarking on a cyber program assessment can feel like a daunting task. However, when done right, it can yield transformative results. Let’s dive into a real-life case study where Upper Echelon Technology Group’s expertise paved the way for remarkable improvements in a client’s cybersecurity posture.
Client Background
Our client, a mid-sized business in Wilmington, DE was experiencing a series of cybersecurity challenges. Despite having basic security measures in place, they faced persistent issues, primarily due to the lack of a comprehensive cybersecurity strategy. Their existing setup was unable to keep up with the evolving cyber threat landscape, leading to frequent system vulnerabilities and inefficiencies. The client realized the need for a robust cyber program assessment to identify their cybersecurity gaps and align their defenses with industry standards.
Assessment Process
Upper Echelon Technology Group undertook a thorough cybersecurity program assessment, which began by defining the current and potential cybersecurity threats faced by the client. Our team identified security vulnerabilities by conducting a detailed analysis of the client’s IT infrastructure. We evaluated the likelihood and potential impact of threats, cataloged information assets, and assessed the overall risk.
Next, we set up appropriate security controls tailored to the client’s specific needs – bearing in mind their business goals, industry compliance requirements, and unique operational landscape. Our approach was not just to “fix tech issues”, but to create a holistic cybersecurity strategy that would serve as an enabler for the client’s business.
Results and Improvements
Post-assessment, the client witnessed significant improvements in their cybersecurity posture. The comprehensive risk assessment helped them understand their cybersecurity weaknesses and invest in the right security controls. The customized strategy developed by Upper Echelon Technology Group ensured that their technology assets were leveraged in the best way possible, enhancing efficiency and bolstering their bottom line.
Furthermore, the client was not left to navigate these changes alone. Upper Echelon Technology Group provided ongoing support, consistently reviewing the effectiveness of the security controls and making necessary adjustments to keep up with evolving threats.
This case study underscores the value of a personalized, business-oriented approach to cyber program assessment. A well-conducted assessment, like the one offered by Upper Echelon Technology Group, can transform your cybersecurity setup from a vulnerability into a powerful tool for business growth.
Conclusion: The Value of Regular Cyber Program Assessments
In the ever-evolving world of cybersecurity, the importance of regular cyber program assessments cannot be overstated. It’s the proverbial flashlight in the dark, illuminating the path to a robust and secure digital landscape for your business.
Just as a car requires periodic maintenance to ensure its optimal performance, so does your cybersecurity program. Regular assessments don’t just fix what’s broken; they proactively identify potential vulnerabilities and provide strategic insights to fortify your defenses, keeping your business one step ahead of the cyber threats.
Moreover, regular cyber program assessments help align your cybersecurity efforts with the dynamic nature of your business. As your business grows and changes, so do its cybersecurity needs. Regular assessments ensure that your cyber defenses evolve in tandem with your business, maintaining a seamless alignment between your security infrastructure and business goals.
Another key benefit of regular assessments is compliance. With a myriad of industry standards and regulatory frameworks to adhere to, staying compliant can be a daunting task. Regular cyber program assessments from a trusted provider like Upper Echelon Technology Group can simplify this process, ensuring your cybersecurity program aligns with the best practices outlined in various industry compliance standards.
Lastly, regular cyber program assessments can significantly contribute to your company’s bottom line. They not only prevent costly security breaches but also optimize your IT resources, making your team more efficient and your company more profitable.
The journey to cybersecurity excellence is a continuous one, and regular cyber program assessments are the compass that keeps you on the right path. It’s not just about having a cybersecurity program; it’s about continually refining it to better protect your business.
In conclusion, the value of regular cyber program assessments lies in their ability to provide a comprehensive, accurate, and up-to-date picture of your cybersecurity posture. They are an indispensable tool in your cybersecurity arsenal, helping you navigate through the complex digital landscapes, and empowering your business to thrive in a cyber-secure environment.










