In the dynamic, fast-paced world of technology, the first line of defense against cyber threats is understanding them. This is where cyber assessments come into play. Cyber assessments, or cybersecurity risk assessments, play a significant role in securing an organization’s information assets and protecting its operations from potential threats. They provide an understanding of the cyber risks to operations, such as mission-critical services, functions, reputation, and image.
Cyber assessments are a crucial part of the risk management strategy for any business, especially for small to medium-sized businesses like yours in Wilmington, DE. As a business owner, you are not only responsible for your company’s physical assets but also its digital ones. These digital assets, such as customer data, proprietary software, and intellectual property, can be targeted by cyber threats. Ignorance is no longer bliss in this digital age; it is a potential business killer.
In this article, we will delve into the nitty-gritty of cyber assessments, from understanding their importance, how to conduct them, to the different types of assessments available. Furthermore, we will shed light on the role of the Cybersecurity and Infrastructure Security Agency (CISA) in cyber assessments and how Upper Echelon Technology Group LLC can assist you in conducting effective cyber assessments.
Ready to uncover the secrets of cyber assessments and reveal your business’s hidden weaknesses? Let’s get started!
Understanding the Importance of Cyber Assessments
In the digital world where cyber threats are increasingly pervasive, cyber assessments play a pivotal role in safeguarding not only public safety organizations but also businesses of all sizes and industries. Simply put, a cyber assessment is your business’s first line of defense against potential cyber threats, serving as a robust shield that can protect your business operations, reputation, and bottom line.
The Role of Cyber Assessments in Public Safety Organizations
For public safety organizations, cyber assessments are indispensable. They assist in understanding the cyber risks that could potentially disrupt their operations, impact their mission, or compromise their critical service. By conducting comprehensive cyber assessments, these organizations can pinpoint their vulnerabilities and take appropriate measures to fortify their cyber defenses. This essentially acts as a strategic roadmap for implementing robust cybersecurity practices and protocols.
The Impact of Cyber Assessments on Business Operations and Reputation
Moving beyond public safety organizations, let’s focus on businesses – more specifically, your business. Regardless of the industry, no business is immune to cyber threats. A security breach could lead to disastrous consequences, including data loss, financial loss, and a tarnished reputation. This is where cyber assessments step in, serving as a powerful tool to protect your business operations and reputation.
Through cyber assessments, you can identify the potential threats and vulnerabilities your business may face, allowing you to take proactive measures to mitigate these risks. A robust cyber assessment can help you maintain the integrity of your operations and preserve your business’s hard-earned reputation.
Moreover, with the personalized approach of Upper Echelon Technology Group LLC, you can leverage cyber assessments in the best way possible to protect your business. With us, you’re not just getting a service – you’re gaining a strategic partner dedicated to safeguarding your business from cyber threats.
In the next section, we’ll delve deeper into how to conduct a cyber risk assessment, ensuring you’re equipped with the knowledge and tools to protect your business effectively. Stay tuned!
How to Conduct a Cyber Risk Assessment
Unraveling the complexities of cybersecurity threats begins with a comprehensive cyber risk assessment. This process helps you uncover the hidden weaknesses in your system, providing a roadmap to enhance your protection measures. Let’s break down how to conduct a cyber risk assessment in eight critical steps.
Defining Cybersecurity Threats
The first step in identifying potential threats is to understand what they are. Cybersecurity threats can range from phishing attacks, ransomware, or even insider threats. Resources such as the MITRE ATT&CK Knowledge Base can provide valuable information on the latest cyber threats.
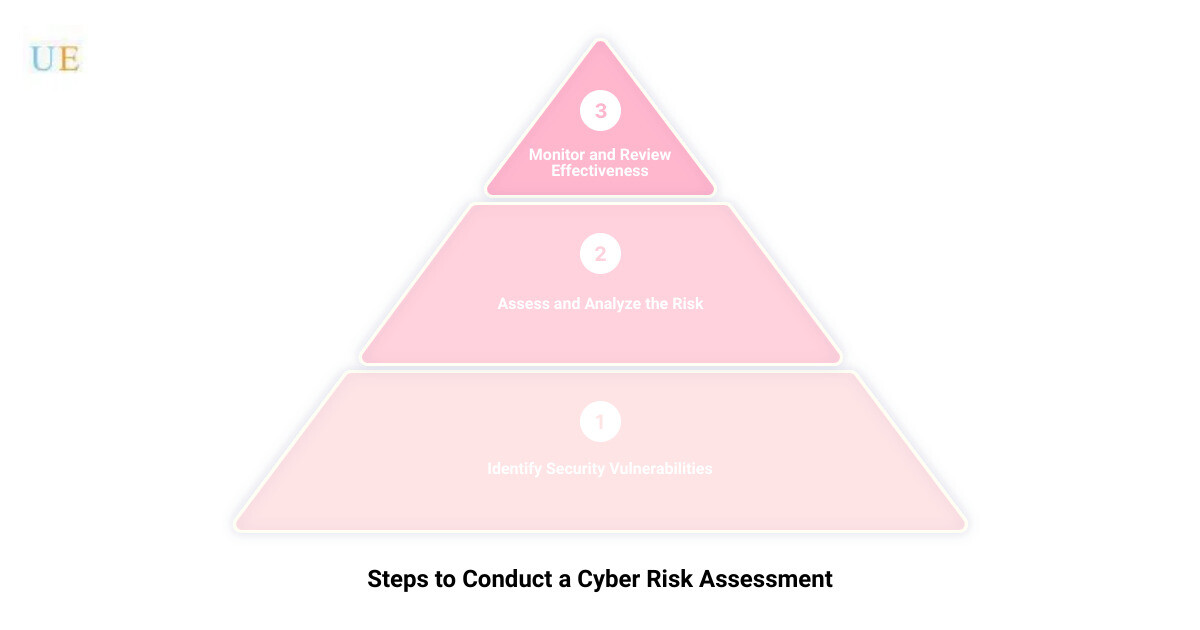
Identifying Security Vulnerabilities
Once you’ve defined potential threats, the next step is to identify the weaknesses in your system that these threats could exploit. These vulnerabilities could be outdated software, weak passwords, or even insufficient employee training.
Determining Threat Likelihood and Threat Impact
The next task is to evaluate how likely it is for the identified threats to exploit your system’s vulnerabilities and the potential impact if they do. This stage involves understanding the business impact of a successful attack on your assets.
Cataloging Information Assets
This step involves creating an inventory of all physical and logical assets within your system. This includes not only your most critical assets but also those that attackers may want to control, like an Active Directory server.
Assessing the Risk
Once you’ve cataloged your assets, the next step is to assess the risk associated with each one. This involves considering both the likelihood of a threat occurring and the potential impact on your business if it does.
Analyzing the Risk
After assessing the risk, you’ll need to analyze the results. This analysis will help you understand the overall risk landscape of your business and identify areas that need immediate attention.
Setting Security Controls
Once you’ve analyzed the risks, it’s time to set up security controls to mitigate them. These controls could range from updating software and hardware, implementing multi-factor authentication, to providing regular employee training.
Monitoring and Reviewing Effectiveness
Lastly, it’s critical to continuously monitor and review the effectiveness of your security controls. Cyber threats evolve rapidly, and your security measures need to adapt accordingly. Regular reviews will help ensure your defenses remain robust and effective.
Conducting a cyber risk assessment might seem daunting, but it’s a vital part of maintaining robust cybersecurity. Remember, the goal is not to eliminate all risks – that’s nearly impossible – but to manage them in a way that aligns with your risk tolerance and business objectives. Partnering with cybersecurity-focused managed services providers like Upper Echelon Technology Group can make this process more manageable and effective, offering a personalized approach to IT Managed Services that focuses on your unique business needs.
Different Types of Cybersecurity Assessments
In the ever-evolving landscape of cyber threats, ensuring your business is well-protected is no small task. However, breaking down the process into three main types of cybersecurity assessments can help provide a systematic and comprehensive way to identify and mitigate risks. These are Compliance Assessments, Risk Assessments, and Maturity Assessments.
Compliance Assessments
Compliance assessments are an essential aspect of a robust cybersecurity strategy. These assessments focus on ensuring that your organization is adhering to the necessary regulatory and industry standards for data protection and cybersecurity, such as ISO/IEC 27001 or NIST Special Publication 800‑53. They help to avoid legal and financial penalties that might result from non-compliance while also promoting best practices for data security and privacy.
Risk Assessments
Risk assessments, as discussed earlier, analyze the potential cyber threats your business may face, identify security vulnerabilities, and determine the likelihood and potential impact of these threats. This type of assessment is at the heart of a proactive cybersecurity strategy, enabling you to predict and prepare for potential security incidents before they occur. Some of the steps involved in a risk assessment include cataloging information assets, assessing the risk, analyzing the risk, setting security controls, and monitoring and reviewing their effectiveness.
Maturity Assessments
Maturity assessments provide a higher-level view of your organization’s cybersecurity posture. They evaluate your organization’s ability to prevent, detect, and respond to cyber threats over time. A maturity assessment can help you understand where your organization stands in terms of cybersecurity readiness and resilience, and identify areas for improvement.
Each of these assessment types plays a crucial role in an effective cybersecurity strategy. By understanding and implementing these assessments, you can ensure your organization is well-prepared to face the ever-evolving threat of cyber attacks. Partnering with a cybersecurity-focused managed services provider like Upper Echelon Technology Group can further enhance these efforts, providing personalized and comprehensive solutions to protect your business and boost your cyber resilience.
The Role of CISA in Cyber Assessments
In the realm of cybersecurity, the Cybersecurity and Infrastructure Security Agency (CISA) plays a pivotal role. This U.S. government agency conducts risk and vulnerability assessments (RVA) to identify potential security weaknesses within organizations. These assessments aren’t exclusive to federal agencies; private organizations, as well as state, local, tribal, and territorial governments, can also request these services.
Understanding CISA’s Cybersecurity Assessments
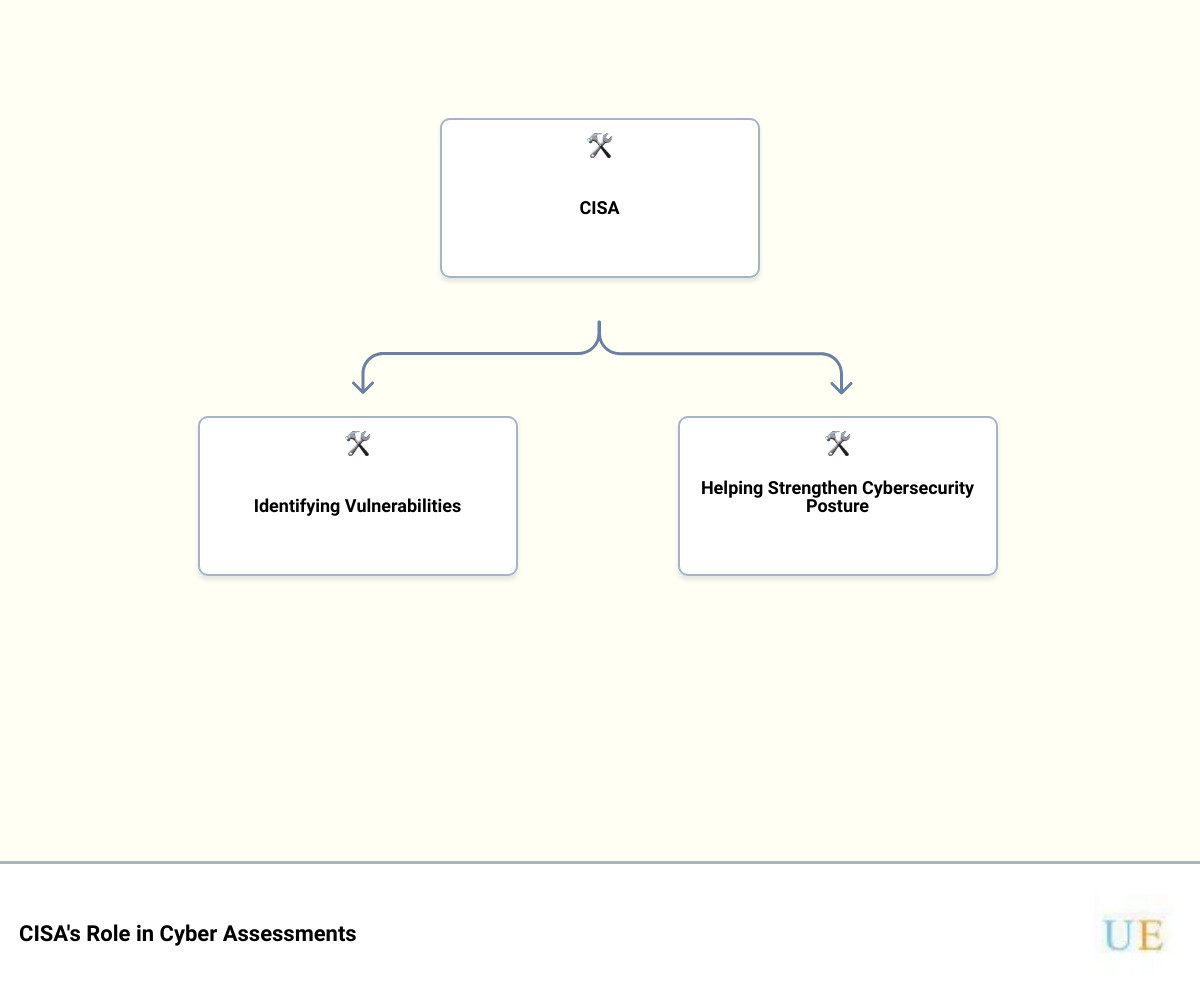
CISA’s cybersecurity assessments are not just about identifying vulnerabilities. They also highlight the areas in which an organization can enhance its cybersecurity practices. By conducting these assessments, CISA provides a holistic review of your cybersecurity posture, and offers valuable insights on how to fortify it.
How CISA Identifies Vulnerabilities
CISA identifies vulnerabilities by conducting a rigorous RVA. This assessment scrutinizes the various aspects of an organization’s cybersecurity, from its security controls to potential areas that adversaries could exploit. Upon completion of the assessment, CISA provides the organization with the data, a tailored risk analysis, and recommendations on how to bolster their cybersecurity.
The Use of the MITRE ATT&CK Framework in CISA Assessments
One of the key tools that CISA uses in its cyber assessments is the MITRE ATT&CK® framework. This globally recognized framework comprises known tactics, techniques, and procedures (TTPs) of threat actors. CISA maps the attack path to this framework, providing a comprehensive overview of how a cyber threat actor could exploit an organization’s weaknesses.
How CISA Helps Organizations Strengthen Their Cybersecurity Posture
CISA’s role doesn’t stop at identifying vulnerabilities and potential attack paths. After the assessment, the agency provides organizations with detailed reports and infographics, outlining the most successful techniques for each documented tactic. These resources, coupled with recommended defensive strategies, empower organizations to strengthen their cybersecurity posture significantly.
In conclusion, CISA plays an instrumental role in cyber assessments, providing invaluable insights that can help organizations like yours safeguard against cyber threats. By understanding and leveraging these assessments, you can further solidify your organization’s cybersecurity and ensure the smooth operation of your business. As an added measure, consider partnering with a cybersecurity-focused managed services provider like Upper Echelon Technology Group to receive a personalized approach to IT Managed Services and further bolster your cyber resilience.
The Process and Benefits of Cyber Risk Assessments
In the digital realm, the unseen can often prove the most dangerous. One of the most effective ways to unveil these hidden threats is through a cyber risk assessment. This critical process not only uncovers vulnerabilities but also empowers your organization to act proactively and decisively in safeguarding your digital assets.
Understanding Cyber Risk
In the simplest terms, cyber risk represents the potential negative disruptions to your sensitive data, business operations, or finances online. It’s crucial to remember that cyber risks are not synonymous with vulnerabilities. While vulnerabilities denote system weaknesses that can be exploited, cyber risks refer to the probability of such exploitation taking place.
For instance, cyber threats like ransomware, data leaks, phishing, and insider threats can all contribute to your overall cyber risk. The more the threats and vulnerabilities, the higher the cyber risk your organization faces.
The Process of Performing a Cyber Risk Assessment
A cyber risk assessment is akin to a comprehensive health check-up for your organization’s cybersecurity posture. It answers essential questions such as the types of data breaches that could significantly impact your business, the potential level of each threat’s impact, and the internal and external vulnerabilities that exist.
The assessment process typically involves steps like:
-
Defining Cybersecurity Threats: Understand the diverse range of cyber threats that can potentially affect your organization.
-
Identifying Security Vulnerabilities: Analyze your IT infrastructure to uncover any weak spots that could be exploited.
-
Determining Threat Likelihood and Threat Impact: Evaluate the probability of a threat occurrence and the potential impact it could have on your organization.
-
Cataloging Information Assets: Identify the information assets that, if compromised, could severely impact your operations.
-
Assessing the Risk: Calculate the risk based on threat likelihood, impact, and the value of the information.
-
Analyzing the Risk: Understand the nature of the risk, its causes, and possible outcomes.
-
Setting Security Controls: Implement measures to mitigate the identified risks.
-
Monitoring and Reviewing Effectiveness: Regularly review and update the security measures to ensure their effectiveness.
The Benefits of Cyber Risk Assessments in Risk Management Strategy and Data Protection
Conducting a cyber risk assessment offers numerous benefits to your organization’s risk management strategy and data protection efforts. It provides valuable insights into your organization’s risk landscape, helping you make informed security decisions. It allows you to prioritize your resources effectively, focusing on the areas posing the highest risk.
Moreover, it helps you comply with industry regulations, safeguarding your organization’s reputation and avoiding hefty fines. Finally, a robust cyber risk assessment can also enhance your organization’s profitability by minimizing losses due to cyber incidents.
Through a cybersecurity-focused managed services provider like Upper Echelon Technology Group, your organization can benefit from a personalized approach to these assessments, ensuring that your unique business needs and technology assets are always at the forefront.
The Role of Upper Echelon Technology Group LLC in Cyber Assessments
In the ever-present battle against cyber threats, having a steadfast partner can be a game-changer. Upper Echelon Technology Group LLC steps into this role, providing a cyber shield for your business.
Personalized IT Managed Services for Cybersecurity
Upper Echelon Technology Group is no ordinary managed services provider. We are a cybersecurity-focused managed services provider that understands the unique challenges faced by small to medium-sized businesses. Our team of experts is always on hand to solve your technology issues, allowing you to focus on what matters most – your business.
We’re not just about fixing tech issues; we offer a holistic approach to IT management, designed to make your team more efficient by leveraging technology. Our services are backed by a firm belief in the value of personal relationships and a relentless pursuit of personal growth. Our core values reflect our commitment to doing the right thing, even when no one is looking, and being of service to make a positive impact in the world.
Tailored Approach to Cyber Assessments
Cyber assessments are a critical component of any robust cybersecurity strategy. But at Upper Echelon Technology Group, we believe in a customized approach that fits your business like a glove. We understand that every organization has its unique needs and vulnerabilities, and we tailor our assessments to reflect this.
We start by identifying your information assets and determining the likelihood and impact of potential threats. This enables us to develop a comprehensive catalog of your assets and the risks associated with them. We then assess and analyze these risks, setting appropriate security controls to mitigate them.
But our job doesn’t end with setting controls. We constantly monitor these controls’ effectiveness, ensuring they continue to protect your organization as threats evolve. This continual review process allows us to adapt and respond quickly to new threats, keeping your business safe in an ever-changing cyber landscape.
In conclusion, the role of Upper Echelon Technology Group in cyber assessments goes beyond mere compliance. It’s about creating a safer, more secure digital environment where your business can thrive. It’s about revealing the hidden weaknesses in your cybersecurity, unlocking the secrets of cyber assessments, and using this knowledge to fortify your defenses. Because in the world of cybersecurity, knowledge is power. And with Upper Echelon Technology Group, that power is in your hands.
Conclusion: The Power of Cyber Assessments in Revealing Hidden Weaknesses
In the vast and ever-evolving digital landscape, performing regular cyber assessments is not just a good practice, but a necessity. It is akin to having a secret weapon in your arsenal that can reveal hidden weaknesses, proactively identify threats, and provide data-driven insights to improve your cybersecurity strategy.
Cyber assessments are a critical part of risk management that helps businesses uncover the chinks in their armor. They provide a comprehensive view of your organization’s cybersecurity landscape, identifying vulnerabilities before they can be exploited. As we’ve explored throughout this article, these assessments are an invaluable tool for maintaining the integrity and security of your data and systems.
Leveraging the power of MITRE ATT&CK framework, as CISA does, can help organizations understand the adversary’s tactics and techniques, providing a blueprint to strengthen their defenses. This knowledge, when combined with a proactive and dynamic approach to cybersecurity, will empower your organization to stay one step ahead of potential threats.
However, the real power of cyber assessments lies not just in revealing your cybersecurity weaknesses but in how you respond to those findings. The true test is in the implementation of effective security controls, constant monitoring, and regular reviews. It’s about creating a culture of cybersecurity in your organization, where everyone plays a part in protecting the business.
That’s where Upper Echelon Technology Group LLC comes in. Our personalized approach to IT Managed Services, coupled with a focus on cybersecurity, allows us to not just identify and fix tech issues but to align your technology assets with your business objectives. Our goal is to make your team more efficient, and your company more profitable, by leveraging the power of technology.
In conclusion, the power of cyber assessments lies in its ability to reveal the hidden weaknesses in your cybersecurity strategy and provide actionable insights to enhance your defenses. By partnering with a cybersecurity-focused managed services provider like Upper Echelon Technology Group, you can unlock the secrets of cyber assessments and use this knowledge to safeguard your business in the digital landscape.
Remember, in the world of cybersecurity, knowledge isn’t just power—it’s protection. And with Upper Echelon Technology Group, that protection is just a call away.