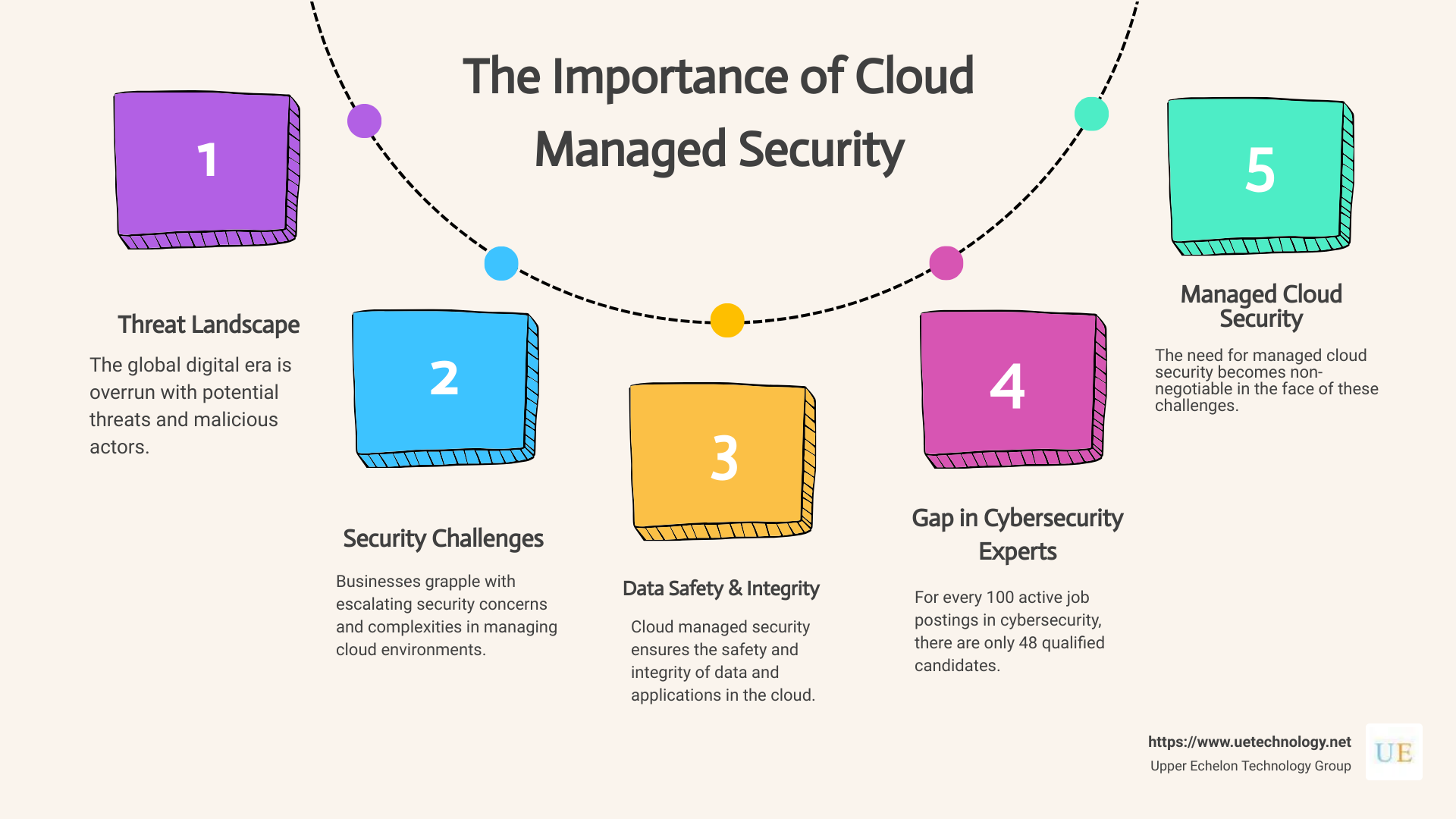
In a global digital era overrun with potential threats and malicious actors, the importance of cloud managed security cannot be overstated. At Upper Echelon Technology Group, we meet businesses every day who grapple with escalating security concerns coupled with the increasingly complex task of managing their cloud environments. As businesses shift towards virtual space, driven largely by the COVID-19 pandemic, the stakes have become higher than ever. A breach can inflict severe damage, not just financially but also to a company’s reputation.
For those unfamiliar with the landscape, cloud managed security refers to the use of services provided by managed security service providers (MSSPs) to ensure the safety and integrity of data and applications in the cloud. With these services, businesses can increasingly assess and mitigate potential security threats, enforcing stricter controls on access and bolstering privacy measures for sensitive data.
Research from eonomicmodeling.com lays bare the harsh reality facing many smaller enterprises, that for every 100 active job postings in cybersecurity, there are only 48 qualified candidates. In such a scenario, the need for managed cloud security becomes non-negotiable. To provide you with a better understanding, we invite you to explore this infographic illustrating the importance of cloud managed security:
Remember that initializing your systems without the requisite expertise could be a costly error, as the global increase in online business has only incentivized attackers to probe for weaknesses in companies’ cloud infrastructure. According to Accurics’ Summer 2020 report, misconfiguration in cloud storage services were commonplace in a staggering 93% of analyzed cloud deployments.
As a company that values relationships and believes that people come first, we strive to provide solutions that effectively neutralize these issues. We believe in open and honest communication and relentless pursuit of personal growth and this dedication resonates in our philosophy of managed services, helping businesses operate smoothly 24x7x365. It’s not just about solving tech issues, but about helping our clients leverage technology to focus better on their business needs. So, whether you are a seasoned expert or new to the world of cloud managed security, join us as we navigate through this ultimate guide to unveil the power of secure cloud computing.
Understanding Cloud Managed Security
In the world of digital data, where businesses are increasingly turning to the cloud for storage and operations, understanding cloud managed security is essential. Let’s delve into what this means and why it matters to your business.
What is Managed Cloud Security?
Managed cloud security is a subscription service that aims to secure your business’s data and applications in the cloud. This service is often provided by Managed Security Service Providers (MSSPs) like Upper Echelon Technology Group, who constantly evaluates services and products to ensure that your network is protected and optimized 24/7. This way, your technology serves your business instead of you serving your technology.
What is Cloud Security Management?
Cloud security management, on the other hand, is a set of strategies designed to allow a business to use cloud applications and networks to their greatest potential while limiting potential threats and vulnerabilities. This is often achieved by identifying and assessing cloud services, implementing the right security measures, and maintaining continuous monitoring to detect and respond to any security incidents promptly.
The Three Categories of Cloud Security: IaaS, PaaS, and SaaS
When we talk about cloud security, it’s important to understand that it’s not a one-size-fits-all concept. There are three categories of cloud computing: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), each with their unique security considerations and requirements.
IaaS offers the highest level of flexibility and management control over your IT resources. PaaS provides a platform allowing customers to develop, run, and manage applications without the complexity of building and maintaining the infrastructure. SaaS, the most common category, allows users to connect to and use cloud-based apps over the internet, like Microsoft 365.
What is a Cloud-Based Security System?
A cloud-based security system is a discipline of cybersecurity dedicated to securing cloud computing systems. This includes keeping data private and safe across online-based infrastructure, applications, and platforms. The ultimate goal is to provide a secure cloud environment that protects your data, supports regulatory compliance, protects customer privacy, and sets up appropriate access controls.
At Upper Echelon Technology Group, we understand how vital cloud managed security is for businesses, and we are equipped to help you navigate this complex world. Our services are designed to not just solve tech issues, but focus on how your business can leverage technology assets in the best way possible. In the next section, we will look at the role MSSPs like us play in enhancing your cloud security.
The Role of Managed Security Service Providers (MSSPs) in Cloud Security
As a business owner, you’re constantly juggling a multitude of responsibilities. Why add cloud security to that overflowing list when you can entrust it to the experts? This is where Managed Security Service Providers (MSSPs) come in. MSSPs are third-party experts who offer comprehensive security services, becoming an invaluable ally in your cloud journey.
AWS Managed Security Service Providers: Enhancing Cloud Security
One of the notable players in this space is AWS, who have crafted a unique model of MSSP Partners. These partners work closely with AWS security experts to develop offerings that operationalize security tools, skill sets, and processes. This includes leveraging native AWS security services such as AWS Security Hub, Amazon GuardDuty, AWS Solutions Implementations, and third-party tools.
As an AWS MSSP Partner, we at Upper Echelon Technology Group are committed to providing services that meet stringent quality standards, ensuring optimal protection and monitoring of essential AWS resources for your business.
The Services Provided by MSSPs: From Vulnerability Management to Digital Forensics
MSSPs offer a range of services tailored to your unique security challenges. These include vulnerability management, cloud security best practices and compliance, 24×7 threat detection and response, network security, data privacy event management, and digital forensics incident response. We ensure that your AWS accounts and deployed resources always align to security best practices. Furthermore, we scan your AWS environment for common compliance standards such as CIS AWS Foundations, PCI DSS, HIPAA, HITRUST, ISO 27001, MITRE ATT@CK, and SOC2.
The Benefits of Working with MSSPs: Operationalizing Cloud Security Tools and More
By collaborating with a MSSP like us, you can fully operationalize your security tools. We ensure full features of native AWS Security Services and third-party security tools are utilized and configured to best practices. We also offer 24/7 security protection and monitoring of essential AWS resources, enabling you to focus on innovation rather than security concerns.
Additionally, we provide full visibility into your AWS resources. This includes tracking what resources are being added, changed, or removed across your organization. We also extend visibility into your hybrid and multi-cloud environments.
In the end, the role of MSSPs in cloud security is not just about protection, it’s about empowering you and your business to thrive and innovate without the constant worry of security threats. In the next section, we will delve deeper into Deloitte’s approach to cloud security management.
Delving into Deloitte’s Cloud Security Management
When it comes to cloud security management, one name that stands out is Deloitte. With its robust and comprehensive solution, it is paving the way for secure and efficient cloud computing.
An Overview of Deloitte’s End-to-End, Enterprise-Grade Security Management Solution
Deloitte offers an enterprise-grade cloud managed services platform that combines advanced, cloud-native security technology with a team of skilled technologists, engineers, and operators. This end-to-end security management solution is designed to scale according to your business requirements.
Deloitte’s solution leverages the firm’s cyber risk framework, embedded with native services, helping businesses migrate to the cloud with increased confidence that their cyber risks are being managed. This approach to cloud security management is highly automated, using Infrastructure as Code (IaC) to deploy new production-ready solutions with supporting cybersecurity guardrails.
The Benefits of Deloitte’s Cloud Security Management: Protecting the Enterprise and Enabling Business Growth
Deloitte’s Cloud Security Management offers a myriad of benefits. It acts as a backbone for digital transformation efforts, helping businesses access capabilities and features that may not have been available with previous on-premises solutions.
Through streamlined operational processes, businesses can respond faster to high-priority security events, dampening the impact of these events, reducing business risk, and improving overall security posture. It’s not just about protection—it’s about enhancing application performance and availability, minimizing risk to the brand, and promoting operational efficiencies.
Moreover, Deloitte’s solution helps businesses achieve cost efficiencies. By utilizing cloud-native services along with consolidated enterprise licensing for analytical tools, businesses can reduce the operational and infrastructure costs of supporting applications and systems.
In terms of governance, Deloitte’s solution ensures that the cloud environment is protected from threats seeking to exploit known vulnerabilities. Continuous detection, investigation, and remediation of vulnerabilities with auto-healing guardrails and autopatching can free up internal resources and further reduce business risks.
Lastly, with Deloitte’s Cloud Security Management, businesses can innovate faster and respond rapidly to business changes. Technology becomes a transformation enabler, facilitating rapid innovation, faster time to market, and greater agility.
In summary, Deloitte’s Cloud Security Management provides a comprehensive, end-to-end solution for managing cyber risks in the cloud. It not only protects enterprises from potential threats but also enables business growth by leveraging the power of secure cloud computing. This balance between protection and enablement is what truly sets Deloitte apart in the realm of cloud managed security.
The Risks and Challenges in Cloud Security
In the ever-evolving world of technology, protecting your business from cyber threats is a continuous battle. While cloud computing offers tremendous benefits, it also brings with it a set of unique challenges and risks that need to be managed effectively to ensure your business’s security.
Potential Risks: Downtime, DoS and DDoS Attacks, and Compliance Challenges
One of the significant risks in the cloud environment is downtime. A lack of proper security measures can result in downtime during an attack, leading to a loss of productivity. Cyber threats like Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks can lead to service disruption or complete outage.
Additionally, navigating regulatory compliance can be a daunting task. A lack of holistic cloud security measures can lead to compliance challenges, potentially resulting in sanctions if protocols aren’t correctly followed.
At Upper Echelon Technology Group, we understand these risks and have developed robust solutions to mitigate them effectively. We offer a comprehensive cloud managed security service that ensures continuous protection, minimizing the risk of downtime and service disruption.
The Importance of Compliance with Regulations like HIPAA, GDPR, and PCI-DSS
In today’s business environment, ensuring compliance with security regulations is not just critical – it’s mandatory. Regulations such as the Health Insurance Portability and Accountability Act (HIPAA), the General Data Protection Regulation (GDPR), and the Payment Card Industry Data Security Standard (PCI-DSS) provide a framework for network security.
However, staying compliant with these regulations requires expertise and up-to-date knowledge. Lack of compliance can lead to severe sanctions, damaging your business reputation and bottom line. We at Upper Echelon Technology Group have the necessary expertise and resources to ensure your business is fully compliant with these regulations.
The Role of Expertise in Cloud Security Tools, Industry Best Practices, and Cloud Adoption Frameworks
Managing cloud security is not just about having the right tools; it’s about knowing how to use them effectively. Understanding how traditional security solutions operate differently in the cloud can be challenging. For instance, the cloud’s automatic scan reporting could cause alarm due to false positives.
In addition, multi-cloud environments require significant administration and development expertise. Cultivating this expertise in-house can be costly and time-consuming.
At Upper Echelon Technology Group, we have the necessary expertise in various cloud security tools, industry best practices, and cloud adoption frameworks. We offer a personalized approach to IT managed services, enabling your business to leverage technology assets in the best possible way.
In conclusion, while cloud security poses certain risks and challenges, with the right expertise and solutions, you can harness the power of the cloud while ensuring your business stays secure. Our team at Upper Echelon Technology Group is ready to help you navigate these challenges and secure your cloud assets effectively.
The Benefits of Outsourcing Cloud Security to Managed Service Providers
The cost of IT downtime due to security failures can be a financial nightmare for businesses – reaching an average of $5,600 per minute according to Gartner. Beyond the financial implications, a breach can also tarnish a company’s reputation, leading to a loss of consumer trust and confidence. This is where we at Upper Echelon Technology Group step in. As a cybersecurity-focused managed services provider, we offer tailored solutions to secure your data and applications in the cloud.
The Cost of Security Failures and the Value of Expertise
Security breaches can hurt your business financially and harm your reputation. However, with our managed IT services, we help you avoid these pitfalls by providing robust, 24x7x365 protection for your network. Our team constantly evaluates the services and products we offer to ensure that your technology serves your business, not the other way around.
The Role of Managed Cloud Service Providers in Access Controls, Real-Time Data Monitoring, and Predictive Analytics
Effective cloud security requires a range of best-practice measures. These include access controls, real-time data monitoring, and predictive analytics. We provide a comprehensive suite of managed cloud security services, including the implementation of the principle of least privilege access. This reduces the risk of cyber attackers gaining access to critical systems or sensitive data by compromising a low-level user account, device, or application.
Our real-time data monitoring (RTDM) service employs predictive analytics to identify critical points where your data may be at risk at the earliest possible moment. Our 24/7 support ensures that there’s no need for your developer team to draw straws for who gets pager duty.
The Importance of Business Continuity and Disaster Recovery Planning
A managed cloud service is a critical component of business continuity and disaster recovery (BCDR) planning. This includes recovering from security problems like data breaches and ransomware. Our managed IT services include backup procedures, data recovery (especially for mission-critical data) and guidelines for implementation, testing, and maintenance.
We also offer disaster recovery as a service (DRaaS) to regularly back up your operating systems, data, files, applications, and configurations. We also deliver uptime guarantees, providing fundamental business value and peace of mind.
Ensuring Data Privacy and Compliance with Regulations like GDPR
Data privacy is a critical component of security, and we take it seriously. We assist with identity and access management (IAM) to define and manage the roles and access privileges of individuals (both employees and applications). This ensures that users are granted (or denied) access under specific circumstances, thereby maintaining data privacy and compliance with regulations like GDPR.
In conclusion, outsourcing cloud security to a managed service provider like Upper Echelon Technology Group can help you leverage the power of secure cloud computing. We offer a personalized approach to IT Managed Services, focusing on your business needs and how you can best utilize your technology assets. We’re here to help you navigate the cybersecurity landscape, providing robust solutions that secure your data and applications in the cloud.
Conclusion: The Power of Secure Cloud Computing with Managed Security Services
In the digital age, the power of secure cloud computing is undeniable. It offers businesses the flexibility and scalability they need to grow and thrive. However, it also poses certain challenges and risks. That’s where managed cloud security services come into play, offering a robust and comprehensive solution to these potential hurdles.
At Upper Echelon Technology Group, we understand the intricacies involved in cloud security management. We offer the best of breed in managed IT services, ensuring your network is protected and optimized 24x7x365. Our team of skilled technologists, engineers, and operators leverage advanced, cloud-native security technology to provide end-to-end security management tailored to your business requirements.
We go beyond just fixing tech issues. We make your team more efficient by leveraging technology, and we strive to make your company more profitable by identifying areas where technology can improve your bottom line. Our managed services help your business operate smoothly, securing your operations, and spearheading business enablement.
Our expertise in access controls, real-time data monitoring, and predictive analytics enables us to identify critical points where your data may be at risk at the earliest possible moment. We also understand the importance of business continuity and disaster recovery planning, offering solutions that ensure your data is safe and readily recoverable in the event of a breach or disaster.
At Upper Echelon Technology Group, we also prioritize privacy as a critical component of security, ensuring data privacy and compliance with regulations like GDPR.
In conclusion, secure cloud computing, when managed correctly, can be a powerful tool for businesses. By leveraging the expertise of managed security service providers like Upper Echelon Technology Group, you can not only mitigate risks but also unlock the full potential of cloud computing to drive your business growth.
Remember, cloud security is not just about protecting your data; it’s about empowering your business. Let us help you unleash the power of secure cloud computing.
For more information about our managed cloud security services, contact us today. We would love to have a conversation with you!