Introduction: The Importance of Cybersecurity Risk Assessment for Businesses
Cybersecurity threats are the invisible enemies lurking in the shadows of your business. As a business owner in today’s digital age, one of the most important things you can do is to conduct a cybersecurity risk assessment. Unveiling your business’s cybersecurity Achilles’ heel can be the difference between thriving and facing devastating losses.
A cybersecurity risk assessment is not only about identifying potential threats but also about understanding how these threats might affect your organization and determining the best ways to mitigate risk. It’s about asking crucial questions like what are your organization’s most important information technology assets? What type of data breach could have a significant impact on your business, whether it’s from malware, cyber attack, or human error? The answers to these questions will guide you in designing a robust cybersecurity strategy that fortifies your business against cyber threats.
Performing a cybersecurity risk assessment is a critical component of your risk management strategy and data protection efforts. Without it, you’re essentially operating in the dark, unaware of the lurking dangers that could potentially cripple your business. This process helps ensure that the cybersecurity controls you choose are appropriate to the risks your organization faces. Without a risk assessment to inform your cybersecurity choices, you could waste time, effort, and resources.
In the following sections, we will delve deeper into understanding cybersecurity risks, the process of performing a cybersecurity risk assessment, and how Upper Echelon Technology Group LLC can help optimize your business’s cybersecurity strategy. Stay tuned as we unveil the ways to uncover and address your business’s cybersecurity Achilles’ heel.
Understanding Cybersecurity Risks for Businesses
In the vast digital landscape, the specter of cyber threats looms large. Various malicious elements are ready to exploit any weak link in your business’s cyber armor. To protect your business and its sensitive data, you must first understand the nature of these cyber threats.
Defining Cybersecurity Risks
In the realm of information security, a cybersecurity risk is the probability of a negative event occurring due to a cyber threat exploiting a vulnerability in your business’s information system. Cyber risks are often associated with data breaches, causing financial, reputational, or operational disruptions. The level of risk can vary from low to high, depending on the threat’s potential to exploit the system’s vulnerability and the potential damage if a breach occurs.
As businesses increasingly lean on technology for operations, the threat landscape expands, exposing your business to new critical vulnerabilities. This makes cyber risk assessment an essential part of risk management, as underlined by the National Institute of Standards and Technology (NIST)‘s Cybersecurity Framework.
Examples of Specific Cyber Threats: Ransomware, Phishing, Malware, and More
To further illustrate the concept of cyber risks, let’s look at some specific examples:
-
Ransomware: This is a type of malware that encrypts your data, holding it hostage until a ransom is paid. Businesses hit by ransomware can face massive operational disruptions, financial losses, and reputational damage.
-
Phishing: This involves fraudulent emails or messages designed to trick users into revealing sensitive information like login credentials or credit card numbers. It’s a common threat that can lead to significant data breaches.
-
Malware: This encompasses various forms of malicious software, including viruses, worms, and trojans, designed to damage, disrupt, or gain unauthorized access to your business’s systems.
-
Insider Threats: These risks come from within your organization. They could be disgruntled employees, contractors, or business associates who misuse their authorized access to your systems and data for malicious purposes.
-
Cyberattacks: These are deliberate attempts by external entities to breach the information system of a business, usually through hacking.
By understanding these threats, you can better prepare your business and reduce its cybersecurity risks. In the next section, we will discuss the process of performing a cybersecurity risk assessment, a crucial step in fortifying your business against these cyber threats.
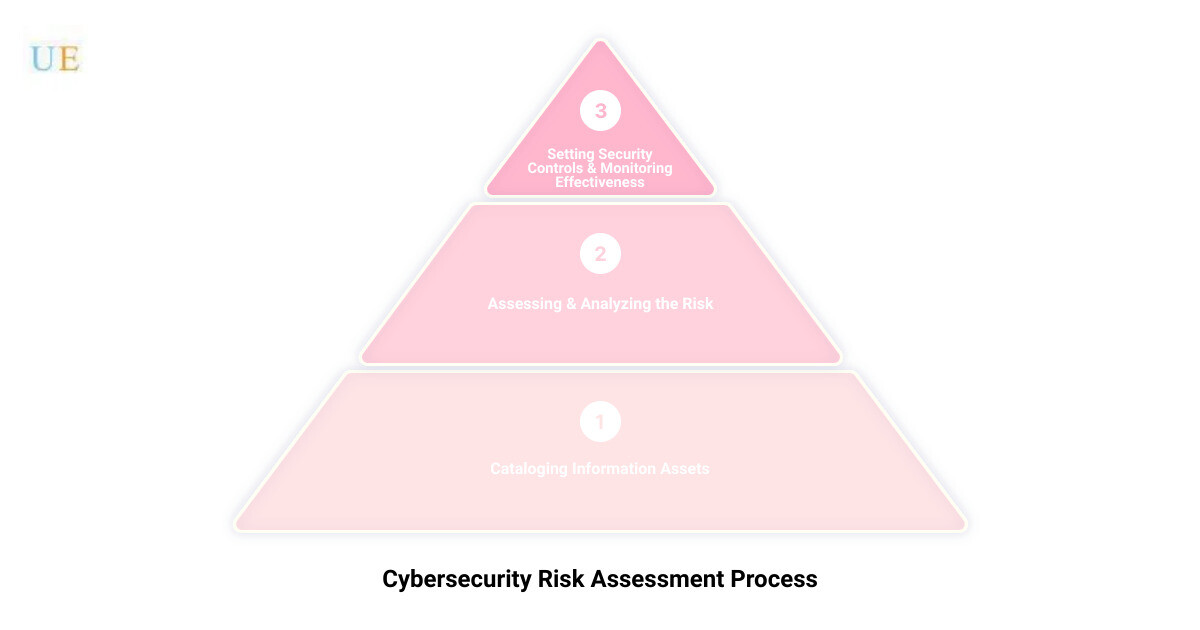
The Process of Performing a Cybersecurity Risk Assessment
A cybersecurity risk assessment is akin to a health check-up for your business’s technology ecosystem. It helps you identify weaknesses, vulnerabilities, and potential threats, offering you insights to formulate a robust defense strategy. This process involves several crucial steps, each designed to give you a comprehensive understanding of your cybersecurity health.
Cataloging Information Assets: Identifying Key Business Objectives and IT Assets
The first step towards conducting a cybersecurity risk assessment is understanding what you need to protect. This process involves identifying your key business objectives and associated IT assets. It’s essential to catalogue all physical and logical assets within the scope of the risk assessment. This includes not only the ‘crown jewels’ of your organization, such as customer data and intellectual property, but also systems and hardware that could be exploited by attackers, such as an Active Directory server.
Assessing the Risk: Identifying Cyber Threats and Vulnerabilities
Once you’ve identified what needs protection, the next step is to understand the threats that could harm these assets. These threats encompass the tactics, techniques, and methods utilized by cyber attackers. You can identify potential threats using resources like the MITRE ATT&CK Knowledge Base or advisories from agencies like the Cybersecurity & Infrastructure Security Agency. It’s also important to consider where each asset sits in the Lockheed Martin cyber kill chain, which maps out the stages and objectives of a typical real-world attack.
Analyzing the Risk: Calculating the Likelihood and Impact of Various Scenarios
After identifying the threats, it’s time to analyze the risk they pose. This involves calculating the likelihood of a successful attack and its potential impact on your business. The risk is usually estimated based on factors such as the potential damage to your business and the probability of a cyber attack. This analysis helps prioritize risk mitigation efforts.
Setting Security Controls: Implementing Mitigation Strategies
Once you’ve analyzed the risks, the next step is to define and implement appropriate controls to mitigate them. These controls can range from technical measures such as encryption and firewalls to administrative controls like access management and training programs. The selected controls should align with the identified risks and help treat them effectively.
Monitoring and Reviewing Effectiveness: Regularly Updating the Risk Assessment
Cybersecurity is not a one-time task but a continuous process. To keep your cybersecurity framework robust and up-to-date, it’s critical to monitor and review the risk environment regularly. Changes in the business context, technology, or threat landscape might necessitate an update in your risk assessment. Therefore, maintaining an overview of the complete risk management process is essential for effective cybersecurity management.
In the next section, we will explore how a cybersecurity risk assessment is an integral part of a risk management strategy and plays a crucial role in data protection.
The Role of Cybersecurity Risk Assessment in Risk Management Strategy and Data Protection
A well-executed cybersecurity risk assessment isn’t a one-off task, but a cornerstone of an effective risk management strategy and data protection plan. It provides the insights needed to prioritize cybersecurity risks and guide decisions on resource allocation, investment, and security control implementation.
Prioritizing Risks and Documenting Results in a Risk Assessment Report
One of the key outputs of a cybersecurity risk assessment is a risk register. This is a document that captures all identified risks, along with pertinent information such as the date of identification, current risk level, treatment plan, progress status, residual risk, and the risk owner. Regularly reviewing and updating this document ensures that your business always has an up-to-date snapshot of its cybersecurity risk landscape.
A well-maintained risk register empowers your organization to prioritize risks based on their potential impact and likelihood. This risk prioritization is crucial in making informed decisions about where to invest your cybersecurity budget, and which vulnerabilities need immediate attention. It allows you to focus on the ‘Achilles’ heel’ of your cybersecurity, the vulnerabilities that could cause the most damage.
Understanding, Controlling, and Mitigating All Forms of Cyber Risk
The cybersecurity risk assessment process helps businesses understand the full spectrum of cyber risks they face. These can range from threats to your data integrity, such as malware and ransomware, to potential disruptions to your IT infrastructure, like DDoS attacks.
Once these risks are understood, your business can take steps to control and mitigate them. This could involve strengthening your existing security controls or implementing new ones. For instance, if your assessment identifies a high risk of phishing attacks, you might decide to invest in additional email filtering tools or user awareness training.
It’s important to note that mitigation doesn’t always mean eliminating the risk entirely. Some risks may be accepted if the cost of mitigation outweighs the potential impact. What matters is that these decisions are made mindfully, with a clear understanding of the potential consequences.
In essence, a cybersecurity risk assessment enables your business to transform its approach from reactive to proactive. Instead of waiting for a cyber attack to occur and dealing with the aftermath, you can anticipate potential threats and take action to prevent them. This proactive approach not only protects your business from costly and disruptive cyber incidents but also helps build trust with customers, suppliers, investors, and other stakeholders who rely on the integrity of your digital operations.
In the next section, we’ll look at how Upper Echelon Technology Group LLC can help your business navigate the complexities of cybersecurity risk assessment and implement a robust risk management strategy.
How Upper Echelon Technology Group LLC Can Help with Your Business’s Cybersecurity Risk Assessment
Cybersecurity risk assessment is a complex task requiring specialized knowledge and expertise. But you’re not alone on this challenging journey. Upper Echelon Technology Group LLC, a cybersecurity-focused managed services provider with a unique, personalized approach to IT Managed Services, is here to provide the support you need.
Personalized IT Managed Services Tailored to Your Business’s Specific Needs
At Upper Echelon Technology Group LLC, we understand that every business is unique, with its distinct set of goals, challenges, and IT assets. That’s why we offer personalized IT Managed Services tailored to your specific needs. We constantly evaluate and optimize our offerings to ensure that your network is protected and functioning at its best 24/7/365, allowing technology to serve your business rather than the other way around. Our aim is to make your business run smoothly, freeing you to focus on what you do best – growing your business.
Beyond Fixing Tech Issues: Improving Efficiency and Profitability Through Effective Cybersecurity
But we don’t stop at merely fixing tech issues. We believe in harnessing the power of technology to drive efficiency and profitability. We strive to make your team more efficient by leveraging technology, and we aim to make your company more profitable by identifying areas where technology can enhance your bottom line.
Our cybersecurity offering not only ensures the security of your network but also helps your business identify and mitigate cybersecurity risks. This proactive approach to cybersecurity management allows you to stay one step ahead of potential threats and safeguard your business’s valuable data and IT assets.
With Upper Echelon Technology Group LLC, you’re not just getting a service provider; you’re getting a partner committed to your business’s success. We believe in building strong relationships, promoting personal growth, and maintaining open, honest, and productive communication. We work as a true team and strive to be a positive influence on your business.
In a world where cybersecurity threats are increasingly sophisticated and damaging, it’s crucial to identify and address your business’s cybersecurity Achilles’ heel. With Upper Echelon Technology Group LLC’s expert support, you can fortify your business’s defenses, optimize your technology assets, and drive growth. Let’s unveil and address your business’s cybersecurity Achilles’ heel together.
In the ever-evolving landscape of digital threats, it’s never been more critical to protect your business from cyber-attacks. Unveiling and addressing your business’s cybersecurity Achilles’ heel is not just about defending against threats – it’s about unlocking new avenues of growth, efficiency, and success.
As we’ve uncovered throughout this article, conducting a thorough cybersecurity risk assessment is paramount to illuminating the vulnerabilities that could potentially expose your business to cyber threats. From identifying key business objectives and IT assets to cataloging and assessing risks, calculating the likelihood of various risk scenarios, to setting up effective security controls, a comprehensive cybersecurity risk assessment is your business’s first line of defense.
But remember, a cybersecurity risk assessment isn’t a one-and-done task. It’s an ongoing process that requires regular monitoring and updating to remain effective. It forms a crucial component of your risk management strategy and data protection efforts, helping your business understand, control, and mitigate all forms of cyber risk.
Here at Upper Echelon Technology Group LLC, we go beyond fixing tech issues. As a cybersecurity-focused managed services provider, we offer a personalized approach to IT managed services. Our goal is to solve your technology issues, improve efficiency, and boost profitability through effective cybersecurity.
Our team is equipped with the knowledge and tools to help perform a detailed cybersecurity risk assessment for your business, identifying areas of vulnerability, and implementing mitigation strategies tailored to your specific needs. We consider your unique business objectives and the specific threats and vulnerabilities that could impact your operations.
With our help, you can move from a mindset of “if I get impacted” to “what are my chances of success when I get impacted.” We work to ensure that your business is not just protected from cyber threats, but also primed for growth and success.
In conclusion, unveiling and addressing your business’s cybersecurity Achilles’ heel is a critical step towards securing your digital landscape and unlocking the full potential of your technology assets. With Upper Echelon Technology Group LLC by your side, you can navigate the complexities of cybersecurity with confidence, knowing that your business is protected, efficient, and ready to thrive in the digital age.