Introduction: The Importance of Cybersecurity Assessment for Businesses
In the digital age where businesses operate in an interconnected virtual landscape, the importance of a robust cybersecurity assessment cannot be overstated. The reality is that no business, irrespective of its size or industry, is immune to cyber threats. There is an alarming rise in cyberattacks targeting small to medium-sized businesses, like yours, in Wilmington, DE, which often lack the resources to combat these threats effectively.
A cybersecurity assessment is akin to a health checkup for your business’s digital ecosystem, identifying potential vulnerabilities before they become costly breaches. It can be the difference between securing your business’s sensitive data and suffering a catastrophic data breach that could cripple your operations, tarnish your reputation, and lead to hefty financial losses.
The assessment process involves a comprehensive evaluation of your organization’s cybersecurity infrastructure, identifying weak points, and providing actionable recommendations to fortify your defenses. It’s not just about fixing tech issues; it’s about leveraging your technology assets in the most strategic way possible to bolster your business’s growth and profitability.
With a prominent cybersecurity-focused managed services provider like Upper Echelon Technology Group taking the helm, you can confidently navigate the complex cybersecurity landscape. We bring a personalized approach to IT Managed Services that addresses your specific business needs and pain points, enabling you to focus on what you do best—running your business.
In this article, ‘Unveiling the Hidden Weaknesses: Propel Your Business with a Game-Changing Cybersecurity Assessment!’, we delve into the nitty-gritty of business cybersecurity assessments. We’ll explore the different facets of a cybersecurity assessment, guide you through the process, and highlight the long-term benefits for your business. So, let’s get started, because in today’s world, cybersecurity isn’t an option—it’s a necessity.
Understanding Cybersecurity Assessment: What It Is and What It Includes
In the digital jungle of the modern business landscape, the cybersecurity assessment is your map, your compass, and your survival guide. It’s your ticket to understanding the vulnerabilities and threats your business faces and provides a proactive approach toward strengthening your defenses.
Defining Cybersecurity Assessment
A cybersecurity assessment is a comprehensive evaluation of an organization’s information security posture. It digs deep into your organization’s defenses to identify and quantify vulnerabilities and threats, providing a clear picture of the risks you face. This evaluation includes not just your technical infrastructure, but also your policies, procedures, and people. The ultimate goal is to identify the weak points in your cybersecurity armor and provide recommendations to bolster your defenses.
Components of a Cybersecurity Assessment
A robust cybersecurity assessment includes several key components that work together to provide a holistic view of your organization’s cybersecurity standing.
-
Risk identification: The first step is to identify the potential risks your business faces. This could include everything from threats posed by unsecured Wi-Fi networks to the risk of phishing attacks targeting your employees.
-
Vulnerability assessment: This involves evaluating your existing security controls and identifying areas where they may be lacking. It’s about finding the weak spots in your defenses before a malicious actor does.
-
Impact and likelihood assessment: Not all risks are created equal. This component involves determining the potential impact of each identified risk and the likelihood of it occurring.
-
Risk prioritization: Based on the impact and likelihood assessment, risks are then prioritized. This helps organizations focus their resources where they are most needed.
-
Recommendation for risk treatment: Finally, the cybersecurity assessment should include recommendations for mitigating the identified risks. This could include a range of solutions, from technical fixes to employee training programs.
Remember, a cybersecurity assessment isn’t a one-and-done exercise. It’s an ongoing process that should be part of your organization’s regular operations, helping you stay ahead of emerging threats and ensure your defenses remain strong. With the support of a cybersecurity-focused managed services provider such as the Upper Echelon Technology Group, you can navigate the complexities of cybersecurity assessments and strengthen your business’s defenses.
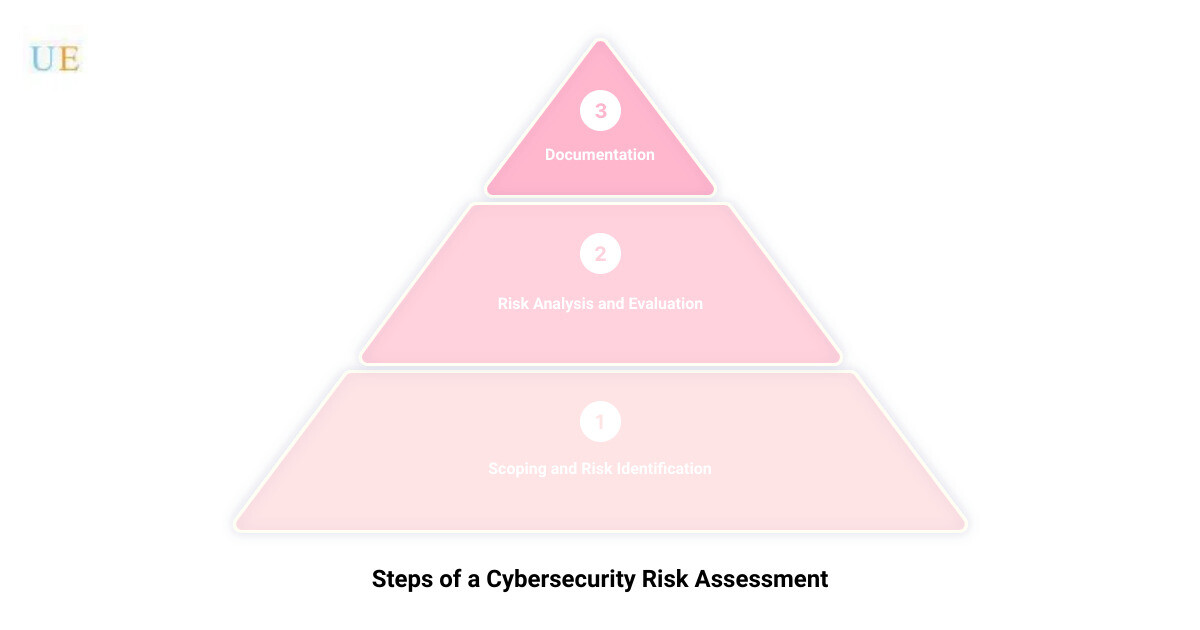
The Five Main Steps of a Cybersecurity Risk Assessment
Prevention is the best cure, especially when it comes to cybersecurity. Identifying potential threats and vulnerabilities can serve as a game-changer in your business’s security strategy. This is where a cybersecurity risk assessment comes into play. Here are the five main steps to conduct an effective cybersecurity risk assessment.
Scoping: Determining the Scope of the Assessment
Before diving into the data and systems, it’s crucial to establish the boundaries. This includes identifying key business objectives and pinpointing the technology assets essential to achieving them. The scope could be a specific business unit, a location, or a certain aspect of the business such as payment processing or a web application. Remember, a cybersecurity risk assessment is a resource-intensive exercise that requires the full support of all stakeholders.
Risk Identification: Creating an Inventory of Assets and Identifying Threats
The second step involves getting a clear picture of your IT landscape. You should identify and create an inventory of all physical and logical assets within the scope of the risk assessment. These assets are not only those critical to the business but also those that attackers would want to control, such as an Active Directory server. To identify potential threats to each asset, use a threat library like the MITRE ATT&CK Knowledge Base and resources from the Cyber Threat Alliance.
Risk Analysis: Determining the Likelihood and Impact of Each Risk Scenario
Once you’ve identified your assets and the threats they face, it’s time to analyze these risks. This step entails determining the likelihood of a cyber attack happening and assessing the potential impact on your business. It’s important to build a complete picture of the threat environment to make informed decisions about how and where to implement security controls.
Risk Evaluation: Classifying and Prioritizing Risks
The fourth step is all about prioritization. Not all risks are equal, so it’s essential to classify and prioritize them. This process helps you focus your resources on managing the most significant risks first. It’s crucial to define risk tolerance levels so that you know which risks are acceptable and which ones require immediate action.
Documentation: Keeping Track of Identified Risks and Progress Status
The final step in a cybersecurity risk assessment is documentation. Keeping a record of identified risks and the status of actions taken to mitigate them is vital. This documentation serves as a reference for future assessments and helps you track your progress over time. It also provides transparency and accountability, ensuring everyone in the organization is aware of the cybersecurity risks and the actions taken to manage them.
A cybersecurity risk assessment is a dynamic process that requires constant review and updates. With the support and expertise of a cybersecurity-focused managed services provider like Upper Echelon Technology Group, you can ensure your assessment is thorough, accurate, and effective in bolstering your business’s defenses against cyber threats.
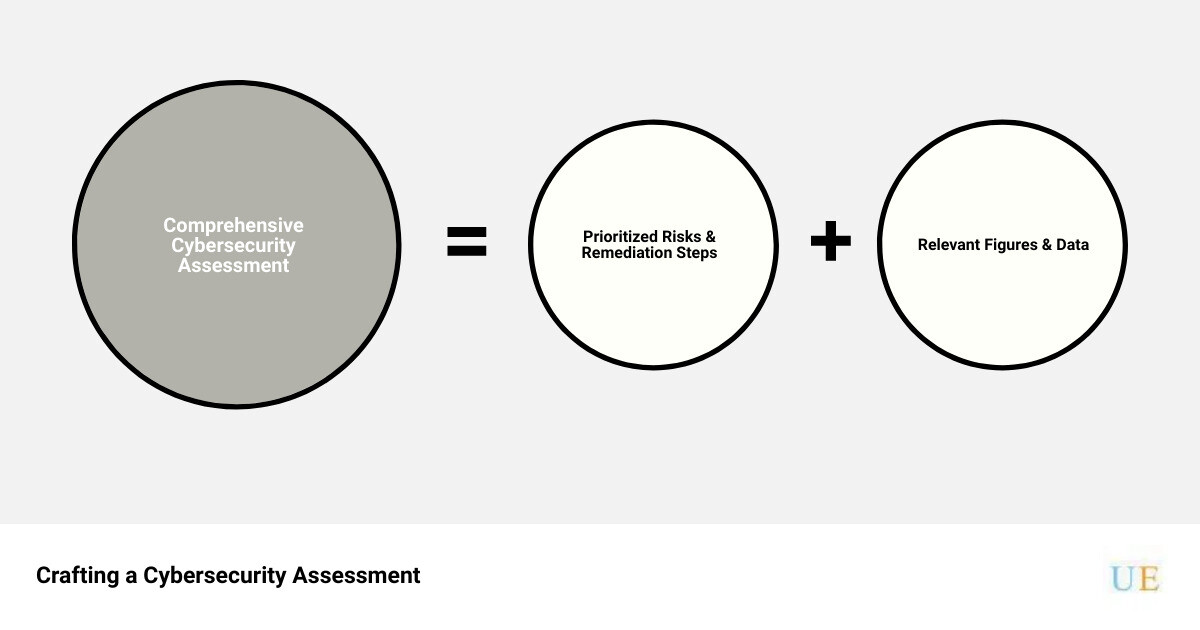
How to Write a Cybersecurity Assessment: A Step-by-Step Guide
A cybersecurity assessment is not just a document, but a detailed roadmap to your business’s digital safety. The assessment should outline the potential threats, vulnerabilities, and risks your business faces. It should also provide actionable solutions to mitigate these risks. Here’s a step-by-step guide on how to write a comprehensive and effective cybersecurity assessment.
Prioritizing Risks and Formulating Remediation Steps
The first step towards creating an effective cybersecurity assessment report is prioritizing risks. Start by identifying the most critical systems and data in your organization. These are the areas where a breach would have the most significant impact on your business. Once you’ve identified these areas, you can prioritize the risks associated with them.
Next, formulate remediation steps. These steps should detail how your organization plans to address each of the identified risks. The remediation plan should be clear, actionable, and specific to each risk.
Documenting the Assessment Methodology and Scope
Documenting the assessment methodology and scope is crucial for maintaining transparency and ensuring all stakeholders are on the same page. It includes stating the objective of the assessment, the areas it covers, the methods used to identify threats and vulnerabilities, and the criteria for evaluating risks. This part of the report ensures that everyone understands how the assessment was conducted and its limitations.
Describing Prioritized Findings and Recommendations
The cybersecurity assessment should include a section that describes your prioritized findings and recommendations. This section should detail each identified risk, its potential impact, the likelihood of occurrence, and the recommended action to mitigate it.
Your recommendations should be practical and achievable, considering your business’s resources and capabilities. They should also be prioritized based on the severity and impact of each risk.
Attaching Relevant Figures and Data to Support the Report
Finally, to add credibility and depth to your cybersecurity assessment, attach relevant figures and data. These could include statistics on the prevalence of certain types of cyber threats, case studies of similar businesses that have faced such threats, or diagrams showing how certain vulnerabilities can be exploited.
This data not only supports the main body of your report but also helps to illustrate the reality of the risks your business faces. It can be a powerful tool in persuading stakeholders of the importance of taking cybersecurity seriously.
Remember, a cybersecurity assessment is not a one-time task, but an ongoing process. Regularly updating your assessment to reflect new threats and vulnerabilities is crucial to maintaining robust cybersecurity defenses. By following these steps, you’ll be well on your way to creating a comprehensive cybersecurity assessment that can protect your business from cyber threats.
Preparing for a Cybersecurity Assessment: A Comprehensive Guide
To effectively safeguard your business, you need to know your enemy as well as understand the battlefield. A cybersecurity risk assessment can be a powerful tool in your arsenal, revealing vulnerabilities, illuminating threats, and guiding your defense strategies. However, without proper preparation, even the most detailed assessment can fall short. Below, we’ve outlined a step-by-step guide to help your business prepare for a cybersecurity assessment, ensuring a comprehensive and effective evaluation.
Mapping Your Assets
Your assessment begins with a clear understanding of your business assets. This can include everything from physical hardware like servers and computers, to digital assets like customer databases and proprietary software. Having a complete inventory of all physical and logical assets within the scope of the risk assessment is crucial. It’s not just about identifying the obvious targets, but also those assets that attackers could potentially leverage to expand an attack, such as an Active Directory server or a communications system.
Identifying Security Threats and Vulnerabilities
Once you’ve mapped your assets, it’s time to identify potential threats and vulnerabilities. Tools like the MITRE ATT&CK Knowledge Base, resources from the Cyber Threat Alliance, and advisories from agencies such as the Cybersecurity & Infrastructure Security Agency can provide valuable insights into potential threats and vulnerabilities. Remember, threats can come from a variety of sources, including new technologies, emerging cybercriminal tactics, and even internal sources.
Determining and Prioritizing Risks
After identifying threats and vulnerabilities, it’s time to determine and prioritize your risks. Analyze the likelihood and potential impact of each risk scenario. This step helps in allocating resources effectively, focusing on those risks that could have the greatest impact on your business.
Analyzing and Developing Security Controls
Next, analyze your current security controls and develop new ones where necessary. Evaluate whether your existing controls are effective against the identified risks. Understanding the effectiveness of your security controls will help ensure that your cybersecurity defenses are robust and up-to-date.
Documenting Results from the Risk Assessment Report
A comprehensive report documenting your findings is crucial for clarity, accountability, and future reference. This report should include your prioritized risks, assessment methodology, and scope. It should also provide detailed recommendations for mitigating the identified risks.
Creating a Remediation Plan to Reduce Risks
Based on your findings, create a clear and actionable remediation plan to address the identified risks. This plan should outline the steps your business will take to reduce its vulnerabilities and strengthen its cyber defenses.
Implementing Recommendations
The next step is implementing the recommendations from your remediation plan. This could involve updating software, strengthening firewalls, implementing new security policies, or even conducting cybersecurity training for your employees.
Evaluating Effectiveness and Repeating the Process
Finally, evaluate the effectiveness of your risk mitigation efforts and make adjustments as necessary. Cybersecurity is not a one-and-done task; it requires ongoing vigilance and adaptation. Regularly repeat the risk assessment process to ensure your defenses are continually updated to face new threats.
Remember, a well-prepared cybersecurity assessment can be a game-changer for your business, providing invaluable insights and guiding your cybersecurity strategy. By following these steps, you can ensure a thorough and effective assessment, keeping your business one step ahead in the ever-evolving cyber battlefield.

The Role of Managed Services Providers in Cybersecurity Assessment
In a digital world where cyber threats evolve with alarming speed, businesses must stay vigilant to protect their invaluable data. However, conducting a comprehensive cybersecurity assessment is a complex task requiring specialized knowledge and experience. This is where the role of a Managed Services Provider (MSP) becomes crucial.
The Need for Expertise: Why Businesses Should Consider Outsourcing Cybersecurity Assessment
Cybersecurity is not a one-size-fits-all solution. Each business faces unique risks based on its operations, data, technologies, and industry regulations. Understanding these nuances and tailoring a cybersecurity strategy requires an in-depth understanding of both IT and cybersecurity, a feat that can be challenging for businesses to achieve in-house.
By outsourcing cybersecurity assessments to a reputable MSP, businesses gain access to a team of experts with deep domain knowledge and experience. These experts can conduct thorough risk assessments, identifying potential vulnerabilities and providing actionable insights to strengthen security measures. An MSP can also provide 24x7x365 network monitoring and rapid incident response, ensuring that your technology serves your business, rather than your business serving your technology.
The Unique Selling Proposition of Upper Echelon Technology Group LLC
When it comes to cybersecurity, not all MSPs are created equal. What sets Upper Echelon Technology Group LLC apart is its personalized approach to IT Managed Services. We understand that solving tech issues is just one piece of the puzzle. We go beyond that and focus on your business needs, leveraging your technology assets in the best possible way to help your business.
At Upper Echelon, we do more than just fix technology issues. We make your team more efficient by leveraging technology and identifying areas where technology can improve your bottom line. Our portfolio of managed IT services offerings, which we constantly evaluate to ensure optimum protection and performance, is designed to serve your business, not the other way around.
Our commitment to our core values, including open communication, relentless pursuit of personal growth, and a true team spirit, drives us to provide a service that not only meets but exceeds your expectations.
In a world where cybersecurity threats loom large, partnering with an MSP like Upper Echelon Technology Group LLC can be a game-changer, providing your business with a robust, tailored cybersecurity strategy that propels you towards success.
Conclusion: The Long-Term Benefits of Regular Cybersecurity Assessments for Businesses
In the age of digital transformation, cybersecurity is no longer an optional add-on but a crucial linchpin that holds the integrity of business operations. It’s a reality that Upper Echelon Technology Group LLC understands and leverages to safeguard businesses. The partnership you form with us is a testament to your commitment to fortifying your business against cyber threats. But why exactly should you opt for regular cybersecurity assessments? Let’s unveil the benefits.
Regular cybersecurity assessments put you on the offensive. Instead of waiting for a cyber threat to disrupt your business operations, you proactively identify and mitigate potential risks. This proactive stance is crucial in a digital landscape where new threats emerge daily. Regular assessments ensure that your cybersecurity strategy remains robust and relevant, protecting your business from emerging threats.
Efficiency and profitability are twin benefits that come with regular cybersecurity assessments. By identifying areas where technology can improve your bottom line, such assessments can transform your IT infrastructure from a cost center into a profit generator. Moreover, by making your team more efficient through technology, assessments can improve overall productivity, further boosting profitability.
Regular assessments also ensure compliance with cybersecurity regulations. In an increasingly regulated environment, falling foul of compliance requirements can result in hefty fines, not to mention reputational damage. Regular assessments help you stay one step ahead, ensuring you meet all regulatory requirements and avoid potential penalties.
Finally, cybersecurity assessments contribute to the creation of a cybersecurity culture within your organization. By involving all employees in the process and making them aware of the threats, you help foster a sense of collective responsibility towards cybersecurity, which can significantly reduce the risk of human error leading to a breach.
Partnering with Upper Echelon Technology Group LLC for your cybersecurity assessments not only offers these benefits but also brings a personalized approach to IT Managed Services that is tailored to your business needs. Let’s make your business more secure, efficient, and profitable together.
In conclusion, regular cybersecurity assessments are more than just a defensive tactic – they are a strategic imperative for businesses looking to thrive in today’s digital world. By uncovering the hidden weaknesses in your cybersecurity strategy and turning them into strengths, you can propel your business forward, secure in the knowledge that your most valuable assets are protected.











