In an era where technology is at the heart of virtually every business operation, understanding and mitigating cyber threats is no longer optional, but a necessity. As a business owner, you’ve probably heard of the term ‘cyber security risk assessment,’ but what does it entail? Better yet, how does one go about assessing threat levels in cyber security? This article seeks to demystify this critical aspect of IT management, shedding light on why it’s crucial for your business growth and security.
Cyber threats are a looming risk for every business, irrespective of its size or industry. They can lead to catastrophic consequences such as loss of sensitive data, financial losses, damage to your brand’s reputation, and even halting of business operations. To safeguard your business from such threats, it’s essential to carry out a comprehensive cyber security risk assessment. This process helps in identifying potential risks and vulnerabilities, thereby enabling your business to establish effective countermeasures.
Assessing threat levels in cyber security involves several key steps, from defining cyber security threats, identifying information assets and potential risks, to conducting a full-blown cyber security risk assessment. This process aligns with international standards such as ISO 27001, which provides a framework for an information security management system (ISMS) to ensure the confidentiality, integrity, and availability of information by applying a risk management process.
In the subsequent sections, we delve deeper into the nitty-gritty of conducting a cyber security risk assessment and how Upper Echelon Technology Group, a cybersecurity-focused managed services provider, can support your business in this process. Stay tuned to learn how to crack the code of assessing threat levels in cyber security.
Understanding Cyber Security Risk Assessments
Unraveling the mystery of cyber security begins with understanding how to assess the potential threats your business might face. A comprehensive cyber security risk assessment is a crucial first step that can help you map out the digital landscape and identify potential hazards.
Defining Cyber Security Threats
Just as a ship’s captain needs to know the depth and temperature of the waters he sails in, as a business owner, you need to understand the various threats lurking in the cyber ocean. Cyber threats are tactics and techniques used by threat actors that can harm your organization’s digital assets. These threats can range from malware attacks to phishing scams and more. By identifying potential threats, you can better equip your business with the necessary defenses.
Identifying Information Assets and Potential Risks
Next, you need to identify the information assets that could be affected by a cyber attack. These can be physical assets like hardware and systems or data assets like customer data and intellectual property. Understanding what you need to protect is crucial in identifying the risks that could affect those assets. This process involves risk estimation and evaluation, followed by the selection of controls to treat the identified risks.
The Role of ISO 27001 in Information Security Management
To help structure your risk assessment, the international standard ISO/IEC 27001:2013 (ISO 27001) provides the specifications for a best-practice Information Security Management System (ISMS). It outlines a risk-based approach to information security risk management that addresses people, processes, and technology.
ISO 27001 sets out the requirements of the information security risk assessment process. It mandates that organizations establish and maintain specific information security risk criteria, ensure that risk assessments produce consistent and comparable results, identify risks associated with the loss of confidentiality, integrity, and availability for information, and analyze and evaluate these risks.
The standard emphasizes the need for organizations to document their risk assessment process, which is where a cybersecurity-focused managed services provider like Upper Echelon Technology Group can be invaluable.
In the following sections, we will delve deeper into the process of conducting a cyber security risk assessment, highlighting how Upper Echelon Technology Group can support your business at every step of the way.
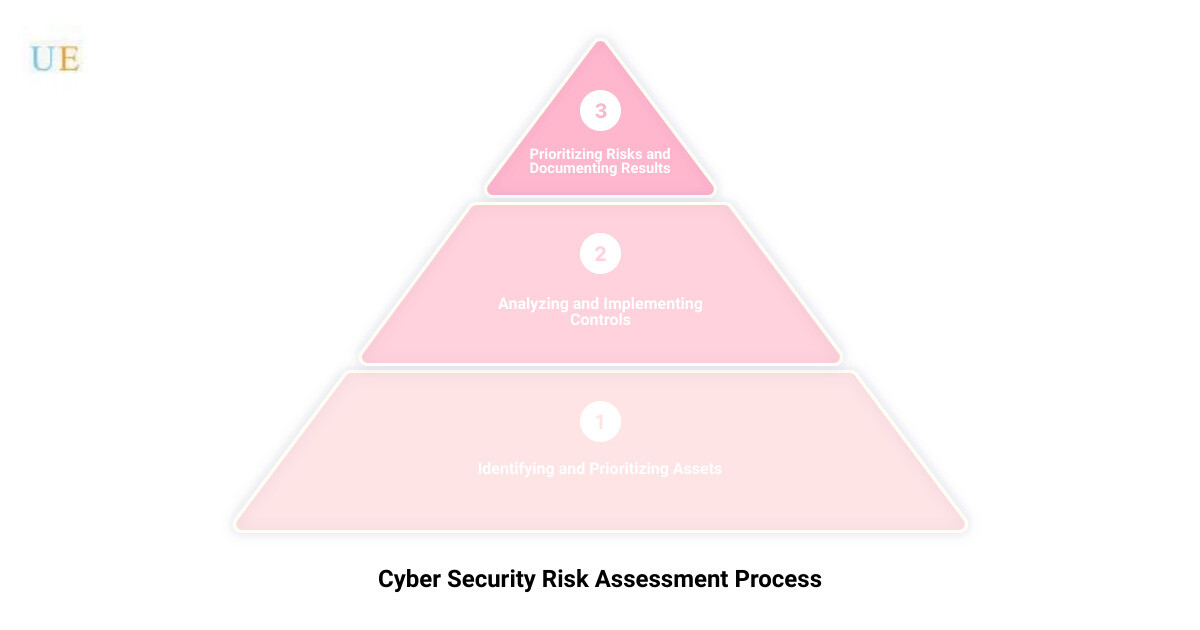
The Process of Conducting a Cyber Security Risk Assessment
Navigating the cyberspace can feel like a labyrinth, and without a proper map, you may find yourself lost in a maze of threats and vulnerabilities. That’s where a cyber security risk assessment comes in, providing a comprehensive blueprint to guide your business. Let’s walk through each crucial step of this process.
Identifying and Prioritizing Assets
The first step in any cyber security risk assessment is to identify and prioritize the assets that could be affected by a cyber attack. These assets could include physical assets like hardware, systems, and laptops, as well as intangible assets such as customer data and intellectual property. The goal is to create an inventory of all assets within the scope of the risk assessment, identifying those critical to your business operations.
Identifying Cyber Threats and Vulnerabilities
After identifying and prioritizing your assets, it’s time to identify the potential threats and vulnerabilities that could affect these assets. This involves exploring the tactics, techniques, and methods used by potential threat actors. High-quality, up-to-date cyber threat information can be found in resources like the MITRE ATT&CK Knowledge Base and advisories from government agencies, such as the Cybersecurity & Infrastructure Security Agency.
Analyzing and Implementing Controls
Next, it’s about analyzing and implementing controls that can address those threats. This involves evaluating the risks identified and selecting appropriate controls to mitigate them. The controls you choose should align with the risks your business faces. Implementing measures against unlikely events or events that won’t significantly impact your business can lead to wasted time and resources.
Calculating the Likelihood and Impact of Various Scenarios
Once the controls are in place, the next step is to calculate the likelihood and potential impact of various threat scenarios. This allows you to understand the potential damage a cyber attack could cause to your business. It’s crucial to use common terminology such as likelihood and impact to ensure there’s a shared understanding of the risk assessment across your organization.
Prioritizing Risks and Documenting Results
The final step in the process is prioritizing the identified risks based on their potential impact and likelihood. The results of the risk assessment should be documented thoroughly, providing a comprehensive overview of the complete risk management process. This not only helps in demonstrating compliance with various standards and laws but also aids in maintaining an overview of the risk environment and detecting any changes.
Remember, cyber security risk assessments are not a one-time event but a continuous process that needs to be revisited regularly. A proactive approach to identifying and managing risks can help your business stay ahead of potential threats and ensure your IT infrastructure remains robust and secure. And with the personalized approach of Upper Echelon Technology Group, you’re always one step ahead in the cyber security game.
Tools and Services for Effective Cyber Security Risk Assessment
When it comes to cyber security, your business can’t afford to be reactive. Effective risk assessment is a proactive game, and having the right tools and services can make all the difference. Let’s delve into the world of risk assessment tools and services that can bolster your defenses.
The Role of Risk Assessment Software Tools
Risk assessment software tools, such as vsRisk, play a pivotal role in simplifying and streamlining the complex process of cyber security risk assessments. These tools are designed to save your business time, effort, and resources by delivering consistent and repeatable assessments. With features like custom acceptance criteria, risk assessment wizards, and control set synchronization, these tools allow you to easily identify your assets, assess their vulnerabilities, and plan appropriate controls. Plus, with the ability to export your asset database, risk assessment software tools can also aid in populating an asset management system or register.
The Benefits of Cyber Health Check
Another service that can significantly enhance your cyber risk management strategy is a Cyber Health Check. This comprehensive service combines consultancy, audit, testing, and vulnerability assessments to evaluate your cyber risk exposure. In a fixed-price, three-day process, a Cyber Health Check will identify your actual risks, audit your responses, analyze your risk exposure, and create a prioritized action plan. This approach ensures you’re not just aware of potential threats but are actively working towards managing those risks in line with your business objectives.
The Expertise of IT Governance in Risk Assessment
Having a trusted partner in risk assessment can also be a game-changer for your business. IT Governance, for example, brings a wealth of experience in the cyber security and risk management domains. They have been delivering comprehensive risk assessments for over ten years, working with hundreds of organizations in all industries. Their team of qualified and experienced advisers can provide business-driven consultation and guidance, helping you navigate the risk assessment process with confidence.
In today’s digital world, a comprehensive and proactive approach to cyber security is non-negotiable. By leveraging the right tools and services, and partnering with experienced providers, your business can stay ahead of threats and ensure your information systems remain secure.
The Unique Approach of Upper Echelon Technology Group LLC in Cyber Security Risk Assessment
With the rising tide of cyber threats, navigating the vast ocean of cybersecurity can feel like a daunting task. But fear not, for Upper Echelon Technology Group LLC is your compass in this sea of uncertainty. Offering a unique approach to cybersecurity risk assessments, Upper Echelon Technology Group LLC goes beyond merely fixing tech issues, focusing instead on the larger picture of how technology can aid in business growth.
Personalized IT Managed Services
At the heart of their approach lies a commitment to personalized IT managed services. This means that the company doesn’t just address your tech issues; it dives deep into understanding your business needs, and helps you leverage your technology assets to improve your bottom line. This personalized approach sets Upper Echelon Technology Group LLC apart from other IT service providers, making them a trusted partner in managing your IT infrastructure.
This personalized approach translates into a thorough and tailored cybersecurity risk assessment process. Upper Echelon Technology Group LLC understands that each business is unique, and hence, the threats they face and the vulnerabilities they harbor are unique as well. Therefore, their risk assessment process is customized to suit the specific needs of your business, ensuring that your network is protected and optimized round the clock.
Tailored Solutions for Business-Specific Needs
In addition to providing personalized IT managed services, Upper Echelon Technology Group LLC also offers tailored solutions for business-specific needs. They understand that the one-size-fits-all approach doesn’t work when it comes to securing your business against cyber threats. Therefore, they work closely with you to understand your business, identify the areas where technology can improve your operations, and then implement solutions that specifically address those areas.
For instance, if your business has a strong online presence, Upper Echelon Technology Group LLC will focus on securing your web applications and data. If your business relies heavily on cloud services, they will ensure that your cloud infrastructure is secure. In essence, they identify the areas where technology can enhance your business and then provide solutions that are specifically tailored to meet those needs.
By offering personalized IT managed services and tailored solutions for business-specific needs, Upper Echelon Technology Group LLC ensures that your business is not only secure against cyber threats but is also able to leverage technology for business growth. In the ever-evolving landscape of cybersecurity, having a partner like Upper Echelon Technology Group LLC can make all the difference.
Conclusion: The Critical Role of Cyber Security Risk Assessment in Business Operations
As we navigate the complex waters of the digital age, the importance of cyber security risk assessment in business operations can’t be overstated. It’s not just about setting up firewalls and installing antivirus software anymore. It’s about understanding the unique risks your business faces, and strategically implementing controls to mitigate those risks.
Cyber security risk assessments are not a one-time event, but rather an ongoing process that helps businesses stay ahead of potential threats. It’s about identifying your information assets, understanding the risks that could affect those assets, and implementing the necessary controls to protect your business.
In the world of cyber security, complacency can be costly. Implementing the ISO 27001 framework not only ensures the protection of your information assets but also fosters a culture of risk management within your organization. It’s a comprehensive approach that looks at people, processes, and technology, ensuring that your business stays resilient in the face of cyber threats.
But conducting a cyber security risk assessment isn’t a simple task. It requires expertise and a deep understanding of the threat landscape. That’s where professional IT governance and managed services providers like Upper Echelon Technology Group LLC come in. With their personalized approach to IT managed services, they can help businesses identify their unique risks and implement tailored strategies to address those risks.
Upper Echelon Technology Group LLC goes beyond just fixing tech issues. They focus on your business needs and how you can leverage your technology assets in the best way possible. Their aim is to solve your technology issues, make your team more efficient by leveraging technology, and make your company more profitable by identifying areas where technology can improve your bottom line.
In conclusion, a cyber security risk assessment is a vital part of any business’s operations. It’s not something you can afford to ignore or put on the backburner. With the right approach and the right partner, you can turn cyber security from a threat into an opportunity for growth.
Remember, in the digital age, your business’s security is only as strong as its weakest link. Don’t let that weak link be a lack of understanding of your cyber security risks. Start your cyber security risk assessment today and safeguard your business against the threats of tomorrow.